- Remove From My Forums
-
Общие обсуждения
-
Тип события: Ошибка
Источник события: DNS
Категория события: Отсутствует
Код события: 7050
Дата: 31.05.2010
Время: 7:36:32
Пользователь: Н/Д
Компьютер: SERVERHP
Описание:
Ошибка функции recv() DNS-cервера. Данные события содержат сведения об ошибке.Дополнительные сведения можно найти в центре справки и поддержки, в «http://go.microsoft.com/fwlink/events.asp».
Данные:
0000: 46 27 00 00 F’..Такая ошибка появляется с завидной регулярностью. Так как собираемся поднимать резервный контролер домена то хотелось бы от этой ошибки избавится.
Какие соображение специалисты?
-
Изменен тип
31 мая 2010 г. 10:07
-
Изменен тип
ILYA [ sie ] Sazonov
1 июня 2010 г. 8:32 -
Изменен тип
Vinokurov Yuriy
15 июня 2010 г. 4:55
Давность и отсутствие активности в теме -
Изменен тип
Vinokurov Yuriy
15 июня 2010 г. 4:56
-
Изменен тип
3 Replies
-
EminentX
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.ghost chili
Active Directory & GPO Expert
-
check
149
Best Answers -
thumb_up
350
Helpful Votes -
format_list_bulleted
3
How-tos
Are you running any port scanning software on the network, or do you have debug logging enabled on DNS?
Was this post helpful?
thumb_up
thumb_down
-
check
-
I don’t have port scanning software and debug logging is disabled. it always happen when all users login as same time and it works after I restarted the server
Was this post helpful?
thumb_up
thumb_down
-
1 found this helpful
thumb_up
thumb_down
Информационная безопасность
Рекомендация: подборка платных и бесплатных курсов Java — https://katalog-kursov.ru/

Исследователи в области кибербезопасности из компании Check Point раскрыли новую критическую уязвимость, которая затрагивает версии Windows Server 2003–2019 с оценкой критичности 10 из 10 по шкале CVSS.
17-летний программный недостаток приводит к удаленному выполнению кода (CVE-2020-1350), названному Check Point «SigRed» и может позволить удаленному злоумышленнику, не прошедшему проверку подлинности, получить права администратора домена над целевыми серверами и получить полный контроль над ИТ-инфраструктурой организации.
Атакующий может использовать уязвимость SigRed, отправляя специально созданные вредоносные DNS-запросы на DNS-сервер Windows и выполнять произвольный код, позволяя хакеру перехватывать и обрабатывать электронные письма пользователей и сетевой трафик, собирать учетные данные пользователей и многое другое.
В отчете, опубликованном в блоге компании, исследователь Check Point Саги Цадик подтвердил, что этот недостаток имеет ужасный характер, позволяя атакующим начать атаку, которая может распространиться с одного уязвимого компьютера на другой без какого-либо вмешательства человека. Т.е. уязвимость носит явный «wormable»-характер.
После того, как Check Point ответственно сообщила о своих выводах Microsoft, производитель Windows подготовил исправление для этой уязвимости и выпустил его, начиная с сегодняшнего дня, в рамках своего июльского исправления во вторник, которое также включает в себя обновления безопасности для 122 других уязвимостей.
В Microsoft заявили, что не нашли никаких доказательств того, что эта ошибка активно использовалась злоумышленниками, и посоветовали пользователям немедленно устанавливать исправления.
«Windows DNS Server — это основной сетевой компонент. Хотя в настоящее время неизвестно, чтобы эта уязвимость использовалась в активных атаках, важно, чтобы клиенты применяли обновления Windows для ее устранения как можно скорее».
Детали
Переадресованный запрос происходит, когда DNS-сервер не может разрешить IP-адрес для данного доменного имени (например, www.google.com ), в результате чего запрос перенаправляется на официальный DNS-сервер имен (NS).
Чтобы использовать эту архитектуру, SigRed включает в себя настройку записей ресурсов NS домена («deadbeef.fun») для указания на вредоносный сервер имен («ns1.41414141.club») и запрос целевого DNS-сервера для домена, чтобы последний анализировал ответы от сервера имен для всех последующих запросов, связанных с доменом или его поддоменами.
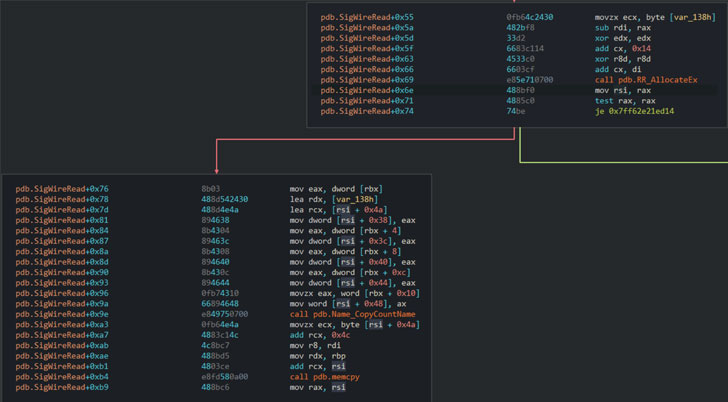
Таким образом злоумышленник может вызвать ошибку целочисленного переполнения в функции, которая анализирует входящие ответы для перенаправленных запросов («dns.exe!SigWireRead»), чтобы отправить ответ DNS, содержащий запись ресурса SIG размером более 64 КБ, и вызвать контролируемое переполнение кучи примерно исходя из небольшого выделенного буфера.
Ошибка выявлена в функции, ответственной за выделение памяти для записи ресурса («RR_AllocateEx»), чтобы генерировать результат размером более 65 535 байт, что вызывает переполнение целых чисел, которое приводит к гораздо меньшему выделению, чем ожидалось.
Но с одним сообщением DNS, ограниченным 512 байтами в UDP (или 4096 байтами, если сервер поддерживает механизмы расширения) и 65 535 байтами в TCP, исследователи обнаружили, что ответа SIG с одной только длинной сигнатурой было недостаточно, чтобы вызвать уязвимость.
Чтобы достичь этого, атака использует преимущества сжатия DNS-имен в ответах DNS, чтобы создать переполнение буфера с использованием вышеупомянутого метода для значительного увеличения размера выделения.
SigRed может быть запущен удаленно через браузер в ограниченных сценариях (например, Internet Explorer и браузеры Microsoft Edge не на основе Chromium), позволяя злоумышленнику злоупотреблять поддержкой DNS-серверов Windows в функциях повторного использования соединений и конвейерной обработки запросов, чтобы «переправить» DNS-запрос внутри полезной нагрузки HTTP-запроса к целевому DNS-серверу при посещении веб-сайта под их контролем.
DNS-клиенты («dnsapi.dll») не подвержены этой ошибке, что заставляет исследователей подозревать, что Microsoft управляет двумя совершенно разными базами кода для DNS-сервера и DNS-клиента и не синхронизирует исправления ошибок между ними.
Исправление
Учитывая серьезность уязвимости и высокие шансы на активную эксплуатацию, пользователям рекомендуется срочно обновить уязвимые DNS-серверы Windows для снижения риска.
В качестве временного обходного пути, максимальная длина сообщения DNS (через TCP) может быть установлена в значение «0xFF00», чтобы исключить вероятность переполнения буфера:
reg add "HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesDNSParameters" /v "TcpReceivePacketSize" /t REG_DWORD /d 0xFF00 /f && net stop DNS && net start DNSYou should upgrade or use an alternative browser.
Guest
Guest
-
#1
I get this error message in event viewer for my DNS. [The
DNS server recv() function failed. The event data contains
the error.] I am running Win/2000 server with active
directory and only one forward lookup zone. Any help would
be greatly appreciated. Thanks
-
- Mar 31, 2004
-
- 515
-
- 0
-
- 18,980
-
#2
I got the same thing this afternoon. One 7050 error on
each of my 8 DNS servers in 3 domains (parent + 2 child
domains) this afternoon. The error came only once on each
server — but all within 5 minutes. DNS seems to be working
ok — ran netdiag and dcdiag. Any info would really help.
>——Original Message——
>I get this error message in event viewer for my DNS. [The
>DNS server recv() function failed. The event data
contains
>the error.] I am running Win/2000 server with active
>directory and only one forward lookup zone. Any help
would
>be greatly appreciated. Thanks
>.
>
Guest
Guest
-
#3
In news:1c8b01c48caa$53f10590$a301280a@phx.gbl,
Mary <anonymous@discussions.microsoft.com> made a post then I commented
below
> I got the same thing this afternoon. One 7050 error on
> each of my 8 DNS servers in 3 domains (parent + 2 child
> domains) this afternoon. The error came only once on each
> server — but all within 5 minutes. DNS seems to be working
> ok — ran netdiag and dcdiag. Any info would really help.
Seems to be a rare issue that a DNS probe would cause:
http://www.eventid.net/display.asp?eventid=7050&eventno=4151&source=DNS&phase=1
—
Regards,
Ace
Please direct all replies ONLY to the Microsoft public newsgroups
so all can benefit.
This posting is provided «AS-IS» with no warranties or guarantees
and confers no rights.
Ace Fekay, MCSE 2003 & 2000, MCSA 2003 & 2000, MCSE+I, MCT, MVP
Microsoft Windows MVP — Windows Server — Directory Services
Security Is Like An Onion, It Has Layers
HAM AND EGGS: A day’s work for a chicken;
A lifetime commitment for a pig.
—
=================================
-
#4
Hi Ace,
I think that was my post at EventID, matches what I submitted. We’ve gotten
a few more 7050 errors that was not my co-worker doing a port probe — the
new 7050 events happened at about 2:30 am and 3:30 am est 6 days apart on
all four DNS servers (two are AD empty root, two are AD child) at HQ.
Interestingly, too, even though all 4 servers in same switch, our 2 AD Root
servers also reported 7050 on two other days at 11 am and 2 pm respectively,
whereas the child servers did not. The 11 am and 2pm I can possibly see as
port probes (most of HQ is software engineers), but 2:30 am and 3:30 am?
None of the DNS servers are public, all internal and AD structure hidden
from Internet. DNS looks fine, no one is having problems, no other errors
(System, Application, Directory Service, NTFS, Security logs).
I still think first occurance was port probe, too much coincidence that 7050
occurred on every DNS server exactly when port probe done. But I’m back to
investigating cause of newest 7050s, if same cause or not. Did a Google
search, saw this thread and thought I’d post the additional info. Still
investigating.
No need to reply.
Regards,
Joan
«Ace Fekay [MVP]»
<PleaseSubstituteMyActualFirstName&LastNameHere@hotmail.com> wrote in
message news:%23oLyYOKkEHA.2668@TK2MSFTNGP10.phx.gbl…
> In news:1c8b01c48caa$53f10590$a301280a@phx.gbl,
> Mary <anonymous@discussions.microsoft.com> made a post then I commented
> below
> > I got the same thing this afternoon. One 7050 error on
> > each of my 8 DNS servers in 3 domains (parent + 2 child
> > domains) this afternoon. The error came only once on each
> > server — but all within 5 minutes. DNS seems to be working
> > ok — ran netdiag and dcdiag. Any info would really help.
>
>
> Seems to be a rare issue that a DNS probe would cause:
>
>
http://www.eventid.net/display.asp?eventid=7050&eventno=4151&source=DNS&phase=1
>
> —
> Regards,
> Ace
>
> Please direct all replies ONLY to the Microsoft public newsgroups
> so all can benefit.
>
> This posting is provided «AS-IS» with no warranties or guarantees
> and confers no rights.
>
> Ace Fekay, MCSE 2003 & 2000, MCSA 2003 & 2000, MCSE+I, MCT, MVP
> Microsoft Windows MVP — Windows Server — Directory Services
>
> Security Is Like An Onion, It Has Layers
> HAM AND EGGS: A day’s work for a chicken;
> A lifetime commitment for a pig.
> —
> =================================
>
>
Guest
Guest
-
#5
In news:%23SjBu9PkEHA.704@TK2MSFTNGP09.phx.gbl,
Joan <anonymous@discussions.microsoft.com> made a post then I commented
below
> Hi Ace,
>
> I think that was my post at EventID, matches what I submitted. We’ve
> gotten a few more 7050 errors that was not my co-worker doing a port
> probe — the new 7050 events happened at about 2:30 am and 3:30 am
> est 6 days apart on all four DNS servers (two are AD empty root, two
> are AD child) at HQ. Interestingly, too, even though all 4 servers in
> same switch, our 2 AD Root servers also reported 7050 on two other
> days at 11 am and 2 pm respectively, whereas the child servers did
> not. The 11 am and 2pm I can possibly see as port probes (most of HQ
> is software engineers), but 2:30 am and 3:30 am?
>
> None of the DNS servers are public, all internal and AD structure
> hidden from Internet. DNS looks fine, no one is having problems, no
> other errors (System, Application, Directory Service, NTFS, Security
> logs).
>
> I still think first occurance was port probe, too much coincidence
> that 7050 occurred on every DNS server exactly when port probe done.
> But I’m back to investigating cause of newest 7050s, if same cause or
> not. Did a Google search, saw this thread and thought I’d post the
> additional info. Still investigating.
>
> No need to reply.
>
> Regards,
> Joan
Hmm, at a lost, because this is a new one and there’s little on it.
According to this article:
http://www.oriweb.com/updateip.htm
It has something to do with dynamic updates. Maybe those are the times that
the netlogon service from a particular DC is trying to update into DNS.
And another link I found, someone mentions it maybe a Winsock driver based
error.
http://www.mail-archive.com/imail_forum@list.ipswitch.com/msg89439.html
Now, if you isolate the machine that is trying the updates (netmon? retina?)
and take a look at the NIC conifig, drivers, etc, maybe that can be a start?
Determine if any DCs or DNS servers have mulitple NICs, or teamed NICs, etc,
for a start as well. Another link mentions the ‘birthday’ attack against
BIND servers. But doesn’t seem likely in your case, since its MS DNS.
—
Regards,
Ace
Please direct all replies ONLY to the Microsoft public newsgroups
so all can benefit.
This posting is provided «AS-IS» with no warranties or guarantees
and confers no rights.
Ace Fekay, MCSE 2003 & 2000, MCSA 2003 & 2000, MCSE+I, MCT, MVP
Microsoft Windows MVP — Windows Server — Directory Services
Security Is Like An Onion, It Has Layers
HAM AND EGGS: A day’s work for a chicken;
A lifetime commitment for a pig.
—
=================================
Guest
Guest
-
#6
In news:%23SjBu9PkEHA.704@TK2MSFTNGP09.phx.gbl,
Joan <anonymous@discussions.microsoft.com> wrote their comments
Then Kevin replied below:
> Hi Ace,
>
> I think that was my post at EventID, matches what I
> submitted. We’ve gotten a few more 7050 errors that was
> not my co-worker doing a port probe — the new 7050
> events happened at about 2:30 am and 3:30 am est 6 days
> apart on all four DNS servers (two are AD empty root, two
> are AD child) at HQ. Interestingly, too, even though all
> 4 servers in same switch, our 2 AD Root servers also
> reported 7050 on two other days at 11 am and 2 pm
> respectively, whereas the child servers did not. The 11
> am and 2pm I can possibly see as port probes (most of HQ
> is software engineers), but 2:30 am and 3:30 am?
>
> None of the DNS servers are public, all internal and AD
> structure hidden from Internet. DNS looks fine, no one is
> having problems, no other errors (System, Application,
> Directory Service, NTFS, Security logs).
>
> I still think first occurance was port probe, too much
> coincidence that 7050 occurred on every DNS server
> exactly when port probe done. But I’m back to
> investigating cause of newest 7050s, if same cause or
> not. Did a Google search, saw this thread and thought I’d
> post the additional info. Still investigating.
Are you using the Advanced logging features? (Advanced tab)
Under higher load DNS will log 7050 events with Advanced logging enabled.
Advanced logging adds considerable load to DNS to write the log. When the
load gets to a certain point DNS just cannot write the log and answer
queries. DNS can handle thousands of queries a minute as long as it doesn’t
have to write a log. If it has to write a log, it slows DNS down way too
much. There was a poster with this event just yesterday, he had advanced
logging turned on, he turned off the logging and it resolved the issue.
—
Best regards,
Kevin D4 Dad Goodknecht Sr. [MVP]
Hope This Helps
================================================
—
When responding to posts, please «Reply to Group»
via your newsreader so that others may learn and
benefit from your issue, to respond directly to
me remove the nospam. from my email address.
================================================
http://www.lonestaramerica.com/
================================================
Use Outlook Express?… Get OE_Quotefix:
It will strip signature out and more
http://home.in.tum.de/~jain/software/oe-quotefix/
================================================
Keep a back up of your OE settings and folders
with OEBackup:
http://www.oehelp.com/OEBackup/Default.aspx
================================================
Guest
Guest
-
#7
In news:eACpzMXkEHA.3988@TK2MSFTNGP14.phx.gbl,
Kevin D. Goodknecht Sr. [MVP] <admin@nospam.WFTX.US> made a post then I
commented below
> Are you using the Advanced logging features? (Advanced tab)
>
> Under higher load DNS will log 7050 events with Advanced logging
> enabled. Advanced logging adds considerable load to DNS to write the
> log. When the load gets to a certain point DNS just cannot write the
> log and answer queries. DNS can handle thousands of queries a minute
> as long as it doesn’t have to write a log. If it has to write a log,
> it slows DNS down way too much. There was a poster with this event
> just yesterday, he had advanced logging turned on, he turned off the
> logging and it resolved the issue.
Curious Kevin, where is that other post? I tried to search on 7050, but no
luck.
Thanks!
Ace
Guest
Guest
-
#8
In news:uHBI4hXkEHA.1652@TK2MSFTNGP09.phx.gbl,
Ace Fekay [MVP] <PleaseSubstituteMyActualFirstName&LastNameHere@hotmail.com>
wrote their comments
Then Kevin replied below:
> Curious Kevin, where is that other post? I tried to
> search on 7050, but no luck.
It is in the windows.server.dns group under this subject line:
Windows 2003 DNS forwarder suddenly doesn’t work anymore
news:436501c4903d$4573d380$a601280a@phx.gbl
—
Best regards,
Kevin D4 Dad Goodknecht Sr. [MVP]
Hope This Helps
================================================
—
When responding to posts, please «Reply to Group»
via your newsreader so that others may learn and
benefit from your issue, to respond directly to
me remove the nospam. from my email address.
================================================
http://www.lonestaramerica.com/
================================================
Use Outlook Express?… Get OE_Quotefix:
It will strip signature out and more
http://home.in.tum.de/~jain/software/oe-quotefix/
================================================
Keep a back up of your OE settings and folders
with OEBackup:
http://www.oehelp.com/OEBackup/Default.aspx
================================================
Guest
Guest
-
#9
In news:eDVn96akEHA.3724@TK2MSFTNGP11.phx.gbl,
Kevin D. Goodknecht Sr. [MVP] <admin@nospam.WFTX.US> made a post then I
commented below
> It is in the windows.server.dns group under this subject line:
> Windows 2003 DNS forwarder suddenly doesn’t work anymore
>
> news:436501c4903d$4573d380$a601280a@phx.gbl
>
Thanks. I couldn’t find it searching the message because I haven’t read the
thread yet, so the messages were never downloaded.
Interesting how advanced logging would do that and mimic a probe.
Ace
-
#10
Hi Ace, Kevin,
Just found your replies, thanks for info! Will investigate accordingly.
Regards,
Joan
«Ace Fekay [MVP]»
<PleaseSubstituteMyActualFirstName&LastNameHere@hotmail.com> wrote in
message news:uCYgj8bkEHA.3104@TK2MSFTNGP14.phx.gbl…
> In news:eDVn96akEHA.3724@TK2MSFTNGP11.phx.gbl,
> Kevin D. Goodknecht Sr. [MVP] <admin@nospam.WFTX.US> made a post then I
> commented below
> > It is in the windows.server.dns group under this subject line:
> > Windows 2003 DNS forwarder suddenly doesn’t work anymore
> >
> > news:436501c4903d$4573d380$a601280a@phx.gbl
> >
>
> Thanks. I couldn’t find it searching the message because I haven’t read
the
> thread yet, so the messages were never downloaded.
>
> Interesting how advanced logging would do that and mimic a probe.
>
> Ace
>
>
Guest
Guest
-
#11
In news:eEPpIeQlEHA.2884@TK2MSFTNGP09.phx.gbl,
Joan <anonymous@discussions.microsoft.com> made a post then I commented
below
> Hi Ace, Kevin,
>
> Just found your replies, thanks for info! Will investigate
> accordingly.
>
> Regards,
> Joan
>
Please let us know if it helped.
Ace
Guest
Guest
-
#12
I am also having the same problem…. Any answers yet? I am trying to
use Terminal Services….Everyone can log in…. But the remote
control will Not work — including the SHADOW Command.
Thanks
Angela
—
shotz11111
————————————————————————
Posted via http://www.mcse.ms
————————————————————————
View this thread: http://www.mcse.ms/message994513.html
Guest
Guest
-
#13
I am also having the same problem…. Any answers yet? I am trying to
use Terminal Services….Everyone can log in…. But the remote
control will Not work — including the SHADOW Command.
Thanks
Angela
—
shotz11111
————————————————————————
Posted via http://www.mcse.ms
————————————————————————
View this thread: http://www.mcse.ms/message994513.html
Guest
Guest
-
#14
In news:shotz11111.1dohcd@mail.mcse.ms,
shotz11111 <shotz11111.1dohcd@mail.mcse.ms> made a post then I commented
below
> I am also having the same problem…. Any answers yet? I am trying to
> use Terminal Services….Everyone can log in…. But the remote
> control will Not work — including the SHADOW Command.
>
> Thanks
> Angela
Shdow command has nothing to do with DNS. Both users need to be in a session
in order to use remote control (shadow a session). You cannot do it from the
console session.
—
Regards,
Ace
Please direct all replies ONLY to the Microsoft public newsgroups
so all can benefit.
This posting is provided «AS-IS» with no warranties or guarantees
and confers no rights.
Ace Fekay, MCSE 2003 & 2000, MCSA 2003 & 2000, MCSE+I, MCT, MVP
Microsoft Windows MVP — Windows Server — Directory Services
Security Is Like An Onion, It Has Layers
HAM AND EGGS: A day’s work for a chicken;
A lifetime commitment for a pig.
—
=================================
Similar threads
- Advertising
- Cookies Policies
- Privacy
- Term & Conditions