ORA-01031: Insufficient Privileges means that the current user did not use the right privilege to process the SQL statement.
Since this error can be seen almost in every kind of SQL statement, sometimes you would never know what privilege you lack. So I do my best to collect cases for you.
There’re several error patterns of ORA-01031 in this post. You may click whichever situation you encountered.
- Select (Query)
- Create Table
- Create Index
- Create View
- Create Synonym
- Insert, Update and Delete
- Alter Table (Add Constraint)
- Alter Table (Other’s Table)
- Alter User
- Analyze Table
- Password Change
- EXECUTE IMMEDIATE
- DGMGRL
- Alter Pluggable Database Close
- PDB Clone
- GRANT System Privilege
Select (Query)
Tried to select other’s table, we got ORA-01031: insufficient privileges.
SQL> show user
USER is "HR"
SQL> select distinct gender from oe.customers;
select distinct gender from oe.customers
*
ERROR at line 1:
ORA-01031: insufficient privileges
Theoretically, if we can’t see other’s table, we got ORA-00942: table or view does not exist. But the error message indicates us that we don’t use the right privilege to do it. Why? We’d better do some tests.
The first test is that, can we describe the table’s definition?
SQL> desc oe.customers;
Name Null? Type
----------------------------------------- -------- ----------------------------
...
GENDER VARCHAR2(1)
...
Yes, we can see its metadata, but not data.
So what object privileges we have now? Let’s check them by a privileged user.
SQL> show user
USER is "SYSTEM"
SQL> select privilege from dba_tab_privs where owner = 'OE' and table_name = 'CUSTOMERS' and grantee = 'HR' order by 1;
PRIVILEGE
----------------------------------------
DELETE
INSERT
UPDATE
OK, we can INSERT, UPDATE and DELETE, but no SELECT privilege. This is really weird.
Solution to ORA-01031
To solve insufficient privilege in querying, we should grant SELECT privilege to the user.
SQL> grant select on oe.customers to hr;
Grant succeeded.
Then we query the table again.
SQL> select distinct gender from oe.customers;
G
-
M
F
OK, the problem is solved.
Create Table
Let’s see what will happen if the new user wants to create a table.
C:UsersAdministrator>sqlplus thomas/thomas@orcl
...
SQL> create table test1 (id number, e_id number);
create table test1 (id number, e_id number)
*
ERROR at line 1:
ORA-01031: insufficient privileges
Immediately, ORA-01031: insufficient privileges shows up, which tells the user who doesn’t have the right privilege to do that.
Solution to ORA-01031
The solution is simple, just grant CREATE TABLE to user, a schema-based privilege or CREATE ANY TABLE, a system-wide privilege.
SQL> conn / as sysdba
Connected.
SQL> grant create table to thomas;
Grant succeeded.
Then tell him to try it again.
SQL> create table test1 (id number, e_id number);
Table created.
If you use EXECUTE IMMEDIATE to run CREATE TABLE in a stored procedure, you may check ORA-01031 in EXECUTE IMMEDIATE section in this post.
Create Index
In the above section, we have granted CREATE TABLE to the new user, which naturally enables it to CREATE INDEX in his own schema.
Please note that, CREATE INDEX is not a valid privilege, but CREATE ANY INDEX is.
Let’s see an example and then we guess what privilege we need.
Suppose the new user wants to create an index for SH.CUSTOMERS in his own schema, so we grant SELECT on that table (object privilege) by instinct.
SQL> grant select on sh.customers to thomas;
Grant succeeded.
Then it tries to create an index on that table.
SQL> create index customer_id_gen_idx on sh.customers (cust_id, cust_gender);
create index oe.customer_id_gen_idx on sh.customers (cust_id, cust_gender)
*
ERROR at line 1:
ORA-01031: insufficient privileges
Solution to ORA-01031
This is because SELECT on that table is not enough, you should additionally grant INDEX on that table to user, which is an object privilege.
SQL> grant index on sh.customers to thomas;
Grant succeeded.
Try again.
SQL> create index customer_id_gen_idx on sh.customers (cust_id, cust_gender);
Index created.
Even though the case is possible in reality, we seldom create index for other user’s table in our schema.
Create View
If you have read the above section, then you have known that you have to grant CREATE VIEW to the user in order to solve ORA-01031.
SQL> grant create view to thomas;
Grant succeeded.
If the user still got ORA-01031 after granting CREATE VIEW to him, it must be a deeper problem. That’s why this section is little longer.
Inherit Privilege from Role
Some privileges inherit from role do not work in some situation, especially when accessing intermediate kinds of object, like views or store procedures.
Here is a case that can reproduce the error.
We grant role RESOURCE to the user. Then we grant the system privilege SELECT ANY TABLE to the role RESOURCE.
SQL> grant resource to thomas;
Grant succeeded.
SQL> grant select any table to resource;
Grant succeeded.
So we can expect that the user inherits the system privilege from RESOURCE. That is, it can select any other’s table.
Let’s do the first test. Use it to select other user’s table SH.SALE.
SQL> select count(*) from sh.sales;
COUNT(*)
----------
918843
Good, it acts as we expect, although the user has not any object privilege on SH.SALE.
Let’s do the second test. We use it to create a view which is based on other user’s table SH.SALE.
SQL> create view sh_sales_v as select * from sh.sales;
create view sh_sales_v as select * from sh.sales
*
ERROR at line 1:
ORA-01031: insufficient privileges
What happened? the user has CREATE VIEW and inherit SELECT ANY TABLE from RESOURCE, it should have no problem.
The result implies that the role’s privileges does not reach underlying objects through intermediate objects like views.
Solution to ORA-01031
The solution to this problem is to grant SELECT on the table to user directly.
First, grant the object privilege explicitly to resolve the problem.
SQL> grant select on sh.sales to thomas;
Grant succeeded.
Then tell Thomas to create view again.
SQL> create view sh_sales_v as select * from sh.sales;
View created.
Now, it’s no problem.
Please notice that, if you create a synonym on SH.SALES, it will succeed whether the explicit object privilege is granted directly or not.
Create Synonym
Tried to create a private synonym, but it failed with ORA-01031.
SQL> show user
USER is "HR"
SQL> create synonym customers for oe.customers;
create synonym customers for oe.customers;
*
ERROR at line 1:
ORA-01031: insufficient privileges
To solve the problem, just simply grant CREATE SYNONYM to the user.
SQL> grant create synonym to hr;
Grant succeeded.
Then create it again.
SQL> create synonym customers for oe.customers;
Synonym created.
Problem solved.
Insert, Update and Delete
You may have the right to select other’s table.
SQL> conn sh/sh
Connected.
SQL> select * from hr.t1;
ID
----------
1
2
3
But you may not have the right to perform some Data Manipulation Language (DML) operations on the table. For example, INSERT INTO some data like this:
SQL> insert into hr.t1 values (4);
insert into hr.t1 values (4)
*
ERROR at line 1:
ORA-01031: insufficient privileges
This is because you lack INSERT, UPDATE or DELETE privilege to modify on that table which is usually owned by others.
Solution to ORA-01031
Clearly, the right privilege is INSERT, UPDATE or DELETE at object-level. You may ask for DBA or the object owner to grant the privilege to you.
Grant DML
We may grant individual privileges to the user.
SQL> conn hr/hr
Connected.
SQL> grant insert,update,delete on hr.t1 to sh;
Grant succeeded.
As we can see, the grantor grants 3 object privileges INSERT, UPDATE and DELETE on the table to the grantee at a time.
Grant All
In some cases, you may consider to grant all possible object privileges to user, for example:
SQL> grant all on hr.t1 to sh;
Grant succeeded.
In the statement, ALL is a keyword which means all possible privileges on specified object. For a table, it naturally includes not only SELECT, but also INSERT, UPDATE and DELETE.
As a result, we can insert some rows.
SQL> conn sh/sh
Connected.
SQL> insert into hr.t1 values (4);
1 row created.
SQL> commit;
Commit complete.
SQL> select * from hr.t1;
ID
----------
1
2
3
4
That is to say, not only SELECT, but also INSERT, UPDATE or DELETE privilege you should have to manipulate tables owned by other users.
Alter Table (ADD CONSTRAINT)
In the above section, we have granted CREATE TABLE to the user. Implicitly, he also has the right to ALTER TABLE on schema-level. So the cause of ORA-01031 in ALTER TABLE is not so obvious as we thought.
Please note that, ALTER TABLE is not a privilege, but ALTER ANY TABLE is. That’s why there’s no such GRANT ALTER TABLE TO statement.
Let’s see an example. User Thomas wants to add a constraint so as to make a reference to another user’s data, so we grant SELECT on that table to the user by instinct.
SQL> grant select on hr.employees to thomas;
Then we make the reference.
SQL> alter table test1 add constraint fk_eid foreign key (e_id) references hr.employees (employee_id);
alter table test1 add constraint fk_eid foreign key (e_id) references hr.employees (employee_id)
*
ERROR at line 1:
ORA-01031: insufficient privileges
We got ORA-01031.
Solution to ORA-01031
The right privilege to reference other’s data is not SELECT, it’s REFERENCES.
We should grant REFERENCES on the table to user either by HR or privileged users.
SQL> grant references on hr.employees to thomas;
Grant succeeded.
Now Thomas can finish his job.
SQL> alter table test1 add constraint fk_eid foreign key (e_id) references hr.employees (employee_id);
Table altered.
Alter Table (Other’s Table)
If you were trying to alter other user’s table without a proper privilege, you may get ORA-01031 like this:
SQL> show user
USER is "HR"
SQL> alter table sh.customers add (col varchar2(10));
alter table sh.customers add (col varchar2(10))
*
ERROR at line 1:
ORA-01031: insufficient privileges
Although you have some other object privilege like SELECT or UPDATE on the table, you still cannot add a column for other user’s table.
Solution
The right privilege to alter other’s table is not UPDATE, it’s ALTER. The single word, the single word can be an object privilege.
SQL> grant alter on sh.customers to hr;
Grant succeeded.
Then do it again.
SQL> alter table sh.customers add (col varchar2(10));
Table altered.
System privilege ALTER ANY TABLE shall also work, but it’s unnecessary for most cases.
Alter User
Tried to add some quota on tablespace to itself, but it lacks of some privileges.
SQL> show user
USER is "HR"
SQL> alter user hr quota unlimited on users;
alter user hr quota unlimited on users
*
ERROR at line 1:
ORA-01031: insufficient privileges
Solution
The right privilege in this case is ALTER USER.
SQL> show user
USER is "SYSTEM"
SQL> grant alter user to hr;
Grant succeeded.
Then we do it again.
SQL> show user
USER is "HR"
SQL> alter user hr quota unlimited on users;
User altered.
SQL> alter user oe account lock;
User altered.
As you can see, with ALTER USER privilege, the user not only can grant some quota to itself, but also can change other’s status.
Analyze Table
We saw ORA-01031 when we tried to analyze other user’s table.
SQL> show user
USER is "HR"
SQL> analyze table sh.customers validate structure;
analyze table sh.customers validate structure
*
ERROR at line 1:
ORA-01031: insufficient privileges
Solution
To enable an user to analyze and gather statistics, the correct privilege is ANALYZE ANY.
SQL> show user
USER is "SYS"
SQL> grant analyze any to hr;
Grant succeeded.
Then analyze the table again.
SQL> analyze table sh.customers validate structure;
Table analyzed.
We solved it.
Password Change
Tried to change other’s password by SQL*Plus command password, but the user has inadequate privileges.
SQL> show user
USER is "HR"
SQL> password oe
Changing password for oe
New password:
Retype new password:
ERROR:
ORA-01031: insufficient privileges
Password unchanged
Since password command is actually an ALTER USER statement, the correct privilege to change other’s password is ALTER USER.
SQL> grant alter user to hr;
Grant succeeded.
Then do it again.
Let’s see how I reproduce ORA-01031 for statements using EXECUTE IMMEDIATE by the following example.
Inherit Privilege from Role
In the above section, I have granted role RESOURCE to THOMAS. Now I grant CREATE ANY DIRECTORY and DROP ANY DIRECTORY to the role RESOURCE.
SQL> grant create any directory, drop any directory to resource;
Grant succeeded.
So we can expect that the user can also do such operations by inheriting all privileges from RESOURCE.
Things look fine when we use the user to create or drop directories.
SQL> create directory tmp_path as '/u02/tmp';
Directory created.
SQL> drop directory tmp_path;
Directory dropped.
SQL> create directory tmp_path as '/u02/tmp';
Directory created
Now, Thomas would like to create directories in stored procedures which is also called named PL/SQL blocks or programming units.
First of all, DBA have to grant CREATE PROCEDURE to him before Thomas doing anything.
SQL> grant create procedure to thomas;
Grant succeeded.
Then Thomas create a procedure like this:
SQL> create or replace procedure drop_create_tmp_dir is
begin
execute immediate 'drop directory tmp_path';
execute immediate 'create or replace directory tmp_path as ''/u02/tmp''';
end drop_create_tmp_dir;
/
2 3 4 5 6
Procedure created.
It seems no problem. But when we execute the stored procedure (named PL/SQL), we got ORA-01031 at line 3.
SQL> exec drop_create_tmp_dir;
BEGIN drop_create_tmp_dir; END;
*
ERROR at line 1:
ORA-01031: insufficient privileges
ORA-06512: at "THOMAS.DROP_CREATE_TMP_DIR", line 3
ORA-06512: at line 1
Rationale
This is because the system privileges inherit from role cannot be used in named stored procedures with definer’s right.
Solutions to ORA-01031
Now we have several options, the first one is to grant all necessary privilege to the user directly, the second one is to use invoker’s right, and the last one is to use anonymous PL/SQL blocks.
1. Directly Granting to User
The user should directly get the system privilege from DBA, not inherit from role.
SQL> grant create any directory, drop any directory to thomas;
Grant succeeded.
Back to THOMAS, we can execute it again.
SQL> exec drop_create_tmp_dir;
PL/SQL procedure successfully completed.
The better thing is that we don’t have to recompile the procedure.
2. Use Invoker’s Right
Another way to solve ORA-01031 for statements in EXECUTE IMMEDIATE is to use invoker’s right to define the procedure.
Let’s revert the granting by SYS.
SQL> revoke create any directory, drop any directory from thomas;
Revoke succeeded.
Then we created the procedure with AUTHID CURRENT_USER clause.
SQL> create or replace procedure drop_create_tmp_dir authid current_user is
begin
execute immediate 'drop directory tmp_path';
execute immediate 'create or replace directory tmp_path as ''/u02/tmp''';
end drop_create_tmp_dir;
/
2 3 4 5 6
Procedure created.
Try to execute the procedure by the user.
SQL> exec drop_create_tmp_dir;
PL/SQL procedure successfully completed.
By invoker’s right, we can use role’s privileges.
3. Anonymous PL/SQL Block
What we mean in the above is that role privileges cannot penetrate NAMED stored procedures. That is to say, you can use role privileges in anonymous PL/SQL blocks. For instance, we can rewrite the stored procedure to an anonymous PL/SQL as this:
begin
execute immediate 'drop directory tmp_path';
execute immediate 'create or replace directory tmp_path as ''/u02/tmp''';
end;
/
You can save and use it as a normal SQL script file.
For the same reason, CREATE TABLE in EXECUTE IMMEDIATE can also throw ORA-01031.
DGMGRL
DGMGRL allows user to query the status of all nodes involved through the local authentication without problem, but it might fail to switchover to a standby database or convert to a snapshot standby.
DGMGRL Switchover
Let’s see a switchover in 11g, it will fail when you connect DGMGRL with local authentication.
[oracle@primary01 ~]$ dgmgrl /
...
DGMGRL> switchover to standb
Performing switchover NOW, please wait...
Operation requires shutdown of instance "primdb2" on database "primdb"
Shutting down instance "primdb2"...
ORA-01031: insufficient privileges
Warning: You are no longer connected to ORACLE.
Please complete the following steps and reissue the SWITCHOVER command:
shut down instance "primdb2" of database "primdb"
DGMGRL>
But if you connect DGMGRL with the database password, the switchover will succeed.
[oracle@primary01 ~]$ dgmgrl sys/password@primdb1
...
DGMGRL> switchover to standb
Performing switchover NOW, please wait...
Operation requires shutdown of instance "primdb2" on database "primdb"
Shutting down instance "primdb2"...
Database closed.
Database dismounted.
ORACLE instance shut down.
New primary database "standb" is opening...
Operation requires shutdown of instance "primdb1" on database "primdb"
Shutting down instance "primdb1"...
ORA-01109: database not open
Database dismounted.
ORACLE instance shut down.
Operation requires startup of instance "primdb1" on database "primdb"
Starting instance "primdb1"...
ORACLE instance started.
Database mounted.
Switchover succeeded, new primary is "standb"
DGMGRL>
DGMGRL Convert
Same error happened in a conversion.
[oracle@primary01 ~]$ dgmgrl /
...
DGMGRL> CONVERT DATABASE standb TO SNAPSHOT STANDBY;
Converting database "standb" to a Snapshot Standby database, please wait...
Operation requires shutdown of instance "standb2" on database "standb"
Shutting down instance "standb2"...
ORA-01031: insufficient privileges
Warning: You are no longer connected to ORACLE.
Please complete the following steps and reissue the CONVERT command:
shut down instance "standb2" of database "standb"
Solution to ORA-01031
You must use the database authentication to convert a standby database.
[oracle@primary01 ~]$ dgmgrl sys/password@primdb1
...
DGMGRL> CONVERT DATABASE standb TO SNAPSHOT STANDBY;
Converting database "standb" to a Snapshot Standby database, please wait...
Operation requires shutdown of instance "standb2" on database "standb"
Shutting down instance "standb2"...
ORA-01109: database not open
Database dismounted.
ORACLE instance shut down.
Continuing to convert database "standb" ...
Database "standb" converted successfully
...
For the same reason, the broker is unable to startup the new standby database during a switchover and throws ORA-01017 due to OS authentication.
Alter Pluggable Database Close
We saw an error when we tried to close a pluggable database (PDB) by a normal user.
SQL> conn hr/password@orclpdb
Connected.
SQL> show user
USER is "HR"
SQL> alter pluggable database close;
alter pluggable database close
*
ERROR at line 1:
ORA-01031: insufficient privileges
To solve ORA-01031, we take two steps to make the user be able to close a PDB.
1. Grant SYSDBA to the User
Please make sure that you login as SYS and are in the right container.
SQL> show user
USER is "SYS"
SQL> show con_namev
CON_NAME
------------------------------
ORCLPDB
Then we grant SYSDBA privilege to the user.
SQL> grant sysdba to hr;
Grant succeeded.
2. Connect as SYSDBA
The user should use SYSDBA privilege to connect to the PDB.
SQL> conn hr/password@orclpdb as sysdba
Connected.
SQL> alter pluggable database close;
Pluggable database altered.
Actually, the normal user has become a SYS which of course has the ability to maintain database.
PDB Clone
When you try to clone a remote PDB via a database link, you may see ORA-17628 and ORA-01031 at that moment. I have talk about it in that post.
GRANT System Privilege
It failed with ORA-01031 when we tried to grant a system privilege to another user.
SQL> show user
USER is "HR"
SQL> grant create table to oe;
grant create table to oe
*
ERROR at line 1:
ORA-01031: insufficient privileges
To be able to grant any system privilege to any grantee, the grantor requires GRANT ANY PRIVILEGE privilege.
SQL> show user
USER is "SYSTEM"
SQL> grant grant any privilege to hr;
Grant succeeded.
That is to say, the insufficient privilege in this case is GRANT ANY PRIVILEGE.
for ORA-01031: insufficient privileges. Some of the more common causes are:
- You tried to change an Oracle username or password without having the appropriate privileges.
- You tried to perform an
UPDATEto a table, but you only haveSELECTaccess to the table. - You tried to start up an Oracle database using
CONNECT INTERNAL. - You tried to install an Oracle database without having the appropriate privileges to the operating-system.
The option(s) to resolve this Oracle error are:
- You can have the Oracle DBA grant you the appropriate privileges that you are missing.
- You can have the Oracle DBA execute the operation for you.
- If you are having trouble starting up Oracle, you may need to add the Oracle user to the dba group.
For ORA-00942: table or view does not exist. You tried to execute a SQL statement that references a table or view that either does not exist, that you do not have access to, or that belongs to another schema and you didn’t reference the table by the schema name.
If this error occurred because the table or view does not exist, you will need to create the table or view.
You can check to see if the table exists in Oracle by executing the following SQL statement:
select *
from all_objects
where object_type in ('TABLE','VIEW')
and object_name = 'OBJECT_NAME';
For example, if you are looking for a suppliers table, you would execute:
select *
from all_objects
where object_type in ('TABLE','VIEW')
and object_name = 'SUPPLIERS';
OPTION #2
If this error occurred because you do not have access to the table or view, you will need to have the owner of the table/view, or a DBA grant you the appropriate privileges to this object.
OPTION #3
If this error occurred because the table/view belongs to another schema and you didn’t reference the table by the schema name, you will need to rewrite your SQL to include the schema name.
For example, you may have executed the following SQL statement:
select *
from suppliers;
But the suppliers table is not owned by you, but rather, it is owned by a schema called app, you could fix your SQL as follows:
select *
from app.suppliers;
If you do not know what schema the suppliers table/view belongs to, you can execute the following SQL to find out:
select owner
from all_objects
where object_type in ('TABLE','VIEW')
and object_name = 'SUPPLIERS';
This will return the schema name who owns the suppliers table.
ORA-01031
ORA-01031: не достаточно привилегий
Причина:
Вы предприняли попытку изменить текущее имя пользователя или пароль без привилегии АБД. Эта ошибка часто происходит, если вы пытаетесь изменить (UPDATE) таблицу, для которой вы имеете только SELECT привилегии, или если вы пытаетесь связаться внутренне без необходимых привилегий операционной системы.
Действие:
Попросите своего АБД выполнить операцию или дать вам необходимую привилегию.
Troubleshooting ORA-1031: Insufficient Privileges While Connecting As SYSDBA
Posted by Patrick Hamou on 2016:04:19 20:15:14
Applies To
Oracle Database — Enterprise Edition — Version 9.2.0.1 to 11.2.0.3 [Release 9.2 to 11.2]
Information in this document applies to any platform.
Purpose
This document is intended to supply some commonly used steps for diagnosing error ORA-1031 encountered while connecting as sysdba.
RENAPS Offers Oracle Database & Middleware Managed Services. Learn More about how we can help your business
Generic Concepts
A user can connect AS SYSDBA from the Oracle Server host machine using one of the following methods:
- OS authentication
- password file authentication
A user should connect to the database AS SYSDBA from a remote machine only by using password file authentication . When the Oracle Server runs on Windows it is possible to connect remotely as sysdba without providing a username and a password since in this case the connection might be secure.
Starting with Oracle 11g it is also possible to use strong authentication for SYSDBA. See Note 457083.1 for details.
SYSDBA OS Authentication
The OS authentication is the process of verifying the identity of the user connecting to the database with the information managed by the OS. An OS user is able to use this authentication method if the following conditions are met:
1. the user is a member of a special group.
2. the OS authentication is allowed by the server settings(sqlnet.authentication_services is set correctly)
The OS user should belong to the OSDBA group in order to login as sysdba. On Unix the default name of these group is dba. On Windows the name of the group is ORA_DBA.
On Unix Parameter sqlnet.authentication_services must be set to (ALL) or to (BEQ, <other values>) for this to work. On Windows this parameter must be set to (NTS).
SYSDBA Password File Authentication
The credentials provided when connecting remotely as sysdba are compared to the contents of the passwordfile.
Password file authentication is enabled by setting the database parameter remote_login_password file to «shared» or «exclusive».
SQL> alter system set remote_login_passwordfile=exclusive scope=spfile;Note: When both OS authentication and password file authentication are enabled then the OS Authentication will be used. This means that you can connect with any username/password combination. See Note 242258.1 for details.
Troubleshooting ORA-1031 when connecting as SYSDBA using OS Authentication
1. Check whether the OS user is part of the OSDBA group.
On Unix
A. See what are the groups of the user:
[oracle@seclin4 ~]$ id
uid=500(oracle) gid=500(oinstall) groups=500(oinstall),501(dba) context=user_u:system_r:unconfined_tB. See what is the OSDBA group defined in file $ORACLE_HOME/rdbms/lib/config.[cs]
Example for Linux:
[oracle@seclin4 ~]$ cat $ORACLE_HOME/rdbms/lib/config.c
/* SS_DBA_GRP defines the UNIX group ID for sqldba adminstrative access. */
/* Refer to the Installation and User's Guide for further information. */
/* IMPORTANT: this file needs to be in sync with
rdbms/src/server/osds/config.c, specifically regarding the
number of elements in the ss_dba_grp array.
*/
#define SS_DBA_GRP "dba"
#define SS_OPER_GRP "dba"
#define SS_ASM_GRP ""
char *ss_dba_grp[] = {SS_DBA_GRP, SS_OPER_GRP, SS_ASM_GRP};Example for AIX:
[celcaix3]/grdbms/64bit/app/oracle/product/1120/rdbms/lib> cat config.s
# SS_DBA_GRP defines the UNIX group ID for sqldba adminstrative access.
# Refer to the Installation and User's Guide for further information.
.rename H.10.NO_SYMBOL{TC},""
.rename H.11.NO_SYMBOL{TC},""
.rename H.12.NO_SYMBOL{TC},""
.rename H.13.NO_SYMBOL{RO},""
.rename H.14.NO_SYMBOL{RO},""
.rename H.15.NO_SYMBOL{RO},""
.rename H.16.ss_dba_grp{TC},"ss_dba_grp"
.lglobl H.13.NO_SYMBOL{RO}
.lglobl H.14.NO_SYMBOL{RO}
.lglobl H.15.NO_SYMBOL{RO}
.globl ss_dba_grp{RW}
# .text section
# .data section
.toc
T.16.ss_dba_grp:
.tc H.16.ss_dba_grp{TC},ss_dba_grp{RW}
T.10.NO_SYMBOL:
.tc H.10.NO_SYMBOL{TC},H.13.NO_SYMBOL{RO}
T.11.NO_SYMBOL:
.tc H.11.NO_SYMBOL{TC},H.14.NO_SYMBOL{RO}
T.12.NO_SYMBOL:
.tc H.12.NO_SYMBOL{TC},H.15.NO_SYMBOL{RO}
.csect ss_dba_grp{RW}, 3
.llong H.13.NO_SYMBOL{RO}
.llong H.14.NO_SYMBOL{RO}
.llong H.15.NO_SYMBOL{RO}
# End csect ss_dba_grp{RW}
.csect H.13.NO_SYMBOL{RO}, 3
.string "dba"
# End csect H.13.NO_SYMBOL{RO}
.csect H.14.NO_SYMBOL{RO}, 3
.string "dba"
# End csect H.14.NO_SYMBOL{RO}
.csect H.15.NO_SYMBOL{RO}, 3
.string ""
# End csect H.15.NO_SYMBOL{RO}
.llong 0x00000000
# .bss sectionExample for Solaris:
.section ".text",#alloc,#execinstr
/* 0x0000 7 */ .file "x.c"
.section ".data",#alloc,#write
/* 0x0000 9 */ .global ss_dba_grp
/* 0x0000 10 */ .align 8
.global ss_dba_grp
ss_dba_grp:
/* 0x0000 17 */ .align 8
/* 0x0000 18 */ .xword (.L12+0)
/* 0x0004 24 */ .align 8
/* 0x0004 25 */ .xword (.L13+0)
/* 0x0008 26 */ .type ss_dba_grp,#object
/* 0x0008 27 */ .size ss_dba_grp,16
.section ".rodata1",#alloc
/* 0x0008 13 */ .align 8
.L12:
/* 0x0008 15 */ .ascii "dba"
/* 0x0014 20 */ .align 8
.L13:
/* 0x0014 22 */ .ascii "dba"In the above examples we see that the user is a member of the «dba» group which matches the value of SS_DBA_GRP in config.c. If the groups seem to be correctly configured but the connection is still failing use the script from Note 67984.1 to see whether Oracle evaluates correctly the group membership.
Intermittent ora-1031 errors for sysdba OS authentication can occur because of the nscd service that caches information from the /etc/passwd and /etc/group as configured in /etc/nscd.conf, if stopping this service makes the problem go away then please refer to the OS vendor.
On Windows
When using OS authentication on Windows the OS user must be a member of one of the following two groups:
- ORA_DBA
- ORA_<%ORACLE_SID%>_DBA
The membership to the second group allows the OS user to use OS authentication while connecting to the instance with the name %ORACLE_SID%> only.
Check whether the OS user is a member of any of these two local groups:
Get the name of the OS user:
D:oracleproduct10.2.0db_1NETWORKADMIN>echo %username%
dbadminObtain the list of the members of the local group:
D:oracleproduct10.2.0db_1NETWORKADMIN>NET LOCALGROUP ORA_DBA
Alias name ORA_DBA
Comment Members can connect to the Oracle database as a DBA without a password
Members
-------------------------------------------------------------------------------
dbadmin
NT AUTHORITYSYSTEM
The command completed successfully.
D:oracleproduct10.2.0db_1NETWORKADMIN>set oracle_sid=d1v10204
D:oracleproduct10.2.0db_1NETWORKADMIN>NET LOCALGROUP ORA_%ORACLE_SID%_DBA
Alias name ORA_d1v10204_DBA
Comment Members can connect to instance d1v10204 as a DBA without a password
Members
-------------------------------------------------------------------------------
dbadmin
The command completed successfully.If the user is a member of these groups but the connection is still failing then compile the C program from the following page and then run the executable to see whether Oracle evaluates the group membership correctly:
http://msdn.microsoft.com/en-us/library/aa370655(VS.85).aspx
2. Check the value of the SQLNET.AUTHENTICATION_SERVICES parameter in file $ORACLE_HOME/network/admin/SQLNET.ORA
On Unix
This parameter should not be set if no strong authentication method is used. If such a method is being used then set the parameter to one of the following values:
SQLNET.AUTHENTICATION_SERVICES = (ALL)or
SQLNET.AUTHENTICATION_SERVICES = (BEQ,)Where can be any combination of the following values: TCPS, KERBEROS5, RADIUS
NOTE: If the definition of SQLNET.AUTHENTICATION_SERVICES is preceded by a leading blank space, an ORA-1031 error may occur
On Windows
This parameter should be set to NTS:
SQLNET.AUTHENTICATION_SERVICES = (NTS)If needed you can add other strong authentication methods besides NTS:
SQLNET.AUTHENTICATION_SERVICES = (NTS,TCPS)Note: If the parameter is set to NONE then the OS authentication will be disabled and the user will have to provide a valid username/password combination to be able to connect to the database.
As above, if the definition of SQLNET.AUTHENTICATION_SERVICES is preceded by a leading blank space an ORA-1031 error may occur
Note:
On Windows the user who is not able to connect as sysdba using OS authentication might be a domain user. Check the following if you are in this scenario:
- It is important that this user is a direct member of the local ORA_DBA group( See Note 1065023.1 for details).
- Oracle Service must be started as a user who is able to check the group membership for any domain user who might be connecting as sysdba locally( See Note 1071638.1 for details).
- Check whether the clocks of the RDBMS Server and of the Active Directory Server are perfectly synchronized. Even small clock drifts can cause issues to the underlying kerberos authentication mechanism used by default on Windows. In these cases the ORA-1031 would be most of the times intermittent.
- Check whether the Oracle Service is started by an user whose name contains non ASCII characters . See Note 1280996.1 for details
ORA-12638 might be seen when the user is managed in Active Directory rather than locally
On Windows, when the OS user is a domain user, the error that is seen can be ORA-12638. In these situations it is important to obtain a client SQL*Net trace file and analyze the MS Windows errors encountered by function naun5authent:
A) Add the following lines in client’s sqlnet.ora file(The client might be the same as the RDBMS Server):
trace_level_client = 16
trace_directory_client = c:tempnewsqlnetB) Retry the SYSDBA connection and get the SQL*Net trace file. Look for the string «SSPI» inside this file. You will see something similar to this:
[02-OCT-2011 09:21:02:076] naun5authent: SSPI: 0x8009030c error in InitializeSecurityContext
[02-OCT-2011 09:21:02:076] naun5authent: exit
[02-OCT-2011 09:21:02:076] naunauthent: exit
[02-OCT-2011 09:21:02:076] nau_ccn: get credentials function failed
[02-OCT-2011 09:21:02:076] nau_ccn: failed with error 12638
[02-OCT-2011 09:21:02:076] nacomsd: entry
[02-OCT-2011 09:21:02:076] nacomfsd: entry
[02-OCT-2011 09:21:02:076] nacomfsd: exit
[02-OCT-2011 09:21:02:076] nacomsd: exit
[02-OCT-2011 09:21:02:076] nau_ccn: exit
[02-OCT-2011 09:21:02:076] na_csrd: failed with error 12638
[02-OCT-2011 09:21:02:076] na_csrd: exit
[02-OCT-2011 09:21:02:076] nacomer: error 12638 received from authentication service C) Search for the MS error (0x8009030c in the above example) in the following page:
http://technet.microsoft.com/en-us/library/cc786775%28WS.10%29.aspx
D) Contact the AD administrators and let them perform the actions suggested by Microsoft. For the above SSPI error the solution is the following:
«Logon Denied. Group Policy impersonates both the computer and the user when it determines the scope of policy, meaning it acts on behalf the user. This could be a machine account needing its password reset or a user account that has some problem. Check Active Directory to make sure the user account is set up correctly. Use a utility, like netdom or nltest, to test the computer account’s password.»
3. After checking the configuration as per steps 1) and 2) review the problems described in the following notes
Note 69642.1 — UNIX: Checklist for Resolving Connect AS SYSDBA Issues
Note 114384.1 — WIN: Checklist for Resolving CONNECT AS SYSDBA (INTERNAL) Issues
4. If the problem is not solved after reviewing the above notes open a service request with Oracle Support and provide the following information
For Unix
A) File $ORACLE_HOME/network/admin/sqlnet.ora
B) File $ORACLE_HOME/rdbms/lib/config.c(or config.s)
C) The output of command «id»
D) A trace file obtained with the following commands:
Linux:
strace -o /tmp/strace_sysdba.output -cfT sqlplus / as sysdba
AIX, Solaris:
truss -fea -o /tmp/truss_sysdba.output sqlplus / as sysdba
HP-UX:
tusc -afpo /tmp/tusc_sysdba.output -aef sqlplus / as sysdbaFor Windows
A) File %ORACLE_HOME%/network/admin/sqlnet.ora
B) The output of the commands «echo %username% and «NET LOCALGROUP ORA_DBA»
C) A pair of client/server SQL*Net traces obtained while reproducing the problem as per Note 395525.1 and Note 374116.1.
Troubleshooting ORA-1031 seen while using password file authentication
1.Check the value of parameter remote_login_passwordfile. This has to be set to either EXCLUSIVE or SHARED:
SQL> show parameter remote_login_passwordfile
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
remote_login_passwordfile string EXCLUSIVEIf the parameter is not set correctly then modify it and then restart the database:
SQL> ALTER SYSTEM SET REMOTE_LOGIN_PASSWORDFILE=EXCLUSIVE SCOPE=SPFILE;2. Check whether the password file with the correct name exists in the right directory/folder and has the right ownership and permissions
On Unix
The password file with the name orapw<ORACLE_SID> must exist in directory $ORACLE_HOME/dbs. If it does not exist then recreate it using the orapwd command
$ > orapwd file=$ORACLE_HOME/dbs/orapw<sid> password=<password> force=y ignorecase=nThe permissions of the file should be the following:
-rw-r----- 1 oracle oinstall 1536 Jul 21 13:50 orapwdv11201More information about using the orapwd command can be seen in Note 1029539.6.
On Windows
The default location of the password file on Windows is folder %ORACLE_HOME%/database and the name of the password file must be pwd<%ORACLE_SID%>.ora. When the passwordfile authentication is being used Oracle searches for the password file in the following locations(in this exact order):
- The folder pointed to by the registry key HKEY_LOCAL_MACHINESOFTWAREORACLEHomeXXORA_<%ORACLE_SID%>_PWFILE
- The folder pointed to by the registry key HKEY_LOCAL_MACHINESOFTWAREORACLEHomeXXORA_PWFILE
- The default location ( %ORACLE_HOME%/database)
Note: Make sure that the password file exists in the folder specified by the registry keys if these are set.
If the password file does not exist in the right folder then create it using the orapwd command:
D:> cd %ORACLE_HOME/database
D:> orapwd file=pwd<sid>.ora password=<password> force=y nosysdba=nMore information about using the orapwd command can be seen in Note 1029539.6.
3. Check whether the user was granted the SYSDBA privilege
SQL> select * from v$pwfile_users;
USERNAME SYSDB SYSOP SYSAS
------------------------------ ----- ----- -----
SYS TRUE TRUE FALSEIf the user is not granted the privilege then run:
grant SYSDBA to myadminuser; where myadminuser is the user you want to use to connect as sysdba.
4. Check that there is no issue with the configuration of the listener used to connect to the database.
The value of the ORACLE_HOME parameter in the listener’s definition must be correctly specified:
SID_LIST_LISTENER =
(SID_LIST =
(SID_DESC =
(GLOBAL_DBNAME = d1v11203)
(ORACLE_HOME = /oracle/product/11203)
(SID_NAME = d1v11203)
)
)The case of the SID in the definition of the listener must match the case of the instance name specified by ORACLE_SID:
SID_LIST_LISTENER =
(SID_LIST =
(SID_DESC =
(GLOBAL_DBNAME = d1v11203)
(ORACLE_HOME = /oracle/product/11203)
(SID_NAME = d1v11203)
)
)Frequent problems with passwordfile authentication
1) Connecting remotely as SYSDBA to a TNS alias that is defined using more TNS addresses with load balancing fails intermittently with ORA-1031.
The TNS alias is defined in tnsnames.ora this way:
CLIENT_load_balance=
(DESCRIPTION =
(LOAD_BALANCE = yes)
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCP)(HOST = ro-rac1.ro.oracle.com)(PORT = 1521))
(ADDRESS = (PROTOCOL = TCP)(HOST = ro-rac2.ro.oracle.com)(PORT = 1521))
)
(CONNECT_DATA =
(SERVICE_NAME = service.idc.oracle.com)
)
)If there is at least one node having the passwordfile configured incorrectly we will see this error intermittently. Make sure that the passwordfile is configured correctly on all the nodes.
2) RMAN auxiliary connections fail with the following error
RMAN-04006: error from auxiliary database: ORA-01031: insufficient privilegesBefore running the RMAN command make sure that the passwordfile is correctly configured for the remote auxiliary database.
3) EM proper configuration/functioning depends on the ability to connect remotely as sysdba. For example while installing EM, these error could be found in file emca_repos_config_yyyy_mm_dd_hh_mm_ss.log
Caused by: oracle.sysman.emdrep.config.ConfigurationException:
Cannot Create Connection:(DESCRIPTION=(ADDRESS_LIST=(ADDRESS=(PROTOCOL=TCP)(HOST=testemconfig.us.oracle.com)(PORT=1553)))(CONNECT_DATA=(SERVICE_NAME=TESTDB)))
SYS
sysdba
ORA-01031: insufficient privilegesThis issue could be reproduced in sqlplus:
[oracle@test dbs]$ sqlplus sys/oracle@r01 as sysdba
SQL*Plus: Release 10.2.0.1.0 - Production on Tue Jun 7 16:02:39 2011
Copyright (c) 1982, 2005, Oracle. All rights reserved.
ERROR:
ORA-01031: insufficient privilegesTo remedy this make sure that you follow the sysdba passwordfile authentication troubleshooting steps.
Are you getting the “ORA-01031 insufficient privileges” error? Learn what causes this error and how to resolve it in this article.
ORA-01031 Cause
The cause of the ORA-01031 error is that you’re trying to run a program or function and you don’t have the privileges to run it.
This could happen in many situations, such as:
- You attempted to change a username or password, without having the appropriate privileges.
- You attempted to query a table where you have at least one privilege but not the required privilege to run the query (e.g. you have SELECT but not UPDATE).
- You attempted to start an Oracle database using the CONNECT INTERNAL command.
- You attempted to install an Oracle database without having the appropriate privileges on the operating system.
There are many solutions to this error message.
First, you could ask the Oracle database administrator to grant you the privileges you are missing. Often this can be an oversight (a missing privilege in a script or a change that wasn’t implemented correctly), so they may grant it to you.
If they won’t grant you the required privileges, you can ask the DBA to execute the code or statement for you.
This is common if you have some privileges but not the required privileges. Let’s take a look at an example.
Some Privileges But Not All Required Privileges
You might get the ORA-01031 error if you have SELECT privileges on a table, but you’re trying to run another statement (such as UPDATE or DELETE) and don’t have permission to do that.
Let’s see an example.
CREATE USER userA IDENTIFIED BY password;
CREATE USER userB IDENTIFIED BY password;
CREATE USER testUser IDENTIFIED BY password;
GRANT CONNECT, CREATE SESSION TO testUser;
CREATE TABLE userA.table1(someValue VARCHAR2(1));
CREATE TABLE userB.table2(someValue VARCHAR2(1));
GRANT DELETE ON userB.table2 to testUser;The above statements show that:
- Two users have been created (userA and userB)
- They each have one table in their schema (userA.table1, and userB.table2)
- We’ll use testUser to test our SELECT queries.
- The only privilege granted to testUser is DELETE on userB.table2. Nothing has been granted on userA.table1.
Now, let’s connect as the testUser and run some queries.
SELECT *
FROM userA.table1;ORA-00942: table or view does not exist
More information on the ORA-00942 error can be found here.
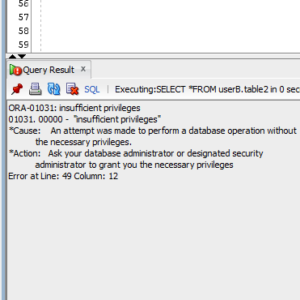
SELECT *
FROM userB.table2;ORA-01031: insufficient privileges
We get the first error because, according to testUser, the table doesn’t exist. It actually does exist, but testUser has no privileges on it, so this is expected behaviour.
Now, we get the ORA-01031 on the second table because we have the DELETE privilege, but not the SELECT privilege. We can see the table because we have at least one privilege on it, but we get this error because we don’t have the privilege to do what we want on it.
ORA-01031 On Create View
If you’re getting this error when creating a view, then it’s likely due to not having the correct privileges on the underlying table, or tables.
A CREATE VIEW statement contains a SELECT statement. So, check that you can run the SELECT statement successfully.
If you can’t, then check your privileges against this table. You might need to ask for the privileges from the DBA, or ask the DBA to create the view (as mentioned above).
If you can see the data from the SELECT query, but can’t create the view, it could be you don’t have the appropriate privileges to create the view.
To create a view in the database, you need the CREATE VIEW privilege, as well as the SELECT privilege on the underlying tables. If you don’t have this, then ask the DBA to grant it to you, or ask them to create the view for you.
ORA-01031 Create Table
You could get this error as you’re creating a table.
If so, then it means you don’t have the right privileges to create the table.
This might seem obvious, but I thought I’d clarify.
You need the CREATE TABLE privilege to create a table on the database.
Just like with the earlier scenarios of this error message, you can ask the DBA to grant you the privilege, or get the DBA to run the statement and create the table for you.