As the various other answers to this question show, there are many different possible causes for this error message. The reason why it is happening to you may be totally different from the reasons why it is happening to me. And unfortunately, the error message is completely failing to point at the actual source of the problem, so it is completely unhelpful in troubleshooting. It is in fact entirely misleading.
So, instead of giving you yet one more from the myriad of possible causes of this error message, what I will do instead is show you how to troubleshoot this problem so as to find out what is causing it in your particular situation.
At work we commonly use the following two commands to enable some software to talk to various servers, for example to enable IntelliJ IDEA to talk to our internal maven repositories:
[Elevated]keytool
-printcert -rfc -sslserver maven.services.{our-company}.com:443 > public.crt
[Elevated]keytool
-import -storepass changeit -noprompt -trustcacerts -alias services.{our-company}.com
-keystore libsecuritycacerts -file public.crt
Now, what sometimes happens is that the keytool -printcert command is unable to do its job, either due to misconfiguration, or simply because of temporary connectivity issues, such as the firewall preventing it, the user forgot to start his VPN, whatever. It is a fact of life that this may happen. This is not actually the problem.
The problem is that when the stupid tool encounters such an error, it does not emit the error message to the standard error device, it emits it to the standard output device!
So here is what ends up happening:
- When you execute the first command, you don’t see any error message, so you have no idea that it failed. However, instead of a key, the
public.crtfile now contains an error message sayingkeytool error: java.lang.Exception: No certificate from the SSL server. - When you execute the second command, it reads
public.crtand it finds the text of the error message instead of a key in it, so it fails, sayingkeytool error: java.lang.Exception: Input not an X.509 certificate.
Bottom line is: after keytool -printcert ... > public.crt always dump the contents of public.crt to make sure it is actually a key and not an error message before proceeding to run keytool -import ... -file public.crt
Обновлено 26.06.2018
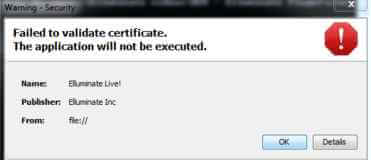
Добрый день уважаемые читатели блога pyatilistnik.org, сегодня я хочу рассказать о проблеме, с которой я столкнулся, где при попытке попасть на веб морду одного из fc свичей получил ошибку Java Failed to validate certificate. The application will not be executed. Давайте смотреть как ее исправить и попасть в веб интерфейс свитчей.
Как исправить ошибки java Failed to validate certificate
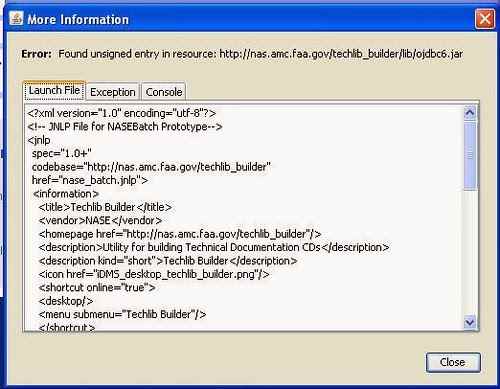
Давайте посмотрим само предупреждение и разберем как исправить ошибки java. В окне ошибки вы видите, что найдена не подписанная запись ресурса.
Ошибка Java Failed to validate certificate. The application will not be executed-02
Немного погуглив нашел несколько решений.
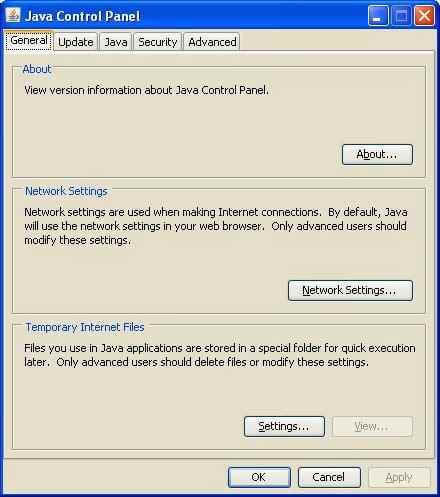
- Идем в панель управления-java. Ее можно найти в панели управления Windows.
Ошибка Java Failed to validate certificate. The application will not be executed-03
Жмем Settings.
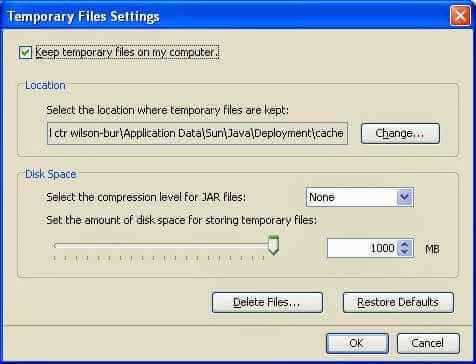
Ошибка Java Failed to validate certificate. The application will not be executed-04
и чистим кэш. Для этого нажимаем Delete Files.
Мне не помогло.
- 2 способ. Удаляем с помощью ccleaner все java что есть на компе, чистим реестр и все остатки файлов.
Ошибка Java Failed to validate certificate. The application will not be executed-05
переустанавливаем. У меня до этого стояла java 6.45 поставил версию поменьше.
ЕЩЕ ОЧЕНЬ ВАЖНО ИСПОЛЬЗОВАТЬ 32 БИТНУЮ ВЕРСИЮ JAVA.
- 3 причина ошибки Failed to validate certificate. The application will not be executed, идет файл java.security. Данный файл содержит в себе, настройки безопасности, его найти можно вот по такому пути
C:Program FilesJavaверсияlibsecurity для 64x версий, для x86 путь такой C:Program Files (x86)Javajre7libsecurity
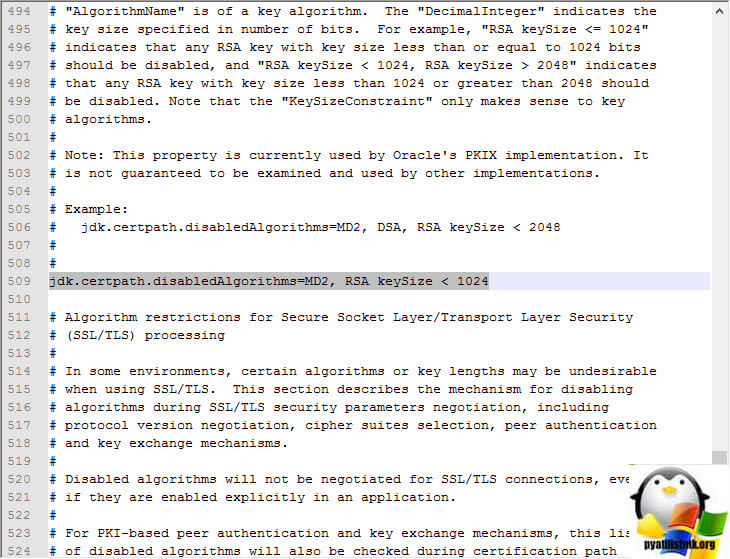
Щелкаем по java.security правым кликом и выбираем открыть с помощью текстового редактора или блокнота, находим там вот такую строку
jdk.certpath.disabledAlgorithms=MD2, RSA keySize < 1024
И редактируем ее вот к такому виду
jdk.certpath.disabledAlgorithms=MD2, RSA keySize < 256
После этого вы больше не увидите подобных ошибок в вашей операционной системе.
Июн 26, 2018 23:06
I am having trouble connecting to a secure site using a Java program. I have imported 3 certificates given from the server that I will be connecting to; public, inter and root certificate. I have properly imported the 3 certs to the java cacerts. And also specified in calling the Java class with the following parameters:
java -Djavax.net.debug=ssl
Djavax.net.ssl.keystore=JAVACACERTS -Djavax.net.ssl.keystorePassword=changeit -server -cp $CLASSPTH -Xmx500m SendOrderResponse
However, I’m getting a «bad_certificate» error. I looked at the details of the logs and it seems like the root certificate is not in the certificate chain.
Any idea why it happened? when I have imported the 3 certs in the Java cacerts? I assume that the bad certificate was thrown because of the certificate chain error.
ring bearer
20.3k7 gold badges59 silver badges71 bronze badges
asked Dec 13, 2011 at 4:32
2
I suggest you run:
openssl s_client -connect remoteserver:443
Assuming the remote server requires or requests client certificate authentication, it should send you a list of acceptable CAs.
You should send a certificate ultimately signed by one of these CAs.
The ssl specification does not require that you send the CA, however you should send the certificate and the full intermediate chain to that CA.
My experience is that two CA certificates may look extremely similar to each other. The move to 2048 bits has not helped in this regard. Double check.
As a side note, your client received the bad certificate alert. The problem lies with the certificates your client is sending, not the validation of the server certificates.
(Edit)
Did I mention that the certificates you send must be valid ? in particular,
- non expired end date and sensible start date
- a CN which matches the public DNS server name of the machine your are connecting from: the server may be performing a reverse DNS lookup on the client IP and matching it to the CN of the sent certificate.
tshepang
12k21 gold badges91 silver badges135 bronze badges
answered Jun 27, 2013 at 15:26
Bruno GriederBruno Grieder
27.8k8 gold badges69 silver badges99 bronze badges
It looks like you’re not using client-certificates.
In this case, don’t set the javax.net.ssl.keystore parameters in your client application. Importing only the root (and perhaps intermediate) certificates in your truststore (cacerts by default) should be sufficient too.
More details about keystore/truststore in this answer: https://stackoverflow.com/a/6341566/372643
answered Dec 13, 2011 at 12:55
BrunoBruno
119k31 gold badges268 silver badges376 bronze badges
3
If you have imported the certificates than try this
Set PATH=<YOUR JRE/BIN>;%PATH%
and than run your java client
answered Oct 24, 2012 at 5:53
rbhawsarrbhawsar
8057 silver badges25 bronze badges
1
При подключении к панели управления SAN свитча Brocade, запускается JAVA-апплет. Итогом запуска получил сообщение:
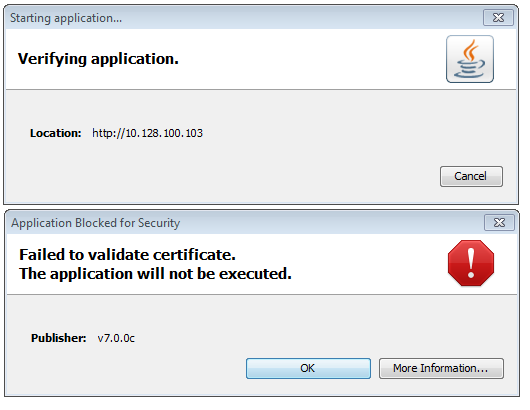
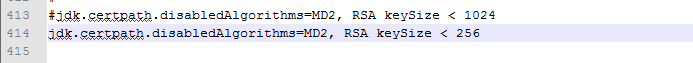
В этом файле надо поправить строку:
jdk.certpath.disabledAlgorithms=MD2, RSA keySize < 1024
На
jdk.certpath.disabledAlgorithms=MD2, RSA keySize < 256
или просто закомментировать.
Таким образом понижаем уровень безопасности, но получаем возможность работы с Java апплетом.
Problem :
Unable to launch Java applications with error «Failed to validate certificate, The application will not be executed.» error.
Failed to validate certificate,
The application will not be executed.
sun.security.validator.ValidatorException:
PKIX path validation failed:
java.security.cert.CertPathValidatorException: algorithm constraints
check failed
at sun.security.validator.PKIXValidator.doValidate(Unknown Source)
at sun.security.validator.PKIXValidator.engineValidate(Unknown Source)
in this case i run for brocade san switch
Description:
Starting
with Java/JRE 7u40, Java requires the application (the jar file
executed via jnlp) to be signed by a certificate with a minimum public
key size of 1024 bits.
At this time the Live Health jnlps are
signed with a certificate of less than 1024 bits (we use 512 bits),
causing a security validation failure.
solution :
Changing the value 1024 to 256 solves the issue in eHealth Live clients
(as they are currently signed by a certificate with a 512-bit key). This
change in java.security has to be done by a user with the administrator
role, and java must be restarted in order for changes to take effect.
— edit java security @ : C:Program Files (x86)Javajre1.8.0_181libsecurityjava.security
jdk.certpath.disabledAlgorithms=MD2, MD5, SHA1 jdkCA & usage TLSServer,
RSA keySize < 1024, DSA keySize < 1024, EC keySize < 224
to :
jdk.certpath.disabledAlgorithms=MD2, MD5, SHA1 jdkCA & usage TLSServer,
RSA keySize < 256, DSA keySize < 256, EC keySize < 224
==> tested on windows 10 with