HTTP response status code 508 is a server error message that is relevant to either WebDAV and alternatively to Cloudflare.
For WebDAV, 508 Loop Detected indicates that the server has terminated the directory tree request because an infinite loop has been detected.
For Cloudflare, 508 Resource Limit Reached indicates that the client account is exceeding one of the allocated resource limits.
Usage specific to WebDAV
When the 508 Loop Detected status code is received, it is because the client has submitted a WebDAV request for an entire directory and as part of the result, it creates a target somewhere in the same tree. As such, an infinite request/response loop is created and the server responds with Depth: Infinity. Consequently, the entire operation fails.
Usage specific to Cloudflare
When the 508 Resource Limit Reached status code is received, it is an error that is generated on the origin server indicating that one of the resource limits has been exceeded. Examples of resource limits include CPU usage, physical memory, and the number of processes.
Code references
.NET
HttpStatusCode.LoopDetected
Rust
http::StatusCode::LOOP_DETECTED
Rails
:loop_detected
Go
http.StatusLoopDetected
Symfony
Response::HTTP_LOOP_DETECTED
Python3.5+
http.HTTPStatus.LOOP_DETECTED
Apache HttpComponents Core
org.apache.hc.core5.http.HttpStatus.SC_LOOP_DETECTED
Angular
@angular/common/http/HttpStatusCode.LoopDetected
Takeaway
The 508 status code generated by WebDAV indicates that an infinite loop has been discovered while attempting to display a directory tree, whereas, with Cloudflare, the 508 status code indicates that a resource limit has been reached, as reported by the origin server.
See also
- WebDAV
- Cloudflare Error 508
- RFC 5842
Last updated: June 29, 2022
Coming across “Error 508. Resource Limit Is Reached” can put you off balance. It’s not a common HTTP error, but it can make both your site and webserver inaccessible.
But fret not. This article will explain what the HTTP Error 508 is, how you can troubleshoot it, and the preventative measures you can take to make sure that it doesn’t occur again.
Let’s get started!
Check out the video version
What Causes the “508 Resource Limit Is Reached” Error?
Most web host accounts have set limits on resources. If this limit is breached, a “508 Resource Limit Is Reached” error is triggered, and your site will be temporarily inaccessible.
This error is triggered at the server level and can be caused due to various factors, including excessive strain on server CPU and RAM resources. It’s also commonly associated with a high demand for concurrent processes, often seen if your site experiences an unusually high traffic volume.
A spike in website traffic could also be the result of an attempted DDoS attack. In this instance, your site will trigger a “508 Resource Limit Is Reached” error once the available resources have been exhausted during the attack. However, you might not have to do anything to fix the issue!
If you consider this surge in web traffic to be a one-off event, then you might choose to wait it out and see if the traffic subsides.
If you’re on a shared server, or you’ve subscribed to an entry-level hosting package, it’s more likely you’ll run into this type of error. If that’s the case, you’ll need to raise the resource limits in the short term to get your site back up and running again.
It might not be common, but when HTTP Error 508 does pop up, it can cause major problems for your site and your webserver. 👀 Learn how to fix it right here ⬇️Click to Tweet
How to Fix the “508 Resource Limit Is Reached” Error
When seeing higher traffic volumes than expected, your site can quickly exceed allocated resources, resulting in your server grinding to a halt.
Check Your Resource Usage
The first thing you can do to fix a resource limit error is to check your resource usage. Be sure to view server activity logs too. That’ll help in identifying the root cause of the problem.
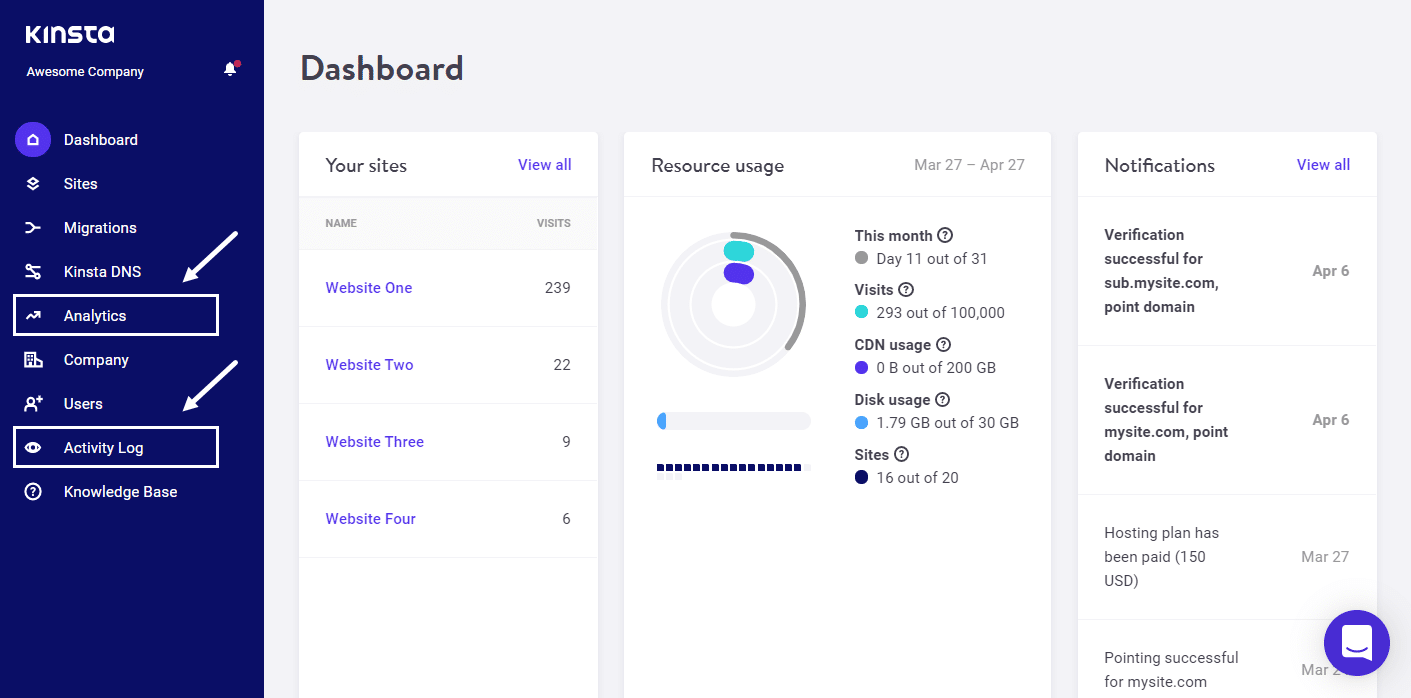
If you’re a Kinsta customer, then you can view resource usage and activity logs quite easily.
Log into your MyKinsta dashboard and select the site you wish to view. You can view the resource usage via the Analytics menu and activity logs via the Activity Log menu.
There are additional tools and methods you can use to supplement this as well.
Bear in mind that the limits you see imposed on your site will be slightly less than the limits required to keep it running.
Why is this?
Let’s say your website is on a shared server, along with many other customers and their sites (bear in mind this wouldn’t be the case with Kinsta). As your site starts to attract more traffic, the server that hosts all these many websites, including yours, is processing more and more requests to accommodate your growing traffic.
If your popularity trend continues, the server will eventually hit its resource limits for every site it’s hosting, including yours. You can spot this trend early to prevent downtime. A good hosting provider keeps a watchful eye on the volume. Your web host should contact you to warn you that your site will go down if it continues to consume resources at a higher rate than your plan permits.
Check Internal Processes Running on Your Site and Third-Party Code
The cause of a “508 Resource Limit Is Reached” error may not always be external. Resources can be excessively consumed by one or more rogue processes running internally on your site, such as:
- Site backups
- Cron jobs
- Long or complex database queries
- A hacked site running a harmful script
- Third-party code
In the case of third-party code, this can often be down to a particular Content Management Solution (CMS) extension. If, for instance, you’re running WordPress and have one or more plugins installed that are regularly consuming more resources than are allocated, then you’ll run into 508 errors sooner or later.
To avoid such a situation, it’s advisable to keep your CMS extensions up to date. With WordPress, this means keeping your themes and plugins updated to the latest versions.
If no update has been available for a particular theme or plugin for a while, then consider discontinuing using it in favor of a similar, more recently updated product or contacting the author to check if a new version is imminent.
Deactivate All Your Site’s Extensions and Enable Them One by One
It could be that one of your CMS extensions is consuming more server resources than it should—in which case you should try disabling them all. If the error vanishes, then your suspicion is confirmed—an extension is a culprit.
Begin by deactivating the site’s extensions.
Once all extensions are deactivated, reactivate them one at a time, retesting your site each time to identify the culprit. Your next course of action should be to contact the extension author to report the issue. If the extension is well maintained, its author should get back to you with a workable solution.
Deactivate Your Child Theme
Finally, if you’re using a WordPress child theme, you should check the changes that have been made to it to see if they could be causing any issues. You can quickly test this by temporarily swapping to the parent theme.
Contact Support
If none of those above ways helped you pinpoint the cause of the increased resource usage, you should contact your web host’s support team and ask them for more detailed information. Kinsta’s support team is available 24/7.
Preventative Measures
It’s a good idea to keep one eye on server resource usage as a preventative measure. It will give you a chance to get ahead of any potential issues that could bring your site down.
Self-maintenance is a sensible approach to helping keep hosting costs under control as your site grows and matures while simultaneously making sure your site’s downtime is minimized. Ideally, you’ll want to stay well below the allocated resource limit to reduce the risk.
Many add-on applications can help you keep track of your site’s usage. An application performance monitoring tool (like Kinsta APM) should be a top consideration when deciding how to keep watch over your site.
If you’re running any promotions or marketing drives, then expect and prepare for increases in site traffic. It can help to understand how your hosting provider counts visits to your site. In most cases, you won’t necessarily see a massive spike in traffic, but it’s still sensible to try and predict whether you’re likely to run close to your limits.
Additionally, make sure that your contact details (phone and email) are always up to date. That way, you won’t miss any resource usage alerts.
For peace of mind, we recommend investing in a dedicated webserver, or—barring that—a higher allocation of initial resources, such as with Kinsta’s disk space add-on. Having this flexibility will cost more, but the chances of your website going down will drop to nearly nothing.
Don’t let an HTTP Error 508 message ruin your day. 😥 With these quick tips you can troubleshoot it and take preventative measures to stop it from happening again👇Click to Tweet
Summary
When your site hits a “508 Resource Limit Is Reached” error, it can be challenging. You’ll want to get things back up and running as soon as possible. To prevent this error from happening again in the future, you should:
- Fix the current issue by checking what’s causing the high resource usage and
- Raise your site’s resources limits to take into account future growth and traffic as well
For more, check out how Kinsta does things differently with Google Cloud infrastructure and isolated software containers for each site.
From Wikipedia, the free encyclopedia
This is a list of Hypertext Transfer Protocol (HTTP) response status codes. Status codes are issued by a server in response to a client’s request made to the server. It includes codes from IETF Request for Comments (RFCs), other specifications, and some additional codes used in some common applications of the HTTP. The first digit of the status code specifies one of five standard classes of responses. The optional message phrases shown are typical, but any human-readable alternative may be provided, or none at all.
Unless otherwise stated, the status code is part of the HTTP standard (RFC 9110).
The Internet Assigned Numbers Authority (IANA) maintains the official registry of HTTP status codes.[1]
All HTTP response status codes are separated into five classes or categories. The first digit of the status code defines the class of response, while the last two digits do not have any classifying or categorization role. There are five classes defined by the standard:
- 1xx informational response – the request was received, continuing process
- 2xx successful – the request was successfully received, understood, and accepted
- 3xx redirection – further action needs to be taken in order to complete the request
- 4xx client error – the request contains bad syntax or cannot be fulfilled
- 5xx server error – the server failed to fulfil an apparently valid request
1xx informational response
An informational response indicates that the request was received and understood. It is issued on a provisional basis while request processing continues. It alerts the client to wait for a final response. The message consists only of the status line and optional header fields, and is terminated by an empty line. As the HTTP/1.0 standard did not define any 1xx status codes, servers must not[note 1] send a 1xx response to an HTTP/1.0 compliant client except under experimental conditions.
- 100 Continue
- The server has received the request headers and the client should proceed to send the request body (in the case of a request for which a body needs to be sent; for example, a POST request). Sending a large request body to a server after a request has been rejected for inappropriate headers would be inefficient. To have a server check the request’s headers, a client must send
Expect: 100-continueas a header in its initial request and receive a100 Continuestatus code in response before sending the body. If the client receives an error code such as 403 (Forbidden) or 405 (Method Not Allowed) then it should not send the request’s body. The response417 Expectation Failedindicates that the request should be repeated without theExpectheader as it indicates that the server does not support expectations (this is the case, for example, of HTTP/1.0 servers).[2] - 101 Switching Protocols
- The requester has asked the server to switch protocols and the server has agreed to do so.
- 102 Processing (WebDAV; RFC 2518)
- A WebDAV request may contain many sub-requests involving file operations, requiring a long time to complete the request. This code indicates that the server has received and is processing the request, but no response is available yet. [3] This prevents the client from timing out and assuming the request was lost. The status code is deprecated.[4]
- 103 Early Hints (RFC 8297)
- Used to return some response headers before final HTTP message.[5]
2xx success
This class of status codes indicates the action requested by the client was received, understood, and accepted.[1]
- 200 OK
- Standard response for successful HTTP requests. The actual response will depend on the request method used. In a GET request, the response will contain an entity corresponding to the requested resource. In a POST request, the response will contain an entity describing or containing the result of the action.
- 201 Created
- The request has been fulfilled, resulting in the creation of a new resource.[6]
- 202 Accepted
- The request has been accepted for processing, but the processing has not been completed. The request might or might not be eventually acted upon, and may be disallowed when processing occurs.
- 203 Non-Authoritative Information (since HTTP/1.1)
- The server is a transforming proxy (e.g. a Web accelerator) that received a 200 OK from its origin, but is returning a modified version of the origin’s response.[7][8]
- 204 No Content
- The server successfully processed the request, and is not returning any content.
- 205 Reset Content
- The server successfully processed the request, asks that the requester reset its document view, and is not returning any content.
- 206 Partial Content
- The server is delivering only part of the resource (byte serving) due to a range header sent by the client. The range header is used by HTTP clients to enable resuming of interrupted downloads, or split a download into multiple simultaneous streams.
- 207 Multi-Status (WebDAV; RFC 4918)
- The message body that follows is by default an XML message and can contain a number of separate response codes, depending on how many sub-requests were made.[9]
- 208 Already Reported (WebDAV; RFC 5842)
- The members of a DAV binding have already been enumerated in a preceding part of the (multistatus) response, and are not being included again.
- 226 IM Used (RFC 3229)
- The server has fulfilled a request for the resource, and the response is a representation of the result of one or more instance-manipulations applied to the current instance.[10]
3xx redirection
This class of status code indicates the client must take additional action to complete the request. Many of these status codes are used in URL redirection.[1]
A user agent may carry out the additional action with no user interaction only if the method used in the second request is GET or HEAD. A user agent may automatically redirect a request. A user agent should detect and intervene to prevent cyclical redirects.[11]
- 300 Multiple Choices
- Indicates multiple options for the resource from which the client may choose (via agent-driven content negotiation). For example, this code could be used to present multiple video format options, to list files with different filename extensions, or to suggest word-sense disambiguation.
- 301 Moved Permanently
- This and all future requests should be directed to the given URI.
- 302 Found (Previously «Moved temporarily»)
- Tells the client to look at (browse to) another URL. The HTTP/1.0 specification (RFC 1945) required the client to perform a temporary redirect with the same method (the original describing phrase was «Moved Temporarily»),[12] but popular browsers implemented 302 redirects by changing the method to GET. Therefore, HTTP/1.1 added status codes 303 and 307 to distinguish between the two behaviours.[11]
- 303 See Other (since HTTP/1.1)
- The response to the request can be found under another URI using the GET method. When received in response to a POST (or PUT/DELETE), the client should presume that the server has received the data and should issue a new GET request to the given URI.
- 304 Not Modified
- Indicates that the resource has not been modified since the version specified by the request headers If-Modified-Since or If-None-Match. In such case, there is no need to retransmit the resource since the client still has a previously-downloaded copy.
- 305 Use Proxy (since HTTP/1.1)
- The requested resource is available only through a proxy, the address for which is provided in the response. For security reasons, many HTTP clients (such as Mozilla Firefox and Internet Explorer) do not obey this status code.
- 306 Switch Proxy
- No longer used. Originally meant «Subsequent requests should use the specified proxy.»
- 307 Temporary Redirect (since HTTP/1.1)
- In this case, the request should be repeated with another URI; however, future requests should still use the original URI. In contrast to how 302 was historically implemented, the request method is not allowed to be changed when reissuing the original request. For example, a POST request should be repeated using another POST request.
- 308 Permanent Redirect
- This and all future requests should be directed to the given URI. 308 parallel the behaviour of 301, but does not allow the HTTP method to change. So, for example, submitting a form to a permanently redirected resource may continue smoothly.
4xx client errors
This class of status code is intended for situations in which the error seems to have been caused by the client. Except when responding to a HEAD request, the server should include an entity containing an explanation of the error situation, and whether it is a temporary or permanent condition. These status codes are applicable to any request method. User agents should display any included entity to the user.
- 400 Bad Request
- The server cannot or will not process the request due to an apparent client error (e.g., malformed request syntax, size too large, invalid request message framing, or deceptive request routing).
- 401 Unauthorized
- Similar to 403 Forbidden, but specifically for use when authentication is required and has failed or has not yet been provided. The response must include a WWW-Authenticate header field containing a challenge applicable to the requested resource. See Basic access authentication and Digest access authentication. 401 semantically means «unauthorised», the user does not have valid authentication credentials for the target resource.
- Some sites incorrectly issue HTTP 401 when an IP address is banned from the website (usually the website domain) and that specific address is refused permission to access a website.[citation needed]
- 402 Payment Required
- Reserved for future use. The original intention was that this code might be used as part of some form of digital cash or micropayment scheme, as proposed, for example, by GNU Taler,[14] but that has not yet happened, and this code is not widely used. Google Developers API uses this status if a particular developer has exceeded the daily limit on requests.[15] Sipgate uses this code if an account does not have sufficient funds to start a call.[16] Shopify uses this code when the store has not paid their fees and is temporarily disabled.[17] Stripe uses this code for failed payments where parameters were correct, for example blocked fraudulent payments.[18]
- 403 Forbidden
- The request contained valid data and was understood by the server, but the server is refusing action. This may be due to the user not having the necessary permissions for a resource or needing an account of some sort, or attempting a prohibited action (e.g. creating a duplicate record where only one is allowed). This code is also typically used if the request provided authentication by answering the WWW-Authenticate header field challenge, but the server did not accept that authentication. The request should not be repeated.
- 404 Not Found
- The requested resource could not be found but may be available in the future. Subsequent requests by the client are permissible.
- 405 Method Not Allowed
- A request method is not supported for the requested resource; for example, a GET request on a form that requires data to be presented via POST, or a PUT request on a read-only resource.
- 406 Not Acceptable
- The requested resource is capable of generating only content not acceptable according to the Accept headers sent in the request. See Content negotiation.
- 407 Proxy Authentication Required
- The client must first authenticate itself with the proxy.
- 408 Request Timeout
- The server timed out waiting for the request. According to HTTP specifications: «The client did not produce a request within the time that the server was prepared to wait. The client MAY repeat the request without modifications at any later time.»
- 409 Conflict
- Indicates that the request could not be processed because of conflict in the current state of the resource, such as an edit conflict between multiple simultaneous updates.
- 410 Gone
- Indicates that the resource requested was previously in use but is no longer available and will not be available again. This should be used when a resource has been intentionally removed and the resource should be purged. Upon receiving a 410 status code, the client should not request the resource in the future. Clients such as search engines should remove the resource from their indices. Most use cases do not require clients and search engines to purge the resource, and a «404 Not Found» may be used instead.
- 411 Length Required
- The request did not specify the length of its content, which is required by the requested resource.
- 412 Precondition Failed
- The server does not meet one of the preconditions that the requester put on the request header fields.
- 413 Payload Too Large
- The request is larger than the server is willing or able to process. Previously called «Request Entity Too Large» in RFC 2616.[19]
- 414 URI Too Long
- The URI provided was too long for the server to process. Often the result of too much data being encoded as a query-string of a GET request, in which case it should be converted to a POST request. Called «Request-URI Too Long» previously in RFC 2616.[20]
- 415 Unsupported Media Type
- The request entity has a media type which the server or resource does not support. For example, the client uploads an image as image/svg+xml, but the server requires that images use a different format.
- 416 Range Not Satisfiable
- The client has asked for a portion of the file (byte serving), but the server cannot supply that portion. For example, if the client asked for a part of the file that lies beyond the end of the file. Called «Requested Range Not Satisfiable» previously RFC 2616.[21]
- 417 Expectation Failed
- The server cannot meet the requirements of the Expect request-header field.[22]
- 418 I’m a teapot (RFC 2324, RFC 7168)
- This code was defined in 1998 as one of the traditional IETF April Fools’ jokes, in RFC 2324, Hyper Text Coffee Pot Control Protocol, and is not expected to be implemented by actual HTTP servers. The RFC specifies this code should be returned by teapots requested to brew coffee.[23] This HTTP status is used as an Easter egg in some websites, such as Google.com’s «I’m a teapot» easter egg.[24][25][26] Sometimes, this status code is also used as a response to a blocked request, instead of the more appropriate 403 Forbidden.[27][28]
- 421 Misdirected Request
- The request was directed at a server that is not able to produce a response (for example because of connection reuse).
- 422 Unprocessable Entity
- The request was well-formed but was unable to be followed due to semantic errors.[9]
- 423 Locked (WebDAV; RFC 4918)
- The resource that is being accessed is locked.[9]
- 424 Failed Dependency (WebDAV; RFC 4918)
- The request failed because it depended on another request and that request failed (e.g., a PROPPATCH).[9]
- 425 Too Early (RFC 8470)
- Indicates that the server is unwilling to risk processing a request that might be replayed.
- 426 Upgrade Required
- The client should switch to a different protocol such as TLS/1.3, given in the Upgrade header field.
- 428 Precondition Required (RFC 6585)
- The origin server requires the request to be conditional. Intended to prevent the ‘lost update’ problem, where a client GETs a resource’s state, modifies it, and PUTs it back to the server, when meanwhile a third party has modified the state on the server, leading to a conflict.[29]
- 429 Too Many Requests (RFC 6585)
- The user has sent too many requests in a given amount of time. Intended for use with rate-limiting schemes.[29]
- 431 Request Header Fields Too Large (RFC 6585)
- The server is unwilling to process the request because either an individual header field, or all the header fields collectively, are too large.[29]
- 451 Unavailable For Legal Reasons (RFC 7725)
- A server operator has received a legal demand to deny access to a resource or to a set of resources that includes the requested resource.[30] The code 451 was chosen as a reference to the novel Fahrenheit 451 (see the Acknowledgements in the RFC).
5xx server errors
The server failed to fulfil a request.
Response status codes beginning with the digit «5» indicate cases in which the server is aware that it has encountered an error or is otherwise incapable of performing the request. Except when responding to a HEAD request, the server should include an entity containing an explanation of the error situation, and indicate whether it is a temporary or permanent condition. Likewise, user agents should display any included entity to the user. These response codes are applicable to any request method.
- 500 Internal Server Error
- A generic error message, given when an unexpected condition was encountered and no more specific message is suitable.
- 501 Not Implemented
- The server either does not recognize the request method, or it lacks the ability to fulfil the request. Usually this implies future availability (e.g., a new feature of a web-service API).
- 502 Bad Gateway
- The server was acting as a gateway or proxy and received an invalid response from the upstream server.
- 503 Service Unavailable
- The server cannot handle the request (because it is overloaded or down for maintenance). Generally, this is a temporary state.[31]
- 504 Gateway Timeout
- The server was acting as a gateway or proxy and did not receive a timely response from the upstream server.
- 505 HTTP Version Not Supported
- The server does not support the HTTP version used in the request.
- 506 Variant Also Negotiates (RFC 2295)
- Transparent content negotiation for the request results in a circular reference.[32]
- 507 Insufficient Storage (WebDAV; RFC 4918)
- The server is unable to store the representation needed to complete the request.[9]
- 508 Loop Detected (WebDAV; RFC 5842)
- The server detected an infinite loop while processing the request (sent instead of 208 Already Reported).
- 510 Not Extended (RFC 2774)
- Further extensions to the request are required for the server to fulfil it.[33]
- 511 Network Authentication Required (RFC 6585)
- The client needs to authenticate to gain network access. Intended for use by intercepting proxies used to control access to the network (e.g., «captive portals» used to require agreement to Terms of Service before granting full Internet access via a Wi-Fi hotspot).[29]
Unofficial codes
The following codes are not specified by any standard.
- 419 Page Expired (Laravel Framework)
- Used by the Laravel Framework when a CSRF Token is missing or expired.
- 420 Method Failure (Spring Framework)
- A deprecated response used by the Spring Framework when a method has failed.[34]
- 420 Enhance Your Calm (Twitter)
- Returned by version 1 of the Twitter Search and Trends API when the client is being rate limited; versions 1.1 and later use the 429 Too Many Requests response code instead.[35] The phrase «Enhance your calm» comes from the 1993 movie Demolition Man, and its association with this number is likely a reference to cannabis.[citation needed]
- 430 Request Header Fields Too Large (Shopify)
- Used by Shopify, instead of the 429 Too Many Requests response code, when too many URLs are requested within a certain time frame.[36]
- 450 Blocked by Windows Parental Controls (Microsoft)
- The Microsoft extension code indicated when Windows Parental Controls are turned on and are blocking access to the requested webpage.[37]
- 498 Invalid Token (Esri)
- Returned by ArcGIS for Server. Code 498 indicates an expired or otherwise invalid token.[38]
- 499 Token Required (Esri)
- Returned by ArcGIS for Server. Code 499 indicates that a token is required but was not submitted.[38]
- 509 Bandwidth Limit Exceeded (Apache Web Server/cPanel)
- The server has exceeded the bandwidth specified by the server administrator; this is often used by shared hosting providers to limit the bandwidth of customers.[39]
- 529 Site is overloaded
- Used by Qualys in the SSLLabs server testing API to signal that the site can’t process the request.[40]
- 530 Site is frozen
- Used by the Pantheon Systems web platform to indicate a site that has been frozen due to inactivity.[41]
- 598 (Informal convention) Network read timeout error
- Used by some HTTP proxies to signal a network read timeout behind the proxy to a client in front of the proxy.[42]
- 599 Network Connect Timeout Error
- An error used by some HTTP proxies to signal a network connect timeout behind the proxy to a client in front of the proxy.
Internet Information Services
Microsoft’s Internet Information Services (IIS) web server expands the 4xx error space to signal errors with the client’s request.
- 440 Login Time-out
- The client’s session has expired and must log in again.[43]
- 449 Retry With
- The server cannot honour the request because the user has not provided the required information.[44]
- 451 Redirect
- Used in Exchange ActiveSync when either a more efficient server is available or the server cannot access the users’ mailbox.[45] The client is expected to re-run the HTTP AutoDiscover operation to find a more appropriate server.[46]
IIS sometimes uses additional decimal sub-codes for more specific information,[47] however these sub-codes only appear in the response payload and in documentation, not in the place of an actual HTTP status code.
nginx
The nginx web server software expands the 4xx error space to signal issues with the client’s request.[48][49]
- 444 No Response
- Used internally[50] to instruct the server to return no information to the client and close the connection immediately.
- 494 Request header too large
- Client sent too large request or too long header line.
- 495 SSL Certificate Error
- An expansion of the 400 Bad Request response code, used when the client has provided an invalid client certificate.
- 496 SSL Certificate Required
- An expansion of the 400 Bad Request response code, used when a client certificate is required but not provided.
- 497 HTTP Request Sent to HTTPS Port
- An expansion of the 400 Bad Request response code, used when the client has made a HTTP request to a port listening for HTTPS requests.
- 499 Client Closed Request
- Used when the client has closed the request before the server could send a response.
Cloudflare
Cloudflare’s reverse proxy service expands the 5xx series of errors space to signal issues with the origin server.[51]
- 520 Web Server Returned an Unknown Error
- The origin server returned an empty, unknown, or unexpected response to Cloudflare.[52]
- 521 Web Server Is Down
- The origin server refused connections from Cloudflare. Security solutions at the origin may be blocking legitimate connections from certain Cloudflare IP addresses.
- 522 Connection Timed Out
- Cloudflare timed out contacting the origin server.
- 523 Origin Is Unreachable
- Cloudflare could not reach the origin server; for example, if the DNS records for the origin server are incorrect or missing.
- 524 A Timeout Occurred
- Cloudflare was able to complete a TCP connection to the origin server, but did not receive a timely HTTP response.
- 525 SSL Handshake Failed
- Cloudflare could not negotiate a SSL/TLS handshake with the origin server.
- 526 Invalid SSL Certificate
- Cloudflare could not validate the SSL certificate on the origin web server. Also used by Cloud Foundry’s gorouter.
- 527 Railgun Error
- Error 527 indicates an interrupted connection between Cloudflare and the origin server’s Railgun server.[53]
- 530
- Error 530 is returned along with a 1xxx error.[54]
AWS Elastic Load Balancer
Amazon’s Elastic Load Balancing adds a few custom return codes
- 460
- Client closed the connection with the load balancer before the idle timeout period elapsed. Typically when client timeout is sooner than the Elastic Load Balancer’s timeout.[55]
- 463
- The load balancer received an X-Forwarded-For request header with more than 30 IP addresses.[55]
- 464
- Incompatible protocol versions between Client and Origin server.[55]
- 561 Unauthorized
- An error around authentication returned by a server registered with a load balancer. You configured a listener rule to authenticate users, but the identity provider (IdP) returned an error code when authenticating the user.[55]
Caching warning codes (obsoleted)
The following caching related warning codes were specified under RFC 7234. Unlike the other status codes above, these were not sent as the response status in the HTTP protocol, but as part of the «Warning» HTTP header.[56][57]
Since this «Warning» header is often neither sent by servers nor acknowledged by clients, this header and its codes were obsoleted by the HTTP Working Group in 2022 with RFC 9111.[58]
- 110 Response is Stale
- The response provided by a cache is stale (the content’s age exceeds a maximum age set by a Cache-Control header or heuristically chosen lifetime).
- 111 Revalidation Failed
- The cache was unable to validate the response, due to an inability to reach the origin server.
- 112 Disconnected Operation
- The cache is intentionally disconnected from the rest of the network.
- 113 Heuristic Expiration
- The cache heuristically chose a freshness lifetime greater than 24 hours and the response’s age is greater than 24 hours.
- 199 Miscellaneous Warning
- Arbitrary, non-specific warning. The warning text may be logged or presented to the user.
- 214 Transformation Applied
- Added by a proxy if it applies any transformation to the representation, such as changing the content encoding, media type or the like.
- 299 Miscellaneous Persistent Warning
- Same as 199, but indicating a persistent warning.
See also
- Custom error pages
- List of FTP server return codes
- List of HTTP header fields
- List of SMTP server return codes
- Common Log Format
Explanatory notes
- ^ Emphasised words and phrases such as must and should represent interpretation guidelines as given by RFC 2119
References
- ^ a b c «Hypertext Transfer Protocol (HTTP) Status Code Registry». Iana.org. Archived from the original on December 11, 2011. Retrieved January 8, 2015.
- ^ Fielding, Roy T. «RFC 9110: HTTP Semantics and Content, Section 10.1.1 «Expect»«.
- ^ Goland, Yaronn; Whitehead, Jim; Faizi, Asad; Carter, Steve R.; Jensen, Del (February 1999). HTTP Extensions for Distributed Authoring – WEBDAV. IETF. doi:10.17487/RFC2518. RFC 2518. Retrieved October 24, 2009.
- ^ «102 Processing — HTTP MDN». 102 status code is deprecated
- ^ Oku, Kazuho (December 2017). An HTTP Status Code for Indicating Hints. IETF. doi:10.17487/RFC8297. RFC 8297. Retrieved December 20, 2017.
- ^ Stewart, Mark; djna. «Create request with POST, which response codes 200 or 201 and content». Stack Overflow. Archived from the original on October 11, 2016. Retrieved October 16, 2015.
- ^ «RFC 9110: HTTP Semantics and Content, Section 15.3.4».
- ^ «RFC 9110: HTTP Semantics and Content, Section 7.7».
- ^ a b c d e Dusseault, Lisa, ed. (June 2007). HTTP Extensions for Web Distributed Authoring and Versioning (WebDAV). IETF. doi:10.17487/RFC4918. RFC 4918. Retrieved October 24, 2009.
- ^ Delta encoding in HTTP. IETF. January 2002. doi:10.17487/RFC3229. RFC 3229. Retrieved February 25, 2011.
- ^ a b «RFC 9110: HTTP Semantics and Content, Section 15.4 «Redirection 3xx»«.
- ^ Berners-Lee, Tim; Fielding, Roy T.; Nielsen, Henrik Frystyk (May 1996). Hypertext Transfer Protocol – HTTP/1.0. IETF. doi:10.17487/RFC1945. RFC 1945. Retrieved October 24, 2009.
- ^ «The GNU Taler tutorial for PHP Web shop developers 0.4.0». docs.taler.net. Archived from the original on November 8, 2017. Retrieved October 29, 2017.
- ^ «Google API Standard Error Responses». 2016. Archived from the original on May 25, 2017. Retrieved June 21, 2017.
- ^ «Sipgate API Documentation». Archived from the original on July 10, 2018. Retrieved July 10, 2018.
- ^ «Shopify Documentation». Archived from the original on July 25, 2018. Retrieved July 25, 2018.
- ^ «Stripe API Reference – Errors». stripe.com. Retrieved October 28, 2019.
- ^ «RFC2616 on status 413». Tools.ietf.org. Archived from the original on March 7, 2011. Retrieved November 11, 2015.
- ^ «RFC2616 on status 414». Tools.ietf.org. Archived from the original on March 7, 2011. Retrieved November 11, 2015.
- ^ «RFC2616 on status 416». Tools.ietf.org. Archived from the original on March 7, 2011. Retrieved November 11, 2015.
- ^ TheDeadLike. «HTTP/1.1 Status Codes 400 and 417, cannot choose which». serverFault. Archived from the original on October 10, 2015. Retrieved October 16, 2015.
- ^ Larry Masinter (April 1, 1998). Hyper Text Coffee Pot Control Protocol (HTCPCP/1.0). doi:10.17487/RFC2324. RFC 2324.
Any attempt to brew coffee with a teapot should result in the error code «418 I’m a teapot». The resulting entity body MAY be short and stout.
- ^ I’m a teapot
- ^ Barry Schwartz (August 26, 2014). «New Google Easter Egg For SEO Geeks: Server Status 418, I’m A Teapot». Search Engine Land. Archived from the original on November 15, 2015. Retrieved November 4, 2015.
- ^ «Google’s Teapot». Retrieved October 23, 2017.[dead link]
- ^ «Enable extra web security on a website». DreamHost. Retrieved December 18, 2022.
- ^ «I Went to a Russian Website and All I Got Was This Lousy Teapot». PCMag. Retrieved December 18, 2022.
- ^ a b c d Nottingham, M.; Fielding, R. (April 2012). «RFC 6585 – Additional HTTP Status Codes». Request for Comments. Internet Engineering Task Force. Archived from the original on May 4, 2012. Retrieved May 1, 2012.
- ^ Bray, T. (February 2016). «An HTTP Status Code to Report Legal Obstacles». ietf.org. Archived from the original on March 4, 2016. Retrieved March 7, 2015.
- ^ alex. «What is the correct HTTP status code to send when a site is down for maintenance?». Stack Overflow. Archived from the original on October 11, 2016. Retrieved October 16, 2015.
- ^ Holtman, Koen; Mutz, Andrew H. (March 1998). Transparent Content Negotiation in HTTP. IETF. doi:10.17487/RFC2295. RFC 2295. Retrieved October 24, 2009.
- ^ Nielsen, Henrik Frystyk; Leach, Paul; Lawrence, Scott (February 2000). An HTTP Extension Framework. IETF. doi:10.17487/RFC2774. RFC 2774. Retrieved October 24, 2009.
- ^ «Enum HttpStatus». Spring Framework. org.springframework.http. Archived from the original on October 25, 2015. Retrieved October 16, 2015.
- ^ «Twitter Error Codes & Responses». Twitter. 2014. Archived from the original on September 27, 2017. Retrieved January 20, 2014.
- ^ «HTTP Status Codes and SEO: what you need to know». ContentKing. Retrieved August 9, 2019.
- ^ «Screenshot of error page». Archived from the original (bmp) on May 11, 2013. Retrieved October 11, 2009.
- ^ a b «Using token-based authentication». ArcGIS Server SOAP SDK. Archived from the original on September 26, 2014. Retrieved September 8, 2014.
- ^ «HTTP Error Codes and Quick Fixes». Docs.cpanel.net. Archived from the original on November 23, 2015. Retrieved October 15, 2015.
- ^ «SSL Labs API v3 Documentation». github.com.
- ^ «Platform Considerations | Pantheon Docs». pantheon.io. Archived from the original on January 6, 2017. Retrieved January 5, 2017.
- ^ «HTTP status codes — ascii-code.com». www.ascii-code.com. Archived from the original on January 7, 2017. Retrieved December 23, 2016.
- ^
«Error message when you try to log on to Exchange 2007 by using Outlook Web Access: «440 Login Time-out»«. Microsoft. 2010. Retrieved November 13, 2013. - ^ «2.2.6 449 Retry With Status Code». Microsoft. 2009. Archived from the original on October 5, 2009. Retrieved October 26, 2009.
- ^ «MS-ASCMD, Section 3.1.5.2.2». Msdn.microsoft.com. Archived from the original on March 26, 2015. Retrieved January 8, 2015.
- ^ «Ms-oxdisco». Msdn.microsoft.com. Archived from the original on July 31, 2014. Retrieved January 8, 2015.
- ^ «The HTTP status codes in IIS 7.0». Microsoft. July 14, 2009. Archived from the original on April 9, 2009. Retrieved April 1, 2009.
- ^ «ngx_http_request.h». nginx 1.9.5 source code. nginx inc. Archived from the original on September 19, 2017. Retrieved January 9, 2016.
- ^ «ngx_http_special_response.c». nginx 1.9.5 source code. nginx inc. Archived from the original on May 8, 2018. Retrieved January 9, 2016.
- ^ «return» directive Archived March 1, 2018, at the Wayback Machine (http_rewrite module) documentation.
- ^ «Troubleshooting: Error Pages». Cloudflare. Archived from the original on March 4, 2016. Retrieved January 9, 2016.
- ^ «Error 520: web server returns an unknown error». Cloudflare.
- ^ «527 Error: Railgun Listener to origin error». Cloudflare. Archived from the original on October 13, 2016. Retrieved October 12, 2016.
- ^ «Error 530». Cloudflare. Retrieved November 1, 2019.
- ^ a b c d «Troubleshoot Your Application Load Balancers – Elastic Load Balancing». docs.aws.amazon.com. Retrieved May 17, 2023.
- ^ «Hypertext Transfer Protocol (HTTP/1.1): Caching». datatracker.ietf.org. Retrieved September 25, 2021.
- ^ «Warning — HTTP | MDN». developer.mozilla.org. Retrieved August 15, 2021.
Some text was copied from this source, which is available under a Creative Commons Attribution-ShareAlike 2.5 Generic (CC BY-SA 2.5) license.
- ^ «RFC 9111: HTTP Caching, Section 5.5 «Warning»«. June 2022.
External links
- «RFC 9110: HTTP Semantics and Content, Section 15 «Status Codes»«.
- Hypertext Transfer Protocol (HTTP) Status Code Registry at the Internet Assigned Numbers Authority
- MDN status code reference at mozilla.org
Error 508 occurs when you exceed the resource limits in your plan. There are several reasons that can cause this.
In this guide, 508 error: how to solve it, we will see what are the possible causes of the error 508. Based on the origin of the problem, we’ll also see how to solve it, in order to get the site accessible again and avoid the error from recurring.
To start with, let’s see what is meant by resource limits and what systems are used to keep consumption under control.
Error 508 and resource limits
Hosting resource limits are used to ensure that all sites hosted on the server are functioning properly, without overloads that compromise one or more sites.
The moment these limits are exceeded when trying to visit the site you will see an error page with a warning like this:
Error 508 Resource Limit Is Reached
How is resource management monitored?
Our servers are equipped with CloudLinux, a management system designed specifically for hosting environments.
CloudLinux uses a technology called LVE or Lightweight Virtual Environment. This system allows you to isolate individual accounts and limit resources. Thus, by imposing limits on the use of CPU, RAM, I/O and the number of processes, you can get a proper distribution of resources.
The goal is to prevent a single user from overloading the entire server, causing problems for all users sharing the same server. A situation that could occur in a shared hosting, but that can be avoided by adopting this system.
In the absence of such systems, and before they were adopted, the sudden spike in traffic of a single site was able to cause disruption to all sites hosted on the same machine. In such a situation, you would have had the site down because of an excessive request of resources from another site hosted on the same server.
What happens when you exceed your resource limit?
First, we need to understand what kind of resources we are talking about. CloudLinux monitors the usage of RAM, CPU, I/O and the number of processes.
Error 508 or, as we will see other errors 5xx, occur when an account exceeds the threshold of allowed resources. For example, exceeding the memory usage or the maximum number of processes allowed.
Let’s see what happens in the different cases.
If you reach the set memory limit, the system will first try to free memory, starting with the cache. If the memory is still insufficient, some processes will be terminated.
This will result in error 500 or error 503. These are temporary errors that are removed automatically as soon as you are within the limits.
When the CPU limit is reached, the system first slows down the running processes to keep them within the limits. If, on the other hand, the maximum number of processes is exceeded, you get error 508.
When the I/O limits are exceeded, i.e. reading and writing data on the disk, CloudLinux slows down the processes in progress so as to keep them within the limits, in these cases the site remains active.
How to check the resources used by your site
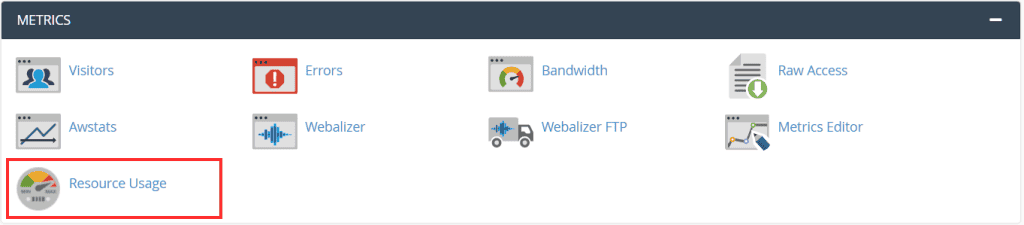
You can check your resource usage and see if you’ve exceeded your limits by checking your account metrics from your control panel.
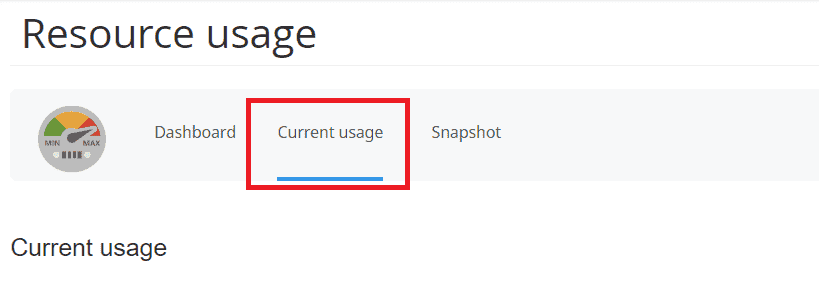
Log in to cPanel and open the “Resource Usage” tool from the metrics section.
This will allow you to see if your site has been forced back into the limits recently. For real-time consumption just click on Current usage as you see in this screenshot.
Error 508: possible causes and how to solve it
We have seen that error 508 appears when you exceed your account limits, but what is behind it, how can you solve it?
Identifying the causes of error 508 is the only way to solve the problem. Let’s take a look at the possible causes and what methods we can use to fix them.
High traffic and DDoS attacks
Among the most common situations that can lead to an error 508, is a spike in traffic.
You might have a sudden increase in traffic to your site after starting an advertising campaign. In this case, since this is a situation that you can predict, you should take action beforehand, perhaps switching to a plan with more resources.

The traffic spike, however, can also be unexpected. In that case, you can assess whether it is an isolated event and wait for the traffic to return to normal.
In other circumstances, however, an unusual increase in traffic could be due to a DDoS attack that tries to overwhelm the server with continuous requests.
To prevent such attacks, CloudLinux monitors the number of simultaneous connections (entry process) that occur on the site. If the limit is exceeded, error 508 appears.
Spam in the comments section
Contact forms are often targeted by bots with the goal of automatically sending massive amounts of spam comments.
While the bot is in action, multiple connections are opened, exhausting the available resources. As a result, the limits are exceeded and error 508 is displayed to anyone trying to visit the site.
One of the methods to avoid spam in comments is to use the CAPTCHA code.
Executing processes
There are several processes that can be resource-intensive and cause the error 508. Some common situations are an ongoing site backup process, or while running a cron job.
Similarly, a particularly complex database request can also be responsible for error 508.
If your site has experienced a hacker attack, the massive resource usage could be coming from a malicious script that is running without your knowledge. In this case, the first thing to do is to analyze the access logs to the site.
The entry process limit can also be exceeded if your site is undergoing a brute force attack. This type of attack involves trying to access a site using combinations of username and password to try to find the correct ones.
At SupporHost we use proprietary rules to protect your site from this type of attack. In any case, remember that using long and complex passwords is crucial to keeping your site safe.
Third-party applications
In detail, you should also pay attention to third-party applications and scripts used. An example may be a WordPress plugin or theme that requires more resources than it should.
The best way to avoid such problems is to keep WordPress plugins and themes up to date and avoid using applications that are not updated frequently.
If you want to make sure that the error 508 is caused by a massive resource usage of a plugin you can do a test. First, deactivate all plugins (this applies to themes as well) and check if the error still occurs.

If the error does not appear anymore, you will have to figure out which plugin is causing the problem. To do that, reactivate the plugins one by one and check continuously if error the 508 reappears after you’ve reactivated each plugin.
In case you manage to identify the “culprit” there are three alternatives. First, check if there are any available updates, update the plugin and try to see if the error has been fixed.
If there are no updates available, try to contact the developer. Reporting the error will ensure that other users do not end up in the same situation as you.
In case you can’t solve it, you will have to find an alternative to the plugin (or an extension) you were using.
If you have a WordPress site you can find a plugin that has the same functions by searching in the official directory. For Joomla you can check the extensions directory and for PrestaShop the modules directory.
It’s clear that you certainly care about the performance of your site and you know how important it is to have a fast site, so remember to avoid plugins that slow down WordPress.
Upgrade the plan: when is it necessary?
As we have seen, the first thing you should do is to rule out the possibility that the cause is a resolvable problem.
Among the cases we’ve looked at is an attempted hacker attack, a site targeted by spam, or a plugin that takes too many resources.
You also have to consider possible problems with the code due to adding site features that use resources disproportionately. Exclude the possibility that it is a temporary problem, such as a backend operation: from running a backup to a database query.
If you’ve ruled out all possible causes, it means your site really needs more resources. The most likely scenario is that you’re registering more visitors. If this trend becomes the norm, it means that it’s time to switch to a plan with increased resources.
In case your plan is a shared hosting you can consider switching to a semi-dedicated hosting. Or if the resources of the latter are not enough, you can choose a dedicated solution: a VPS cloud hosting or a dedicated server.
With SupportHost, you can upgrade at any time, without any disruption and only pay the difference.
Conclusion
In this article, 508 error: how to solve it, We’ve seen the possible causes of the error 508, an alert of this type tells you that your site is using more resources than your plan provides. Among the causes we’ve examined there can be a programming error, a plugin that doesn’t work properly or an unauthorized access attempt.
In all these cases by taking action at the source of the problem, the error can be fixed. When the 508 error is caused by the consumption of resources that actually serve your site and it’s not just a temporary traffic spike, all you need to do to resolve it is to switch to a higher level.
Have you ever encountered error 508 on your site? Were you able to identify the cause and fix it? Let me know in the comments below.
The ‘508 – Resource Limit is Reached’ error is one that leaves both website owners and people browsing the web a little bemused. In this article we focus on some tips for a website owner to be able to identify the cause and some practical remedies to this common problem amongst people using shared web hosting.
The history of 508 Errors and why they occur
First off, lets look at the history of where ‘508 – Resource Limit Reached’ errors came about. The 508 error was first ratified as a HTTP code in RFC5842, but known as HTTP Error code ‘508 – Loop Detected’ in 2010. Around the same Cloudlinux was being first released with the goal of being able to provide extra security and stability to shared web hosting servers. One of these technologies they introduced was ‘LVE’ or ‘Lightweight Virtual Environment‘ which is a Linux kernel module based off OpenVZ technology that was designed for the web hosting industry, having the core goal of ensuring that a single website cannot bring down a shared web hosting server.
LVE technology allowed shared web hosting providers to be able to limit the amount of resources that a website could consume on a shared hosting server before blocking the account from being able to use more. Back in the shared hosting days before this was in place, it was a common occurrence that a single website could crash an entire shared web hosting server because it had a sudden influx of traffic. When this happened, it would result in server downtime and effect all of the websites hosted on the server. As one could imagine, this wasn’t really fair to the other clients on the server, it being no direct result of their own actions that they had experienced downtime.
When Cloudlinux was released, the web hosting community adopted this new technology at a very rapid pace as it provided more stability for their infrastructure and a fairer system for their clients. All of a sudden, limits were being imposed on shared web hosting accounts that were not there in the past that would restrict the amount of system memory, CPU and PHP processes that a site could utilize at any given moment in time. Presumably, the closest code that Cloudlinux could find in the IANA HTTP codes that would match LVE detecting that a website was using all of it’s resources was the ‘508’ code that had been recently introduced. This became the code that Cloudlinux would use when resource usage was exceeding the limits imposed by LVE and from 2010 on-wards, shared hosting servers became a lot more stable, albeit at the cost of individual websites with high resource usage.
Establishing which limit is causing your ‘508 Resource Limit is Reached’ error
If you are a web site owner and you have detected that on occasion your site is issuing 508 errors to web site viewers, there are methods to identify what is the cause of the 508 errors you are experiencing. The majority of 508 errors are generated by cPanel based servers that are running Cloudlinux. The 508 error is generated by one of two things occurring on the server.
- Memory usage (your account has exceeded the amount of memory allocated to your cPanel account and there is no available memory allocated to your account for the server to process your request as the memory is in use by other requests on the account)
- Entry processes exceeded (your account has exceeded the amount of entry processes allowed that can be run simultaneously on the account at the time your request was sent to the web server)
Contrary to belief, CPU limitations do not cause 508 errors directly. If the CPU allocation of an account is reached, it will stay at this maximum and slow down other processes running on the server. This can cause the amount of entry processes to go up as requests cannot be fulfilled as quick as they would be without a limit in place, potentially causing the entry processes exceeded trigger of a 508 error.
If you have cPanel access to your shared web hosting account and the server is running Cloudlinux, there should be an option for you to be able to review your resource usage for the account and ascertain the cause of the 508 error you are experiencing. The option you should be looking for within cPanel is the “CPU and Concurrent Connection Usage” icon, under the “Metrics” group of options.
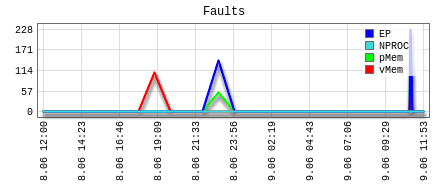
Once you have opened this up you are presenting with information that indicates whether or not your site has hit resource limits within the past 24 hour period and has a link to the ‘details’ of your usage of which will outline the cause of any 508 errors along with the the amount of errors that have occurred during that period of time as well as some additional historical data.
An example of the ‘Faults’ section of these graphs is below (taken from an account that is under-resourced):
As you can see, the website I have taken the above graphic from has had hundreds of 508 errors in the past 24 hour period. Both Entry Processes and Memory usage has been a factor in this site now being able to display to visitors who otherwise would be able to view the content. This will show you which limits have been reached but not necessarily why they were reached in the first place.
Possible Causes of 508 Resource Limits being Reached
There are many potential causes of the 508 error, some of the most common ones are listed below.
Your hosting provider has limits lower than the requirement of your website.
Many hosting providers have low limits so that they can fit many hundreds of hosting accounts on the one server. These limits may be well below the requirements for your website, especially if it is a heavy website (lots of plugins), or running a heavy E-Commerce CMS such as Magento or WordPress / WooCommerce.
The best thing to do in an instance like this would be to find out what limits your web hosting provider has in place (ask them) and perform some concurrency testing to see how many visitors your website can handle simultaneously before the resources are exhausted. If this limit is not high enough then look to either another web host, or another package where you are provided with enough resources to prevent this from happening.
Often it can be the case (if you have a really busy site) that you should not be on shared webhosting at all and that a dedicated solution without limits could be the best thing for your website and your business.
Website traffic spikes
Many times we have seen clients advertise on TV or Radio whilst still being on a shared web hosting package and receive 508 errors. If you are undertaking any activity that will send spikes of traffic to your website you will need to be on a dedicated hosting platform otherwise you may be wasting the valuable exposure that your website should be getting through the advertising you are carrying out.
If you ever are going to get large amounts of web exposure, make sure to be on a platform that can handle this well before the actual spikes occur.
You have rogue processes, back-end jobs or cron jobs that are impacting on your resource usage
Often it could be a backup job, a long query that has been initialised from the back-end of a website or a cron job that carries out high-memory tasks that could be causing your 508 error. Usually the events should coincide with the actions being carried out which makes this a little easier to detect. Especially if you have resource usage errors at the same time that the cron jobs are being carried out or an website administrator is performing tasks in the backend that are causing resources to be consumed.
Web Crawlers, Search Engines or Denial of Service Attacks
Web crawlers or automated scripts that are browsing your website can often be the cause of resource limit depletion. In addition to this, search engines indexing your site at a rapid pace can also cause your resource limits to be exceeded. In addition to this, sometimes malicious entities may be consistently accessing pages on your site that they know will be generating a lot of resource usage in order to Denial of Service your site. Looking through the servers access logs at the time the 508 error is being generated should be able to give you an idea of the activity on the site which has caused the issue and potentially be able to find the IP Addresses that are causing the issue and block them.
Google’s webmaster tools can be used to change the rate in which they index your site if you believe it is Google cause the issue when it is indexing your site. This can be adjusted to a lower rate of requests per second to prevent this from happening.
Poorly scripted plugins or code
Sometimes it can be badly written CMS plugins, theme or custom code that causes 508 errors. Being able to see which processes your account has running often assists in being able to identify files that the site gets stuck on that use up excess CPU or Memory. This is also a major cause of a site being slow when no one else is using the site.
Summary
Unfortunately the 508 limits are an essential part of being able to provide stable web hosting in a shared environment. There are many reasons you may get one and they are the result of your website or web hosting account using more resources than the hosting provider has allocated the account.
If you do receive these on a consistent basis across your site, the most logical thing to do is to move to either a bigger shared hosting package or look at alternatives such as virtual dedicated server hosting in order to ensure that limitations will not cause your site downtime. Sometimes the revenue you are losing as your site is down is far greater than the cost of upgrading to a suitable package for your businesses website.