Аннотация
В этой статье описано исправление, которое позволяет вести новую функциональность ведения журнала при возникновении ошибок DCOM в приложениях Microsoft COM+. Кроме того, здесь кратко рассматриваются ошибки DCOM, причины ошибок DCOM и способы устранения ошибок DCOM.
Проблемы
При возникновении ошибки DCOM сообщение об ошибке не содержит достаточных сведений для определения причины ошибки DCOM. Вместо этого в средстве просмотра событий может появиться сообщение об ошибке, подобное приведенному ниже.
Тип события: источник события ошибки: код события DCOM: 10009 описание: не удалось установить связь DCOM с компьютером с помощью любого из настроенных протоколов.
Примечание. В сообщении об ошибке ComputerName — это заполнитель для имени недоступного компьютера. В журнале ошибок отсутствуют другие сведения. Чтобы найти дополнительные сведения об обнаруженной ошибке, необходимо как правило выполнить отладку приложения или проанализировать сетевой трафик.
Решение
Исправление для этой проблемы теперь доступно в Microsoft. После применения этого исправления DCOM будет записывать в журнал событий расширенные сведения об ошибках, которые помогут определить причину ошибки DCOM.
Сведения о пакете обновления
Чтобы устранить эту проблему, установите последнюю версию пакета обновления для Windows Server 2003. Чтобы получить дополнительные сведения, щелкните следующий номер статьи базы знаний Майкрософт:
889100 Как получить последний пакет обновления для Windows Server 2003
Сведения о пакете исправлений
Эта проблема устранена в пакете исправлений 7 (SP1) для Microsoft Windows Server 2003, выпущенных после пакета обновления 1,5 1 (SP3). Дополнительные сведения см. в следующей статье базы знаний Майкрософт:
910730 Пакет исправлений 7 (SP1) для Windows Server 2003, выпущенных после пакета обновления 1,5 1
Сведения об исправлении
Предварительные условия
Чтобы применить это исправление, необходимо установить Windows Server 2003.
Требование перезагрузки
Чтобы включить это исправление, необходимо перезагрузить компьютер после внесения изменений в реестр.
Сведения о замене исправлений
Это исправление не заменяет других исправлений.
Сведения о внесении изменений в реестр
Чтобы включить это исправление, необходимо внести изменения в реестр. Важно! В этом разделе, о методе или задаче содержатся инструкции по изменению реестра. Однако в случае неправильного изменения реестра могут возникнуть серьезные проблемы. Таким образом, убедитесь, что вы должны выполнить эти действия осторожно. Для дополнительной защиты создавайте резервную копию реестра перед ее изменением. После этого вы можете восстановить реестр в случае возникновения проблемы. Для получения дополнительных сведений о том, как создать резервную копию и восстановить реестр, щелкните следующий номер статьи базы знаний Майкрософт:
322756 Как создать резервную копию и восстановить реестр в WindowsЧтобы включить это исправление, выполните указанные ниже действия.
-
Нажмите кнопку Пуск, выберите выполнить, введите regeditи нажмите кнопкуОК.
-
Найдите и выберите следующий раздел реестра:
HKEY_LOCAL_MACHINESoftwareMicrosoftOle
-
В меню Правка выберите команду Добавить параметр, а затем добавьте следующий параметр реестра.
Имя значения
Тип данных
Значение
Примечания.
EnableEELogging
REG_DWORD
1
Этот параметр реестра включает или выключает ведение журнала в текстовом формате. Этот формат подходит для анализа журналов вручную.
LogEEInfoAsNative
REG_DWORD
1
Этот параметр реестра включает или выключает ведение журнала в средстве просмотра событий. Если вы включаете ведение журнала такого типа, вы можете использовать автоматический анализ для проверки расширенных сведений об ошибках.
-
Закройте редактор реестра.
Английская версия исправления содержит файлы с атрибутами, указанными в следующей таблице, или более поздние. Даты и время для файлов указаны в формате времени UTC. При просмотре сведений о файлах выполняется перевод соответствующих значений в местное время. Чтобы узнать разницу между временем UTC и местным временем, откройте вкладку Часовой пояс элемента «Дата и время» панели управления.
Сведения о файлах
Windows Server 2003, Архитектура Itanium
|
Имя файла |
Версия файла |
Размер |
дата |
Время |
Платформа |
Направление поддержки |
|---|---|---|---|---|---|---|
|
Catsrv.dll |
2001.12.4720.445 |
622 080 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Catsrvut.dll |
2001.12.4720.445 |
1 555 456 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Clbcatex.dll |
2001.12.4720.445 |
263 680 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Clbcatq.dll |
2001.12.4720.445 |
1 287 168 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Colbact.dll |
2001.12.4720.445 |
171 008 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Comadmin.dll |
2001.12.4720.445 |
411 136 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Comrepl.dll |
2001.12.4720.445 |
275 456 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Comsvcs.dll |
2001.12.4720.445 |
3 143 168 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Comuid.dll |
2001.12.4720.445 |
1 873 408 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Es.dll |
2001.12.4720.445 |
654 336 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Msdtcprx.dll |
2001.12.4720.445 |
1 311 744 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Msdtctm.dll |
2001.12.4720.445 |
3 152 384 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Msdtcuiu.dll |
2001.12.4720.445 |
463 360 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Mtxclu.dll |
2001.12.4720.445 |
203 776 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Mtxdm.dll |
2001.12.4720.445 |
45 568 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Mtxoci.dll |
2001.12.4720.445 |
320 000 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Ole32.dll |
5.2.3790.445 |
3 582 976 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Olecli32.dll |
5.2.3790.445 |
223 744 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Olecnv32.dll |
5.2.3790.445 |
89 088 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Rpcproxy.dll |
5.2.3790.141 |
73 216 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Rpcrt4.dll |
5.2.3790.141 |
2 150 400 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Rpcss.dll |
5.2.3790.445 |
694 272 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Stclient.dll |
2001.12.4720.445 |
140 800 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Txflog.dll |
2001.12.4720.445 |
280 064 |
17-Nov-2005 |
02:45 |
IA-64 |
Not Applicable |
|
Wcatsrv.dll |
2001.12.4720.445 |
258,560 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wcatsrvut.dll |
2001.12.4720.445 |
584 192 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wclbcatex.dll |
2001.12.4720.445 |
98 304 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wclbcatq.dll |
2001.12.4720.445 |
490 496 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wcolbact.dll |
2001.12.4720.445 |
56 832 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wcomadmin.dll |
2001.12.4720.445 |
189 440 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wcomsvcs.dll |
2001.12.4720.445 |
1 209 344 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wes.dll |
2001.12.4720.445 |
226 816 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wmsdtcprx.dll |
2001.12.4720.445 |
445 952 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wmsdtcuiu.dll |
2001.12.4720.445 |
160 768 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wmtxclu.dll |
2001.12.4720.445 |
76,288 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wmtxdm.dll |
2001.12.4720.445 |
18 944 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wmtxoci.dll |
2001.12.4720.445 |
109 056 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wole32.dll |
5.2.3790.445 |
1 193 984 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wolecli32.dll |
5.2.3790.445 |
72 192 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wolecnv32.dll |
5.2.3790.445 |
36 352 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wrpcproxy.dll |
5.2.3790.141 |
26 112 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wrpcrt4.dll |
5.2.3790.141 |
544 256 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wstclient.dll |
2001.12.4720.445 |
60 416 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
|
Wtxflog.dll |
2001.12.4720.445 |
95 232 |
17-Nov-2005 |
02:45 |
x86 |
WOW |
Windows Server 2003 с пакетом обновления 1 (SP1), Архитектура Itanium
|
Имя файла |
Версия файла |
Размер |
дата |
Время |
Платформа |
Необходимый пакет обновления |
Ветвь обслуживания |
|---|---|---|---|---|---|---|---|
|
Catsrv.dll |
2001.12.4720.2572 |
657 408 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Catsrvut.dll |
2001.12.4720.2572 |
1 632 256 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Clbcatex.dll |
2001.12.4720.2572 |
279 040 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Clbcatq.dll |
2001.12.4720.2572 |
1 353 728 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Colbact.dll |
2001.12.4720.2572 |
181 760 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Comadmin.dll |
2001.12.4720.2572 |
420 352 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Comrepl.dll |
2001.12.4720.2572 |
285 184 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Comsvcs.dll |
2001.12.4720.2572 |
3 366 912 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Comuid.dll |
2001.12.4720.2572 |
1 977 856 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Es.dll |
2001.12.4720.2572 |
701 440 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Msdtcprx.dll |
2001.12.4720.2572 |
1 337 344 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Msdtctm.dll |
2001.12.4720.2572 |
3 096 064 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Msdtcuiu.dll |
2001.12.4720.2572 |
486 400 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Mtxclu.dll |
2001.12.4720.2572 |
207,872 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Mtxdm.dll |
2001.12.4720.2572 |
47 616 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Mtxoci.dll |
2001.12.4720.2572 |
322 048 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Ole32.dll |
5.2.3790.2572 |
3 999 744 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Olecli32.dll |
5.2.3790.2572 |
252 416 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Olecnv32.dll |
5.2.3790.2572 |
90 112 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Rpcss.dll |
5.2.3790.2572 |
859 136 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Stclient.dll |
2001.12.4720.2572 |
149 504 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Txflog.dll |
2001.12.4720.2572 |
301 568 |
17-Nov-2005 |
02:45 |
IA-64 |
SP1 |
Not Applicable |
|
Wcatsrv.dll |
2001.12.4720.2572 |
273 920 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcatsrvut.dll |
2001.12.4720.2572 |
619 520 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wclbcatex.dll |
2001.12.4720.2572 |
104 960 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wclbcatq.dll |
2001.12.4720.2572 |
514 048 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcolbact.dll |
2001.12.4720.2572 |
58 880 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcomadmin.dll |
2001.12.4720.2572 |
196 608 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcomsvcs.dll |
2001.12.4720.2572 |
1 268 736 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcomuid.dll |
2001.12.4720.2572 |
596,480 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wes.dll |
2001.12.4720.2572 |
238 592 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmsdtcprx.dll |
2001.12.4720.2572 |
470 528 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmsdtcuiu.dll |
2001.12.4720.2572 |
165 888 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmtxclu.dll |
2001.12.4720.2572 |
78 848 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmtxdm.dll |
2001.12.4720.2572 |
20 992 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmtxoci.dll |
2001.12.4720.2572 |
111 104 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wole32.dll |
5.2.3790.2572 |
1 247 232 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wolecli32.dll |
5.2.3790.2572 |
75,776 |
17-Nov-2005 |
02:45 |
Not Applicable |
SP1 |
WOW |
|
Wolecnv32.dll |
5.2.3790.2572 |
38 912 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wstclient.dll |
2001.12.4720.2572 |
64 000 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wtxflog.dll |
2001.12.4720.2572 |
98,816 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
Windows Server 2003 SP1, x64
|
Имя файла |
Версия файла |
Размер |
дата |
Время |
Платформа |
Необходимый пакет обновления |
Ветвь обслуживания |
|---|---|---|---|---|---|---|---|
|
Catsrv.dll |
2001.12.4720.2572 |
418 304 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Catsrvut.dll |
2001.12.4720.2572 |
1 083 904 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Clbcatex.dll |
2001.12.4720.2572 |
175 104 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Clbcatq.dll |
2001.12.4720.2572 |
882 688 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Colbact.dll |
2001.12.4720.2572 |
97 280 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Comadmin.dll |
2001.12.4720.2572 |
288 768 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Comrepl.dll |
2001.12.4720.2572 |
188 928 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Comsvcs.dll |
2001.12.4720.2572 |
2 194 944 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Comuid.dll |
2001.12.4720.2572 |
1 478 144 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Es.dll |
2001.12.4720.2572 |
365 568 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Msdtcprx.dll |
2001.12.4720.2572 |
830 464 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Msdtctm.dll |
2001.12.4720.2572 |
2 073 088 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Msdtcuiu.dll |
2001.12.4720.2572 |
291 328 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Mtxclu.dll |
2001.12.4720.2572 |
144 896 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Mtxdm.dll |
2001.12.4720.2572 |
30 208 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Mtxoci.dll |
2001.12.4720.2572 |
175 104 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Ole32.dll |
5.2.3790.2572 |
2 546 688 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Olecli32.dll |
5.2.3790.2572 |
131 584 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Olecnv32.dll |
5.2.3790.2572 |
56 832 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Rpcss.dll |
5.2.3790.2572 |
698 368 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Stclient.dll |
2001.12.4720.2572 |
101 888 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Txflog.dll |
2001.12.4720.2572 |
180 224 |
17-Nov-2005 |
02:45 |
x64 |
SP1 |
Not Applicable |
|
Wcatsrv.dll |
2001.12.4720.2572 |
273 920 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcatsrvut.dll |
2001.12.4720.2572 |
619 520 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wclbcatex.dll |
2001.12.4720.2572 |
104 960 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wclbcatq.dll |
2001.12.4720.2572 |
514 048 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcolbact.dll |
2001.12.4720.2572 |
58 880 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcomadmin.dll |
2001.12.4720.2572 |
196 608 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcomsvcs.dll |
2001.12.4720.2572 |
1 268 736 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wcomuid.dll |
2001.12.4720.2572 |
596,480 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wes.dll |
2001.12.4720.2572 |
238 592 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmsdtcprx.dll |
2001.12.4720.2572 |
470 528 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmsdtcuiu.dll |
2001.12.4720.2572 |
165 888 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmtxclu.dll |
2001.12.4720.2572 |
78 848 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmtxdm.dll |
2001.12.4720.2572 |
20 992 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wmtxoci.dll |
2001.12.4720.2572 |
111 104 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wole32.dll |
5.2.3790.2572 |
1 247 232 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wolecli32.dll |
5.2.3790.2572 |
75,776 |
17-Nov-2005 |
02:45 |
Not Applicable |
SP1 |
WOW |
|
Wolecnv32.dll |
5.2.3790.2572 |
38 912 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wstclient.dll |
2001.12.4720.2572 |
64 000 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
|
Wtxflog.dll |
2001.12.4720.2572 |
98,816 |
17-Nov-2005 |
02:45 |
x86 |
SP1 |
WOW |
Windows Server 2003, x86
|
Имя файла |
Версия файла |
Размер |
дата |
Время |
|---|---|---|---|---|
|
Catsrv.dll |
2001.12.4720.445 |
258,560 |
17-Nov-2005 |
03:09 |
|
Catsrvut.dll |
2001.12.4720.445 |
584 192 |
17-Nov-2005 |
03:09 |
|
Clbcatex.dll |
2001.12.4720.445 |
98 304 |
17-Nov-2005 |
03:09 |
|
Clbcatq.dll |
2001.12.4720.445 |
490 496 |
17-Nov-2005 |
03:09 |
|
Colbact.dll |
2001.12.4720.445 |
56 832 |
17-Nov-2005 |
03:09 |
|
Comadmin.dll |
2001.12.4720.445 |
189 440 |
17-Nov-2005 |
03:09 |
|
Comrepl.dll |
2001.12.4720.445 |
86 528 |
17-Nov-2005 |
03:09 |
|
Comsvcs.dll |
2001.12.4720.445 |
1 209 344 |
17-Nov-2005 |
03:09 |
|
Comuid.dll |
2001.12.4720.445 |
565 248 |
17-Nov-2005 |
03:09 |
|
Es.dll |
2001.12.4720.445 |
226 816 |
17-Nov-2005 |
03:09 |
|
Msdtcprx.dll |
2001.12.4720.445 |
445 952 |
17-Nov-2005 |
03:09 |
|
Msdtctm.dll |
2001.12.4720.445 |
965 120 |
17-Nov-2005 |
03:09 |
|
Msdtcuiu.dll |
2001.12.4720.445 |
160 768 |
17-Nov-2005 |
03:09 |
|
Mtxclu.dll |
2001.12.4720.445 |
76,288 |
17-Nov-2005 |
03:09 |
|
Mtxdm.dll |
2001.12.4720.445 |
18 944 |
17-Nov-2005 |
03:09 |
|
Mtxoci.dll |
2001.12.4720.445 |
109 056 |
17-Nov-2005 |
03:09 |
|
Ole32.dll |
5.2.3790.445 |
1 193 984 |
17-Nov-2005 |
03:09 |
|
Olecli32.dll |
5.2.3790.445 |
72 192 |
17-Nov-2005 |
03:09 |
|
Olecnv32.dll |
5.2.3790.445 |
36 352 |
17-Nov-2005 |
03:09 |
|
Rpcproxy.dll |
5.2.3790.141 |
26 112 |
16-Mar-2004 |
03:17 |
|
Rpcrt4.dll |
5.2.3790.141 |
659 968 |
16-Mar-2004 |
03:17 |
|
Rpcss.dll |
5.2.3790.445 |
296,960 |
17-Nov-2005 |
03:09 |
|
Stclient.dll |
2001.12.4720.445 |
60 416 |
17-Nov-2005 |
03:09 |
|
Txflog.dll |
2001.12.4720.445 |
95 232 |
17-Nov-2005 |
03:09 |
Windows Server 2003 SP1, x86
|
Имя файла |
Версия файла |
Размер |
дата |
Время |
Платформа |
Необходимый пакет обновления |
|---|---|---|---|---|---|---|
|
Catsrv.dll |
2001.12.4720.2572 |
273 920 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Catsrvut.dll |
2001.12.4720.2572 |
619 520 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Clbcatex.dll |
2001.12.4720.2572 |
104 960 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Clbcatq.dll |
2001.12.4720.2572 |
514 048 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Colbact.dll |
2001.12.4720.2572 |
58 880 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Comadmin.dll |
2001.12.4720.2572 |
196 608 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Comrepl.dll |
2001.12.4720.2572 |
88 576 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Comsvcs.dll |
2001.12.4720.2572 |
1 268 736 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Comuid.dll |
2001.12.4720.2572 |
596,480 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Es.dll |
2001.12.4720.2572 |
238 592 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Msdtcprx.dll |
2001.12.4720.2572 |
470 528 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Msdtctm.dll |
2001.12.4720.2572 |
1 009 664 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Msdtcuiu.dll |
2001.12.4720.2572 |
165 888 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Mtxclu.dll |
2001.12.4720.2572 |
78 848 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Mtxdm.dll |
2001.12.4720.2572 |
20 992 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Mtxoci.dll |
2001.12.4720.2572 |
111 104 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Ole32.dll |
5.2.3790.2572 |
1 247 232 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Olecli32.dll |
5.2.3790.2572 |
75,776 |
17-Nov-2005 |
03:20 |
Not Applicable |
SP1 |
|
Olecnv32.dll |
5.2.3790.2572 |
38 912 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Rpcss.dll |
5.2.3790.2572 |
421 888 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Stclient.dll |
2001.12.4720.2572 |
64 000 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
|
Txflog.dll |
2001.12.4720.2572 |
98,816 |
17-Nov-2005 |
03:20 |
x86 |
SP1 |
Статус
Корпорация Майкрософт подтверждает наличие этой проблемы в своих продуктах, которые перечислены в разделе «Применяется к». Впервые эта проблема была исправлена в Windows Server 2003 с пакетом обновления 2 (SP2).
Дополнительная информация
Событие DCOM 10009 имеет недостаточные данные о базовой ошибке, которая привела к их возникновению. Обычно события DCOM 10009 записываются из-за сбоев сетевого соединения с сервером DCOM. Сюда входят проблемы, такие как разрешение имен и проблемы с брандмауэром. Эти проблемы часто ведут к ошибкам RPC 0x6ba (0x800706BA). Чтобы получить дополнительные сведения об ошибке, связанные с этой ошибкой, с этим исправлением в Windows Server 2003, включите расширенные сведения об ошибке RPC (EEINFO). Если EEINFO, дополнительные данные записываются в раздел данных о событиях DCOM 10009 события. В Windows Vista вам не нужно включать EEINFO, так как она включена по умолчанию и по умолчанию копируется в данные события DCOM 10009. Обычно EEinfo содержат ошибки, специфические для Winsock, например 10048 (WSAEADDRINUSE), например, когда все доступные порты TCP будут исчерпаны. Дополнительные сведения о расширенных ошибках RPC, в том числе о том, как включить и каким образом интерпретировать данные, можно найти на веб-сайте Microsoft Developer Network (MSDN):
http://msdn2.microsoft.com/en-us/library/aa373803.aspx
http://msdn2.microsoft.com/en-us/library/aa379109.aspx Ниже приведен пример события, которое регистрируется в журнале. Она включает дополнительные полезные данные. В частности, сведения о статусе, gencomp и detloc в данных об ошибке будут представлять собой интересные. Например, состояние 11001 имеет значение «отсутствует известный узел» и генерируется с помощью Winsock (gencomp = 8). Дополнительные сведения можно найти в центре справки и поддержки на веб-сайте корпорации Майкрософт по следующему адресу:
http://support.microsoft.comData: 0000: 3c 52 65 63 6f 72 64 23 <Record# 0008: 31 3a 20 43 6f 6d 70 75 1: Compu 0010: 74 65 72 3d 28 6e 75 6c ter=(nul 0018: 6c 29 3b 50 69 64 3d 31 l);Pid=1 0020: 31 30 30 3b 31 2f 35 2f 100;1/5/ 0028: 32 30 30 36 20 31 34 3a 2006 14: 0030: 34 3a 33 33 3a 31 31 36 4:33:116 0038: 3b 53 74 61 74 75 73 3d ;Status= 0040: 31 37 32 32 3b 47 65 6e 1722;Gen 0048: 63 6f 6d 70 3d 38 3b 44 comp=8;D 0050: 65 74 6c 6f 63 3d 33 32 etloc=32 0058: 32 3b 46 6c 61 67 73 3d 2;Flags= 0060: 30 3b 50 61 72 61 6d 73 0;Params 0068: 3d 30 3b 3e 3c 52 65 63 =0;><Rec 0070: 6f 72 64 23 32 3a 20 43 ord#2: C 0078: 6f 6d 70 75 74 65 72 3d omputer= 0080: 28 6e 75 6c 6c 29 3b 50 (null);P 0088: 69 64 3d 31 31 30 30 3b id=1100; 0090: 31 2f 35 2f 32 30 30 36 1/5/2006 0098: 20 31 34 3a 34 3a 33 33 14:4:33 00a0: 3a 31 31 36 3b 53 74 61 :116;Sta 00a8: 74 75 73 3d 31 31 30 30 tus=1100 00b0: 31 3b 47 65 6e 63 6f 6d 1;Gencom 00b8: 70 3d 38 3b 44 65 74 6c p=8;Detl 00c0: 6f 63 3d 33 32 30 3b 46 oc=320;F 00c8: 6c 61 67 73 3d 30 3b 50 lags=0;P 00d0: 61 72 61 6d 73 3d 31 3b arams=1; 00d8: 7b 50 61 72 61 6d 23 30 {Param#0 00e0: 3a 7d 65 72 54 48 65 72 :Server 00e8: 7d 3e }> Ошибка, упомянутая в разделе «проблема», часто является ошибкой сетевого соединения. Ниже перечислены возможные причины данной ошибки.
-
Ошибки при разрешении имен.
-
Все порты TCP на сервере используются.
-
Происходит конфликт TCP порта.
Для устранения ошибок DCOM 10009 используйте указанные ниже способы.
Способ 1: Убедитесь, что разрешение имен работает правильно
Страница активации прокси-приложения COM+ имеет свойство Remote Server Name (RSN). Свойство RSN может представлять собой IP-адрес, полное доменное имя (FQDN) или имя NetBIOS. Чтобы устранить эту проблему, используйте команду ping для проверки подключения к удаленному серверу с использованием IP-адреса, полного доменного имени и имен NetBIOS.
Способ 2: Проверка использования TCP порта
Когда клиент выполняет вызовы DCOM на серверное приложение COM+, каждое подключение может использовать другой TCP-порт. Следовательно, все порты TCP на сервере могут использоваться. При возникновении этого условия сервер не может допускать дополнительные подключения. Дополнительные сведения о том, как определить использование порта TCP при устранении проблем с подключением по протоколу TCP/IP, можно найти в статьях базы знаний Майкрософт, выполнив следующие номера статей:
832919 Новые функции и функции в PortQry версии 2,0
301512 Многие подключения к протоколу TCP установлены для прокси-сервера или заглушки COM+
Способ 3: Проверка базового сетевого подключения для устранения проблем с конфликтом TCP
Для получения дополнительных сведений об устранении ошибок, возникающих при использовании обычной сети, для устранения проблем с конфликтом TCP щелкните следующий номер статьи базы знаний Майкрософт:
325487 Устранение неполадок с подключением к сети
Ссылки
Чтобы получить дополнительные сведения об использовании TCP-портов, когда клиент делает вызов DCOM для серверного приложения COM+, щелкните следующий номер статьи базы знаний Майкрософт:
301512 Многие подключения к протоколу TCP установлены для прокси-сервера или заглушки COM+ Чтобы получить дополнительные сведения о терминологии обновления программного обеспечения, щелкните следующий номер статьи базы знаний Майкрософт:
824684 Стандартные термины, используемые при описании обновлений программных продуктов Майкрософт
- Remove From My Forums
-
Question
-
I get this message on a domain controller that i just put into production, running windows server 2008 r2, AD 2003. This gets generated almost everytime i reboot the server. It occurs 4 times in succession relating once to each of our external dns forwarders. I have checked that DCOM uses tcp/ip. I do not believe this to be impacting us significantly however i do prefer to know what this means and how to prevent it.
Thanks
Answers
-
Hi,
Thanks for the post.
From your description, I understand that the Event error 10009 stating “DCOM was unable to communicate with the computer %1 using any of the configured protocols” is received on the new DC.
There is a problem accessing the COM Service on a remote computer. To resolve this problem:
- Ensure that the remote computer is online.
- This problem may be the result of a firewall blocking the connection. For security, COM+ network access is not enabled by default. Check the system to determine whether the firewall is blocking the remote connection.
- Other reasons for the problem might be found in the Extended Remote Procedure Call (RPC) Error information that is available in Event Viewer.
For detailed information about the above steps, please refer to the following article:
Event ID 10009 — COM Remote Service Availability
http://technet.microsoft.com/en-us/library/cc774368(WS.10).aspx
Does it work?
If the problem continues, please collect the MPSReport from Windows Server 2008 R2.
1. Download proper MPS Report tool from the website below.
Microsoft Product Support Reports
http://www.microsoft.com/downloads/details.aspx?FamilyID=CEBF3C7C-7CA5-408F-88B7-F9C79B7306C0&displaylang=en
2. Double-click to run it, if requirement is not met, please follow the wizard to download and install them. After that, click Next, when the «Select the diagnostics you want to run» page appears, select «General», “Internet and Networking”,“Server Components”, click Next.
3. After collecting all log files, choose «Save the results», choose a folder to save <Computername>MPSReports.cab file.
For your convenience, I have created a workspace for you. You can upload the information files to the following link. (Please choose «Send Files to Microsoft»)
Workspace URL: (https://sftasia.one.microsoft.com/choosetransfer.aspx?key=a7031c4a-e8ca-48cd-bb5d-7727e2967780)
Password: #PAxwF2A+1xvy[zj
Note: Due to differences in text formatting with various email clients, the workspace link above may appear to be broken. Please be sure to include all text between ‘(‘ and ‘)’ when typing or copying the workspace link into your browser.
Thanks,
Miles
-
Marked as answer by
Thursday, August 26, 2010 4:16 AM
Hi There, I have a similar issue as above. Our Primary DPM server is throwing up an error «DCOM unable to communicate with the computer xxxxx using any of the configured protocols» But the computer in question no longer exists! how can we stop DCOM from
reporting this. The computer is also showing up under available members when modifying a protection group — is there any way removing references to this computer manually form DPM. Any help appriciated.
Hi,
Thanks for the post.
From your description, I understand that the Event error 10009 stating “DCOM was unable to communicate with the computer %1 using
any of the configured protocols” is received on the new DC.There is a problem accessing the COM Service on a remote computer. To resolve this problem:
- Ensure that the remote computer is online.
- This problem may be the result of a firewall blocking the connection. For security, COM+ network access is not enabled by default. Check the system to determine whether the firewall
is blocking the remote connection.- Other reasons for the problem might be found in the Extended Remote Procedure Call (RPC) Error information that is available in Event Viewer.
For detailed information about the above steps, please refer to the following article:
Event ID 10009 — COM Remote Service Availability
http://technet.microsoft.com/en-us/library/cc774368(WS.10).aspx
Does it work?
If the problem continues,
please collect the MPSReport from Windows Server 2008 R2.1. Download proper MPS Report tool from the website below.
Microsoft Product Support Reports
http://www.microsoft.com/downloads/details.aspx?FamilyID=CEBF3C7C-7CA5-408F-88B7-F9C79B7306C0&displaylang=en
2. Double-click to run it, if requirement is not met, please follow the wizard to download and install them. After that, click Next, when the «Select the diagnostics
you want to run» page appears, select «General», “Internet and Networking”,“Server Components”, click Next.
3. After collecting all log files, choose «Save the results», choose a folder to save <Computername>MPSReports.cab file.
For your convenience, I have created a workspace for you. You can upload the information files to the following link. (Please choose «Send Files to Microsoft»)
Workspace URL: (https://sftasia.one.microsoft.com/choosetransfer.aspx?key=a7031c4a-e8ca-48cd-bb5d-7727e2967780)
Password: #PAxwF2A+1xvy[zj
Note: Due to differences in text formatting with various email clients, the workspace link above may appear to be broken. Please be sure to include all
text between ‘(‘ and ‘)’ when typing or copying the workspace link into your browser.Thanks,
Miles
hi
what do you mean «ensure computer is online»?
i have the same issue, but again it is trying to dcom to external DNS servers (the DNS servers we have as forwarders in DNS where only dns queries are done).
could you pls clarify why this access would be required?
brgds
Angelos
Then check AD and you will probablly find the computer still exists in which you need to delete the object.
Seeing the same issue, and neither AD nor DNS has any trace of the system referenced in the error. Any thoughts on that?
same, system is gone, and not in AD/DNS, where else could a reference exist?
I’m getting a whole bunch of these filling up my event log, historically we have had scavenging turned off (for some unknown reason). Have just turned this on; will keep all updated to see if these errors stop.
JR
I’m on SBS 2011 that was migrated from SBS 2008. Old server gone (removed) and I’m getting DCOM errors in Event Log. Same boat as you guys, nothing in AD and DNS.
I went to «Active Directory Administrative Center» and searched for offending server (changed scope to Global Catalog Search). Got two results. ADSI Edit and delete them.
Now, wait and see.
Dave
I’m also having this issue, however it’s for our ISP’s DNS servers. They are both online and responding, but I’m not sure why DCOM would be attempting to contact external DNS servers.
Holy Hannah! I’m not alone — ANYone find a way to stop my bleepin’ SBS 2011 server from attempting DCOM connections to nonexistent (or, Linux) boxes?
I have the same problem here in our university environment. The error logs are filling up on a number of computers. One thing these all have in common is that they were ghostcast. The DCOM error references the original name of the computer
I gathered from.
Windows XP SP3 boxes. Anyone have any luck fixing this?
Brad
That regedit proposed above really didn’t do much, and perhaps made my situation worse, because now I have no idea which computers we’re getting the DCOM errors:
Description:
The description for Event ID 10009 from source DCOM cannot be found. Either the component that raises this event is not installed on your local computer or the installation is corrupted. You can install or repair the component on the local computer.
I’m also having this issue, however it’s for our ISP’s DNS servers. They are both online and responding, but I’m not sure why DCOM would be attempting to contact external DNS servers.
You are not alone. I have at least one client server that is receiving DCOM 10009 errors, and the IP addresses are of the server’s external DNS forwarders. The server’s DNS settings are fine, as are those of its NIC.
Every search I’ve done points me to opening firewall settings for COM+ —the problem isn’t the firewall settings (which I don’t want to change), the problem is I don’t want the DCOM behavior to be occurring in the first place.
Everyone gets everything he wants. Me, I wanted to be a sysadmin. And for my sins —they made me one.
-
Edited by
LoneWolf15
Thursday, February 23, 2012 4:01 PM
I’m getting this problem on a MS SQL Server. I think it’s trying to contact an old web server which has since been decommissioned and no longer exists. Did anyone find a solution to this problem?
I have the same problem here in our university environment. The error logs are filling up on a number of computers. One thing these all have in common is that they were ghostcast. The DCOM error references the original name of the computer
I gathered from.Windows XP SP3 boxes. Anyone have any luck fixing this?
Brad
Exact same issue here!! And I am unable to find an answer. Anyone at MS able to help? I have delted every printer, deleted every file/regkey etc that might possibly containg the orginal host name. I have
ran ghostwalker, NewSid, etc. Nothing has worked.
I’m also having this issue, however it’s for our ISP’s DNS servers. They are both online and responding, but I’m not sure why DCOM would be attempting to contact external DNS servers.
You are not alone. I have at least one client server that is receiving DCOM 10009 errors, and the IP addresses are of the server’s external DNS forwarders. The server’s DNS settings are fine, as are those of its NIC.
Every search I’ve done points me to opening firewall settings for COM+ —the problem isn’t the firewall settings (which I don’t want to change), the problem is I don’t want the DCOM behavior to be occurring in the first place.
Everyone gets everything he wants. Me, I wanted to be a sysadmin. And for my sins —they made me one.
I have the same issue…SBS2011 Essentials logging DCOM errors for all DNS forwarders
Can someone please «unmark as answer» Mr. Zhang’s above post? It clearly is not an answer/resolution/explanation!
Hi, Miles—
Not sure if you are still around at Microsoft, but there are major unanswered questions on this post.
Why does DCOM continue to look for non-existent computers? In our case, the computers are on foreign domains to which we connected briefly through their VPN. Others question how to turn this off for particular nodes since those nodes are deleted
from the Domain.
If you could respond to these, we would be most grateful.
Sincerely,
Graeme
-
Edited by
The Oracle
Friday, April 27, 2012 10:15 AM
I replied to Mr. Zhang on our behalf. If everyone votes the reply as Helpful, maybe we can get Mr. Zhang (or someone at Microsoft) to take notice.
Graeme
-
Edited by
The Oracle
Friday, April 27, 2012 10:14 AM
I am receiving this error not even from a windows box but from a 3com switch. WTF Microsoft. Could someone post a fix pls.
Similir issue here, the error is pointing to my linksys router (home lab) and Google DNS server 8.8.8.8. These errors are not allowing me to setup my Exchange lab. arrrrgggghh.
Ncruz1980
Same here… My DNS servers are generating these events every often when trying to access external DNS forwarders
Mate
Is this one of those issues with no fix?
There has to be a way to find where the dcom service lists the computers it tries to communicate with.
CPC Computers
-
Proposed as answer by
OTL-UPT
Wednesday, May 23, 2012 1:06 AM -
Unproposed as answer by
OTL-UPT
Wednesday, May 23, 2012 1:06 AM
Same here.
Server 2008 R2 DC. DCOM errors (Event ID 1009) because it can’t create an RPC connection to my DNS forwarder (OpenDNS)!?!
WTH is it trying to do that?!?
-
Edited by
Alceryes
Sunday, June 3, 2012 1:17 AM
Just wanted to add that we’re also seeing this at multiple clients. I’ve posted the below in the MS Partner Forums but was met with a complete lack of interest in the issue or any information that was of use:
Problem: Multiple servers are throwing DCOM 10009 errors in the System Log stating that «DCOM was unable to communicate with the computer <EXTERNAL DNS FORWARDER> using any of the configured protocols.»
Notes:
- The issue started occuring after May 13th 2012 when we patched our clients boxes.
- One common factor appears to be that
KB2676562 was installed to all the servers at this point. (EDIT: having seen that people were experiencing this prior to this patch update I now suspect that this is irrelevant) - The issue is affecting mulitple servers covering 2003, SBS2003, 2008 R2/SBS2011, all DC’s, secondary DNS servers that are not DC’s are not exhibiting the problem.
- There is an entry per DNS Forwarder in the System logs, these DNS Forwarders vary per client but generally include Google (8.8.8.8, 8.8.4.4), OpenDNS (208.67.222.222, 208.67.220.220) and two from each clients ISP which vary.
- It appears to be happening daily at approx 1490 minute (24hrs 50mins) intervals but one server is producing the errors far more frequently, every hour in two sets 10 minutes apart, this is a 2008 R2 box.
- No other DNS errors or issues are encountered in the logs or on the networks.
- Various people have also comment at the bottom of this thread. They appear to be experiencing the same issue.
MS Article Link :
http://social.technet.microsoft.com/Forums/en-US/winservergen/thread/353d381d-0911-41c3-98fb-2475b65c32f6
Any assistance appreciated in resolving.
Additional: Extended info dump from one of the events on a SBS2011 server
<Record#1: Computer=(null);Pid=144;6/5/2012 19:30:33:820;Status=1722;Gencomp=2;Detloc=1710;Flags=0;Params=1;{Param#0:0}>
<Record#2: Computer=(null);Pid=144;6/5/2012 19:30:33:820;Status=1722;Gencomp=18;Detloc=1442;Flags=0;Params=1;{Param#0:8.8.8.8}>
<Record#3: Computer=(null);Pid=144;6/5/2012 19:30:33:820;Status=1722;Gencomp=18;Detloc=323;Flags=0;Params=0;>
<Record#4: Computer=(null);Pid=144;6/5/2012 19:30:33:820;Status=1237;Gencomp=18;Detloc=313;Flags=0;Params=0;>
<Record#5: Computer=(null);Pid=144;6/5/2012 19:30:33:820;Status=10060;Gencomp=18;Detloc=311;Flags=0;Params=3;{Param#0:135}{Param#1:0}{Param#2:0x808080800000000}>
<Record#6: Computer=(null);Pid=144;6/5/2012 19:30:33:820;Status=10060;Gencomp=18;Detloc=318;Flags=0;Params=0;>
-
Edited by
Greg Steer
Monday, June 11, 2012 5:17 PM
We’re seeing the same error as Greg. Servers on multiple customer sites are connecting via port 135 to the Google DNS servers (configures as our forwarders) — would be great to get this nailed? Is it a configuration problem or a bug do you think?
Edmund
I don’t think it’s a config problem…unless three dozen Microsoft articles are also wrong.
Because this thread has been marked as «answered», I feel we should start a new one (with obvious links to this one).
Anyone else agree?
As an update to my post we’ve now tracked down the source of our issue.
The offending article is our managed services software Labtech. It appears that the latest update must have introduced a monitor or script that is running on a regular basis that is causing these requests to happen at our clients sites, disabling it at one
client last night knocked out the production of the errors.
I’m following up with them to establish exactly which script/monitor is causing it and will report back, at least to let people know what mechanism is triggering it, in case there is something similar being run on your systems.
Cheers
Greg
Hi Greg,
Interesting — we also use Labtech — I’ll send a ticket in…
Edmund
Nice find, Greg. We use LabTech too. I found this MS article(http://support.microsoft.com/kb/957713), but I am curious if you heard anything back from LT. Thanks for your persistence.
-brad
Solve IT
Lakewood, CO
This is in no way «answered» unless i Missed something.
CPC Computers
I agree that this is not answered. We also use LabTech like the last couple of people have mentioned. We are getting the same error with DCOM trying to communicate with the external dns servers.
For us, it is only occurring on:
2008 R2 Enterprise x64
2008 R2 Foundation x64
2008 R2 Standard x64
2011 SBS Standard x64
but is not occurring on:
2008 Standard Federation Edition
2008 Standard (32 bit)
Any 2003 server
Same «DCOM trying to communicate with ISP DNS / DNS Forwarders» here and running Labtech. LabTech mentioned this is not caused by their product and must be DNS related on our side.
-
Edited by
Broxigar1983
Tuesday, July 17, 2012 3:59 AM
We also have the same problem with the DCOM error message on our DNS and the IP referenced is the external DNS. We are also a LabTech user. If enough of us complain, maybe they will acknowledge this.
Is anyone getting this exact symptom with external DNS IP on an internal DNS machine that is NOT on LabTech??
This is NOT a LabTech specific problem.
I’ve got a Server 2008 R2 lab at home (domain controller, exchange, web, dev, etc…) and I do not use LabTech.
After digging in, I learned that LabTech is just running a DCDIAG script which triggers the event in the log. It isn’t the root cause of the issue, only the timing
The specific command to reproduce is DCDIAG /TEST:DNS /DNSforwarders
This is the resolution provided by labtech
I am including a resolution that I found on Microsoft’s Support Page. This is actually a Microsoft Issue, but here is their resolution.
http://support.microsoft.com/kb/957713
2.1DCOM Event ID 10009:
Problem: The DCOM event ID 10009 will occur when a client workstation has a misconfigured firewall or other issues affecting its network communications within the domain. For example, if the workstation is not managed by an SBS GPO. In this scenario, the DCOM
event ID 10009 will happen repeatedly, potentially hundreds per day.
Resolution: To attempt to resolve configuration issues with the firewall try the following:
* Make sure to allow remote management exception. Depending on your firewall solution this might be implemented or might require opening several ports. Unfortunately, this means opening common ports like TCP/135, TCP/139 but also a range of dynamic ports that
cannot easily be defined and start at 1025. Check with your firewall manufacturer for the proper ways of allowing dynamic RPC traffic.
* If the workstation is on a different subnet than the SBS server and it is running Windows XP SP2 or higher, the firewall exceptions provided by the SBS group policies will not properly allow the required connectivity. You should edit the Client XP GPO and
change the scope of the rules to allow subnet + the internal IP of the server. Follow the extra steps below to properly monitor XP SP2 (or higher) machines running in the SBS domain on different subnets than the SBS server, and prevent the DCOM event ID 10009
errors if that is the case.
1. Click Start, click Run, type GPMC.MSC, and click OK.
2. Click Continue on the UAC prompt.
3. Expand Forest: Domain.local, Domains, Domain.local and select Group Policy Objects. (Replace Domain.local with your domain)
4. Right-click the Windows SBS Client — Windows XP Policy and click Edit.
5. Expand Computer Configuration, Policies, Administrative Templates, Network, Network Connections, Windows Firewall, Domain Profile.
6. Find the IP Address of the server: Open a command prompt window (cmd.exe) from the Start menu. In the command prompt window type IPConfig and press return. Make note of the IPv4 address listed.
7. In the Group Policy Management Editor, double click Windows Firewall: Allow inbound file and printer sharing exception
a. In the text box labeled Allow unsolicited incoming messages from these IP addresses, add the IP (IPv4) of the server. For example, if the IP of the server is 192.168.1.2, the text box should read: localsubnet,192.168.1.2.
b. Click OK.
8. Repeat Steps 7.a and 7.b for the following rules:
Windows Firewall: Allow inbound remote administration exception
Windows Firewall: Allow inbound remote desktop exceptions
-
Proposed as answer by
alexpking
Wednesday, July 18, 2012 9:13 PM
Not a solution, so please PLEASE don’t close this thread.
I realize this thread is lengthy, but the common complaints are: attempted DCOM communications to either 1) servers that do not exist, or 2) servers with which we should NOT be having DCOM comms with (e.g. ISP DNS servers!)
-
Edited by
BB8771
Wednesday, July 18, 2012 10:21 PM
Also having this problem, except with two Win 7 workstations that are active. We do not use LabTech, however, we do use Kaseya. Oddly enough, the two workstations in question are two where the Kaseya agent is not installed (it seems to have some problem
installing).
Why can’t we simply get a solution that involves telling DCOM to ignore these machines?
I’m also seeing the same dcom errors when N-Able is trying to connect to machines that are no longer on the network. I’ve removed them but will have to see if the 10009 errors clear up.
I also ran the «dcdiag /test:dns /dnsforwarders» command at a couple clients. Both claim every test passed. One finished quickly and didn’t log any errors, the other took 2-3 mins and logged 3 errors… 8.8.8.8 being one of them. The only difference between
the 2 configurations that I see is that one has the 3 static DNS forwarders configured and the other is using just the Root Hints.
Removing the forwarders from DNS seems to have cleared the errors when running the command from above, and the test runs much faster. Which makes sense because according to a couple Technet articles the forwarders actually have to time out before the root
hints kick in, and if there’s no forwarders configured then the /test:dns /dnsforwarders skips them. This article has some good info about Root hints and forwarders,
http://social.technet.microsoft.com/Forums/en-US/winserverNIS/thread/16c8211b-eaea-4c78-beea-435686056ff3/ and
http://technet.microsoft.com/en-us/library/ff807391%28v=ws.10%29.aspx
It looks like the issue is with what the actual «dcdiag /test:dns /dnsforwarders» command is designed to test and how it goes about it (http://technet.microsoft.com/en-us/library/cc776854%28v=ws.10%29.aspx).
Your servers just don’t have access to your ISP’s or Google’s DNS server through the DCOM protocols (probably due to the firewall restrictions mentioned earlier in this thread), where as if you run that command on a dns server forwarding to an internal DNS
server that is then relaying all dns out through root hints or another forwarder you wont get any errors.
In which case the Labtech script attempting to monitor the dns forwarders is whats actually at fault becuase its not using the dcdiag command as intended.
I hope this helps everyone.
-J
-
Proposed as answer by
Jay Forster
Tuesday, July 31, 2012 9:05 PM -
Edited by
Jay Forster
Tuesday, July 31, 2012 9:09 PM
added labtech comment
I’m also seeing the same dcom errors when N-Able is trying to connect to machines that are no longer on the network. I’ve removed them but will have to see if the 10009 errors clear up.
I also ran the «dcdiag /test:dns /dnsforwarders» command at a couple clients. Both claim every test passed. One finished quickly and didn’t log any errors, the other took 2-3 mins and logged 3 errors… 8.8.8.8 being one of them. The only difference between
the 2 configurations that I see is that one has the 3 static DNS forwarders configured and the other is using just the Root Hints.Removing the forwarders from DNS seems to have cleared the errors when running the command from above, and the test runs much faster. Which makes sense because according to a couple Technet articles the forwarders actually have to time out before the root
hints kick in, and if there’s no forwarders configured then the /test:dns /dnsforwarders skips them. This article has some good info about Root hints and forwarders,http://social.technet.microsoft.com/Forums/en-US/winserverNIS/thread/16c8211b-eaea-4c78-beea-435686056ff3/ and
http://technet.microsoft.com/en-us/library/ff807391%28v=ws.10%29.aspx
It looks like the issue is with what the actual «dcdiag /test:dns /dnsforwarders» command is designed to test and how it goes about it (http://technet.microsoft.com/en-us/library/cc776854%28v=ws.10%29.aspx).
Your servers just don’t have access to your ISP’s or Google’s DNS server through the DCOM protocols (probably due to the firewall restrictions mentioned earlier in this thread), where as if you run that command on a dns server forwarding to an internal DNS
server that is then relaying all dns out through root hints or another forwarder you wont get any errors.In which case the Labtech script attempting to monitor the dns forwarders is whats actually at fault becuase its not using the dcdiag command as intended.
I hope this helps everyone.
-J
Tested this on one of the DNS servers and seems to have solved the issue. But we will not implement this solution, rather keep the DNS forwarders and just ignore these error messages in the eventlog.
I have had a problem similar to this that had been driving me crazy for a long time; I eventually solved this by solving another error that I was also experiencing for the same non-existent server
Event ID 13
Certificate enrollment for Local system failed to enroll for a DomainController certificate with request ID N/A from servername.domain.comabc CA (The RPC server is unavailable. 0x800706ba (WIN32: 1722)).
Event ID 10009
DCOM was unable to communicate with the computer servername.domain.com using any of the configured protocols.
By following
Step 6: Remove CA objects from Active Directory
in this article
http://support.microsoft.com/kb/889250/en-us
This solved my problem as I found the unknown server listed here, this might help someone.
-
Proposed as answer by
Trade of Jacks
Friday, February 8, 2013 4:41 PM
Thanks BocalT helped me solve my Domain problems.
All LabTech users try this:
Find the dctest.bat file in the windowsltsvc folder on the server and edit it so that it only does the basic DNS tests and all others full tests:
dcdiag.exe /c /test:DNS /DNSBasic
e.g.
@echo off
if exist %windir%system32dcdiag.exe %windir%system32dcdiag.exe /c /test:DNS /DnsBasic | findstr /I /C:»failed test» | findstr /I /V /C:»systemlog»
if exist %windir%system32dcdiag.exe goto :end
if exist %windir%ltsvcdcdiag.exe %windir%ltsvcdcdiag.exe /c /test:DNS /DnsBasic | findstr /I /C:»failed test» | findstr /I /V /C:»systemlog»
if exist %windir%ltsvcdcdiag.exe goto :end
echo failed test Unable to find dcdiag.exe
:end
Also — edit the dctest.bat in LTShareTransferMonitors on the LabTech server for all future Agents to use
This does not run all the full DNS tests, but should be fine — see http://technet.microsoft.com/en-us/library/cc731968(v=ws.10).aspx for more info
-
Proposed as answer by
Broxigar1983
Tuesday, October 9, 2012 5:37 AM
All LabTech users try this:
Find the dctest.bat file in the windowsltsvc folder on the server and edit it so that it only does the basic DNS tests and all others full tests:
dcdiag.exe /c /test:DNS /DNSBasic
e.g.
@echo off
if exist %windir%system32dcdiag.exe %windir%system32dcdiag.exe /c /test:DNS /DnsBasic | findstr /I /C:»failed test» | findstr /I /V /C:»systemlog»
if exist %windir%system32dcdiag.exe goto :end
if exist %windir%ltsvcdcdiag.exe %windir%ltsvcdcdiag.exe /c /test:DNS /DnsBasic | findstr /I /C:»failed test» | findstr /I /V /C:»systemlog»
if exist %windir%ltsvcdcdiag.exe goto :end
echo failed test Unable to find dcdiag.exe
:endAlso — edit the dctest.bat in LTShareTransferMonitors on the LabTech server for all future Agents to use
This does not run all the full DNS tests, but should be fine — see http://technet.microsoft.com/en-us/library/cc731968(v=ws.10).aspx for more info
Thanks Jez Nolan!!
I have tested this on both of our DNS servers and all DCOM 10009 errors disappeared.
Hey All,
I can verify that this fixes the issue with Labtech. I found it only today after our LT backend server was crashing. Well, this was due to an overwhelmingly high number of Event Logs being generated from Domain Controllers in our environment
and for our clients. Why were these logs being generated? Because of Labtech running the DCDIAG tests and associated «fix» script pretty much continuously. So, a Microsoft bug is found by Labtech, only to have Labtech recursively spread the
bug to the point it crashes itself…awesome. Anyway, the fix above works, whether you’re a Labtech customer or not.
Long time and no response from me I know as I originally posted it being related to LabTech.
The fix from Jez above was also the one we ended up using.
The reason it happens is that the full DNS Diagnostics are running queries that are specific to MS AD DNS servers, if these are run against a non-MS DNS server then no response is received and these errors are thrown.
Quoting a LabTech Tech’s response:
«Greg, This issue is due to the labtech service running a DC Diag to ensure your AD environment is healthy and following MSFT’s best practices. The DC DIAG tool will write the DCOM errors
to the event log. The reason that these are valid is that the systems should only contain AD DNS servers per MSFT best practices. LabTech follows these best practices and will alert you when you are not following them. At this time, there are two options.
Disable the Master Script Run 2008 R2 Best Practice Report from the group: Service Plans. Windows Servers.Server Roles.Windows Servers Core Services.Domain Controllers or remove the DNS entries of non-AD DNS servers. Kevin»
Is there a way to modify this batch file so it is pushed out to the DCs again from LabTech? Or do we need to modify this batch file manually on all DCs (ugh)…
IIRC Labtech’s answer was «no it won’t be pushed».
But you could knock up a script in LT to do the file copy and run it against the Service Plans -> Windows Servers -> Server Roles -> Windows Servers Core Services -> Domain Controllers group.
This link helped me. I was getting the DCOM 10009 error for a SBS 2003 server I had removed from the domain during a migration to SBS 2011. The SBS2003 server was configured as a Certification Authority, and as a result there will still left
over entries in AD for the server. This link helped me find and delete them.
Hi there. I’ve seen this issue on mainly our SBS 2008 / 2012 installations
Beleive it or not it is by design, as for whatever reason Microsoft decided that using root hints instead of forwarders for SBS server was a good idea
Its a relatively simply fix, remove all of your DNS forwarder addresses from the DNS server — then add the FQDN and the IP address of your forwarders to the root hint list
TechieBuff,
Can you clarify something for me? We use OpenDNS servers as forwarders on all of our servers and have for sometime. If we remove them from the DNS forwarders and add them to the root hint list, do we need to remove all of the other root hint addresses in
order to be certain that our external traffic is only going to those DNS servers? Will we run into any other issues by removing the other root hint servers?
Thanks.
Michael Kanet ITernal Networks
This is not limited to SBS. I am running server 2008 R2.
-
Proposed as answer by
Skip47025B
Wednesday, March 20, 2013 4:32 PM -
Unproposed as answer by
Skip47025B
Wednesday, March 20, 2013 4:32 PM
I am also having this problem. I have searched and searched and cannot find the answer.
The server DCOM is trying to communicate with is dead and gone. It is no longer in AD or DNS or DHCP records. I cannot find a thing on the server that should make it want to communicate with this dead and gone server.
I am running windows Server 2008 R2 and have never used LabTech.
Please help.
Thanks,
-
Edited by
Skip47025B
Wednesday, March 20, 2013 4:36 PM
Anyone figure this out yet?
Having the same problem here, The server that DCOM is trying to communicate with has been removed from the domain and pulled out of the rack. We are getting this error every 10 minutes. I also have never used LabTech.
Thanks,
Hi,
Thanks for the post.
From your description, I understand that the Event error 10009 stating “DCOM was unable to communicate with the computer %1 using any of
the configured protocols” is received on the new DC.There is a problem accessing the COM Service on a remote computer. To resolve this problem:
- Ensure that the remote computer is online.
- (remainder left out)
From my side I can add that the same error is also occurring in mass on our SCCM 2007 server.
I see not only machines that are no longer existing, but most often : machines that were
not available/online at the point in time the job was running !!
The (portable) machine may have just been switched off, or the owner may be on the road at the given moment. Or not connected through VPN onto the local network.
Nevertheless, the eventlog is flooded with this type of messages. And because of those, our monitoring system is indicating full red alerts for a reason of no relevance ! We really would like to find a way to disable the generating of these messages
!
Here is one solution that worked for me
http://community.spiceworks.com/topic/288546-dcom-was-unable-to-communicate-with-the-computer-64-99-64-32
For reference in case link breaks.
We see this sometimes if your DNS server isn’t resolving your domain right — sometimes it’s because you have a .com as part of your local domain. For example, Spiceworks will try to query localhost, but your DNS server returns the results for localhost.com.
Go to the hosts file on the Spiceworks server and uncomment the IPV4 localhost entry, but leaving the IPV6 entry commented out. You’ll need to restart your computer after you save the changes, but it should be good to go afterwards!
- Remove From My Forums
-
Вопрос
-
С недавних пор на серверах Windows Server 2008 SP2 в журнале событий выдается сообщение при каждом входе на сервер через удаленный рабочий стол:
Источник: DistributedCOM
ID: 10009
Не удалось установить связь DCOM с компьютером <имя компьютера с которого я подключаюсь> через один из настроенных протоколов.
При этом подключение RDP происходит. Сообщения стали появляться недавно, видимо, после очередного обновления.
Как избежать появления этих ошибок?
Михаил
-
Перемещено
20 апреля 2012 г. 9:42
merge forums (От:Windows Server 2008)
-
Перемещено
Ответы
-
-
Помечено в качестве ответа
MikAndr
3 июня 2015 г. 8:46
-
Помечено в качестве ответа
Cause
Distributed COM (DCOM) extends the Component Object Model (COM) technology to enable applications using a COM server to communicate across machines on the network.
COM Server is a dynamic-link library (DLL) or an executable (.exe) file that exposes some functionality to be used by different applications.
Event ID 10009 (Event ID 10028 for Windows Server 2012 and above) indicates that the remote machine could not be found by DCOM, in most cases this error is not fatal.
Might be caused, because the remote machine is not available, either because it is down or there is has no network connectivity, by default Windows Firewall does not allow COM+ network access.
Frequent instances of this error might be caused when trying to perform “Discovery” with “Citrix AppCenter” with the help of a remote XenApp server, and it does not respond for example.
Could also appear because of a remote ControlUp Agent failing to communicate with the ControlUp Console.
User Actions
- Verify that the remote machine is up and running, and there are no firewall rules restricting the TCP connection, which uses Extended Remote Procedure Call (RPC) with port 135.
- Verify that the protocol settings on the machine for DCOM are configured properly.
From the command prompt type, dcomcnfg. This will open the Component Services mmc.
In the left pane, expand Component Services, then expand Computers, and right-click on My Computer and open Properties.
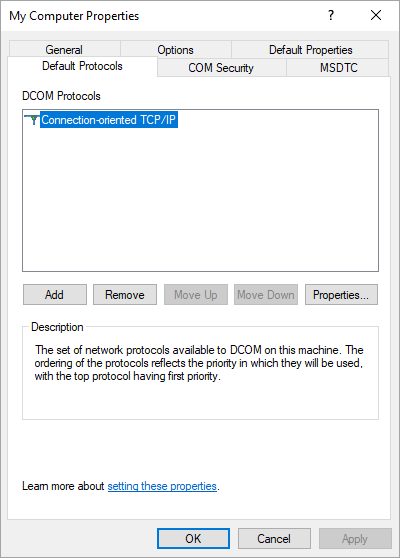
Switch to the Default Protocols tab and ensure that the DCOM Protocols are configured to use “Connection-oriented TCP/IP”.
Was this article helpful?
We have a Server 2008 R2 DC that is generating Event ID 10009 — «DCOM was unable to communicate with the computer X using any of the configured protocol.» I found this question: Event ID 10009 on Server 2008 R2 DCOM was unable to communicate with computer X. The only difference for me is that I know what the «computers» are. They are all our networking gear: switches, routers, firewall, WAPs etc.
Why would our DC being trying to contact network equipment via DCOM? And is there any way to stop it? It’s really annoying seeing thousands of errors a day in the event log.
asked Aug 14, 2013 at 20:18
1
I did a bit of research and found an interesting technet blog article from MS about the ID 10009 DCOM Troubleshooting. It does give the reason of the DCOM attempts, but explains you what is triggering the DCOM call and gives tips on getting rid of it.
In the same article (comments section from the blog team), it’s suggested to run tools like Network Monitor and Process Monitor, look at which process keeps sending failured RPC requests to identify which application is culprit in your scenario.
Hope it helps
sources : http://blogs.msdn.com/b/asiatech/archive/2010/03/16/how-to-troubleshoot-dcom-10009-error-logged-in-system-event.aspx
answered Aug 26, 2013 at 6:59
DoudaDouda
865 bronze badges
The possible causes explained above are valid and useful in common troubleshootings. Also duplicated/obsolete DNS records or firewall misconfigurations at the workstation level could lead to DCOM event ID 10009.
In my case, this type of error started to appear every 30 minutes (01:00, 01:30 and so on, the whole day) and most of the workstations that the server failed to connect to were powered off.
After digging a lot and by chance, I just find a simple solution: Stop (and set to manual startup) the Windows SBS Manager service.
Server is SBS 2011 with Exchange/DC/DNS/DHCP but I really don’t use the SBS Console, so finally no more polling errors.
answered Mar 9, 2017 at 13:37