by Loredana Harsana
Loredana is a passionate writer with a keen interest in PC software and technology. She started off writing about mobile phones back when Samsung Galaxy S II was… read more
Updated on February 14, 2023
- The most common reason for certificate validation failure on VPN is an expired certificate.
- VPN certificates are essential because they are a more secure way for authentication than preshared keys.
- Users reported that updating the certificate will solve the certificate validation failure error.
VPN, an acronym for Virtual Privacy Networks has certificates by a public authority that manages them. They are essential electronic documents, as VPN devices use them to indicate if they are the ones you connect to. Thus, it is imperative to quickly fix any VPN certificate validation failure.
Digital certificates of VPN are also used for authentication, and this is more secure than preshared keys. VPN certificates expire due to security reasons and when there is a need to replace them.
It used to take a more extended period of time for a valid VPN certificate to last, however, in 2021, SSL certificate expiration was reduced and a valid certificate lasted for 12 months only.
Still, this may not be the sole reason you are getting a failure in certificate validation. There are many other reasons why this may be happening with Cisco or some other VPN service provider.
Virtual Privacy Networks improve your security and privacy as you browse the Internet, which is why people use them. Therefore if you cannot validate VPN security, the purpose of getting the VPN in the first place is defeated.
How do I get a VPN certificate?
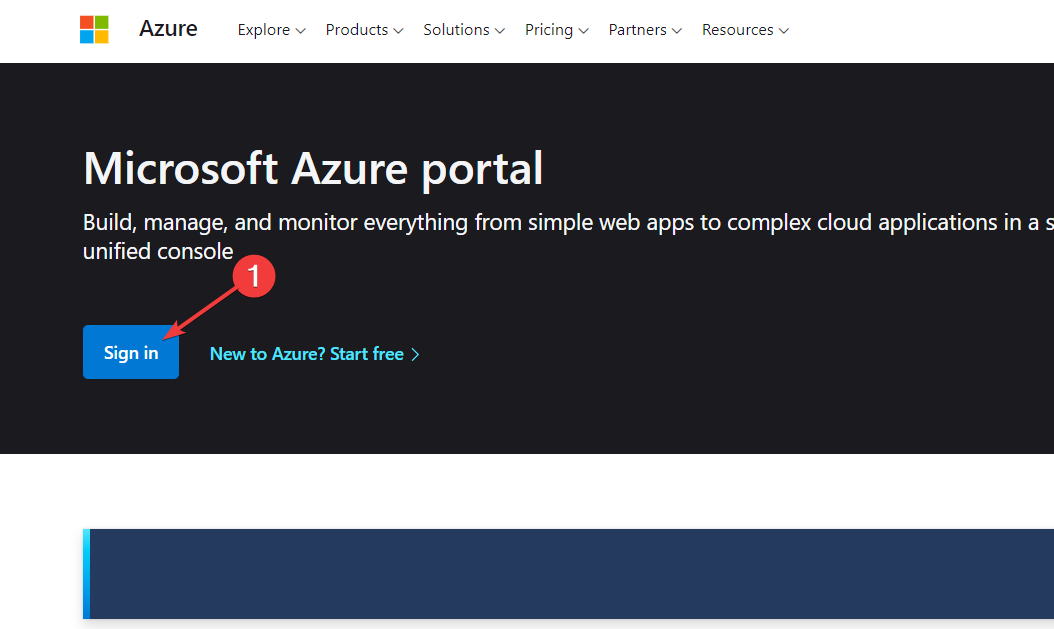
- Visit the Azure portal as an administrator.
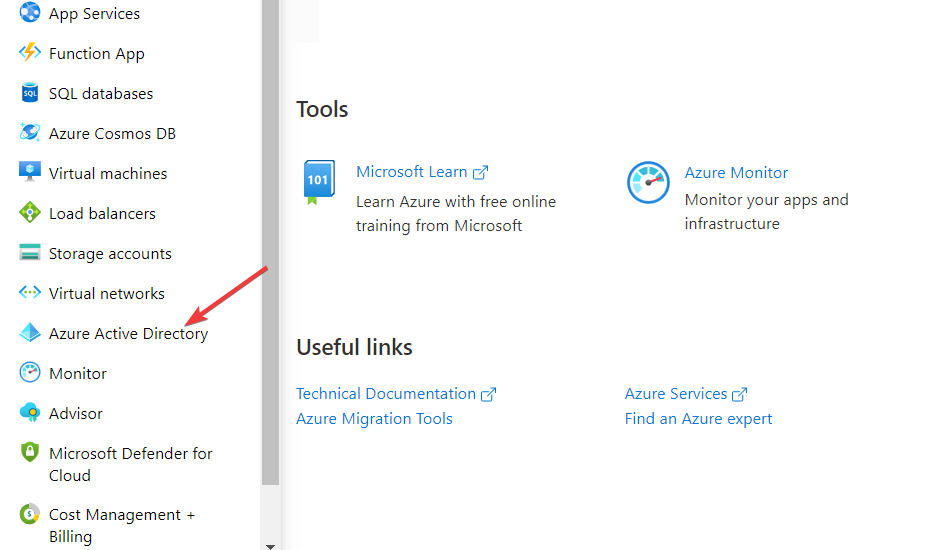
- Click on Azure Active Directory on the left menu.
- Go to the Manage section in the Azure Active Directory menu and click on Security.
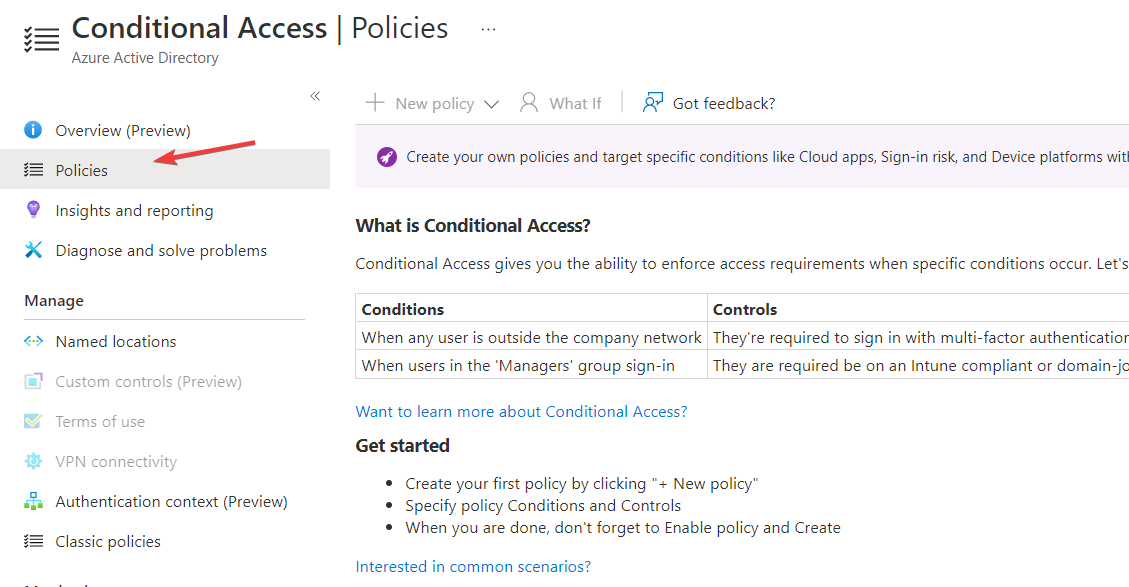
- Click on the Protect section on the Security page and select Conditional Access.
- Go to the Policies page on the Conditional access page and click on VPN Connectivity.
- Click New Certificate and generate one for yourself.
To have access to generate a new VPN certificate, you need to create an Azure Microsoft account. Microsoft has a free trial that you can use to gain access before you need to pay.
When your VPN certificate expires, you need to update it. If you do not update your VPN certificate, you lose security and become exposed to threats that make your private and classified information vulnerable.
How do I update my VPN certificate?
In order to update your VPN certificate, you will have to enter the Certificates – Local Computer app from your system and tweak your current certificate.
For an in-depth, step-by-step guide on how to achieve this, follow the second solution from the list below in order to update your VPN certificate.
Do VPN certificates expire?
VPN certificates are issued with an expiration date for the sake of increased security. After that date has passed, the certificates must be updated with fresh ones.
There is a validity period of three years attached to the VPN certificates that were issued by both the Internal RSA CA for Gateways and the Internal ECDSA CA.
How do I fix VPN validation failure?
1. Check the validity of your VPN certificate
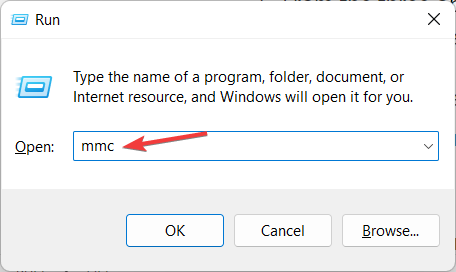
- Press the Windows and R keys on your device to open the Run tab and type in mmc then press Enter.
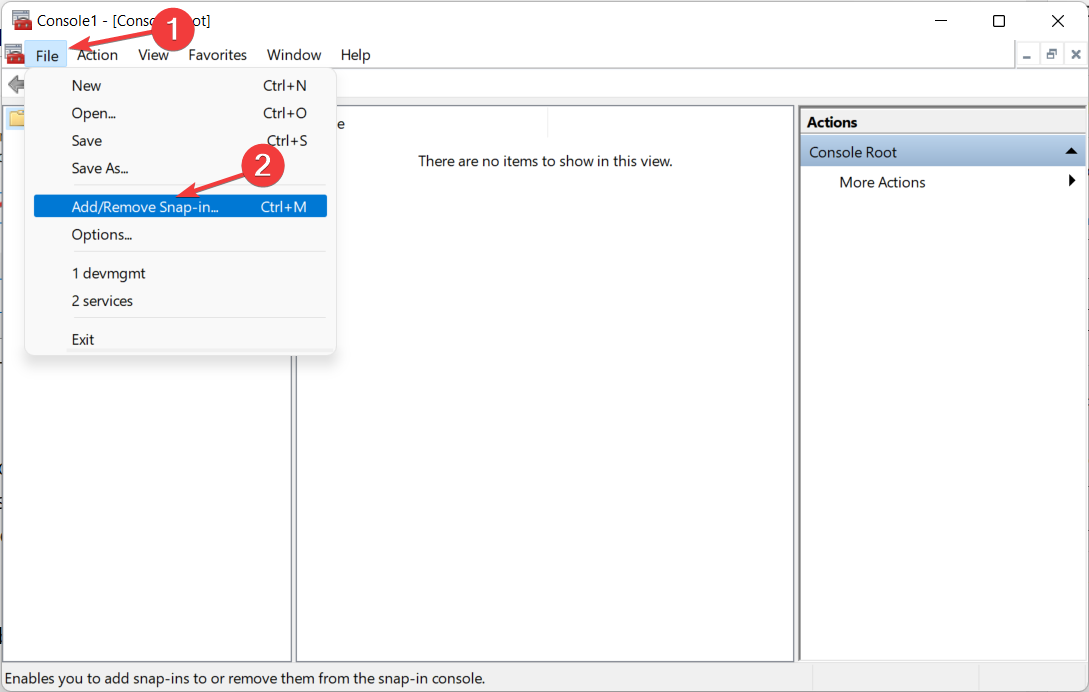
- Click on the File option in the top right corner and select Add/Remove Snap-in from the drop-down menu.
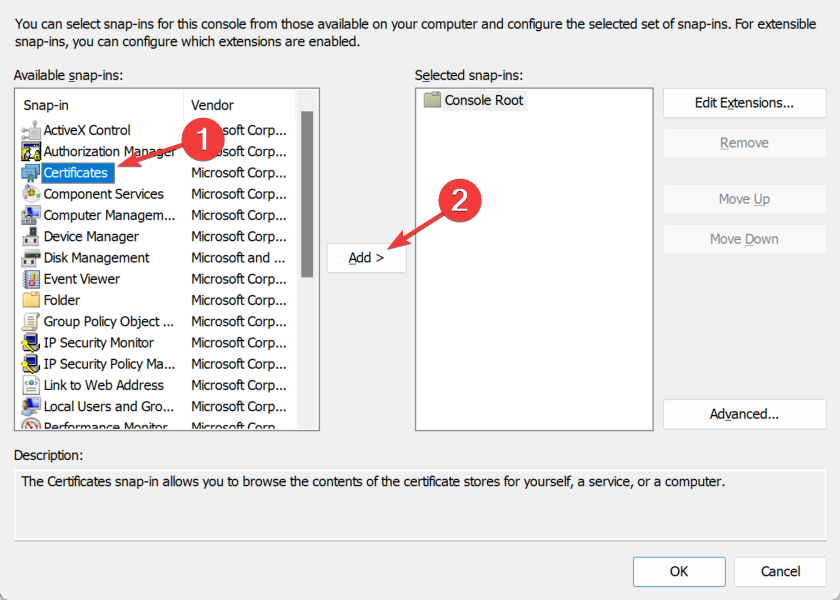
- Choose Certificates from the Available snap-ins section then click on the Add button.
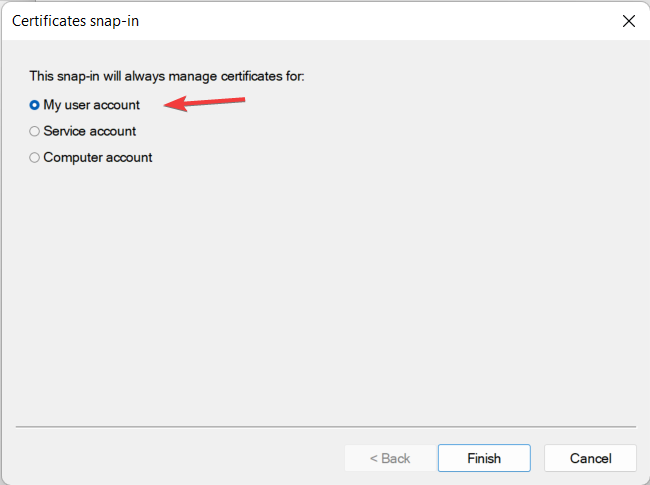
- From the three options, click on My User Account.
These steps will enable you access to the current User certificates to see the certificate that you have in the system. When you double-click on the certificate, you can see the details, which include the validity and expiry date.
After you check, and find that your VPN certificate may have expired, proceed to renew it.
- Fix: WiFi certificate error on Windows 10 [Can’t Connect]
- Set up a Windows 11 Ikev2 VPN in record time and with ease
- FIX: Cannot connect to L2TP VPN on Windows 10/11
2. Update your VPN certificate
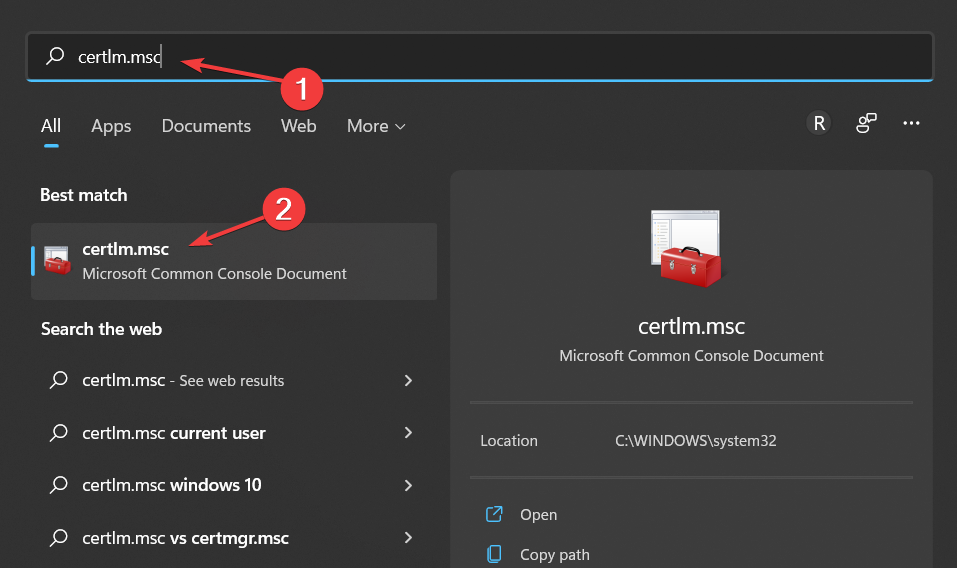
- Click on the magnifying glass icon from your Taskbar then type in certlm.msc and select the topmost result.
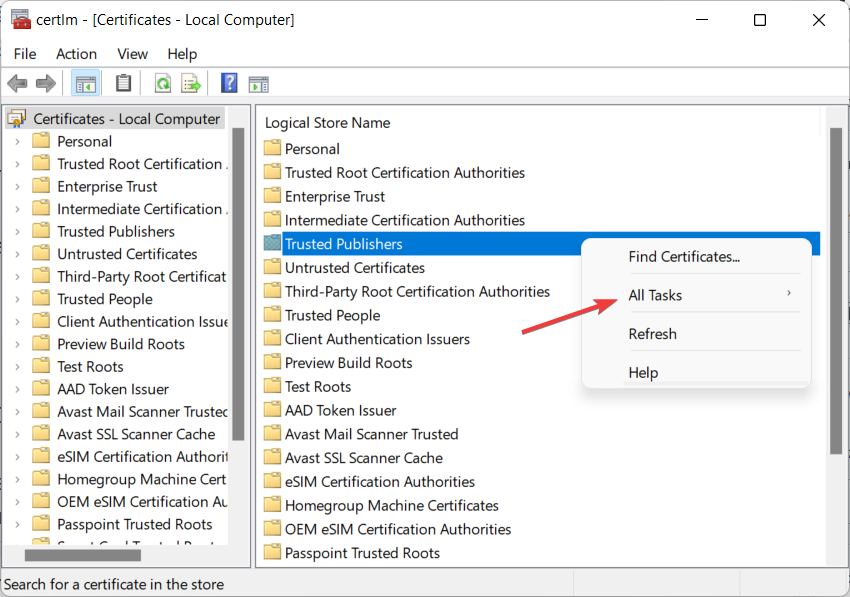
- Right-click on the open space and select All Tasks.
- Click on Advanced Operations and select Create Custom Request.
- Select Proceed without enrollment and continue with the onscreen steps.
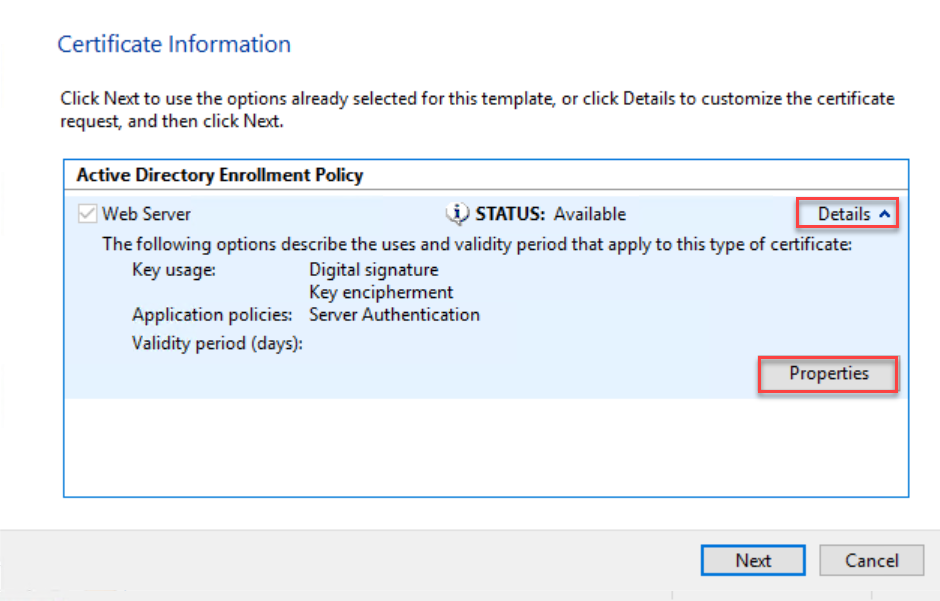
- Click on the arrow next to Details and select Properties from the drop-down menu.
- Name the certificate a title that is easy to remember then click on Subject and select common name from the Full QDN drop-down menu.
- Enter the Fully Qualified Domain Name and click Add followed by Next.
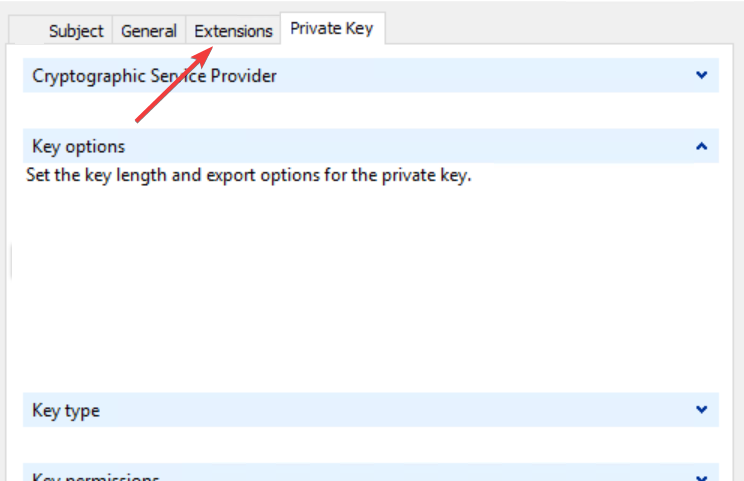
- Go back to Properties and select the Extensions tab.
- Select Extended Key Usage, and click on Server Authentication and Add.
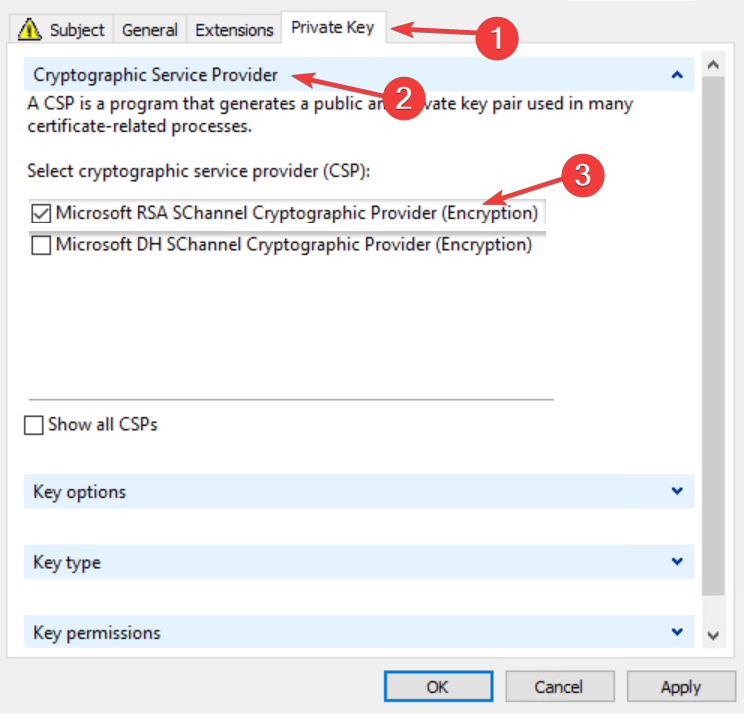
- Click on the Private Key tab then select Cryptographic service provider and check the Microsoft RSA or Microsoft DH option as you wish.
- Save everything by clicking on Apply and OK then click on the magnifying glass icon on your Taskbar and type PowerShell. Finally, click on the topmost result in order to open it.
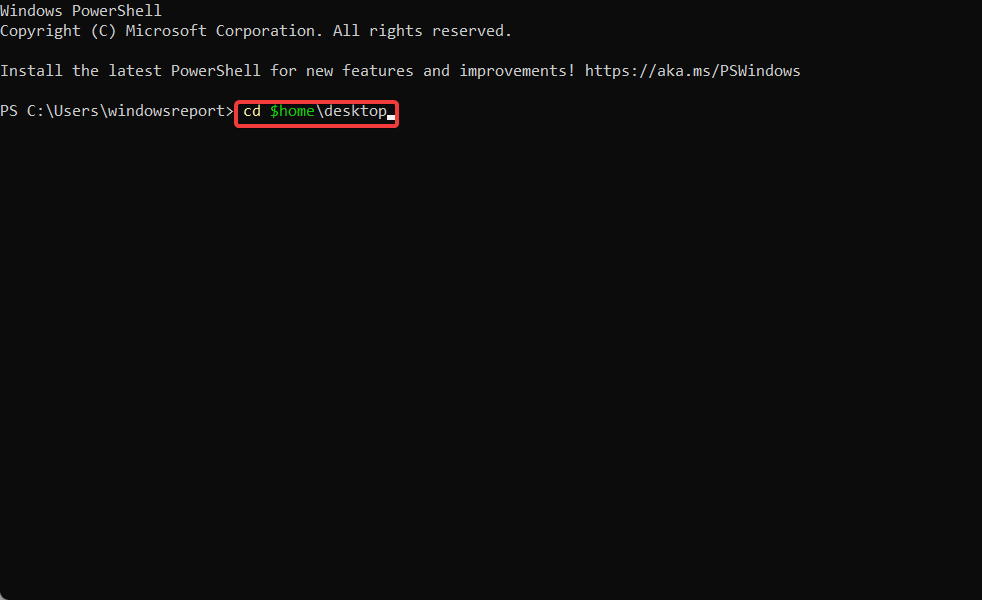
- Type in the following command and press Enter:
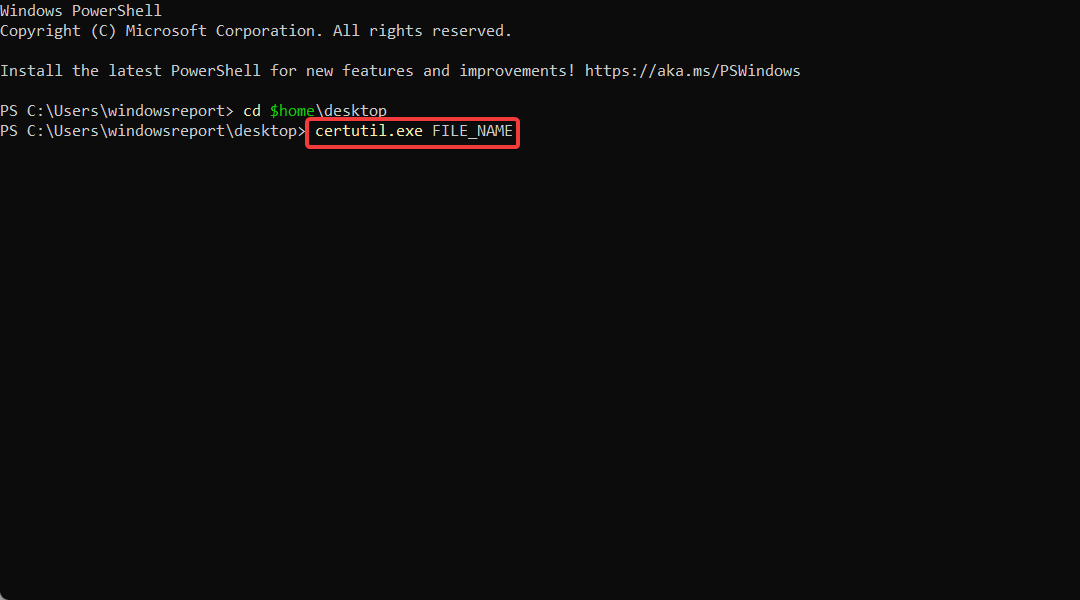
cd $homedesktop - On the next line, type in the following command and replace the FILE_NAME with your certificate’s name:
certutil.exe FILE_NAME - Copy the content of the file and submit it to your public certification authority for signing.
To fix certificate validation failure VPN Cisco, and certificate validation failure VPN anyconnect, you have to first verify that the hostname and host address are still valid and then check if the certificate has expired before you proceed to install a new certificate or update the existing one.
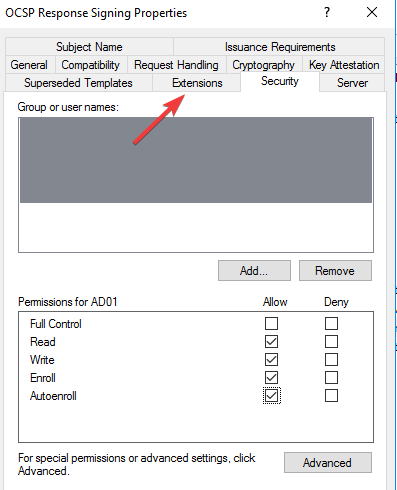
3. Turn on OCSP Nonce on the Windows server
- Press the Windows and R keys to open a command bar and type certlm.msc to open the Certificate Service Management Console.
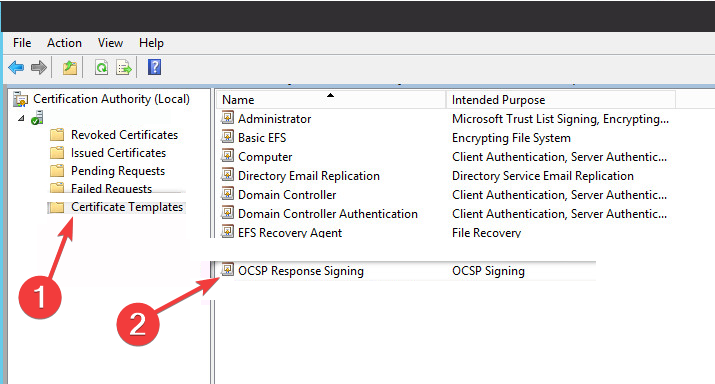
- Select Certificate template from the left menu and click on Manage then find OCSP Respond Signing from the drop-down menu and select it.
- Right-click on it and select Properties.
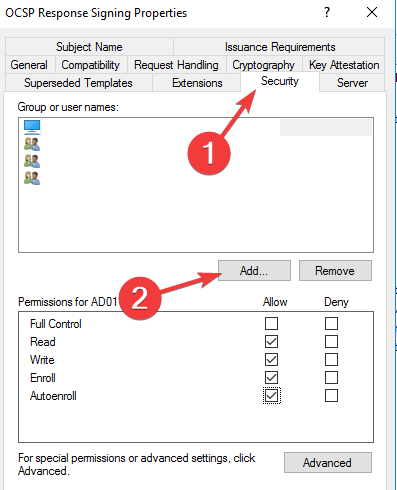
- Click on the Security tab and add the server that will be hosting the OCSP services.
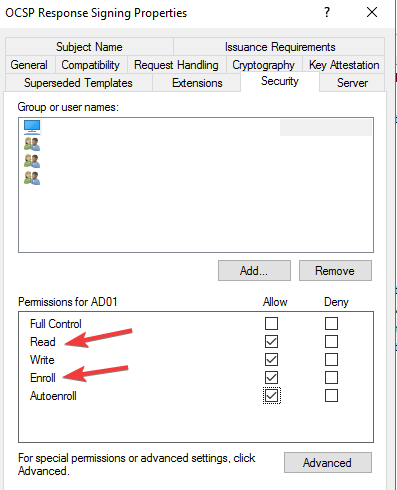
- Check Read and Enrol then go back to Certificate template. Click on New, select Certificate Template to issue, and choose OCSP signing.
- Click on the certificate server and select Properties.
- Select the Extension tab and choose Authority Information Access. Select the URL of the server and click on Add.
- Go to the dashboard of the server manager of the OCSP service and click on Add roles and features.
- Check Active directory services and select Role services. Uncheck Certification Authority and check Online Responder.
- Launch the Online Responder management console.
OCSP is Online Certificate Status Protocol, and it is a method that browsers use to ensure that a security certificate is valid. Enabling OCSP service nonce protects secure network communication.
Microsoft Windows uses RFC 5019 while Cisco AnyConnect VPN ASA uses RFC 2560. This disparity causes VPN validation failure, and as such needs fixing.
When OpenVPN certificate verification failed and VPN certificate validation failure occurs, these are the steps that you can follow to rectify them.
Also, for IBM VPN certificate validation failure, there is a renew certificate application in the IBM store that can help you with renewing your certificate if it is outdated.
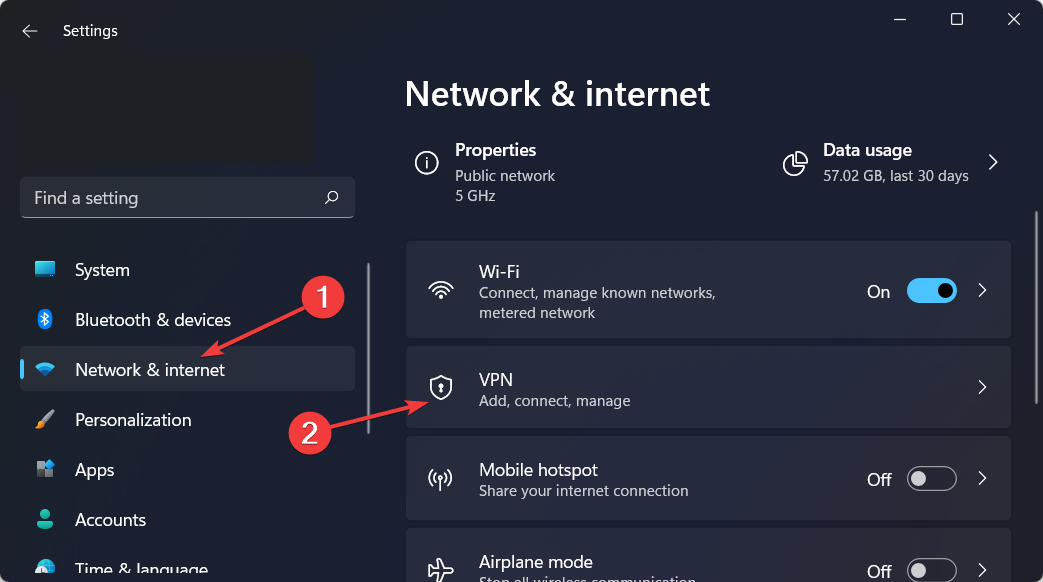
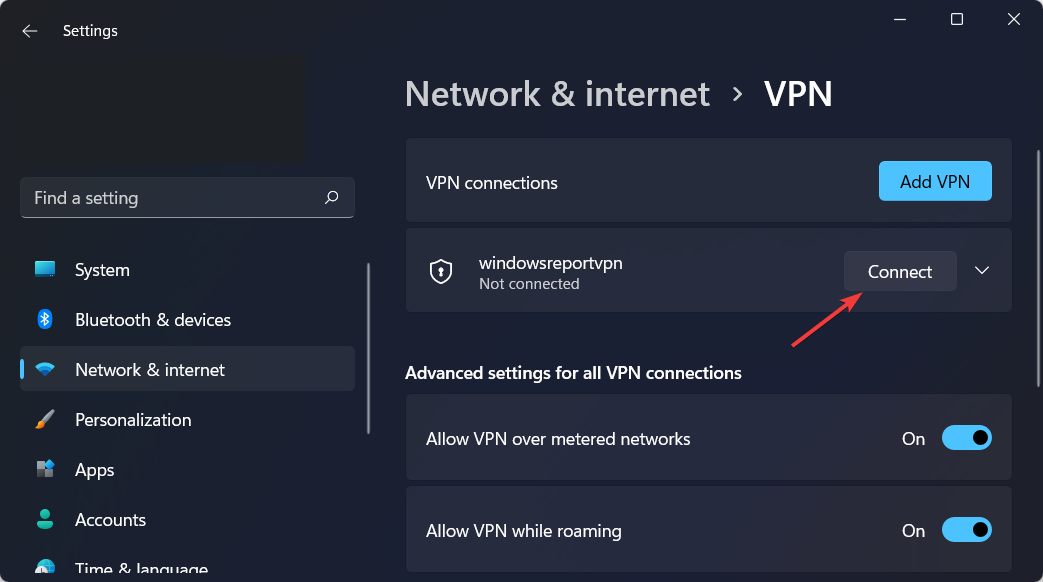
How do I add a VPN certificate to Windows 10/11?
- Open Settings by holding Windows and I together then go to Network and Internet followed by VPN.
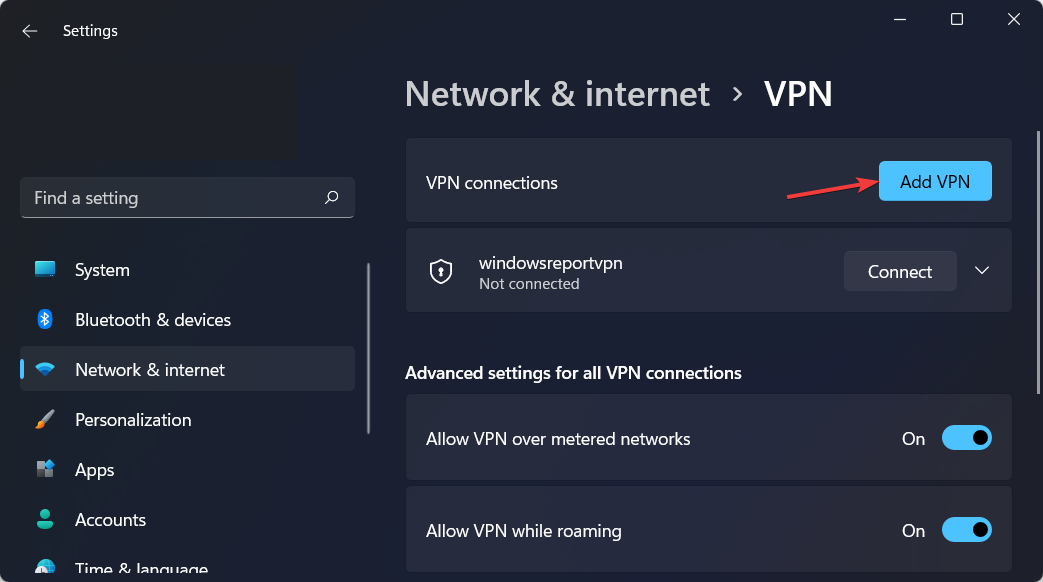
- Click on Add VPN.
- On the dropdown menu, select Windows built-in as the VPN provider.
- Type in a name for the VPN connection in the Connection name field.
- Get the server name and address from the provider and type it into the Server address field.
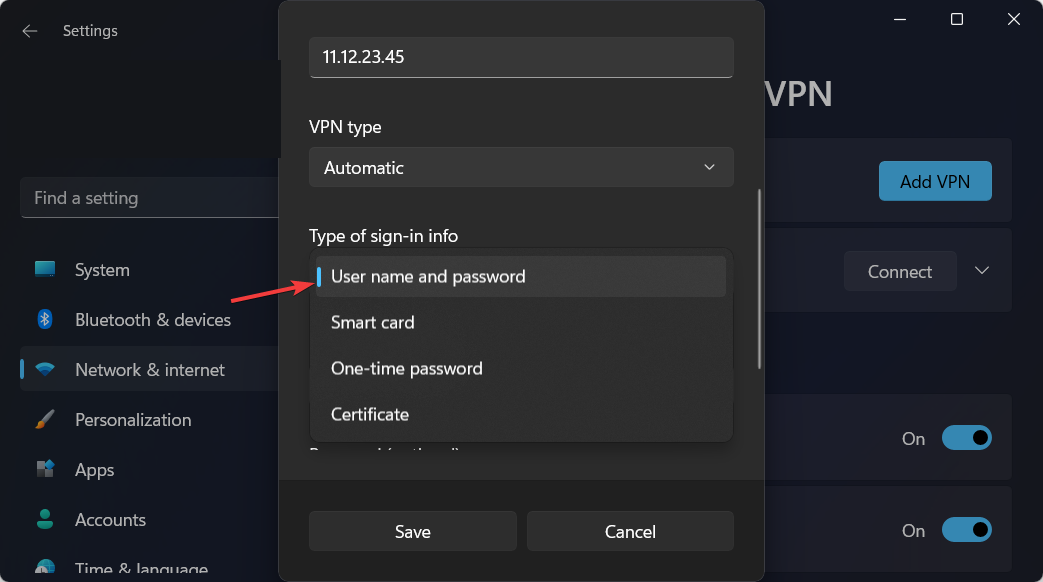
- In the Type-of-sign-in info bar, type in the one your VPN provider uses and click on Save.
- When the name of the VPN appears, connect to it.
Is there any good 3rd party VPN for business?
There is another security method to protect all your business data and avoid certificate validation failure for your VPN protection.
You can use the Perimeter 81 as a Zero Trust Application Access software and secure any sensitive data from public use. This way, you guarantee private communication with IPSec or WireGuard technology.
Plus, it provides safer digital support against data leaking or cyber threats with access by role, a cloud-based interface, or monitoring tools.
⇒ Get Perimeter 81
In conclusion, VPN is vital because of the protection and security that users get from it. These steps will fix the validation failure that pops up. However, if these do not work, you can disconnect completely and start a new connection.
Check out our post with the five best VPNs for Windows 11, after 3 months of usage and tests, to decide which one to get on your devices.
We hope our guide proved to be useful to you. Don’t hesitate to share your thoughts with us in the comments section below. Thanks for reading!
error parsing certificate : X509 — The date tag or value is invalid
This is not a bug in OpenVPN but is because of a faulty certificate. See this detailed forum post for more info.
certificate verification failed : x509 — certificate verification failed, e.g. crl, ca or signature check failed
This is an error that tells you that the certificate could not be verified properly. This can occur for example if you are using an MD5 signed certificate. With such a type of certificate, the security level is so low, that the authenticity of the certificate simply cannot by any reasonable means be assured. In other words, it could very well be a fake certificate. The solution is to use a certificate not signed with MD5, but with SHA256 or better. You can find more information in the MD5 signature algorithm support section.
digest_error: NONE: not usable
This can occur if you specify auth none and also tls-auth in your client profile. This occurs because tls-auth needs an auth digest, but none was specified. There’s a straightforward fix: just remove the tls-auth directive, since it can’t be enabled anyway unless you have anything other but ‘none’ in the auth directive.
SSL — Processing of the ServerKeyExchange handshake message failed
There’s a good chance this may be related to using older versions of OpenVPN/OpenSSL on the server side. Some users have solved this issue by updating their OpenVPN and/or OpenSSL software on the server side.
BIO read tls_read_plaintext error: error:1408A0C1:SSL routines:SSL3_GET_CLIENT_HELLO:no shared cipher
This is usually remedied by going to the OpenVPN Preferences menu and selecting «Force AES-CBC ciphersuites».
There are more general OpenVPN client connectivity error messages and solutions available.
-
-
August 16 2011, 04:08
- IT
- Cancel
Захотел запустить еще один OpenVPN сервер под Ubuntu для экспериментов на кошках.
Уперся в ошибку «VERIFY ERROR: depth=0, error=unable to get local issuer certificate» результатом которой было «TLS Error: TLS handshake failed».
Теперь по-порядку
Так как хотел создать новый CA, то перекинул easy-rsa в домашнюю папку. Создал новый конфиг файл в папке /etc/openvpn для запуска второго сервера с указанием новой папки сертификатов. В vars так же подправил пути.
Делаю:
source ./vars
./clean-all
./build-ca
./build-dh
./build-key-server server
./build-key zhmak
openvpn —genkey —config /etc/openvpn/openvpn_2.conf —secret ta.key
После этого сервер запускается. Только вот клиенты подключиться не могут. Выдают «VERIFY ERROR: depth=0, error=unable to get local issuer certificate» и реконнектятся бесконечно.
В инете эта ошибка как-то вяло обсуждается. Даже встречаются предложения создать CA на другой машине. А ответ плавал на поверхности.
Так как ключи сервера и клиентов создаются и появляются в папке, то подозрения пали на генератор ключа TLS. Сначала подумал, что проблема в файле конфига. Указал параметром командной строки —config — не помогло. Потом обратил внимание на то, что в папке certs уже работающего сервера стали появляться файлы, созданные во время конфигурации нового CA.
Начал шерстить конфиги в easy-rsa. В openssl.cnf был прописан путь к папке со старыми сертификатами.
То есть если создается еще один CA с папкой сертификатов отличной от дефолтной, то помимо редактирования vars надо еще и openssl.cnf заглянуть.
Иначе «VERIFY ERROR: depth=0, error=unable to get local issuer certificate» и красноглазие обеспечены 
This topic has been deleted. Only users with topic management privileges can see it.
I’m having issues with my OpenVPN site configurations after upgrading to 2.5.0 (reproduced on two pfsense boxes). I previously have not had any issues while upgrading with previous pfsense versions. It seems that certificate verification may be broken or working differently in 2.5.0 — I can connect successfully only after disabling certificate verification.
For my setup, I have a self-signed root CA, intermediate CA (signed by the root CA), and server/user certificates (signed by the intermediate CA). The root CA, intermediate CA, and server/user certificates are all imported into pfsense. My certificate depth verification is set to Two (Client+Intermediate+Server). The peer certificate authority is set to the intermediate CA. I get the following logs when attempting to connect from a client (as well as a pfsense to pfsense site-to-site setup):
Feb 21 13:16:20 openvpn 99514 <user ip>:51909 VERIFY WARNING: depth=0, unable to get certificate CRL: <user cert>
Feb 21 13:16:20 openvpn 99514 <user ip>:51909 VERIFY WARNING: depth=1, unable to get certificate CRL: <intermediate cert>
Feb 21 13:16:20 openvpn 99514 <user ip>:51909 VERIFY WARNING: depth=2, unable to get certificate CRL: <root cert>
Feb 21 13:16:20 openvpn 99514 <user ip>:51909 VERIFY SCRIPT OK: depth=2, <root cert>
Feb 21 13:16:20 openvpn 99514 <user ip>:51909 VERIFY OK: depth=2, <root cert>
Feb 21 13:16:20 openvpn 99514 <user ip>:51909 WARNING: Failed running command (--tls-verify script): external program exited with error status: 1
Feb 21 13:16:20 openvpn 99514 <user ip>:51909 VERIFY SCRIPT ERROR: depth=1, <intermediate cert>
Feb 21 13:16:21 openvpn 99514 <user ip>:51909 SSL alert (write): fatal: unknown CA
Feb 21 13:16:21 openvpn 99514 <user ip>:51909 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Feb 21 13:16:21 openvpn 99514 <user ip>:51909 TLS_ERROR: BIO read tls_read_plaintext error
Feb 21 13:16:21 openvpn 99514 <user ip>:51909 TLS Error: TLS object -> incoming plaintext read error
Feb 21 13:16:21 openvpn 99514 <user ip>:51909 TLS Error: TLS handshake failed
It seems like there is a verification of the intermediate CA at depth=1 which fails with unknown CA. I’m not sure what is normally done in previous versions of pfsense.
@joshh
I have observed same failure to connect after updating to pfsense 21.02 and OpenVPN 2.5.0. I also use a similar setup where I have a self generated root CA, intermediate CA with server/client certs signed by the intermediate CA.
I don’t have a copy of the previous openvpn server config generated by pfsense, but it appears that pfsense enabled an additional feature tls-verify that wasn’t used in previous version of pfsense. After upgrading pfsense, the «Certificate Depth» option was set to «Two (Client + Intermediate + Server)».
This results in following config line in the generated config file /var/etc/openvpn/server1/config.ovpn:
tls-verify «/usr/local/sbin/ovpn_auth_verify tls ‘myhostname.mydomain.com’ 2»
One would have thought this would work since both client and server are signed by the same intermediate cert. But as with your failure, the script returns a non zero value causing openvpn to fail the connection. The script «/usr/local/sbin/ovpn_auth_verify» appears to be maintained by pfsense.
I’ve not yet spent anytime troubleshooting the script «/usr/local/sbin/ovpn_auth_verify» to determine why it’s failing with my self generated root CA and intermediate cert. As a workaround, disabling «Certificate Depth» by setting to «Do Not Check» allows clients to connect until able to resolve why the tls-verify script is failing.
I think I may have found cause of failure. The tls-verify cmd calls «/usr/local/sbin/ovpn_auth_verify» which in turn calls following «/usr/local/sbin/fcgicli»
The fifth arg ($5) to ovpn_auth_verify looks to be the subject of the root CA (passed by openvpn). I found that if the CN of the this subject contains a space (the last element of subject), the call to fcgicli fails with error message «Something wrong happened while reading request». I suspect that fcgicli fails the parsing of key value pairs if the last element of the subject contains a space. Adding some escapes/quotes to the command in «/usr/local/sbin/ovpn_auth_verify» seems to fix. If I set cert depth to 2 (or more) with fix applied, the RESULT is «OK» and passes. If I set to depth of 1, it fails as expected with «FAILED».
> diff ovpn_auth_verify ovpn_auth_verify.fixed
27c27
< RESULT=$(/usr/local/sbin/fcgicli -f /etc/inc/openvpn.tls-verify.php -d "servercn=$2&depth=$3&certdepth=$4&certsubject=$5&serial=$serial&config=$config")
---
> RESULT=$(/usr/local/sbin/fcgicli -f /etc/inc/openvpn.tls-verify.php -d "servercn=$2&depth=$3&certdepth=$4&certsubject=\"$5\"&serial=$serial&config=$config")
Searching bug reports, seems that problem may be more of string length rather than whitespace in CN (my testing also confirms). The length of my subject name 137 chars which looks to be a little larger than length that causes problem per bug report.
See bug report #10560 and #4521.
@gribnut ‘s fix didn’t work for me, however …
For some reason, OpenVPN confuses things by having TWO clients: «OpenVPN Connect v3», (The one you download from openvpn.net), «OpenVPN GUI v11», which is what PFSense uses when you download the full client installer from «Client Export».
Since some clients have more than one VPN profile they need to connect to, and not everyone is using PFSense with their fancy bundled deploy, I use the OpenVPN Connect client. It’s got a nicer UI that’s easier to use for the end-users plus has a nice traffic graph. It’s also the one readily downloadable from openvpn.net.
PFSense seems to have broken the OpenVPN Connect client. If you use the crappy client PFSense bundles with Client Export it works for me.
@gribnut
Same problem here, same fix as you suggested.
CA CN is «Home CA» (note the space) and client is an old OpenVPN v2.3.4 (with the associated network-manager-openvpn plugin v0.9.10) on a Debian Jessie.
pfSense v2.4.5p1 has no issue, upgraded to pfSense v2.5.0 it is impossible to connect with the «client certificate verification failed» error already reported in the starting post.
Applied your fix (\"$5\" in the verification script) and everything works again as expected for the old Debian Jessie.
Android phone with «OpenVPN for Android» v0.7.21 has no issue whatsoever, before or after the fix, thus the issue seems also related to the OpenVPN client used.
For sure the /usr/local/sbin/ovpn_auth_verify script distributed with pfSense v2.5.0 is buggy: v2.4.5p1 had no problem at all.
@gribnut This fix seems to have solved a similar problem I have been having with TLS/SSL OpenVPN connections.
Converted a stable 2.4.5p1 to 2.4.5p1 pair to 2.5.0 — 2.5.0 and lost the existing S2S OpenVPN link. I rebuilt the CA/Certs for Server and Client under 2.5.0 and got the link back.
Later I realized the Server had a secondary RoadWarrior setup that was also now failing previously stable clients. Logs pointed to failure to find CA.
Tried your fix and Voila it all came back to life.
Looks like a definite bug here, what’s interesting is my CA common name has no spaces as far as I can tell.
It’s «811pow-ovpn-rdwar-ca» although I’m not sure if there’s a leading space buried in there. I’ve used an OpenSSL command to dump the subject, but it’s not clear if the output adds a space to the entries as they are printed.
@divsys
I was a bit off when I though was due to space as removing space appeared to fix problem. Looks like the root problem is length of string (all key value pairs) for -d arg to fcgicli. If combination of server hostname (as used by client), cert subject and serial number is too long, fcgicli bombs and returns «Something wrong happened while reading request». Guessing the length of various values in your environment also exceed what works for fcgicli.
Looks like bug #4521 was reported some time ago and no indication of when will be fixed. I added comment to confirm it is still a problem in hopes it gets fixed in near future. Fortunately, I don’t have a dependency upon limiting cert depth.
@fr3ddie
I forgot to mention that anytime you save openvpn config, it will write over any changes made to /usr/local/sbin/ovpn_auth_verify. I’ve not looked to see which file updates /usr/local/sbin/ovpn_auth_verify, so I just disabled cert depth check altogether until long arg to fcgicli is resolved.
Just guessing, but suspect that reason one of your clients might work whereas as others don’t is due to length of cert subject for client. The tls_verify will iterate through entire chain (depending up configured depth to search). The length of string for subject (the entire subject not just CN) could end up causing arg passed to fcgiclie to exceed value that works.
@gribnut Thanks for your help in tracking this down. Makes me much more hopeful about converting up to 2.5.0.
@gribnut
So, does disabling that depth check allow the VPN to work? Currently, I can get it to work on the same LAN, but not from outside the firewall.
@jknott
Disabling depth check is only a workaround if the tls-verify script is failing. Won’t fix other problems. Recommend checking your logs to see cause of failure.
@gribnut Hmmmmm, I think there’s a bit more to this one than meets the eye.
On ahunch, I backed out the code change to ovpn_auth_verify back to factory.
Roadwarrior links still good
Restarted the RoadWarror server process
Roadwarrior links still good
Rebooted the remote pfSense box
Roadwarrior links still good
So now I ‘m at the point that I can’t make it fail anymore after backing all my changes out <sigh>
One thing to note in all this — none of my OpenVPN Servers do more than a depth check of 1.
@gribnut I just upgraded to 2.5 today and noticed right away that I couldn’t connect to OpenVPN.
Once I set Certificate Depth to Do not check it worked again.
@gribnut
thank you for your information.
But there is still something that I can’t understand: how a length issue on the certificate subject can be fixed by just enclosing the subject in apexes?
What I believe is that, probably, there is more than one issue here in fcgicli: an issue linked to the subject length and maybe another issue linked to «special» characters (spaces? slashes?) included in the certificate subject that is fixed by simply enclosing the subject between apexes.
@nycspud Do you know what error messages OpenVPN was logging while it was failing?
I’d be curious what happens if you set Certificate Depth back to Level one, does OpenVPN start failing again or is it «magically» OK?
As noted below, there seems to be an internal interaction were not catching that trips the Certficate checks and causes OpenVPN to fail. My experiences so far have been odd in that I’ve seen hard fails right after an upgrade but once I managed to massage the certificate depth or the ovpn_auth_verify «fix», I could no longer replicate the issue by backing out the fix.
@divsys Yes, setting Certificate Depth = 1 or higher causes it to fail.
With Certificate Depth = 1 or higher
Feb 23 07:10:48 openvpn 21518 xx.xx.xx.xx:53817 WARNING: Failed running command (—tls-verify script): external program exited with error status: 1
Feb 23 07:10:48 openvpn 21518 xx.xx.xx.xx:53817 VERIFY SCRIPT ERROR: depth=1, C=US, ST=XX, L=XX, O=XX, emailAddress=XX@XX.XX, CN=ovpn
Feb 23 07:10:48 openvpn 21518 xx.xx.xx.xx:53817 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Feb 23 07:10:48 openvpn 21518 xx.xx.xx.xx:53817 TLS_ERROR: BIO read tls_read_plaintext error
Feb 23 07:10:48 openvpn 21518 xx.xx.xx.xx:53817 TLS Error: TLS object -> incoming plaintext read error
Feb 23 07:10:48 openvpn 21518 xx.xx.xx.xx:53817 TLS Error: TLS handshake failed
Feb 23 07:10:48 openvpn 21518 xx.xx.xx.xx:53817 SIGUSR1[soft,tls-error] received, client-instance restarting
On the client side when Certificate Depth = 1 or higher
2021-02-23 07:11:48 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
2021-02-23 07:11:48 TLS Error: TLS handshake failed
2021-02-23 07:11:48 SIGUSR1[soft,tls-error] received, process restarting
2021-02-23 07:11:48 MANAGEMENT: >STATE:1614093108,RECONNECTING,tls-error,,,,,
2021-02-23 07:11:48 Restart pause, 5 second(s)
I only have a self signed root CA, and no intermediate CA.
If it is from fcgicli, you might try the original change for #9460 (before it was fixed properly last time) by using the System Patches package and then create an entry for ce76f299853dccb036de229f08a30013593c98fd to apply the change. It will use php-cgi instead of fcgicli.
@fr3ddie
I agree on skepticism that surrounding one of the key values with quotes in key/value pairs submitted to fcgicli actually fixes the problem. It’s possible that while it returns OK using workaround I listed it could cause a different behavior that may or may not work for accurately detecting cert depth. Since saving openvpn config changes overwrites ovpn_auth_verify anyway, I just went with workaround to disable cert depth check until (or if) issue is resolved with fcgicli and lengthy args to -d from bug reported in redmine.
@gribnut I tried your fix and it worked for me. (I’m on pfSense 2.5.0-RELEASE)
Thank you
I tried the patch on pfSense 2.5.0-RELEASE also. No change. PIA VPN connection will not connect.
Feb 24 13:45:36 openvpn 31850 Restart pause, 5 second(s)
Feb 24 13:45:36 openvpn 31850 SIGUSR1[soft,tls-error] received, process restarting
Feb 24 13:45:36 openvpn 31850 TCP/UDP: Closing socket
Feb 24 13:45:36 openvpn 31850 TLS Error: TLS handshake failed
Feb 24 13:45:36 openvpn 31850 TLS Error: TLS object -> incoming plaintext read error
Feb 24 13:45:36 openvpn 31850 TLS_ERROR: BIO read tls_read_plaintext error
Feb 24 13:45:36 openvpn 31850 OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
Feb 24 13:45:36 openvpn 31850 VERIFY ERROR: depth=1, error=self signed certificate in certificate chain: C=US, ST=CA, L=LosAngeles, O=Private Internet Access, OU=Private Internet Access, CN=Private Internet Access, name=Private Internet Access, emailAddress=secure@privateinternetaccess.com, serial=11996199170155461251
PIA suggested rolling back OpenVPN from 2.5 to 2.4.
Any suggestions?
Thanks.
@wtw said in OpenVPN 2.5.0 Certificate Verification Fails:
I tried the patch on pfSense 2.5.0-RELEASE also. No change. PIA VPN connection will not connect.
The problem in this thread is for OpenVPN servers on pfSense, not clients. Your problem is unlikely to be related. Start a new thread for your issue if you haven’t already.
As @jimp noted, the failure of cert depth check with long cert subject name is due fcgicli inability to parse long key/value strings. I have verified that replacing fcgicli with php-cgi as noted in patch for #4521 ( and #9460 ) resolves. When using php-cgi, cert depth check works as expected with my self generated cert, intermediate and root CA.
@gribnut said in OpenVPN 2.5.0 Certificate Verification Fails:
As @jimp noted, the failure of cert depth check with long cert subject name is due fcgicli inability to parse long key/value strings. I have verified that replacing fcgicli with php-cgi as noted in patch for #4521 ( and #9460 ) resolves. When using php-cgi, cert depth check works as expected with my self generated cert, intermediate and root CA.
I tried the suggestion you provded «The fifth arg ($5)» above. No change.
I tried the patch #9460; ce76f299853dccb036de229f08a30013593c98fd as suggested. No change.
I started a new topic: pfSense 2.5.0-RELEASE OpenVPN Cert bug
What worked was creating a new self-signed cert using the same data. The difference in the backup XML is provided there.
Is patch #4521 different than #9460?
If the patch in only for an OpenVPN server, then this would be expected.
@jimp said in OpenVPN 2.5.0 Certificate Verification Fails:
If it is from fcgicli, you might try the original change for #9460 (before it was fixed properly last time) by using the System Patches package and then create an entry for
ce76f299853dccb036de229f08a30013593c98fdto apply the change. It will use php-cgi instead of fcgicli.
I had the same issue immediately after upgrading from 2.4.5p1 to 2.5.0, and this fix did not work for me either. However, this was because it fixes the wrong thing.
The commit above modifies /usr/local/sbin/ovpn_auth_verify_async, while OpenVPN actually calls /usr/local/sbin/ovpn_auth_verify. I changed this script in the same way the commit does:
- change
/usr/local/sbin/fcgiclito/usr/local/bin/php-cgi - remove the
-din front of the query string
This worked; OpenVPN now again allows incoming connections.
Here is the patch (apply with strip 0 in /usr/local/sbin) for reference:
--- ovpn_auth_verify.orig 2021-03-07 18:20:59.312509000 +0000
+++ ovpn_auth_verify 2021-03-07 18:21:42.060270000 +0000
@@ -24,14 +24,14 @@
for check_depth in $(/usr/bin/seq ${3} -1 0)
do
eval serial="$tls_serial_${check_depth}"
- RESULT=$(/usr/local/sbin/fcgicli -f /etc/inc/openvpn.tls-verify.php -d "servercn=$2&depth=$3&certdepth=$4&certsubject=$5&serial=$serial&config=$config")
+ RESULT=$(/usr/local/bin/php-cgi -f /etc/inc/openvpn.tls-verify.php "servercn=$2&depth=$3&certdepth=$4&certsubject=$5&serial=$serial&config=$config")
done
else
# Single quoting $password breaks getting the value from the variable.
# Base64 and urlEncode usernames and passwords
password=$(echo -n "${password}" | openssl enc -base64 | sed -e 's_=_%3D_g;s_+_%2B_g;s_/_%2F_g')
username=$(echo -n "${username}" | openssl enc -base64 | sed -e 's_=_%3D_g;s_+_%2B_g;s_/_%2F_g')
- RESULT=$(/usr/local/sbin/fcgicli -f /etc/inc/openvpn.auth-user.php -d "username=$username&password=$password&cn=$common_name&strictcn=$3&authcfg=$2&modeid=$4&nas_port=$5")
+ RESULT=$(/usr/local/bin/php-cgi -f /etc/inc/openvpn.auth-user.php "username=$username&password=$password&cn=$common_name&strictcn=$3&authcfg=$2&modeid=$4&nas_port=$5")
fi
if [ "${RESULT}" = "OK" ]; then
—
Christian
I can only add that I was bitten by this issue, too.
What is interesting is that certificate verification failed for some users, but not for all.
CA CN contains spaces and user certificates contain spaces. And yet some users can use OpenVPN and some cannot. Disabling Certificate Depth verification fixed that.
I hope this gets classified as a bug and will be fixed in the future.
@shpokas
The initial assumption of having space in the cert Subject was a red herring. Problem is actually due to length of string passed to fcgicli for key value pairs. If the cert Subject was a long value, there was a good chance the command fcgicli would fail. As noted above, it is a known issue. See #4521 for more info and patch. The patch replaces fcgicli with php-cgi in script called by OpenVPN for cert depth check. php-cgi does not have issue with the longer string argument that includes cert Subject name. You can apply the patch as a temp fix until it is applied to future version of pfsense.
I can confirm this.
It is always the same thing: I googled and found do nothing
appropriate.
Than i dived into the things and figured out the length problem myself. Definitely, length is the problem. Reproducable on the commandline.
When googling again with fcgicli in the search, i found this thread.
Manually applied the patch and everthing works fine.
good day to all same problem i have after update pfsense to 2.5.1
this messages i recived in server
Jul 5 13:20:08 openvpn 90254 ip:43573 TLS Error: TLS handshake failed
Jul 5 13:20:08 openvpn 90254 ip:43573 TLS Error: TLS object -> incoming plaintext read error
Jul 5 13:20:08 openvpn 90254 ip:43573 TLS_ERROR: BIO read tls_read_plaintext error
Jul 5 13:20:08 openvpn 90254 ip:43573 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Jul 5 13:20:08 openvpn 90254 ip:43573 VERIFY ERROR: depth=0, error=unsupported certificate purpose: C=RO, ST=HD, L=MT, O=ITL, emailAddress=mail, CN=pfsmtsrv, OU=IT, serial=1
Jul 5 13:19:28 openvpn 90254 Initialization Sequence Completed
Jul 5 13:19:28 openvpn 90254 UDPv4 link remote: [AF_UNSPEC]
Jul 5 13:19:28 openvpn 90254 UDPv4 link local (bound): [AF_INET]ip:44442
Jul 5 13:19:28 openvpn 90254 /usr/local/sbin/ovpn-linkup ovpns4 1500 1622 ip 255.255.255.0 init
Jul 5 13:19:28 openvpn 90254 /sbin/ifconfig ovpns4 10.1.2.1 10.1.2.2 mtu 1500 netmask 255.255.255.0 up
Jul 5 13:19:28 openvpn 90254 TUN/TAP device /dev/tun4 opened
Jul 5 13:19:28 openvpn 90254 TUN/TAP device ovpns4 exists previously, keep at program end
Jul 5 13:19:28 openvpn 90254 WARNING: experimental option —capath /var/etc/openvpn/server4/ca
Jul 5 13:19:28 openvpn 90254 Initializing OpenSSL support for engine ‘devcrypto’
Jul 5 13:19:28 openvpn 90254 NOTE: the current —script-security setting may allow this configuration to call user-defined scripts
Jul 5 13:19:28 openvpn 90243 library versions: OpenSSL 1.1.1k-freebsd 25 Mar 2021, LZO 2.10
Jul 5 13:19:28 openvpn 90243 OpenVPN 2.5.1 amd64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Apr 5 2021
Jul 5 13:19:28 openvpn 90243 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless «allow-compression yes» is also set.
This messages is in client
Jul 5 13:24:23 openvpn 34328 UDPv4 link remote: [AF_INET]ip:44442
Jul 5 13:24:23 openvpn 34328 UDPv4 link local (bound): [AF_INET]ip:0
Jul 5 13:24:23 openvpn 34328 TCP/UDP: Preserving recently used remote address: [AF_INET]ip:44442
Jul 5 13:24:23 openvpn 34328 NOTE: the current —script-security setting may allow this configuration to call user-defined scripts
Jul 5 13:24:23 openvpn 34328 WARNING: No server certificate verification method has been enabled
Jul 5 13:24:18 openvpn 34328 SIGUSR1[soft,ping-restart] received, process restarting
Jul 5 13:24:18 openvpn 34328 [pfsmtsrv] Inactivity timeout (—ping-restart), restarting
Jul 5 13:22:13 openvpn 34328 UDPv4 link remote: [AF_INET]ip:44442
Jul 5 13:22:13 openvpn 34328 UDPv4 link local (bound): [AF_INET]ip:0
Jul 5 13:22:13 openvpn 34328 TCP/UDP: Preserving recently used remote address: [AF_INET]89.121.228.158:44442
Jul 5 13:22:13 openvpn 34328 WARNING: experimental option —capath /var/etc/openvpn/client2/ca
Jul 5 13:22:13 openvpn 34328 Initializing OpenSSL support for engine ‘devcrypto’
Jul 5 13:22:13 openvpn 34328 NOTE: the current —script-security setting may allow this configuration to call user-defined scripts
Jul 5 13:22:13 openvpn 34328 WARNING: No server certificate verification method has been enabled.
Jul 5 13:22:13 openvpn 34328 WARNING: using —pull/—client and —ifconfig together is probably not what you want
Jul 5 13:22:13 openvpn 34039 library versions: OpenSSL 1.1.1k-freebsd 25 Mar 2021, LZO 2.10
Jul 5 13:22:13 openvpn 34039 OpenVPN 2.5.1 amd64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Apr 5 2021
Jul 5 13:22:13 openvpn 34039 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless «allow-compression yes» is also set.
-
-
rules
Frequent Visitor
- Posts: 65
- Joined: Tue Feb 19, 2019 12:10 pm
- Location: Cape Town, South Africa
OVPN Certificate Issue
Fri Nov 13, 2020 11:11 am
Hi All
I’ve got a router set-up as OVPN server with all the corresponding certificates (which I created locally on the router) and I’ve connected about 20 remote routers to it successfully.
I’m now trying to configure my Windows 10 machine to also use OpenVPN but it refuses to connect, complaining about the certificates. I’ve created new certificates and also tried existing ones but it’s not happy.
Connection looks good till it starts with this …
2020-11-13 10:51:26 VERIFY ERROR: depth=0, error=unsupported certificate purpose: CN=MY-CA, serial=01234567890123456789
2020-11-13 10:51:26 OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
2020-11-13 10:51:26 TLS_ERROR: BIO read tls_read_plaintext error
2020-11-13 10:51:26 TLS Error: TLS object -> incoming plaintext read error
2020-11-13 10:51:26 TLS Error: TLS handshake failed
2020-11-13 10:51:26 Fatal TLS error (check_tls_errors_co), restarting
Windows config ….
tls-client
pull
remote 1.2.3.4
nobind
dev tun
proto tcp-client
port 1194
ca C:\Users\someone\OpenVPN\config\cert_export_MY-CA.crt
key C:\Users\someone\OpenVPN\config\cert_export_MY-CA.key
cert C:\Users\someone\OpenVPN\config\cert_export_Office.crt
key C:\Users\someone\OpenVPN\config\cert_export_Office.key
;comp-lzo
persist-tun
persist-key
cipher AES-128-CBC
verb 3
#verify-x509-name server name
remote-cert-tls server
#ns-cert-type server
auth SHA1
auth-user-pass
auth-nocache
Any ideas?
Thanks,
R
-
-
herger
newbie
- Posts: 42
- Joined: Tue Aug 18, 2020 2:48 pm
Re: OVPN Certificate Issue
Fri Nov 13, 2020 11:20 am
error=unsupported certificate purpose
this.
the output of `openssl x509 -in C:\Users\someone\OpenVPN\config\cert_export_MY-CA.crt -text` would be helpful, to see what attributes are set in the certificate.
-
-
rules
Frequent Visitor
- Posts: 65
- Joined: Tue Feb 19, 2019 12:10 pm
- Location: Cape Town, South Africa
Topic Author
Re: OVPN Certificate Issue
Fri Nov 13, 2020 11:44 am
error=unsupported certificate purpose
this.
the output of `openssl x509 -in C:\Users\someone\OpenVPN\config\cert_export_MY-CA.crt -text` would be helpful, to see what attributes are set in the certificate.
Where/how do I run this query?
-
-
rules
Frequent Visitor
- Posts: 65
- Joined: Tue Feb 19, 2019 12:10 pm
- Location: Cape Town, South Africa
Topic Author
Re: OVPN Certificate Issue
Fri Nov 13, 2020 11:52 am
In the meantime opening the certificate from the router, it’s the bare basics …
Key Type: RSA
Key Size: 2048
Trusted
Key Usage: key cert. sign
and a very long fingerprint number.
-
-
tdw
Forum Guru
- Posts: 1670
- Joined: Sat May 05, 2018 11:55 am
Re: OVPN Certificate Issue
Fri Nov 13, 2020 2:20 pm
the output of `openssl x509 -in C:\Users\someone\OpenVPN\config\cert_export_MY-CA.crt -text` would be helpful, to see what attributes are set in the certificate.
Where/how do I run this query?
openssl is included with most linux distributions, there will be windows ports available. Alternatively if you double-click a file with a .crt extension on a Windows PC it should launch the crypto shell extensions handler — select the details tab, in the ‘Field’ list find and click on ‘Key Usage’ which should display the usage options in the lower box.
You should not distribute the .key files to clients as anyone possessing them can generate any other certificates they wish signed by your CA.
-
-
rules
Frequent Visitor
- Posts: 65
- Joined: Tue Feb 19, 2019 12:10 pm
- Location: Cape Town, South Africa
Topic Author
Re: OVPN Certificate Issue
Fri Nov 13, 2020 3:17 pm
the output of `openssl x509 -in C:\Users\someone\OpenVPN\config\cert_export_MY-CA.crt -text` would be helpful, to see what attributes are set in the certificate.
Where/how do I run this query?
openssl is included with most linux distributions, there will be windows ports available. Alternatively if you double-click a file with a .crt extension on a Windows PC it should launch the crypto shell extensions handler — select the details tab, in the ‘Field’ list find and click on ‘Key Usage’ which should display the usage options in the lower box.
You should not distribute the .key files to clients as anyone possessing them can generate any other certificates they wish signed by your CA.
Opened it via Windows Certificate handler … Key Usage: Certificate Signing (04)
The key files are needed to unlock the certificates, aren’t they? I normally import them, unlock and then delete them.
-
-
tdw
Forum Guru
- Posts: 1670
- Joined: Sat May 05, 2018 11:55 am
Re: OVPN Certificate Issue
Fri Nov 13, 2020 4:15 pm
Opened it via Windows Certificate handler … Key Usage: Certificate Signing (04)
That is OK for the CA certificate itself, the child certificate used by the OVPN server should have encipherment usages present.
The key files are needed to unlock the certificates, aren’t they? I normally import them, unlock and then delete them.
No, the private key is used only used by the server. You can encrypt certificates and keys but that is not the same as the private key.
If a certificate is exported from the mikrotik with export-passphrase=MYPASSPHRASE the certificate and corresponding private key are exported encrypted by the passphrase — this should be used to make a backup of certificates if the Mikrotik needs reinstalling.
If a certificate is exported from the mikrotik with no export-passphrase specified only the certificate is exported — this should be distributed to any clients which need to verify the authenticity of the server.
-
-
rules
Frequent Visitor
- Posts: 65
- Joined: Tue Feb 19, 2019 12:10 pm
- Location: Cape Town, South Africa
Topic Author
Re: OVPN Certificate Issue
Mon Nov 16, 2020 1:47 pm
Opened it via Windows Certificate handler … Key Usage: Certificate Signing (04)
That is OK for the CA certificate itself, the child certificate used by the OVPN server should have encipherment usages present.
The key files are needed to unlock the certificates, aren’t they? I normally import them, unlock and then delete them.
No, the private key is used only used by the server. You can encrypt certificates and keys but that is not the same as the private key.
If a certificate is exported from the mikrotik with export-passphrase=MYPASSPHRASE the certificate and corresponding private key are exported encrypted by the passphrase — this should be used to make a backup of certificates if the Mikrotik needs reinstalling.
If a certificate is exported from the mikrotik with no export-passphrase specified only the certificate is exported — this should be distributed to any clients which need to verify the authenticity of the server.
Ah ok, the key thing makes more sense now 😅
As for the child certificate having encipherment, I recreated the client certificate to have both key & data encipherment but it still gives me the same error. Do I need to add this to the CA cert also? If so that probably means I’ll have to redo all 30 of my other connections as well, hey?
Thanks,
R
-
-
sindy
Forum Guru
- Posts: 9961
- Joined: Mon Dec 04, 2017 9:19 pm
Re: OVPN Certificate Issue
Mon Nov 16, 2020 2:58 pm
Let me try to explain it in different words.
The whole concept of certificates is based on a cryptographic scheme where encoding and decoding keys are different and the private one cannot be derived from the public one. The public key is part of the certificate data; the private key is normally only available to the certificate holder, which proves its ownership of the certificate by encrypting some random data, provided by the other party, using that key; the other party then uses the public key in the certificate to decrypt those data and find the expected contents.
The key usage is a different thing, and the name is a bit misleading. It is a list of purposes for which the certificate can be used for authentication of its holder. The idea was probably good but the real world implementation is a bit chaotic. For the Windows client to accept the certificate, you apparently need tls-server to be listed in the key-usage list. So it should be sufficient to recreate the server certificate.
The proper way of creating a certificate is to create a CSR (certificate signing request) at the certificate holder device, which also creates the private key as a separate piece of data. Then you deliver the CSR (which does not contain the private key) to the certificate authority, which signs it using its own private key, and delivers the result back to the certified entity. The certified entity then imports the signed certificate, and in the process of import, it links it with the private key generated when creating the CSR. So the private key data never leave the certified entity. The other two pieces of data (the CSR and the signed certificate) may be transported using open channels as their leakage constitutes no compromise of security; the only risk here is that a man in the middle would replace the CSR by an own one, so it would get certified instead of the actual applicant.
When generating the certificate along with the key on another device than the certificate holder, the strong security provided by non-symmetric cryptography becomes dependent on a typically much weaker security of the passphrase used to protect the private key. So every possible effort needs to be taken that the information wouldn’t leak in transport.
-
-
rules
Frequent Visitor
- Posts: 65
- Joined: Tue Feb 19, 2019 12:10 pm
- Location: Cape Town, South Africa
Topic Author
Re: OVPN Certificate Issue
Mon Nov 16, 2020 3:54 pm
Let me try to explain it in different words.
The whole concept of certificates is based on a cryptographic scheme where encoding and decoding keys are different and the private one cannot be derived from the public one. The public key is part of the certificate data; the private key is normally only available to the certificate holder, which proves its ownership of the certificate by encrypting some random data, provided by the other party, using that key; the other party then uses the public key in the certificate to decrypt those data and find the expected contents.
The key usage is a different thing, and the name is a bit misleading. It is a list of purposes for which the certificate can be used for authentication of its holder. The idea was probably good but the real world implementation is a bit chaotic. For the Windows client to accept the certificate, you apparently need tls-server to be listed in the key-usage list. So it should be sufficient to recreate the server certificate.
The proper way of creating a certificate is to create a CSR (certificate signing request) at the certificate holder device, which also creates the private key as a separate piece of data. Then you deliver the CSR (which does not contain the private key) to the certificate authority, which signs it using its own private key, and delivers the result back to the certified entity. The certified entity then imports the signed certificate, and in the process of import, it links it with the private key generated when creating the CSR. So the private key data never leave the certified entity. The other two pieces of data (the CSR and the signed certificate) may be transported using open channels as their leakage constitutes no compromise of security; the only risk here is that a man in the middle would replace the CSR by an own one, so it would get certified instead of the actual applicant.
When generating the certificate along with the key on another device than the certificate holder, the strong security provided by non-symmetric cryptography becomes dependent on a typically much weaker security of the passphrase used to protect the private key. So every possible effort needs to be taken that the information wouldn’t leak in transport.
Thanks Sindy, that definitely puts it into perspective.
I am starting to wonder whether my current setup is politically correct. So I have a CA (because I cheated and I’m making/signing my own certificates), Server and Client (actually have a few). So when configuring my OVPN server on my main Mikrotik router, do I specify the CA or the Server certificate (currently have CA selected because if I select Server the clients don’t want to connect)? And on the client side, am I supposed to have only the Client certificate selected under the OVPN client setup (currently have the CA loaded this side too but I see using the Client cert also works)?
The guide I followed was either dodgy or I didn’t understand it at all 🙈😅
-
-
tdw
Forum Guru
- Posts: 1670
- Joined: Sat May 05, 2018 11:55 am
Re: OVPN Certificate Issue
Mon Nov 16, 2020 4:25 pm
The OVPN server should have its own server certificate, not the self-signed CA, selected. The private key for the server certificate must also be present.
The CA certificate, and any intermediate certificates if used, must also exist on the server Mikrotik. They will be present if you generated the certificates on that Mikrotik, otherwise they should be imported, without private keys, from wherever they were generated.
An important setting on OVPN clients is verify-server-certificate=yes as unless the server certificate is what you expect man-in-the-middle attacks are trivial. The CA certificate, again without private key, should be imported to the client Mikrotik — this allows the client to verify the server before handing over the username and password.
Client certificates are optional, they permit the server to check the client has both a valid certificate and username/password. If used, they must each be installed on the client Mikrotiks with with their private key and the server told to require client certificates.
The majority of third-party websites / videos are often outdated and/or present less than optimal / insecure suggestions. Stick to the Mikrotik help pages / wiki, MUM presentations and the forum.
-
-
sindy
Forum Guru
- Posts: 9961
- Joined: Mon Dec 04, 2017 9:19 pm
Re: OVPN Certificate Issue
Mon Nov 16, 2020 6:33 pm
Again to systematize that:
- Party A which wants to authenticate itself to party B must have its own certificate and the private key for that certificate. No one else must have the private key.
- Party B which receives the certificate from party A must have the certificate of the CA which has signed the Party A’s certificate in its «trusted root CAs» store on Windows and alike, and just have it imported in case of Mikrotik. It doesn’t need any private keys for the CA certificates. Having a copy of the individual certificate of Party A is not mandatory, party A sends it during the authentication process.
- Each party should verify the other one’s authenticity by the certificate. In RouterOS, at several places you have to explicitly require checking of the other party’s certificate validity; other systems usually do that by default.
Client certificates cannot be checked for domain or IP address matching because the clients are typically not on a static or even public address. So the server accepts any client which presents a valid certificate signed by a certificate authority known to the server. In RouterOS, only IPsec currently allows to choose client identity (and apply individual settings to the connection) based on the certificate received; for this in particular, the responder must have the client’s certificate beforehead, as it compares the received one with the stored one to establish the identity.
-
-
rules
Frequent Visitor
- Posts: 65
- Joined: Tue Feb 19, 2019 12:10 pm
- Location: Cape Town, South Africa
Topic Author
Re: OVPN Certificate Issue
Wed Nov 18, 2020 10:41 am
Ok, I’m getting my head around this, thanks 😉
So my setup is like this now …
Create CA certificate, key usage “crl sign”, “key cert sign”. Sign certificate. Make trusted.
Create Server certificate, key usage “digital signature”, “key enchipherment”, “tls server”. Sign with CA certificate. Make Trusted.
Create Client certificate, key usage “tls client”. Sign with CA certificate. Make trusted.
Set Server certificate on OVPN server.
Import the CA & Client (with key) certificates into client. Set Client certificate in client connection.
This setup works Mikrotik to Mikrotik but still getting this when trying from Windows ….
2020-11-18 10:15:57 Validating certificate extended key usage
2020-11-18 10:15:57 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2020-11-18 10:15:57 VERIFY EKU OK
2020-11-18 10:15:57 VERIFY OK: depth=0, CN=Server
2020-11-18 10:16:12 Connection reset, restarting [0]
2020-11-18 10:16:12 SIGUSR1[soft,connection-reset] received, process restarting
2020-11-18 10:16:12 MANAGEMENT: >STATE:1605687372,RECONNECTING,connection-reset,,,,,
2020-11-18 10:16:12 Restart pause, 5 second(s)
-
-
rules
Frequent Visitor
- Posts: 65
- Joined: Tue Feb 19, 2019 12:10 pm
- Location: Cape Town, South Africa
Topic Author
Re: OVPN Certificate Issue
Wed Nov 18, 2020 3:44 pm
Finally occurred to me to check the logs 🤦♂️ ended up being a TUN / TAP conflict, all working now 👍
Thanks again 😉