I’m using Amazon CloudFront to serve content. My users are receiving an HTTP 403 errors with the messages «The request could not be satisfied” or «Access Denied.»
Resolution
The domain name isn’t associated with an alternate domain name (CNAME) on a distribution
If you create a Domain Name System (DNS) but don’t add a CNAME in your CloudFront distribution configuration, then CloudFront returns a 403 error. This occurs even if the CNAME is redirected towards CloudFront at the DNS level.
To use a CNAME instead of the default CloudFront URL, follow the instructions for Adding an alternate domain name.
For more information, see Using custom URLs by adding alternate domain names (CNAMEs).
CloudFront geographic restrictions were configured on the distribution
CloudFront geographic restrictions can prevent users in specific countries from accessing your content. If geographic restrictions cause the error, then the 403 response contains a message similar to: «The Amazon CloudFront distribution is configured to block access from your country.» Also, the response header Server: CloudFront is present. The corresponding CloudFront access log entry contains ClientGeoBlocked as the value for x-edge-detailed-result-type.
For more information, see Restricting the geographic distribution of your content.
AWS WAF is configured on the CloudFront distribution and is blocking the request
If you use AWS WAF to monitor forwarded requests and the requested content doesn’t match the specified conditions, then the content is blocked by WAF. You receive a 403 error. In this case, the error contains a message similar to: «Request blocked. We can’t connect to the server for this app or website at this time.» The Server response header contains CloudFront as the value. The corresponding access log entry has Error as the value for x-edge-detailed-result-type.
The same error message and a response header value of Cloudfront might be present when the reason the request is blocked isn’t AWS WAF. To confirm that the request is blocked by AWS WAF and identify the rule that blocked it, check the AWS WAF logs for the blocked request. Or, check the AWS WAF CloudFront metrics for the relevant WebACL. Then, check the WebACL to see the rules that are blocked. For more information, see Testing and tuning your AWS WAF protections.
An Amazon S3 origin is returning a 403 error
Based on your Amazon Simple Storage Service (Amazon S3) as origin configuration, see the following for troubleshooting:
I’m using an S3 website endpoint as the origin of my CloudFront distribution. Why am I getting 403 Access Denied errors?
I’m using an S3 REST API endpoint as the origin of my CloudFront distribution. Why am I getting 403 Access Denied errors?
A custom origin is returning the 403 error
A 403 error can be returned by an origin due to an application firewall or other reason at the custom origin. If the response contains a Server header without the value CloudFront, then the error might be returned from the custom origin.
To determine if the error is returned from the custom origin, check the origin HTTP access logs.
If you’re not able to check the origin HTTP access logs, use the following troubleshooting methods:
- Check CloudFront access logs. If the time-taken field for the blocked request is significantly lesser than the average of the time-taken field, then the response might not have come from the origin. A low value in the time-taken field indicates that a response was sent from edge location.
- Make the request directly to the origin. If you can replicate the error without going through CloudFront, then the origin might be returning the 403 error.
The error is caused by a signed URL or signed cookies configuration
If you have Restrict viewer access turned on for your CloudFront’s behavior configuration, then requests made without using signed cookies or URL result in a 403 error.
For more information about configuring signed cookies and signed URLs, see Serving private content with signed URLs and signed cookies.
For troubleshooting steps, see How do I troubleshoot issues related to a signed URL or signed cookies in CloudFront?
The distribution with viewer protocol policy not configured for HTTP and HTTPS
If the HTTP request is sent to a distribution with Viewer Protocol Policy setting of HTTPS only, then the request can return a 403 error.
For more information, see Requiring HTTPS for communication between viewers and CloudFront.
When restricting access to S3 content using a bucket policy that inspects the incoming Referer: header, you need to do a little bit of custom configuration to «outsmart» CloudFront.
It’s important to understand that CloudFront is designed to be a well-behaved cache. By «well-behaved,» I mean that CloudFront is designed to never return a response that differs from what the origin server would have returned. I’m sure you can see that is an important factor.
Let’s say I have a web server (not S3) behind CloudFront, and my web site is designed so that it returns different content based on an inspection of the Referer: header… or any other http request header, like User-Agent: for example. Depending on your browser, I might return different content. How would CloudFront know this, so that it would avoid serving a user the wrong version of a certain page?
The answer is, it wouldn’t be able to tell — it can’t know this. So, CloudFront’s solution is not to forward most request headers to my server at all. What my web server can’t see, it can’t react to, so the content I return cannot vary based on headers I don’t receive, which prevents CloudFront from caching and returning the wrong response, based on those headers. Web caches have an obligation to avoid returning the wrong cached content for a given page.
«But wait,» you object. «My site depends on the value from a certain header in order to determine how to respond.» Right, that makes sense… so we have to tell CloudFront this:
Instead of caching my pages based on just the requested path, I need you to also forward the Referer: or User-Agent: or one of several other headers as sent by the browser, and cache the response for use on other requests that include not only the same path, but also the same values for the extra header(s) that you forward to me.
However, when the origin server is S3, CloudFront doesn’t support forwarding most request headers, on the assumption that since static content is unlikely to vary, these headers would just cause it to cache multiple identical responses unnecessarily.
Your solution is not to tell CloudFront that you’re using S3 as the origin. Instead, configure your distribution to use a «custom» origin, and give it the hostname of the bucket to use as the origin server hostname.
Then, you can configure CloudFront to forward the Referer: header to the origin, and your S3 bucket policy that denies/allows requests based on that header will work as expected.
Well, almost as expected. This will lower your cache hit ratio somewhat, since now the cached pages will be cached based on path + referring page. It an S3 object is referenced by more than one of your site’s pages, CloudFront will cache a copy for each unique request. It sounds like a limitation, but really, it’s only an artifact of proper cache behavior — whatever gets forwarded to the back-end, almost all of it, must be used to determine whether that particular response is usable for servicing future requests.
See http://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/distribution-web-values-specify.html#DownloadDistValuesForwardHeaders for configuring CloudFront to whitelist specific headers to send to your origin server.
Important: don’t forward any headers you don’t need, since every variant request reduces your hit rate further. Particularly when using S3 as the back-end for a custom origin, do not forward the Host: header, because that is probably not going to do what you expect. Select the Referer: header here, and test. S3 should begin to see the header and react accordingly.
Note that when you removed your bucket policy for testing, CloudFront would have continued to serve the cached error page unless you flushed your cache by sending an invalidation request, which causes CloudFront to purge all cached pages matching the path pattern you specify, over the course of about 15 minutes. The easiest thing to do when experimenting is to just create a new CloudFront distribution with the new configuration, since there is no charge for the distributions themselves.
When viewing the response headers from CloudFront, note the X-Cache: (hit/miss) and Age: (how long ago this particular page was cached) responses. These are also useful in troubleshooting.
Update: @alexjs has made an important observation: instead of doing this using the bucket policy and forwarding the Referer: header to S3 for analysis — which will hurt your cache ratio to an extent that varies with the spread of resources over referring pages — you can use the new AWS Web Application Firewall service, which allows you to impose filtering rules against incoming requests to CloudFront, to allow or block requests based on string matching in request headers.
For this, you’d need to connect the distribution to S3 as as S3 origin (the normal configuration, contrary to what I proposed, in the solution above, with a «custom» origin) and use the built-in capability of CloudFront to authenticate back-end requests to S3 (so the bucket contents aren’t directly accessible if requested from S3 directly by a malicious actor).
See https://www.alexjs.eu/preventing-hotlinking-using-cloudfront-waf-and-referer-checking/ for more on this option.
- 17/01/202317/01/2023
- 🕑 1 minute read
- 473 Views

Если AWS CloudFront выдает сообщение об ошибке 403 Error — запрос не может быть удовлетворен. Запрос заблокирован, тогда не волнуйтесь. Это можно исправить в кратчайшие сроки.
Здесь, в этом блоге, мы обсудим способ исправления этой ошибки сразу после того, как поговорим о том, что вызвало эту проблему в первую очередь. Давайте начнем!
Что вызывает ошибку 403, запрос не может быть удовлетворен, запрос заблокирован?
Причин возникновения проблемы может быть несколько. Здесь мы упомянули популярные из них:
- Разрешение заблокировано. Если у вас нет необходимых разрешений для доступа к содержимому на сервере, вы можете получить эту ошибку в CloudFront.
- Неправильно настроен сертификат SSL/TLS. Если в вашей раздаче CloudFront есть сертификат SSL/TLS, но он настроен неправильно, вы можете столкнуться с этой проблемой.
- Ошибки конфигурации. Если CloudFront настроен на блокировку запросов с IP-адреса, вы можете получить ошибку 403.
- Имя домена не связано — если запрошенное альтернативное имя домена не связано с раздачей CloudFront, вы можете получить эту ошибку.
- Действие и правило не согласованы — если для действия по умолчанию установлено значение «Разрешить», но сделанный запрос соответствует правилу, для которого установлено значение «Блокировать». Если для действия установлено значение «Блокировать», но для правила установлено значение «Разрешить».
Как я могу исправить запрос об ошибках 403, который не может быть удовлетворен?
1. Измените правила AWS WAF, если для действия по умолчанию установлено значение «Разрешить».
- Войдите в Консоль управления AWS. Перейдите в консоль CloudFront.
- Выберите идентификатор распространения, который вы хотите изменить или обновить.
- Перейдите на вкладку Общие.
- В разделе «Настройки» найдите AWS WAF и выберите список управления веб-доступом, относящийся к дистрибутиву.
- На странице AWS WAF & Shield выберите Web ACL на левой панели. Теперь для региона AWS выберите Global (CloudFront) на странице Web ACL.
- Перейдите к веб-спискам контроля доступа, которые необходимо просмотреть, на правой панели.
- Перейдите на вкладку «Правила» и в разделе «Действие веб-списка управления доступом по умолчанию» для запросов, которые не соответствуют ни одному из заголовков правил, убедитесь, что для параметра «Действие» установлено значение «Разрешить».
- Теперь проверьте, что запрос, который возвращается с ошибкой блокировки запроса, соответствует правилу, в котором действие установлено на блокировку.
- Чтобы это исправить, необходимо проверить, не соответствует ли сделанный запрос условиям для правил AWS WAF, для которых для параметра «Действие» установлено значение « Блокировать». Нажмите на запрос, который был заблокирован, и в разделе Если запрос соответствует заявлению, проверьте его.
- Если допустимые запросы соответствуют предварительным требованиям для правила, которое блокирует запросы, измените правило, чтобы разрешить запросы. Для этого нажмите кнопку «Изменить».
- На следующей странице прокрутите, чтобы найти Действие. Поставьте галочку рядом с Разрешить и нажмите Сохранить.
2. Измените правила AWS WAF, если для действия по умолчанию установлено значение «Блокировать».
- Выполните указанные выше действия (1–6), чтобы перейти на вкладку «Правила» в консоли AWS WAF.
- В разделе «Действие веб-списка управления доступом по умолчанию» для запросов, которые не соответствуют ни одному из правил, если для параметра «Действие» установлено значение «Блокировать», проверьте запрос, чтобы убедиться, что он соответствует условиям для всех правил AWS WAF с параметром «Действие», для которого установлено значение «Разрешить».
- Вы можете создать правило, если допустимый запрос не связан с какими-либо текущими правилами, для которых действие установлено на Разрешить. Для этого нажмите «Добавить правила», затем в раскрывающемся списке выберите «Добавить мои собственные правила и группы правил».
- На следующей странице перейдите в раздел Заявление. В поле «Проверить» выберите «Заголовок».
- Заполните данные для имени поля заголовка, типа соответствия и строки для сопоставления.
- Выберите действие, чтобы разрешить. Нажмите Добавить правило, чтобы подтвердить изменения.
Таким образом, вы можете исправить ошибку 403: запрос не может быть удовлетворен в CloudFront. Выполните все шаги и сообщите нам, сработало ли это для вас, в разделе комментариев ниже.
Related post
Check AWS WAF default action set to Web ACL
by Loredana Harsana
Loredana is a passionate writer with a keen interest in PC software and technology. She started off writing about mobile phones back when Samsung Galaxy S II was… read more
Updated on January 17, 2023
Reviewed by
Alex Serban
After moving away from the corporate work-style, Alex has found rewards in a lifestyle of constant analysis, team coordination and pestering his colleagues. Holding an MCSA Windows Server… read more
- If CloudFront distribution is set to allow HTTPS requests, but the request has originated over HTTP.
- To fix this, you must check AWS WAF rules to ensure everything is set in action.
XINSTALL BY CLICKING THE DOWNLOAD FILE
This software will repair common computer errors, protect you from file loss, malware, hardware failure and optimize your PC for maximum performance. Fix PC issues and remove viruses now in 3 easy steps:
- Download Restoro PC Repair Tool that comes with Patented Technologies (patent available here).
- Click Start Scan to find Windows issues that could be causing PC problems.
- Click Repair All to fix issues affecting your computer’s security and performance
- Restoro has been downloaded by 0 readers this month.
If AWS CloudFront is coming up with the error message 403 Error – The request could not be satisfied. Request Blocked, then don’t worry. It can be fixed in no time.
Here, in this blog, we will discuss a way to fix this error right after talking about what caused this issue in the first place. Let’s get started!
What causes the 403 error the request could not be satisfied request blocked?
There could be a handful of reasons for the issue to occur. Here we have mentioned the popular ones:
- Permission blocked – If you don’t have the necessary permissions to access the content on the server, then you may get this error on CloudFront.
- SSL/TLS certificate misconfigured – If your CloudFront distribution has SSL/TLS certificate and it is not configured correctly, then you can encounter this issue.
- Configuration errors – If CloudFront is configured to block requests from an IP address, you might get a 403 error.
- Domain name not associated – If the requested alternate domain name is not related to CloudFront distribution, you might get this error.
- Action and Rule are not aligned – If the default action is set to Allow, but the request made matches to a rule which is set to Block. If the action is set to Block, but the rule is set to Allow.
How can I fix the 403 errors request could not be satisfied?
1. Modify the AWS WAF Rules if the default action is set to Allow
- Login to AWS Management Console. Go to the CloudFront console.
- Select the distribution ID that you want to modify or update.
- Switch to the General tab.
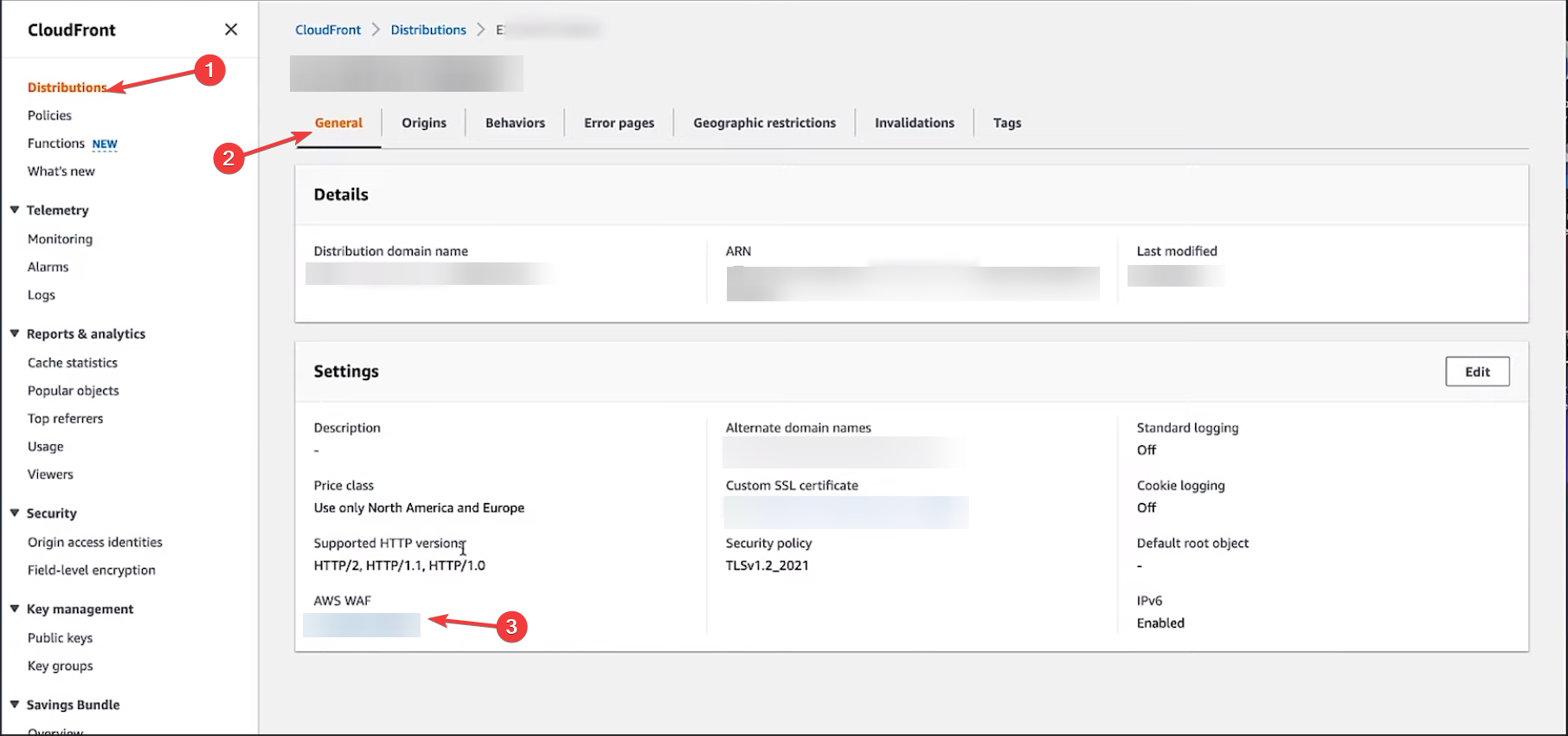
- Under Settings, locate the AWS WAF and select the web access control list related to the distribution.
- On the AWS WAF & Shield page, select Web ACLs from the left pane. Now, for AWS Region, choose Global (CloudFront) on the Web ACLs page.
- Go to the Web ACLs you need to review from the right pane.
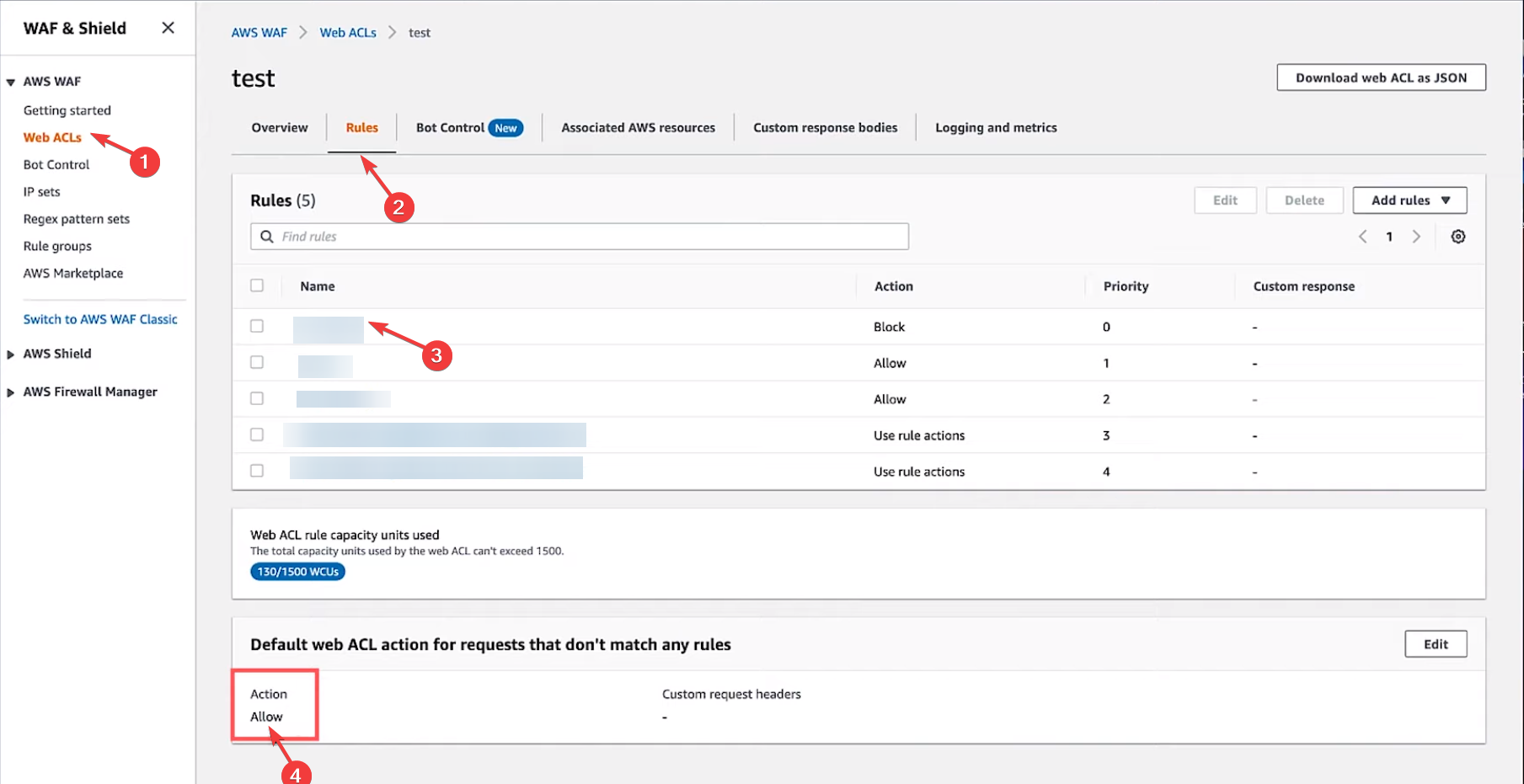
- Switch to the Rules tab, and under Default web ACL action for requests that don’t match any rules header, make sure Action is set to Allow.
- Now check the request which returns with a request blocked error matches a rule that has set Action to Block.
- To fix this, you need to check the request made doesn’t match the conditions for AWS WAF rules that have Action set to Block. Click on the request that was blocked, and under If the request matches the statement, check for the same.
- If valid requests match the prerequisites for a rule that blocks requests, then edit the rule to allow the requests. To do that, click the Edit option.
- On the next page, scroll to find Action. Place a checkmark next to Allow and click Save.
- Event ID 1008: How to Fix It on Windows 10 & 11
- Easy Ways to Bypass Admin Password on Windows 10
- Fix: Your Response to the CAPTCHA Appears to be Invalid
2. Modify the AWS WAF Rules if the default action is set to Block
- Follow the steps mentioned above (1-6) to navigate to the Rules tab on the AWS WAF console.
- Under Default web ACL action for requests that don’t match any rules option, if the Action is set to Block, then check the request to ensure that it matches conditions for all the AWS WAF rules with Action set to Allow.
- You can create a rule if the valid request is not related to any current rules that have Action set to Allow. To do that, click on Add rules, then from the drop-down, select Add my own rules and rule groups.
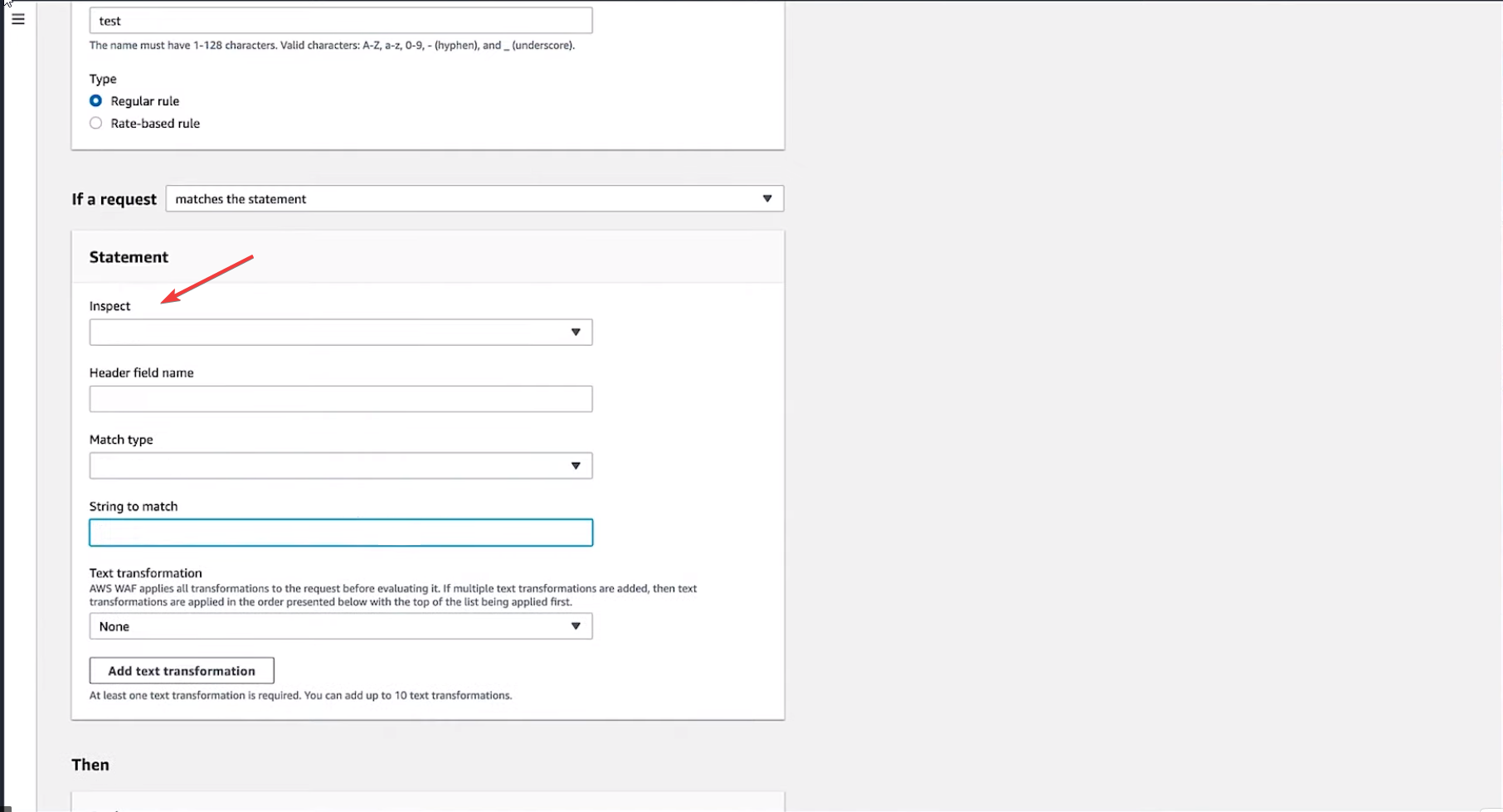
- On the next page, go to the Statement section. For the Inspect field, choose Header.
- Fill in the details for the Header field name, Match type, and String to match.
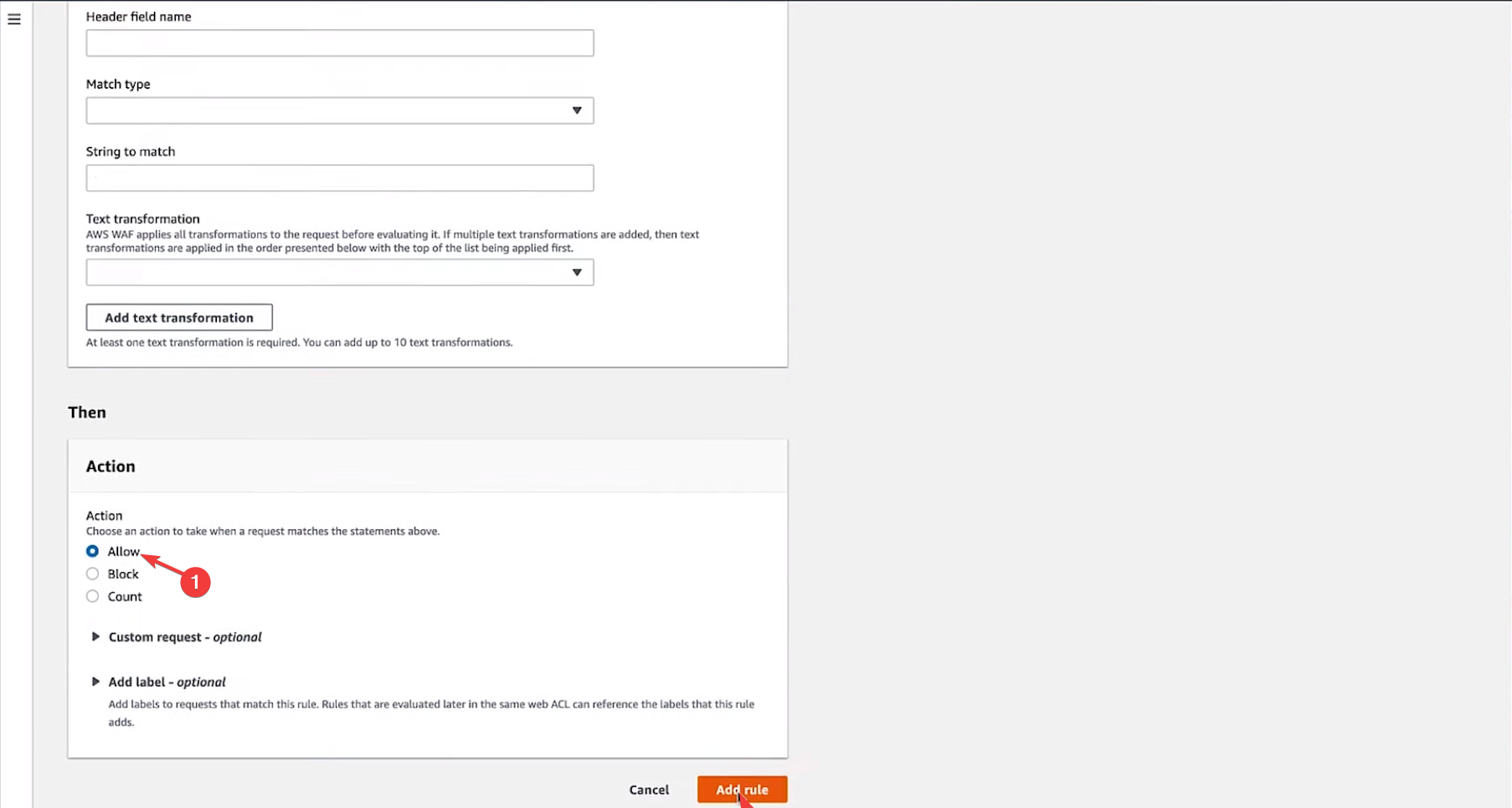
- Choose Action to Allow. Click Add rule to confirm the changes.
So, in this way, you can fix the 403 error the request could not be satisfied error on CloudFront. Follow all the steps and let us know if it worked for you in the comments section below.
Still having issues? Fix them with this tool:
SPONSORED
If the advices above haven’t solved your issue, your PC may experience deeper Windows problems. We recommend downloading this PC Repair tool (rated Great on TrustPilot.com) to easily address them. After installation, simply click the Start Scan button and then press on Repair All.
I’m using Amazon CloudFront to serve content. My users are receiving an HTTP 403 errors with the messages «The request could not be satisfied” or «Access Denied.»
Resolution
The domain name isn’t associated with an alternate domain name (CNAME) on a distribution
If you create a Domain Name System (DNS) but don’t add a CNAME in your CloudFront distribution configuration, then CloudFront returns a 403 error. This occurs even if the CNAME is redirected towards CloudFront at the DNS level.
To use a CNAME instead of the default CloudFront URL, follow the instructions for Adding an alternate domain name.
For more information, see Using custom URLs by adding alternate domain names (CNAMEs).
CloudFront geographic restrictions were configured on the distribution
CloudFront geographic restrictions can prevent users in specific countries from accessing your content. If geographic restrictions cause the error, then the 403 response contains a message similar to: «The Amazon CloudFront distribution is configured to block access from your country.» Also, the response header Server: CloudFront is present. The corresponding CloudFront access log entry contains ClientGeoBlocked as the value for x-edge-detailed-result-type.
For more information, see Restricting the geographic distribution of your content.
AWS WAF is configured on the CloudFront distribution and is blocking the request
If you use AWS WAF to monitor forwarded requests and the requested content doesn’t match the specified conditions, then the content is blocked by WAF. You receive a 403 error. In this case, the error contains a message similar to: «Request blocked. We can’t connect to the server for this app or website at this time.» The Server response header contains CloudFront as the value. The corresponding access log entry has Error as the value for x-edge-detailed-result-type.
The same error message and a response header value of Cloudfront might be present when the reason the request is blocked isn’t AWS WAF. To confirm that the request is blocked by AWS WAF and identify the rule that blocked it, check the AWS WAF logs for the blocked request. Or, check the AWS WAF CloudFront metrics for the relevant WebACL. Then, check the WebACL to see the rules that are blocked. For more information, see Testing and tuning your AWS WAF protections.
An Amazon S3 origin is returning a 403 error
Based on your Amazon Simple Storage Service (Amazon S3) as origin configuration, see the following for troubleshooting:
I’m using an S3 website endpoint as the origin of my CloudFront distribution. Why am I getting 403 Access Denied errors?
I’m using an S3 REST API endpoint as the origin of my CloudFront distribution. Why am I getting 403 Access Denied errors?
A custom origin is returning the 403 error
A 403 error can be returned by an origin due to an application firewall or other reason at the custom origin. If the response contains a Server header without the value CloudFront, then the error might be returned from the custom origin.
To determine if the error is returned from the custom origin, check the origin HTTP access logs.
If you’re not able to check the origin HTTP access logs, use the following troubleshooting methods:
- Check CloudFront access logs. If the time-taken field for the blocked request is significantly lesser than the average of the time-taken field, then the response might not have come from the origin. A low value in the time-taken field indicates that a response was sent from edge location.
- Make the request directly to the origin. If you can replicate the error without going through CloudFront, then the origin might be returning the 403 error.
The error is caused by a signed URL or signed cookies configuration
If you have Restrict viewer access turned on for your CloudFront’s behavior configuration, then requests made without using signed cookies or URL result in a 403 error.
For more information about configuring signed cookies and signed URLs, see Serving private content with signed URLs and signed cookies.
For troubleshooting steps, see How do I troubleshoot issues related to a signed URL or signed cookies in CloudFront?
The distribution with viewer protocol policy not configured for HTTP and HTTPS
If the HTTP request is sent to a distribution with Viewer Protocol Policy setting of HTTPS only, then the request can return a 403 error.
For more information, see Requiring HTTPS for communication between viewers and CloudFront.
Something is causing your files to be requested from CloudFront before they are present in the bucket. The default configuration of CloudFront causes this to be negatively-cached for up to 5 minutes.
By default, when your origin returns an HTTP 4xx or 5xx status code, CloudFront caches these error responses for five minutes and then submits the next request for the object to your origin to see whether the problem that caused the error has been resolved and the requested object is now available.
— http://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/custom-error-pages.html
If the browser, or anything else, tries to download the file from that particular CloudFront edge (or any edge, if the request happens to also go through the regional edge — CloudFront now has two edge layers) before the upload into S3 is complete, S3 will return an error, and CloudFront — at that edge location — will cache that error and remember, for the next 5 minutes, not to bother trying again.
This timer is configurable.
You can specify the error-caching duration—the Error Caching Minimum TTL—for each 4xx and 5xx status code that CloudFront caches. For a procedure, see Configuring Error Response Behavior.
— http://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/custom-error-pages.html
Set the value to 0 for any error codes, like 403, where you want to disable the error cache.
The content in this answer is adapted from my original post on Stack Overflow.
I have a website with a single quote, which I am not able to browse, and few with the same character on same domain it’s getting redirected and I am able opens the URL.
l’Union-Européenne-Dans-l’Europe/xxxxx.html when removed the single quotes from url I am able to browse.
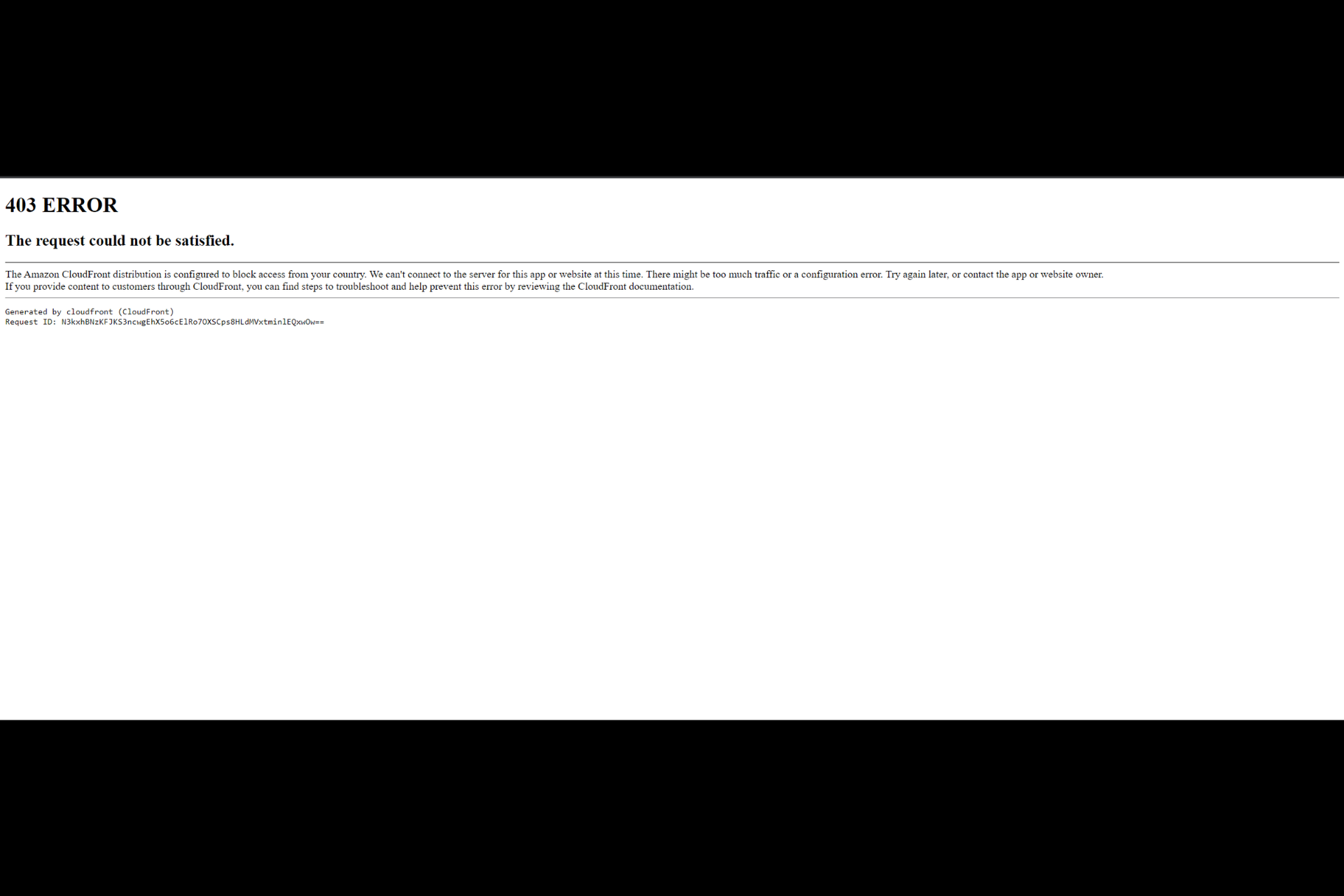
Result when tried to browse: 403 ERROR
The request could not be satisfied.
Request blocked. We can’t connect to the server for this app or website at this time. There might be too much traffic or a configuration error. Try again later, or contact the app or website owner.
If you provide content to customers through CloudFront, you can find steps to troubleshoot and help prevent this error by reviewing the CloudFront documentation.
Generated by cloudfront (CloudFront)
Request ID:
Note: checked on clodfront access logs I could find the log with error code 403, not much information other than URI results /l%27Union-Europ%25C3%25A9enne-Dans-l%27Europe/xxxxx.html
asked Jun 5, 2020 at 13:34
1
Check your CloudFront configuration. This will occur because of below reasons:
- The request is initiated over HTTP, but the CloudFront distribution is configured to only allow HTTPS requests.
- The requested alternate domain name (CNAME) isn’t associated with the CloudFront distribution.
You can refer this link also to resolve your issue: https://aws.amazon.com/premiumsupport/knowledge-center/resolve-cloudfront-bad-request-error/
Jeremy Caney
7,00661 gold badges48 silver badges76 bronze badges
answered Jun 5, 2020 at 16:57
6
Posting my solution here because this was an arduous, weekend-long issue for me, and the solution was not that obvious. As Mani Ezhumalai’s answer mentioned, the issue was alternate CNAME records needed.
In my case, it was www.example.com vs example.com. CloudFront requires both domains to be covered in the alternative domain names list, which requires a single AWS ACM SSL cert to cover both, as well as the appropriate CNAME records configured in the DNS.
answered Nov 14, 2021 at 22:17
NathanaelNathanael
9642 gold badges19 silver badges39 bronze badges
I had the same issue. It was WAF / Firewall which rejected the request. Try to disable that to verify.
answered Dec 23, 2021 at 13:38
guyrombguyromb
7638 silver badges15 bronze badges
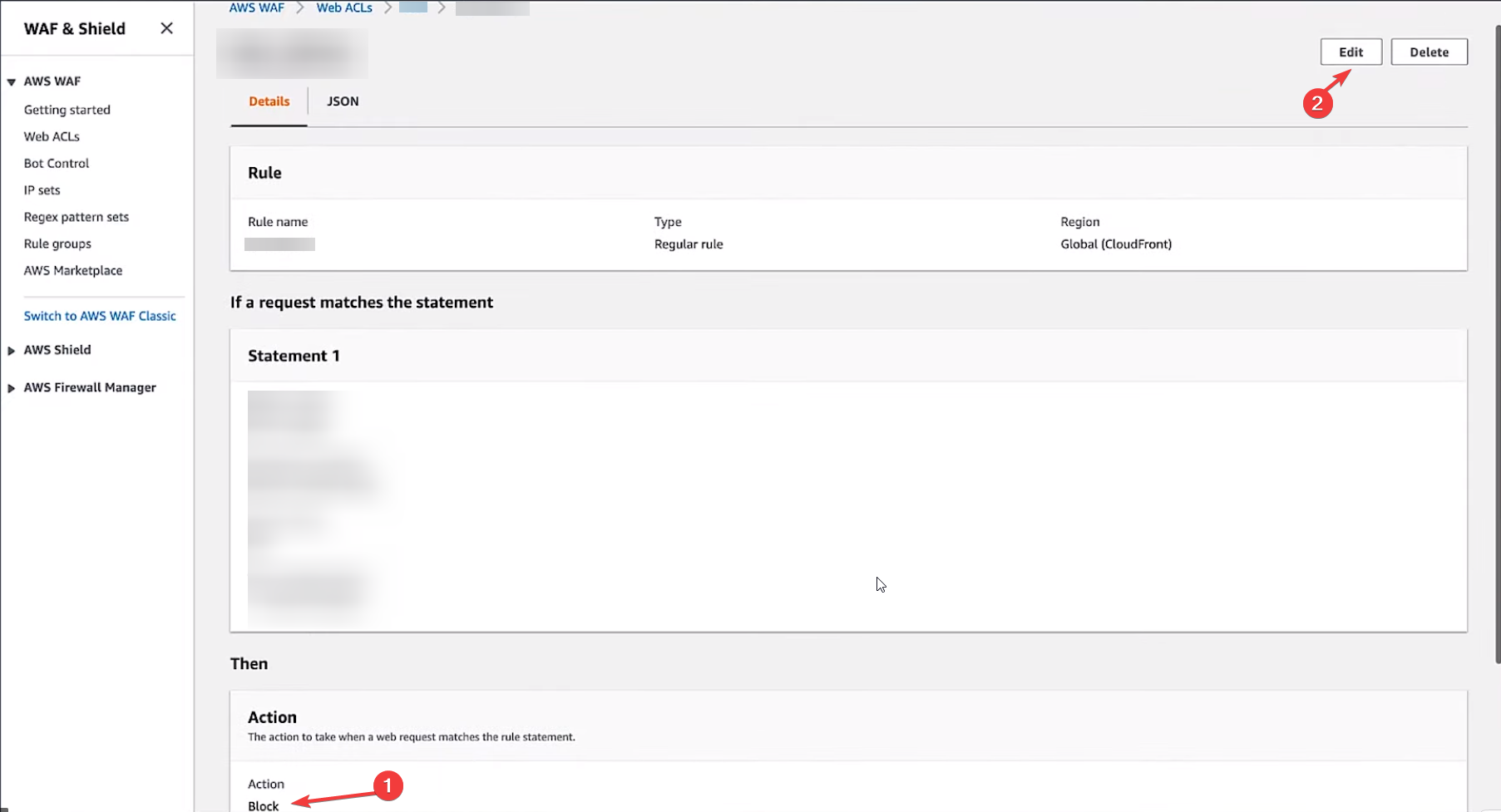
WAF rules are blocking the request
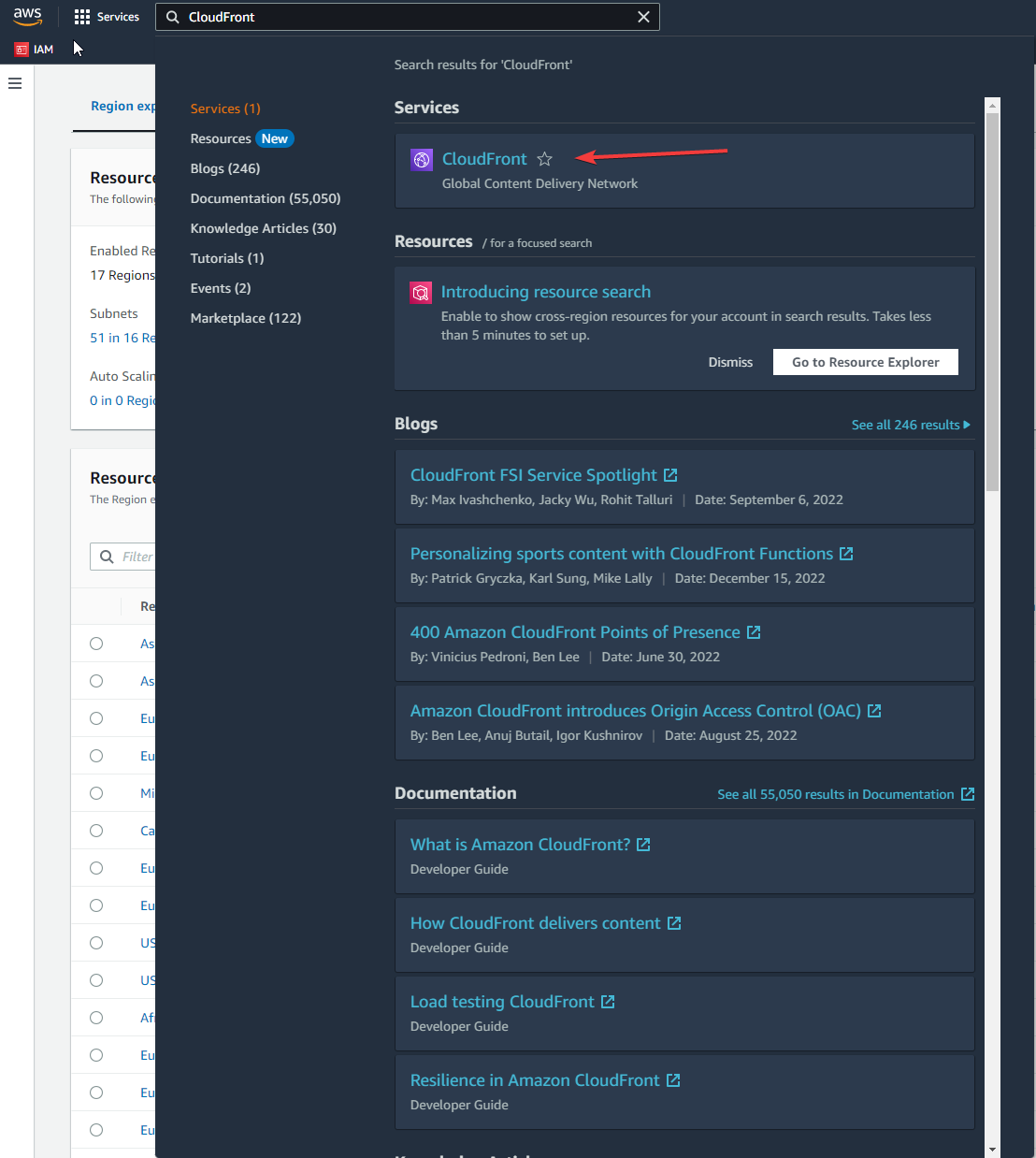
You could navigate to AWS WAF > Web ACLs > yourWebACL and search for block under Sampled requests
Optionally navigate from cloudfront settings
ref this image
Then check in the sample request as given in the below pic
Read more about this modification at https://aws.amazon.com/premiumsupport/knowledge-center/cloudfront-error-request-blocked/?nc1=h_ls
Please don’t disable WAF as is, but either the rule, which prevents this URL from count instead of the default action (in your case the default action seems to be blocked).
- To modify the rule, navigate to AWS WAF > Web ACLs > rule > Edit rule
- and then toggle the control for specific rule under rules
answered Oct 17, 2022 at 6:27
Nafsin VkNafsin Vk
4894 silver badges9 bronze badges