Some common errors and solutions
error parsing certificate : X509 — The date tag or value is invalid
This error message occurs with a faulty certificate. Refer to this detailed forum post for more info.
certificate verification failed : x509 — certificate verification failed, e.g. crl, ca or signature check failed
This error message occurs when a certificate can’t be verified properly. Certificate verification failure can occur, for example, if you are using an MD5-signed certificate. With an MD5-signed certificate, the security level is so low that the authenticity of the certificate can’t by any reasonable means be assured. In other words, it could very well be a fake certificate. The solution is to use a certificate not signed with MD5 but with SHA256 or better. Refer to the MD5 signature algorithm support section for more information.
digest_error: NONE: not usable
This error message occurs if you specify auth none and also tls-auth in your client profile. This happens because tls-auth needs an auth digest, but it isn’t specified. To resolve the error, remove the tls-auth directive. It’s not possible to enable it with auth none enabled.
SSL — Processing of the ServerKeyExchange handshake message failed
This error message likely occurs when using older versions of OpenVPN/OpenSSL on the server-side. Some users have solved this issue by updating their OpenVPN and OpenSSL software on the server-side.
BIO read tls_read_plaintext error: error:1408A0C1:SSL routines:SSL3_GET_CLIENT_HELLO:no shared cipher
This error message relates to cipher suites. You can usually remedy this by going to the app settings in OpenVPN Connect and checking the box for AES-CBC Cipher Algorithm.
Other client error messages
Refer to general OpenVPN client connectivity error messages and solutions for more error messages.
MD5 signature algorithm support
We recommend not using MD5 as an algorithm for a signing certificate due to its possible insecurity. For example, time-standard home computer equipment takes about eight hours to falsify a certificate signed using MD5 as an algorithm. Using MD5 means it’s possible to fake the identity of the server. This opens up to a risk for a man-in-the-middle attack. Such an attack leads to the interception of data communication.
You should only support the use of MD5 for older equipment.
We pushed out a security and functionality upgrade of OpenVPN Connect for Android in November 2017 and discovered that many people’s devices still used MD5-signed certificates.
We recommend converting to a setup with SHA256-signed certificates for any installations that still use MD5-signed certificates. If the devices in use don’t support this option, we recommend updating the device to add the function or replacing the device completely.
For your reference, we have a list of deprecated options and ciphers here: https://community.openvpn.net/openvpn/wiki/DeprecatedOptions
Refer to these links for more information about MD5 signatures:
- https://tools.ietf.org/html/rfc6151#section-2
- http://eprint.iacr.org/2005/067.pdf
- http://eprint.iacr.org/2005/102.pdf
To determine if you are using an MD5 type certificate, use this command with openssl as your testing tool:
openssl x509 -in ca.crt -noout -text | grep "Signature Algorithm"
Example result if the certificate is using MD5:
Signature Algorithm: md5WithRSAEncryption
If you see this result on the CA certificate or client certificate, we recommend converting to a proper, securely signed certificate set that uses at least SHA256 or better.
OpenVPN Access Server doesn’t use MD5-certificate signatures.
For open-source OpenVPN users or users with a third-party device that includes OpenVPN functionality using MD5-type certificates, you should investigate the option to update the software on your device or change the signature algorithm type, if possible.
The default settings of a program like EasyRSA 3, used by open-source OpenVPN for generating client certificates and keys, are pretty secure and will generate certificates that are not signed with MD5.
How to get started with OpenVPN Connect
To use OpenVPN Connect, you must have an OpenVPN profile that connects to a VPN server. OpenVPN profiles are files with the extension .ovpn.
To import a profile, do one of the following:
- If you have a .ovpn profile, copy the profile and any files it references to a folder or SD card on your device. Ensure you copy all files to the same folder. Launch OpenVPN Connect, tap the menu icon, tap Import Profile, and tap File. Select the .ovpn profile from the folder location.
- If you need to connect with OpenVPN Access Server, import the profile directly from Access Server: launch OpenVPN Connect, tap the menu icon, tap Import Profile, and enter the URL for the Access Server Client UI.
- If you need to connect with CloudConnexa, import the profile directly from your private CloudConnexa service: launch OpenVPN Connect, tap the menu icon, tap Import Profile, and enter your CloudConnexa URL.
Is OpenVPN Connect for Android vulnerable to Heartbleed?
No—all versions of OpenVPN Connect for Android use the OpenSSL library, which is immune to Heartbleed.
Are CRLs (certificate revocation lists) supported?
Yes, OpenVPN Connect supports certificate revocation lists (CRLs) as of Android version 1.1.14.
To use a CRL, you must add it to the .ovpn profile:
<crl-verify> -----BEGIN X509 CRL----- MIHxMFwwDQYJKoZIhvcNAQEEBQAwFTETMBEGA1UEAxMKT3BlblZQTiBDQRcNMTQw NDIyMDQzOTI3WhcNMjQwNDE5MDQzOTI3WjAWMBQCAQEYDzIwMTQwNDIyMDQzOTI3 WjANBgkqhkiG9w0BAQQFAAOBgQBQXzbNjXkx8+/TeG8qbFQD5wd6wOTe8HnypQTt eELsI7eyNtiRRhJD3qKfawPVUabSijnwhAPHfhoIOLKe67RLfzOwAsFKPNJAVdmq rYw1t2eucHvGjH8PnTh0aJPJaI67jmNbSI4CnHNcRgZ+1ow1GS+RAK7kotS+dZz9 0tc7Qw== -----END X509 CRL----- </crl-verify>
You can concatenate multiple CRLs together within the crl-verify block above.
If you are importing a .ovpn file that references an external CRL file such as crl-verify crl.pem make sure to drop the file crl.pem into the same place as the .ovpn file during import so the profile parser can access it.
I am having trouble importing my .ovpn file.
The following pointers can help with importing .ovpn files:
1. All files must be in the same directory
When you import a .ovpn file, ensure that all files referenced by the .ovpn file, such as ca, cert, and key files, are in the same directory on the device as the .ovpn file.
2. Check formatting and size
Profiles must be UTF-8 (or ASCII) and under 256 KB in size.
3. Use the unified format for OpenVPN profiles
Consider using the unified format for OpenVPN profiles which allows all certs and keys to be embedded into the .ovpn file. This simplifies OpenVPN configuration management because it integrates all elements of the configuration into a single file.
For example, a traditional OpenVPN profile might specify certs and keys as follows: ca ca.crt cert client.crt key client.key tls-auth ta.key 1. You can convert this usage to unified form by pasting the content of the certificate and key files directly into the OpenVPN profile as follows using an XML-like syntax:
<ca> ——BEGIN CERTIFICATE—— MIIBszCCARygAwIBAgIE… . . . /NygscQs1bxBSZ0X3KRk… Lq9iNBNgWg== ——END CERTIFICATE—— </ca> <cert> ——BEGIN CERTIFICATE—— . . . </cert> <key> ——BEGIN RSA PRIVATE KEY—— . . . </key> key-direction 1 <tls-auth> ——BEGIN OpenVPN Static key V1—— . . . </tls-auth>
Another approach to eliminate certificates and keys from the OpenVPN profile is to use the Android Keychain. For information about this, refer to the section on using the Android Keychain below.
Note: When converting tls-auth to unified format, check for a second parameter after the filename (usually a 0 or 1). This parameter is also known as the key-direction parameter and must be specified as a standalone directive when tls-auth is converted to a unified format. For example, if the parameter is 1, add this line to the profile: key-direction 1. If there is no second parameter to tls-auth, you must add this line to the profile: key-direction bidirectional.
Where are the support forums for OpenVPN Connect?
https://forums.openvpn.net/
Is IPv6 supported?
Yes. OpenVPN Connect supports IPv6 transport and IPv6 tunnels as long as the server supports them as well.
Why does OpenVPN Connect show two notification icons when connected?
The Android operating system requires two notification icons. They show that the VPN session is a high priority and shouldn’t be arbitrarily terminated by the system.
Can I disable the connection notification sound?
On some Android devices, a connection notification sound plays whenever a VPN tunnel is established and can’t be silenced by a non-root app.
How can I maximize battery life?
You can enable Battery Saver within OpenVPN Connect to pause the VPN when the phone screen goes blank:
- Launch OpenVPN Connect.
- Tap the menu icon.
- Tap Settings.
- Tap to enable Battery Saver.
Note: It’s possible if you enable Battery Saver settings and Seamless Tunnel options, you will block any app from reaching the internet while the VPN is active, but the device screen isn’t on. Enabling both can be useful for additional energy savings, as long as you don’t have any background apps that need constant internet access.
Can I control the VPN from outside the app?
Yes, you can control the VPN connection using shortcuts. You can quickly connect to a specific profile by adding a shortcut on your phone for OpenVPN Connect:
- Launch OpenVPN Connect.
- Tap the edit icon for the profile you want to make a shortcut.
- Tap Set Connect Shortcut.
- Enter a shortcut name, or keep the default suggestions and tap Create.
- Add the app shortcut to your home screen.
You can quickly disconnect from the VPN by adding a shortcut on your phone for OpenVPN Connect:
- Launch OpenVPN Connect.
- Tap the menu icon at the top left.
- Tap Settings.
- Tap Set Disconnect Shortcut.
- Add the app shortcut to your home screen.
Why does the VPN disconnect when I make or receive a voice call?
Some cellular networks are incapable of maintaining a data connection during a voice call. If Android detects this as a loss of network connectivity, the VPN pauses during the call and automatically resumes when the call ends.
Given that mobile devices are easily lost or stolen, how best to secure VPN profiles against compromise if the device falls into the wrong hands?
We recommend two steps to provide a little extra protection for your phone:
- Save the private key in the device keychain—it’s the most sensitive data in a profile. Consider removing the client certificate and private key from the profile and saving them in the device Keychain instead. For more information, refer to the section about using the Android Keychain.
- Use a strong device-level password. A strong password is critical for protecting data stored in the device Keychain.
Is it safe to save passwords?
The safest option is not to save your password and use the Android Keychain as a repository for your private key (see below).
You have the option to save the password by checking Save Password when you edit the profile. When you check this, OpenVPN Connect stores your password in the keychain.
Why is the save password switch sometimes disabled?
The save password switch on the authentication password field is typically enabled, but you can disable it by adding the following OpenVPN directive to the profile:
setenv ALLOW_PASSWORD_SAVE 0Note: The above directive only applies to the authentication password. The private key password, if it exists, can always be saved.
How can I make the app work with profiles that lack a client certificate/key?
If you have a profile that connects to a server without a client certificate/key, you must include the following directive in your profile:
setenv CLIENT_CERT 0Including this directive is necessary to resolve an ambiguity when the profile doesn’t contain a client certificate or key. When there isn’t a client certificate or key in the profile, OpenVPN Connect doesn’t know whether to obtain an external certificate/key pair from the Android Keychain or whether the server requires a client certificate/key. For example, a server that doesn’t require a client certificate/key is configured with the client-cert-not-required directive. The option is given as a “setenv” to avoid breaking other OpenVPN clients that might not recognize it.
Why doesn’t the app support TAP-style tunnels?
The Android VPN API currently supports only TUN-style or routed tunnels on Layer 3. TAP-style or bridged tunnels on Layer 2 are not possible on Android. This is a limitation of the Android platform. If you try to connect a profile that uses a TAP-based tunnel, you get an error that says only Layer 3 tunnels are currently supported.
If you want to see TAP-style tunnels supported in OpenVPN Connect, contact the Google Android team and ask them to extend the VpnService API to allow this. Without such changes to the VpnService API, non-root apps such as OpenVPN Connect can’t support TAP-style tunnels.
Are there any OpenVPN directives not supported by the app?
OpenVPN Connect uses the OpenVPN3 client library. While it supports almost all configuration directives, some are deemed obsolete or rarely-used. If you believe there is a directive we’re not supporting right now, but should, let us know by opening a support ticket and providing the details there.
Here is a partial list of directives not currently supported:
- dev tap — This directive is not supported because the underlying Android VPN API doesn’t support tap-style tunnels.
- fragment — The fragment directive is not supported due to the complexity it adds to the OpenVPN implementation. It’s better to leave fragmentation up to the lower-level transport protocols. Note as well that the client doesn’t support connecting to a server that uses the fragment directive.
- secret — Static key encryption mode (non-TLS) isn’t supported.
- socks-proxy — Socks proxy support is currently not supported.
- Not all ciphers are supported — OpenVPN Connect fully supports the AES-GCM and AES-CBC ciphers, and ChaCha20-Poly1305 as of Connect v3.3. The AES-GCM cipher algorithm in particular is well-suited for modern processors generally used in Android devices, iOS devices, macs and modern PCs. The deprecated DES and Blowfish ciphers are currently still supported but will be removed in the future.
- proxy directives — While proxy directives are currently supported (http-proxy and http-proxy-option), they are currently NOT supported in <connection> profiles.
Can I have multiple profiles?
Yes, you can import any number of profiles from the Import menu:
- Launch OpenVPN Connect.
- Tap the Add icon.
- Enter the URL and username credentials or import a .ovpn file.
- To connect to the profile, tap the profile’s radio button.
- Enter your password.
OpenVPN Connect assigns a name to the profile based on the server hostname, username and filename. If you import a profile with the same name as one that already exists, OpenVPN Connect adds (1), (2), etc to the profile name.
How do I delete or rename a profile?
To delete a profile, tap the Edit icon next to the profile. From the Edit Profile screen, tap Delete Profile.
To rename a profile, tap the Edit icon next to the profile. From the Edit Profile screen, tap the Profile Name field and change it.
Can I have multiple proxies?
Yes, you can add any number of proxies from the main menu. Each profile can have one proxy assigned.
To add a proxy:
- Launch OpenVPN Connect.
- Tap the Menu icon in the top left.
- Tap Proxies.
- Tap the Add icon.
- Enter the connection information for the proxy and tap Save.
Once you’ve added a proxy, you can add it to your profile:
- Tap the Edit icon for the profile.
- Under Proxy, tap the radio button of the proxy to add.
- Tap Save.
The profile now displays both the OpenVPN Profile and the proxy name. When you connect, your connection to the VPN server authenticates using the proxy server.
How do I edit or delete a proxy?
To edit or delete a proxy:
- Launch OpenVPN Connect.
- Tap the Menu icon in the top left.
- Tap Proxies.
- Tap the Edit icon next to the proxy you wish to edit or delete.
- Edit the proxy details and tap Save or if you want to delete, tap Delete Proxy.
You can also edit or delete a proxy from within a profile:
- Launch OpenVPN Connect.
- Tap the Edit icon for a profile.
- Tap the Edit icon for the proxy.
- Edit the proxy details and tap Save or if you want to delete, tap Delete Proxy.
How do I use a client certificate and private key from the Android Keychain?
Using the Android Keychain to store your private key leverages the hardware-backed Keystore on many Android devices. This protects the key with the Android-level device password and prevents key compromise even if the device is rooted.
If you already have your client certificate and private key bundled into a PKCS#12 file (extension .p12 or .pfx), you can import it into the Android Keychain using the Import menu or Android Settings.
If you don’t have a PKCS#12 file, you can convert your certificate and key files into PKCS#12 form using this openssl command (where cert, key, and ca are your client certificate, client key, and root CA files).
openssl pkcs12 -export -in cert -inkey key -certfile ca -name MyClient -out client.p12
After converting your certificate and key files into PKCS#12 form, import the client.p12 file into OpenVPN Connect using the Import / Import PKCS#12 menu option.
Once you’ve done this, remove the ca, cert, and key directives from your .ovpn file and re-import it. When you connect the first time, the app will ask you to select a certificate to use for the profile. Just select the MyClient certificate, and you should be able to connect normally.
When I try to import a PKCS#12 file, why am I being asked for a password?
When you generate a PKCS#12 file, you’re prompted for an «export password» to encrypt the file. You must enter this password when you import the PKCS#12 file into the Android Keychain. This prevents interception and recovery of the private key during transport.
Why doesn’t the PKCS#12 file in my OpenVPN configuration file work the same as on desktop systems?
Android uses PKCS#12 files differently than on desktops using OpenVPN. Android manages PKCS#12 in the Android Keychain. In contrast, desktops can reference the PKCS#12 files bundled in the OpenVPN profile. The Android approach is much better from a security perspective because the Keychain can leverage hardware features in the device, such as hardware-backed keystores. However, it requires that you load the PKCS#12 file into the Android Keychain separate from importing the OpenVPN profile. It also moves the responsibility for managing PKCS#12 files to the Android Keychain and away from OpenVPN, potentially introducing compatibility issues.
To use a PKCS#12 file on Android, see the FAQ item above: How do I use a client certificate and private key from the Android Keychain?
How do I set up my profile for server failover?
You can provide OpenVPN with a list of servers to make connections. On connection failure, OpenVPN will rotate through the list until it finds a responsive server. For example, the following entries in the profile will first try to connect to server A via UDP port 1194, then TCP port 443, then repeat the process with server B. OpenVPN will continue to retry until it successfully connects or hits the Connection Timeout, which you can configure in Settings.
remote server-a.example.tld 1194 udp remote server-a.example.tld 443 tcp remote server-b.example.tld 1194 udp remote server-b.example.tld 443 tcp
How do I use tasker with OpenVPN Connect for Android?
Follow the steps outlined here: How do I use Tasker with OpenVPN Connect for Android?
You can send in bug reports and feature requests by opening a support ticket and providing the details there.
Please note that if you want to report a security vulnerability, you can do so by following the security disclosure procedure.
Есть рабочая инфраструктура, состоящая из нескольких серверов OpenVPN и некоторого числа клиентов (Windows, Linux и Android).
Клиентские файлы конфигурации для различных платформ выглядят практически одинаково, за исключением мелких архитектурных особенностей каждой из платформ.
Все SSL-сертификаты (серверные и клиентские) для подключения подписаны одним собственным центром сертификации.
Описанная инфраструктура прекрасно работала до одного момента (примерно конец ноября 2016 г.), затем резко перестали подключаться абсолютно все клиенты под Android. При этом в конфигурацию серверов/клиентов не вносилось никаких изменений. OpenVPN-клиенты на других платформах без проблем продолжают работать.
Ошибка на Android-устройстве при попытке подключения:
OpenVPN server certificate verification failed: PolarSSL: SSL read error: X509 - Certificate verification failed, e.q. CRL, CA or signature check failed.Полная версия лога:
Скриншот
Продолжение
Лог сервера в момент подключения:
Wed Feb 1 22:53:11 2017 us=989593 MULTI: multi_create_instance called
Wed Feb 1 22:53:11 2017 us=989754 Re-using SSL/TLS context
Wed Feb 1 22:53:11 2017 us=989905 LZO compression initialized
Wed Feb 1 22:53:11 2017 us=990087 Control Channel MTU parms [ L:1560 D:168 EF:68 EB:0 ET:0 EL:0 ]
Wed Feb 1 22:53:11 2017 us=990149 Data Channel MTU parms [ L:1560 D:1450 EF:60 EB:135 ET:0 EL:0 AF:3/1 ]
Wed Feb 1 22:53:11 2017 us=991052 Local Options String: 'V4,dev-type tun,link-mtu 1560,tun-mtu 1500,proto TCPv4_SERVER,comp-lzo,keydir 0,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method 2,tls-server'
Wed Feb 1 22:53:11 2017 us=991138 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1560,tun-mtu 1500,proto TCPv4_CLIENT,comp-lzo,keydir 1,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method 2,tls-client'
Wed Feb 1 22:53:11 2017 us=991187 Local Options hash (VER=V4): '9915e4a2'
Wed Feb 1 22:53:11 2017 us=991226 Expected Remote Options hash (VER=V4): '2f2c6498'
Wed Feb 1 22:53:11 2017 us=991277 TCP connection established with [AF_INET]192.168.0.104:58009
Wed Feb 1 22:53:11 2017 us=991309 TCPv4_SERVER link local: [undef]
Wed Feb 1 22:53:11 2017 us=991340 TCPv4_SERVER link remote: [AF_INET]192.168.0.104:58009
RWed Feb 1 22:53:11 2017 us=991762 192.168.0.104:58009 TLS: Initial packet from [AF_INET]192.168.0.104:58009, sid=d7485053 5ae035e5
WRWRWWWWRWRWRWRWRWRWRWRWRWRWRWRWRWRWRWRWRW
Wed Feb 1 22:53:12 2017 us=157279 192.168.0.104:58009 Connection reset, restarting [0]
Wed Feb 1 22:53:12 2017 us=157426 192.168.0.104:58009 SIGUSR1[soft,connection-reset] received, client-instance restarting
Wed Feb 1 22:53:12 2017 us=157552 TCP/UDP: Closing socketВерсия OpenVPN-клиента под Android:
OpenVPN Connect 1.1.17 (build 76)
OpenVPN core 3.0.12 android armv7a thumb2 32-bit built on May 24 2016 09:42:05Версия OpenVPN на сервере:
OpenVPN 2.3.6 x86_64-redhat-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [MH] [IPv6] built on Dec 2 2014
library versions: OpenSSL 1.0.1e-fips 11 Feb 2013, LZO 2.03Примечание: данная ошибка возникает и при попытках подключения к серверу с более новой версией.
Если перенести конфигурацию для Android со всеми файлами, сертификатами и т. д. на любую другую платформу — все Ok.
Причем, данная ошибка появилась одномоментно для всех Android-устройств (планшеты, телефоны), подключающихся из разных мест (разные Интернет-провайдеры) к различным серверам (разные хостинги).
На сегодняшний день я так и не нашел причину данной ошибки и путь для ее решения 
Товарищи, коллеги — прошу поделиться любыми мыслями и доводами на этот счет. При необходимости выложу конфигурационные файлы сервера/клиента, или другую интересующую информацию.
-
ВАЖНО!
Перед началом поиска проблем убедитесь, что все галочки на страницах «Гостевой доступ», «Белый список», «Маршрут по умолчанию» в вашем персональном разделе системы сняты! Это поможет локализовать и исправить ошибку быстрее.
Помните, что настройки туннелей в системе VPNKI применяются при переподключении туннеля. Поэтому при изменении информации в личном кабинете системы всегда переподключайте все туннели в вашем аккаунте.
Шаг 1. Подключение
1.0. Если соединения нет, то первым делом проверьте, что ваш внешний IP адрес не заблокирован в нашей системе. Узнать свой белый IP адрес можно, например, задав в поиске Яндекса фразу «IP address». Запомните адрес, а потом посмотрите на перечень заблокированных IP адресов в нашей системе. Этот список можно найти на странице «Инструменты» — «Заблокированные IP адреса».
1.1. Самая рапространненая причина невозможности устрановления соединения — ошибка в имени пользователя и пароле.
1.2. Если вы несколько раз включали и выключали OpenVPN сервер на личной странице системы, то имеет смысл проверить файл ovpn. Зайдите в личный кабинет, посмотрите параметры включенного сервера. Вас должен интересовать порт, тип протокола (UDP или TCP), а также наличие или отсутствие шифрования. Затем откройте любым редактором загруженный файл профиля и сравните параметры с тем, что есть на сайте системы. Порт будет указан в сроке remote msk.vpnki.ru 3….. . Тип протокола в строке proto tcp или proto udp. Наличие или отсутствие шифрования будут указаны в строке cipher AES-128-CBC или cipher none.
1.4. Если вы все сделали верно, но соединение не устанавливается, то обратитесь к нам в форум.
Сформулируйте ситуацию, сообщите время/дату неуспешного подключения, тип используемого протокола, а также имя пользователя, чье соединение не установилось.
Результат этого шага — Соединение установлено.
Шаг 2. Подключение установлено, как мне проверить что я на верном пути?
2.1. После установления соединения ваше устройство автоматически получит адрес из сети 172.16.0.0/16.
После этого вы должны успешно пинговать адрес сервера vpnki путем выполнения команды ping 172.16.0.1 на своем устройстве.
Для Android существует множество утилит для пинга. Мы, например, используем утилиту Ping & DNS из Google Play. Она содержит в себе не только «пинговалку», но и прочие инстументы. К примеру можно посмотреть перечень интерфейсов, таблицу маршрутов (правда не полную) и прочую нужную информацию.
Если пинг не проходит, то убедитесь что новый интерфейс на вашей системе создался. В утилите Ping & DNS вы можете нажать кнопку Network Info и поискать в выводе интерфейс tunX.
Если интерфейс создан, адрес получен, то пинг адреса 172.16.0.1 должен быть успешным.
Результат этого шага — команда ping 172.16.0.1 выполняется успешно.
Шаг 3. Подключение установлено, пинг адреса 172.16.0.1 успешен. Что дальше?
Дальнейшие действия связаны с наличием маршрутной информации. Дело в том, что после подключения, адрес сервера VPNKI — 172.16.0.1 является адресом, напрямую подключенным к вашему устройству по каналу точка-точка. По этой причине ваше устройство «знает» об этом адресе и успешно пингует его.
Однако, на этом этапе, ваше устройство не обладает информацией о других адресах вашей сети VPNKI. Первым шагом будет являться «обучение» вашего устройства новому маршруту к сети VPNKI 172.16.0.0/16 .
Именно в этой сети находятся все ваши прочие туннели. Подключаясь по протоколу OpenVPN вы должны автоматически получить маршрут к сети 172.16.0.0/16.
Эта сеть должна быть доступна через адрес сервера VPNKI — 172.16.0.1 .
После записи маршрута в таблицу Android вы должны успешно выполнить пинг своего «другого устройства», подключенного к сети VPNKI по его адресу 172.16.x.x. Выполните команду ping 172.16.x.x
Однако обращаем внимание.
— второе устройство также должно содержать в своей таблице маршрутов путь к сети 172.16.0.0/16. Это необходимо для отправки ответов на ваш пинг.
— на втором вашем устройстве межсетевой экран не должен блокировать ответы на пакеты icmp. Проверить принципиальную возможность ответов устройства на пакеты утилиты ping вы можете с нашей страницы «Инструменты», указав адрес устройства. Если вы уверены, что устройство настроено правильно, но пинги с этой страницы не проходят, то смотрите настройки своего устройства, относящиеся к протоколу icmp.
Результат этого шага — наличие маршрута к сети 172.16.0.0/16 в таблице маршрутов Android устройства и успешный пинг вашего второго устройства по адресу 172.16.x.x.
Шаг 4. Пинг моего другого устройства по адресу 172.16.x.x успешен. А как выполнить пинг другого устройства по его внутреннему адресу 192.168.x.x?
Дальше начинается действие, ради которого все и затевалось — получение одним устройством c ОС Android доступа к внутренней сети, расположенной за вторым устройством (маршрутизатором). Эти действия связаны с наличием маршрутной информации о сети «за» маршуртизатором и почти аналогичны предыдущему шагу, но с некоторыми отличиями. Теперь нам необходимо не только обучить ваш Android «знанию» о сети 172.16.0.0/16, что было выполнено на предыдущем шаге/ Теперь ему необходимо дать информацию о сети, расположенной «за» маршрутизатором вашего второго туннеля.
Прежде чем приступить к этому шагу вы должны убедиться в том, что сеть «за» вашим маршрутизатором НЕ пересекается с сетью, в которую подключено ваше Андроид устройство. То есть, если ваш Андроид находится в сети 192.168.0.0/24 (например дом) и такая же сеть 192.168.0.0/24 расположена за вторым устройством (например дача), то такая конфигурация будет некорректной. Из этой ситуации есть два выхода:
— перенастроить одну из сетей на другую схему адресации, например 192.168.1.0/24.
— осуществить трансляцию портов на вашем втором устройстве в адрес, полученный от сети vpnki 172.16.x.x. Эту конфигурацию мы не будем рассматривать в рамках настоящего документа.
Стоит отметить, что маршрут о вашей «другой» сети поступит на ваш Андроид при установлении OpenVPN подключения автоматически.
Обращаем внимание:
— второе устройство (маршрутизатор) должно содержать в своей таблце маршрутов путь к сети 172.16.0.0/16 для отправки ответов на ваш пинг.
— на втором вашем устройстве (маршрутизаторе) межсетевой экране не должен блокировать ответы на пакеты icmp.
Результат этого шага — успешный пинг вашего второго устройства по его внутреннему адресу 192.168.1.x.
PS: В целях борьбы с зависшими сессиями мы принудительно отключаем пользовательские туннели с протоколом OpenVPN в 00:00 по Московскому времени. При правильной настройке соединения должны автоматически переустановиться.
Рекомендации по выбору тарифа
Если вы не планируете передачу видео трафика, то мы рекомендуем вам начинать с выбора тарифа PLAN-MYDEV. Если передача видео будет осуществляться, то стоит сразу начинать с PLAN-VIDEO. Если скорости хватать не будет, то в любое время вы можете изменить тариф на более скоростной.
Если вы используете нашу систему для решения бизнес задач, то можно начать с аналогичных тарифов с приставкой BUSINESS-.
Контролировать объем переданного трафика вы можете на странице с графиками использования.
Узнать реальную скорость своего VPN соединения вы можете утилитой iperf3 на странице «Инструменты». Стоит отметить, что скорость передачи полезных данных будет зависеть от трех факторов:
- от типа используемого протокола VPN;
- типа используемого транспортного протокола — TCP или UDP;
- физической удаленности вашего устройства от нашего сервера.
Худшим вариантом по скорости окажется вариант, когда в качестве транспортного протокола для VPN соединения используется протокол TCP. При этом ваше устройство размещено далеко от сервера VPNKI. В этом случае, реальная скорость передачи данных будет определяться необходимостью подтверждения получения каждого пакета в протоколе TCP.
ДОПОЛНИТЕЛЬНО ПО ТЕМЕ КОНФИГУРАЦИИ УДАЛЕННОГО ДОСТУПА
- Рабочий стол Windows через RDP и OpenVPN. Ссылка здесь.
- Выставить FTP сервер в сеть Интернет через проброс TCP порта. Ссылка здесь.
ОБЩАЯ ИНФОРМАЦИЯ ОБ УДАЛЕННОМ ДОСТУПЕ
- Немного более подробно про IP адреса. Можно прочитать на нашем сайте.
- Про удалённый доступ к компьютеру можно. Можно почитать на нашем сайте.
- Про VPN и протоколы можно почитать здесь.
- Про выход в Интернет через VPN и центральный офис. Можно почитать здесь.
To make issues more manageable, I would appreciate if you fill out the details if applicable
General information
- Android 6.0.1
- MIUI 8.0.5 Global Stable
- Xiaomi Mi 5
- Version 0.6.60 from play store
Can’t import OpenVPN profile file from local storage (I’ve tried both .ovpn and .conf extensions) — it just don’t see any files in folder. So I had to create profile manually and import each cert file separetely plus edit some settings. Can you fix this?
P.S. I have theory that this is firmware bug, when file explorer cannot filter extensions with 4 symbols. In that case it would be nice to remove filter at all to see all files.
-
ketues
- OpenVpn Newbie
- Posts: 6
- Joined: Sun Nov 04, 2018 3:24 pm
Android client does not connect OpenVPN
Good afternoon. I have a problem with my OpenVPN server that I am not able to solve. I no longer have ideas to fix it, so I ask you for help to see if you can come up with a solution.
For 1 year my OpenVPN worked perfectly, I changed the router of the telephone company and I stopped running OpenVPN. In the new router I have opened the TCP / UDP ports to natear the IP of the server.
The server is a raspberry pi 2.
The client is an Android 7 phone.
This is the OpenVPN client log:
Code: Select all
15:42:14.295 -- ----- OpenVPN Start -----
15:42:14.296 -- EVENT: CORE_THREAD_ACTIVE
15:42:14.302 -- Frame=512/2048/512 mssfix-ctrl=1250
15:42:14.307 -- UNUSED OPTIONS
4 [resolv-retry] [infinite]
5 [nobind]
6 [persist-key]
7 [persist-tun]
11 [verify-x509-name] [server_D2SVcFLhsDCR] [name]
15 [verb] [3]
15:42:14.309 -- EVENT: RESOLVE
15:42:14.320 -- Contacting 95.160.128.123:51025 via TCP
15:42:14.322 -- EVENT: WAIT
15:42:14.358 -- Connecting to [dominio.com]:51025 (95.160.128.123) via TCPv4
15:42:14.401 -- EVENT: CONNECTING
15:42:14.405 -- Tunnel Options:V4,dev-type tun,link-mtu 1572,tun-mtu 1500,proto TCPv4_CLIENT,comp-lzo,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client
15:42:14.408 -- Creds: UsernameEmpty/PasswordEmpty
15:42:14.410 -- Peer Info:
IV_GUI_VER=OC30Android
IV_VER=3.2
IV_PLAT=android
IV_NCP=2
IV_TCPNL=1
IV_PROTO=2
IV_LZO=1
IV_AUTO_SESS=1
15:42:14.641 -- VERIFY OK : depth=1
cert. version : 3
serial number : E2:18:54:E0:20:62:E0:E0
issuer name : CN=ChangeMe
subject name : CN=ChangeMe
issued on : 2018-04-27 20:11:59
expires on : 2028-04-24 20:11:59
signed using : RSA with SHA-256
RSA key size : 2048 bits
basic constraints : CA=true
key usage : Key Cert Sign, CRL Sign
15:42:14.643 -- VERIFY OK : depth=0
cert. version : 3
serial number : 01
issuer name : CN=ChangeMe
subject name : CN=server_D2SVc2LhsDCR
issued on : 2018-04-27 20:12:07
expires on : 2028-04-24 20:12:07
signed using : RSA with SHA-256
RSA key size : 2048 bits
basic constraints : CA=false
key usage : Digital Signature, Key Encipherment
ext key usage : TLS Web Server Authentication
15:42:14.838 -- TCP recv EOF
15:42:14.840 -- Transport Error: Transport error on 'dominio.com: NETWORK_EOF_ERROR
15:42:14.841 -- EVENT: TRANSPORT_ERROR info='Transport error on 'dominio.com: NETWORK_EOF_ERROR'
15:42:14.845 -- Client terminated, restarting in 5000 ms...
15:42:19.845 -- EVENT: RECONNECTING
15:42:19.854 -- EVENT: RESOLVE
On the Raspberry with the command: «netstat -atn» I see that the communication arrives at port 51025 as established
Code: Select all
pi@server:~ $ netstat -atn
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:51025 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 192.168.1.199:51025 31.42.159.116:2479 ESTABLISHED
tcp 0 172 192.168.1.199:22 192.168.1.50:38336 ESTABLISHED
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
What I can do?
Thank you!!
-
flint2003
- OpenVPN User
- Posts: 23
- Joined: Mon Sep 24, 2018 11:48 am
Re: Android client does not connect OpenVPN
Post
by flint2003 » Fri Nov 16, 2018 10:54 am
Hi all.
It seems to me that the best way will be to install a new client on WIndows machine and test the new connection
It will the integer answer about the workability of your system
-
ketues
- OpenVpn Newbie
- Posts: 6
- Joined: Sun Nov 04, 2018 3:24 pm
Re: Android client does not connect OpenVPN
Post
by ketues » Sun Feb 03, 2019 6:05 pm
flint2003 wrote: ↑
Fri Nov 16, 2018 10:54 am
Hi all.
It seems to me that the best way will be to install a new client on WIndows machine and test the new connection
It will the integer answer about the workability of your system
Hi flint2003
I create a new client called: «pruebas.ovpn», and this is their log:
*********************
18:51:15.317 — EVENT: RECONNECTING
18:51:15.320 — EVENT: RESOLVE
18:51:15.327 — Contacting 95.xxxx:51xxxx via TCP
18:51:15.336 — EVENT: WAIT
18:51:15.370 — Connecting to [xxxxx.com]:51xxx (95.xxxx) via TCPv4
18:51:15.426 — EVENT: CONNECTING
18:51:15.432 — Tunnel Options:V4,dev-type tun,link-mtu 1572,tun-mtu 1500,proto TCPv4_CLIENT,comp-lzo,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client
18:51:15.434 — Creds: UsernameEmpty/PasswordEmpty
18:51:15.436 — Peer Info:
IV_GUI_VER=OC30Android
IV_VER=3.2
IV_PLAT=android
IV_NCP=2
IV_TCPNL=1
IV_PROTO=2
IV_LZO=1
IV_AUTO_SESS=1
18:51:15.685 — VERIFY OK : depth=1
cert. version : 3
serial number : E2:18:54:8C:xxxxx
issuer name : CN=ChangeMe
subject name : CN=ChangeMe
issued on : 2018-04-27 20:11:59
expires on : 2028-04-24 20:11:59
signed using : RSA with SHA-256
RSA key size : 2048 bits
basic constraints : CA=true
key usage : Key Cert Sign, CRL Sign
18:51:15.686 — VERIFY OK : depth=0
cert. version : 3
serial number : 01
issuer name : CN=ChangeMe
subject name : CN=server_D2SVcxxxxx
issued on : 2018-04-27 20:12:07
expires on : 2028-04-24 20:12:07
signed using : RSA with SHA-256
RSA key size : 2048 bits
basic constraints : CA=false
key usage : Digital Signature, Key Encipherment
ext key usage : TLS Web Server Authentication
18:51:15.868 — TCP recv error: Connection reset by peer
18:51:15.869 — Transport Error: Transport error on ‘xxxxxx.com: NETWORK_RECV_ERROR
18:51:15.870 — EVENT: TRANSPORT_ERROR info=’Transport error on ‘xxxxxx.com: NETWORK_RECV_ERROR’
18:51:15.873 — Client terminated, restarting in 5000 ms..
.
************************************************
This is a server netstat -atn log:
17:50:43.178590 IP 47-xxxxx.14840 > 192.xxxxx.5xxx: Flags [P.], seq 1767:1873, ack 2517, win 340, options [nop,nop,TS val 27007222 ecr 2285711952], length 106
17:50:43.178734 IP 192.xxxx.5xxxx > 47xxxxx.14840: Flags [R], seq 210957447, win 0, length 0
Thank you, so much!!
Здравствуйте.
Можно с разрешения ТС подобный вопрос задать, чтоб темы не плодить.
Подскажите пожалуйста. Поднял сервер openvpn на ubuntu server 18.04, на микрот установил сертификат и ключ. Пробую соединиться — не получается.
Лог сервера:
Код: Выделить всё
Thu Nov 14 01:32:07 2019 TCP connection established with [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS: Initial packet from [AF_INET]***.***.***.***:53340, sid=53ffafd8 2edccd19
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 Fatal TLS error (check_tls_errors_co), restarting
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 SIGUSR1[soft,tls-error] received, client-instance restartingконфигурация сервера:
Код: Выделить всё
port 1194
# Протокол может быть UDP или TCP, я выбрал 1-й вариант.
proto tcp
# Если вы выберите протокол TCP, здесь должно быть устройство tap. Однако, это вариант я не проверял, поэтому ищите информацию отдельно. FIXME
dev tun
# Указываем где искать ключи
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
key /etc/openvpn/keys/server.key # This file should be kept secret
dh /etc/openvpn/keys/dh2048.pem
# Для 12.04 dh1024.pem
# Задаем IP и маску виртуальной сети. Произвольно, но если не уверены лучше делайте как показано здесь
server 10.8.0.0 255.255.255.0
# Указыем, где хранятся файлы с настройками IP-адресов клиентов (создадим ниже)
client-config-dir ccd
# Запоминать динамически выданные адреса для VPN-клиентов и при последующих подключениях назначать те же значения.
ifconfig-pool-persist ipp.txt
# Указываем сети, в которые нужно идти через туннель (сеть-клиента).
route 192.168.0.0 255.255.255.0
# Включаем TLS
tls-server
tls-auth /etc/openvpn/keys/ta.key 0
tls-timeout 120
auth SHA1
cipher AES-256-CBC
# Если нужно, чтобы клиенты видели друг друга раскомментируйте
;client-to-client
keepalive 10 120
# Сжатие трафика
;comp-lzo
# Максимум клиентов
max-clients 10
user nobody
group nogroup
# Не перечитывать ключи, не закрывать и переоткрывать TUNTAP устройство, после получения SIGUSR1 или ping-restart
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
# Детальность логирования
verb 3
# Защита от повторов (максимум 20 одинаковых сообщений подряд)
mute 20
# Файл отозванных сертификатов. Разремить, когда такие сертификаты появятся.
;crl-verify /etc/openvpn/crl.pemлог с микрота:
Настраивал по мануалу с вики ubuntu.ru
Где может быть ошибка?
благодарю
Guide
2018-11-19
02:57 PM
OpenVPN Not connecting in Orbi system
Hi, i have a brandnew ORBI RBK23 system (1 router, 2 satellites), router connected to cable modem. The ORBI router as replacement for a Nighthawk R7000, on which a VPN service worked flawlessly. Connection with Samsung Android smart phone as well as iPad without problems, but Windows Notebook problems with certificates.
But not on the new ORBI: nothing at all works as far as VPN is concerned.
I did all the settings as prescribed, downloaded the right client .ovpn file, but to no avail.
Any suggestions?
HELP PLEASE!
(Firmware: v2.2.1.210; service type TUN mode: TCP; service type TAP mode: UDP; clients access VPN: all internet sites as well as home network)
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 1 of 19
Guide
2018-11-20
01:22 AM
Re: OpenVPN Not connecting in Orbi system
FOUND IT! Thanks to you. I changed the settings of TUN back to UDP and now it is working all right! I forgot that I initially tested it over the home network and as you said, that does not work (but it did on my previous router, so that caused my confusion). When I set the wifi on my iPad to my smart phone 4G hotspot, it works fine now!!
The only thing that is still bothering me is the lg in the windows client (notebook with windows 10). Connection is achieved all right, but in the log I see this:
Tue Nov 20 10:03:33 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Tue Nov 20 10:03:44 2018 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Should I start a new topic on this, or may I ask your opinion about this too? (I tried to understand what is explained in the provided openvpn.net link, but can’t get a grip on the contents; seems that I have to do a lot of programming, which seems very difficult).
But anyhow, by this conversation with you, my problems with the connection, anyway on my iPad as well as my android smart phone, are completely solved! Thank you very much!
Message 8 of 19
Master
2018-11-19
03:45 PM
Re: OpenVPN Not connecting in Orbi system
I have VPN working well on iPhone and iPad.
— What happens when it does not work for you?
— Do you see any event in Logs when VPN is tried? This can show if the VPN connection request arrives to Orbi.
— Is DDNS configured correctly and working? Do you get the correct status when clicking “Status” in the DDNS tab?
— Please note that you can’t try VPN connection while connected to your own wifi or another network using the same IP range as your own LAN.
My Setup | Internet Fiber ONT 250↓/250↑ | ISP Telenor | Wifi Router Orbi RBR850 + RBS850 + 2x RBS750 + 3xRBS350, Wired/Wireless BH / Orbi RBR50 + 6x RBS50 + RBS40V + RBS50Y, Wired/Wireless BH | Switches NG GS208 | Time Zone CET (Sweden)
Message 2 of 19
Guide
2018-11-19
04:19 PM
Re: OpenVPN Not connecting in Orbi system
Thanks for responding!
what happens is that i get time outs. In the log files i see each time the same error: «TCP rcv EOF» followed by «TRANSPORT_ERROR Transport error on ‘(my name).mynetgear.com: NETWORK_EOF_ERROR [ERR]»
in the DDNS, with clicking on «show status» i get the message, after a few seconde of waiting, that an update was performed a few days ago (correct, that was when i tried to setup my VPN first time) on (my name).mynetgear.com.
does this give you any clues?
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 3 of 19
Master
2018-11-19
04:33 PM
Re: OpenVPN Not connecting in Orbi system
Before starting “deeper” troubleshooting, can you please first untick “Enable VPN Service” option under VPN and click Apply, then tick it again and click Apply. Anything changes?
My Setup | Internet Fiber ONT 250↓/250↑ | ISP Telenor | Wifi Router Orbi RBR850 + RBS850 + 2x RBS750 + 3xRBS350, Wired/Wireless BH / Orbi RBR50 + 6x RBS50 + RBS40V + RBS50Y, Wired/Wireless BH | Switches NG GS208 | Time Zone CET (Sweden)
Message 4 of 19
Guide
2018-11-19
11:29 PM
Re: OpenVPN Not connecting in Orbi system
Did what you suggested, nothing changed, i keep the logged error (EOF error).
Also rebooted several times, but again, same problem.
Should i perform a total reset and renew installation? (Don’t like the idea, but on the other hand, it can be done if you think that’s wise).
Or should i delete my mynetgear address and start from scratch there, with a new address on mynetgear.com?
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 5 of 19
Master
2018-11-19
11:38 PM
Re: OpenVPN Not connecting in Orbi system
— You mentioned that your TUN Mode is set to TCP. Any reason for that? The default (which I have working) is UDP.
My Setup | Internet Fiber ONT 250↓/250↑ | ISP Telenor | Wifi Router Orbi RBR850 + RBS850 + 2x RBS750 + 3xRBS350, Wired/Wireless BH / Orbi RBR50 + 6x RBS50 + RBS40V + RBS50Y, Wired/Wireless BH | Switches NG GS208 | Time Zone CET (Sweden)
Message 6 of 19
Guide
2018-11-19
11:46 PM
Re: OpenVPN Not connecting in Orbi system
Did that after the initial udp option did not work (same problem), and on the former router Nighthawk R7000, this was the working setting…
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 7 of 19
Guide
2018-11-20
01:22 AM
Re: OpenVPN Not connecting in Orbi system
FOUND IT! Thanks to you. I changed the settings of TUN back to UDP and now it is working all right! I forgot that I initially tested it over the home network and as you said, that does not work (but it did on my previous router, so that caused my confusion). When I set the wifi on my iPad to my smart phone 4G hotspot, it works fine now!!
The only thing that is still bothering me is the lg in the windows client (notebook with windows 10). Connection is achieved all right, but in the log I see this:
Tue Nov 20 10:03:33 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Tue Nov 20 10:03:44 2018 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Should I start a new topic on this, or may I ask your opinion about this too? (I tried to understand what is explained in the provided openvpn.net link, but can’t get a grip on the contents; seems that I have to do a lot of programming, which seems very difficult).
But anyhow, by this conversation with you, my problems with the connection, anyway on my iPad as well as my android smart phone, are completely solved! Thank you very much!
Message 8 of 19
Master
2018-11-20
01:30 AM
Re: OpenVPN Not connecting in Orbi system
Glad that this helped. Good luck
My Setup | Internet Fiber ONT 250↓/250↑ | ISP Telenor | Wifi Router Orbi RBR850 + RBS850 + 2x RBS750 + 3xRBS350, Wired/Wireless BH / Orbi RBR50 + 6x RBS50 + RBS40V + RBS50Y, Wired/Wireless BH | Switches NG GS208 | Time Zone CET (Sweden)
Message 9 of 19
Guide
2018-11-20
01:54 AM
Re: OpenVPN Not connecting in Orbi system
and to be complete for all readers of this topic, about the added questions concerning the log file of the windows client connection:
the line about the warning of certificates vanishes if one adds the line «remote-cert-tls server» to the .OVPN config file
the second warning, about the passwords cache, is of no real siginificance and can be ignored.
again many thanks to ekhalil!
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 10 of 19
Aspirant
2018-11-20
11:59 AM
Re: OpenVPN Not connecting in Orbi system
I’m having the same issue…I cant seem to connect to my VPN on windows 10. I am able to connect to it no problem on my iphone and ipad. But on windows 10, I’m getting this in the log file:
Enter Management Password:
Tue Nov 20 14:47:48 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Tue Nov 20 14:48:53 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Tue Nov 20 14:49:58 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Tue Nov 20 14:51:05 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Tue Nov 20 14:52:11 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Any help would be appreciated. Thanks in advance
_______________________________________________________________________________________________________________
UPDATE: I was trying to connect while on my home network (not sure if that matters). I tried while on my iphone hotspot and his is what i get:
Enter Management Password:
Tue Nov 20 15:02:04 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Tue Nov 20 15:02:06 2018 TAP-Windows adapter ‘NETGEAR-VPN’ not found
Model: RBK50| Orbi AC3000 High-Performance Tri-Band WiFi System
Message 11 of 19
Aspirant
2018-11-20
12:21 PM
Re: OpenVPN Not connecting in Orbi system
Ok, UPDATE #2: After researching the last log file entry, I renamed the TAP Windows Adapter to «NETGEAR-VPN». Now I’m getting:
Enter Management Password:
Tue Nov 20 15:12:08 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Tue Nov 20 15:12:08 2018 Could not determine IPv4/IPv6 protocol
Tue Nov 20 15:12:13 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
I just cant win!! I already researched that as well and cant seem to find info on it. Now any help would be appreciated. Sorry, and thanks in advance
Model: RBK50| Orbi AC3000 High-Performance Tri-Band WiFi System
Message 12 of 19
Guide
2018-11-20
01:18 PM
Re: OpenVPN Not connecting in Orbi system
Well, since I got it running, you should be able to run it too, especially with your equipment!
I suppose you have the newest ORBI firmware, and you have a valid mynetgear.com account. And you downloaded the right files (those for Windows) from the router.
In VPN settings, leave the TUN service mode and TAP service mode as it is (so leave TUN to UPD and do not change it, like I tried to no avail, to TCP)
You already renamed the TAP adapter to NETGEAR-VPN, that is necessary too.
Did you also add the line «remote-cert-tls server» to your client.ovpn file? Because when you did, the warning about the certificates should not appear. Are you sure that the (in this way edited) client.ovpn is in the C:program filesopenvpnconfig subdirectory?
And indeed, it matters that you test your VPN from a different network than your ORBI network.
Please check the above issues and let us know if this helps?
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 13 of 19
Aspirant
2018-11-20
01:53 PM
Re: OpenVPN Not connecting in Orbi system
Thanks for the fast reply…
- Yes the router and satellites are on the current firmwares
- Yes my mynetgear account is valid
- Yes I downloaded the correct config files for windows
- Both TUN and TAP are default and havnet been changed
- Yes I renamed the adapter to NETGEAR-VPN as you stated
- No, I did not add that line to my config file. Is that simply added that to the send line? My config file is 1 line long…very long and nothing else. Do I add it with quotes or without?
Here is my current config file:

client
dev tap
proto udp
dev-node NETGEAR-VPN
remote (removed for privacy) 12974
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client.crt
key client.key
cipher AES-128-CBC
comp-lzo
verb 0
sndbuf 393216
rcvbuf 393216
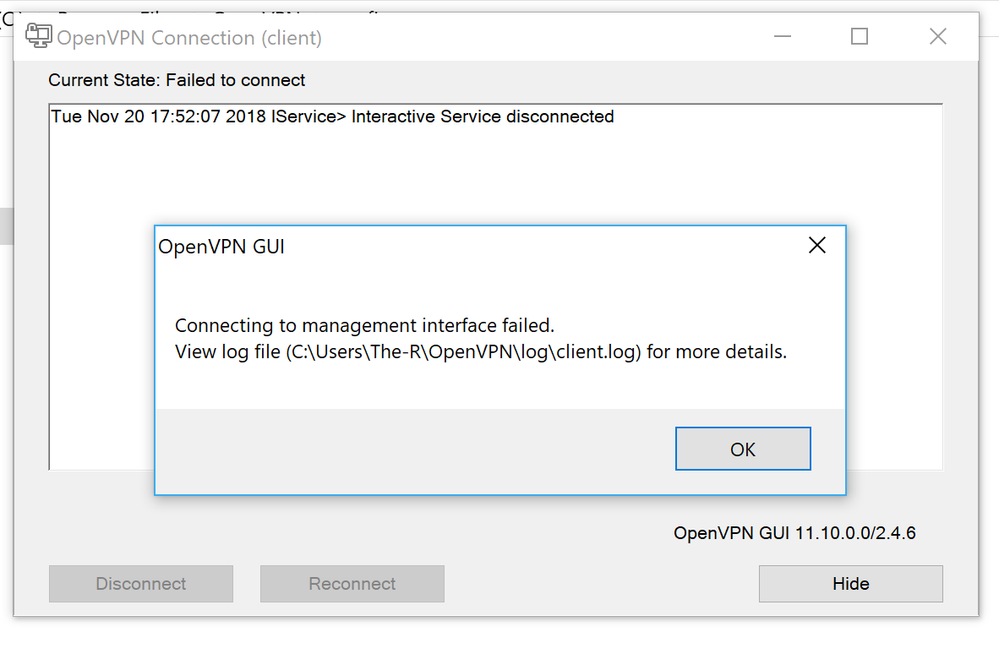
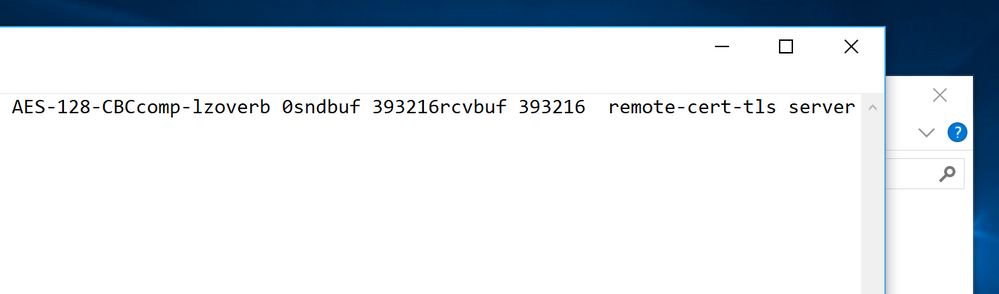
Not sure why it pasted as being multiple lines, that’s why i included the image.
- Lastly, yes, the config file is in the correct directory
I actually gave up until i saw your reply. I will keep at it, but its very frustrating and shouldn’t be this hard.
Message 14 of 19
Aspirant
2018-11-20
02:01 PM
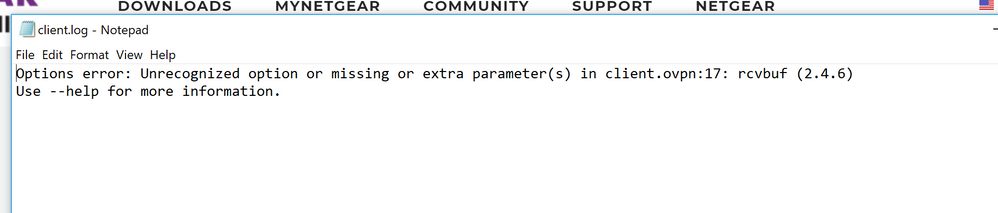
Re: OpenVPN Not connecting in Orbi system
Also, opening the config file in notepad:
I added remote-cert-tls server without the quotes at the very end and when i go to save it, it says i dont have permission and need to seek file owner or administrator. I am the administrator on the machine, only 1 user.
Message 15 of 19
Guide
2018-11-20
02:25 PM
Re: OpenVPN Not connecting in Orbi system
Yes, that is what i saw too. So what i did was editing the ovpn file in the download directory and then copied the new / edited file to the config subdir. Here too the system complained about my rights, but there was the option to continue as administrator. And that worked.
The line is indeed to be placed at the end of the file, i put it right at the end, two spaces after the last character.
And indeed without he quotation marks!
Please inform about the result!
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 16 of 19
Aspirant
2018-11-20
03:01 PM
Re: OpenVPN Not connecting in Orbi system
Thanks again for your help…i really appreciate it.
New Errors — New Logs…so maybe a step in the right direction. BUT, you’re right, i’m not geting the «certificate» warning anymore
Message 17 of 19
Guide
2018-11-21
03:08 AM
Re: OpenVPN Not connecting in Orbi system
I am very sorry your problem still exists…
Btw, your client.ovpn contains exactly the same lines as mine, only mine is one long line without hard returns (in notepad), and no spaces between the lines as compared to yours (where there are hard returns). I wonder why you apparently downloaded another format…
What exactly are the «new ERRORs» you write about in your last post?
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 18 of 19
Guide
2018-11-22
08:18 AM
Re: OpenVPN Not connecting in Orbi system
Ah, now i can see the errors, but i do not understand them…
You have the exact lines in your (as compared to my) client.ovpn, and i also tried what would happen if i make it a file with neat 18 lines (the 18th being the added line remote-cert-tls server). No difference, works equal flawlessly.
The only possible difference (but i do not know its significance) is that you keep also a client file in the C:users(user)openvpnconfig? Because i have not (the only place is the C:program filesopenvpnconfig, along with the 3 other files of course (ca.crt, client.crt and client.key).
If the problem still exists, you might try the good old reboot of your system and / or try the whole operation without the protection of firewalls etc.
I am afraid i can’t be of further assistance (being kind of a novice myself!)
Good luck, and please post again if you have (hopefully good) news flashes!
Model: RBK22| Orbi AC2200 Tri-band WiFi System
Message 19 of 19
Hello!
I’m trying to connect with my samsung galaxy tab note 12.2 Android Version 4.4.2 to my QNAP TS-563 Version 4.2.1 (19.04.2016), but I get always a Connection Timeout.
If I try to connect with my IPhone with the same configuration apart from the deleted last line, the connect works fine.
Here is my configuration:
Code: Select all
client
dev tun2001
script-security 3
proto udp
remote myHome 1194
resolv-retry infinite
nobind
<ca>
-----BEGIN CERTIFICATE-----
....
-----END CERTIFICATE-----
</ca>
auth-user-pass
reneg-sec 0
cipher AES-128-CBC
tls-cipher TLS-SRP-SHA-RSA-WITH-3DES-EDE-CBC-SHA:TLS-DHE-RSA-WITH-AES-128-CBC-SHA:TLS-DHE-RSA-WITH-AES-256-CBC-SHA
comp-lzo
setenv CLIENT_CERT 0And here is my openVPN-Log:
Code: Select all
I/OpenVPNService(13685): ConnectivityReceiver: SCREEN_ON pvbs=false
D/OpenVPNService(13685): SERV: client attach n_clients=1
D/OpenVPNService(13685): SERV: onStartCommand action=net.openvpn.openvpn.CONNECT
D/OpenVPNService(13685): SERV: profile file len=1680
I/OpenVPNService(13685): SERV: CONNECT prof=myHome [openvpn] user=marc proxy=undef serv=null proto=adaptive to=60 resp=null epki_alias=null comp=yes
I/OpenVPNService(13685): EVENT: CORE_THREAD_ACTIVE
I/OpenVPNService(13685): LOG: Frame=512/2048/512 mssfix-ctrl=1250
I/OpenVPNService(13685): LOG: UNUSED OPTIONS
I/OpenVPNService(13685): 2 [script-security] [3]
I/OpenVPNService(13685): 5 [resolv-retry] [infinite]
I/OpenVPNService(13685): 6 [nobind]
I/OpenVPNService(13685): 11 [tls-cipher] [TLS-SRP-SHA-RSA-WITH-3DES-EDE-CBC-SHA:TLS-DHE-RSA-WITH-AES-128-C...]
I/OpenVPNService(13685): 13 [setenv] [CLIENT_CERT] [0]
I/OpenVPNService(13685): EVENT: RESOLVE
I/OpenVPNService(13685): LOG: Contacting 1.2.3.4:1194 via UDP
I/OpenVPNService(13685): EVENT: WAIT
D/OpenVPNService(13685): SOCKET PROTECT: fd=57 protected status=true
I/OpenVPNService(13685): LOG: Connecting to [myHome]:1194 (1.2.3.4) via UDPv4
I/OpenVPNService(13685): EVENT: CONNECTING
I/OpenVPNService(13685): LOG: Tunnel Options:V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-128-CBC,auth SHA1,keysize 128,key-method 2,tls-client
I/OpenVPNService(13685): LOG: Creds: Username/Password
I/OpenVPNService(13685): LOG: Peer Info:
I/OpenVPNService(13685): IV_GUI_VER=net.openvpn.connect.android 1.1.17-76
I/OpenVPNService(13685): IV_VER=3.0.12
I/OpenVPNService(13685): IV_PLAT=android
I/OpenVPNService(13685): IV_NCP=2
I/OpenVPNService(13685): IV_TCPNL=1
I/OpenVPNService(13685): IV_PROTO=2
I/OpenVPNService(13685): IV_LZO=1
I/OpenVPNService(13685): LOG: Session invalidated: KEEPALIVE_TIMEOUT
I/OpenVPNService(13685): LOG: Client terminated, restarting in 2...
I/OpenVPNService(13685): EVENT: RECONNECTING
D/OpenVPNService(13685): SOCKET PROTECT: fd=57 protected status=true
I/OpenVPNService(13685): EVENT: RESOLVE
I/OpenVPNService(13685): LOG: Contacting 1.2.3.4:1194 via UDP
I/OpenVPNService(13685): EVENT: WAIT
I/OpenVPNService(13685): LOG: Connecting to [myHome]:1194 (1.2.3.4) via UDPv4
I/OpenVPNService(13685): EVENT: CONNECTING
I/OpenVPNService(13685): LOG: Tunnel Options:V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-128-CBC,auth SHA1,keysize 128,key-method 2,tls-client
I/OpenVPNService(13685): LOG: Creds: Username/Password
I/OpenVPNService(13685): LOG: Peer Info:
I/OpenVPNService(13685): IV_GUI_VER=net.openvpn.connect.android 1.1.17-76
I/OpenVPNService(13685): IV_VER=3.0.12
I/OpenVPNService(13685): IV_PLAT=android
I/OpenVPNService(13685): IV_NCP=2
I/OpenVPNService(13685): IV_TCPNL=1
I/OpenVPNService(13685): IV_PROTO=2
I/OpenVPNService(13685): IV_LZO=1
D/OpenVPNService(13685): pause_on_connection_timeout false
I/OpenVPNService(13685): EVENT: CONNECTION_TIMEOUT
D/OpenVPNService(13685): EXIT: connect() exited, err=false, msg=''
I/OpenVPNService(13685): STAT BYTES_IN=96
I/OpenVPNService(13685): STAT BYTES_OUT=5242
I/OpenVPNService(13685): STAT PACKETS_IN=4
I/OpenVPNService(13685): STAT PACKETS_OUT=33
I/OpenVPNService(13685): STAT KEEPALIVE_TIMEOUT=1
I/OpenVPNService(13685): STAT CONNECTION_TIMEOUT=1
I/OpenVPNService(13685): STAT N_RECONNECT=1
I/OpenVPNService(13685): EVENT: DISCONNECTED
I/OpenVPNService(13685): EVENT: CORE_THREAD_INACTIVE
I/OpenVPNService(13685): ConnectivityReceiver: SCREEN_OFF pvbs=false
What I’m doing wrong?
Best regards,
Marc