CTX203362
{{tooltipText}}
Article
|
How To / General Question
Security Vulnerability
|
{{likeCount}} found this helpful
|
Created:
{{articleFormattedCreatedDate}}
|
Modified:
{{articleFormattedModifiedDate}}
Symptoms or Error
This article is intended for Citrix administrators and technical teams only.Non-admin users must contact their company’s Help Desk/IT support team and can refer to CTX297149 for more information
Receiver for Linux displays the following error when launching published desktops/applications:
You have not chosen to trust «Certificate Authority», the issuer of the server’s security certificate (SSL error 61).
Solution
Important! This article is intended for use by System Administrators. If you are experiencing this issue and you are not a System Administrator, contact your organization’s Help Desk for assistance and refer them to this article.
Update to the Latest Receiver Version
- Upgrade to the latest version of Receiver to verify if this resolves the issue.
- If you are using SHA2 certificates then the older version of Receiver does not support these certificate. Refer to CTX200114 — Citrix Receiver Support for SHA-2 to view the Receiver versions which supports SHA-2 certificates.
If this does not resolve the issue then proceed to the next section.
For information on Receiver feature updates refer to — Citrix Receiver Feature Matrix.
Missing Root/Intermediate Certificate
This error message suggests that the client device does not have the required root certificate/intermediate certificate to establish trust with the certificate authority who issued the server certificate.
Use a root certificate
If you need to authenticate a server certificate that was issued by a certificate authority and is not yet trusted by the user device, follow these instructions before adding a StoreFront store.
- Obtain the root certificate in PEM format.
Tip: If you cannot find a certificate in this format, use the openssl utility to convert a certificate in CRT format to a .pem file. - As the user who installed the package (usually root):
- Copy the file to $ICAROOT/keystore/cacerts.
- Run the following command:
$ICAROOT/util/ctx_rehash
Use an intermediate certificate
If your StoreFront server is not able to provide the intermediate certificates that match the certificate it is using, or you need to install intermediate certificates to support smart card users, follow these steps before adding a StoreFront store.
- Obtain the intermediate certificate(s) separately in PEM format.
Tip: If you cannot find a certificate in this format, use the openssl utility to convert a certificate in CRT format to a .pem file. - As the user who installed the package (usually root):
- Copy the file(s) to $ICAROOT/keystore/intcerts.
- Run the following command as the user who installed the package:
$ICAROOT/util/ctx_rehash
Additional Resources
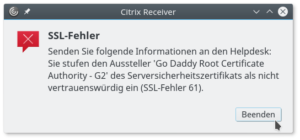
In particular, the problem is about the SSL error 61 in the Citrix (Web) receiver under Linux and how to fix it. Since I have been running almost exclusively under Kubuntu for several months, the Citrix Reiceiver also moved into the new Linux box. Unfortunately, no connection to systems could be established, since the receiver disconnected with the following error message.
SSL Error 61: You have not chosen to trust “Go Daddy Root Certificate Authority – G2”, the issuer to the server’s security certificate.
Now there are two solutions. Either you get the missing certificates and insert them into the following directory:
/opt/Citrix/ICAClient/keystore/cacerts
Or you have Firefox installed… How does Firefox help us? Because the root certificates of Firefox can be shared with the Citrix receiver with only one command via symbolic links. The whole works as follows:
sudo ln -s /usr/share/ca-certificates/mozilla/* /opt/Citrix/ICAClient/keystore/cacerts
In this case, a symbolic link for each root certificate that the Firefox knows is created in the Citrix directory, so that it can participate. Now your SSL error 61 should be gone.
If, for whatever reason, you want to undo the changes, you can run the following two commands:
cd /opt/Citrix/ICAClient/keystore/cacerts sudo find -type l -delete
- Forum
- The Ubuntu Forum Community
- Ubuntu Official Flavours Support
- Networking & Wireless
- [SOLVED] Citrix and SSL Error 61
-
Citrix and SSL Error 61
I’m using Ubuntu 12.04 LTS (32bit) and the latest Linux version of Citrix Receiver. Whenever I try to connect to my work network through Citrix I get the error message below. As far as I can see it’s not true, I *am* trusting the issuer of the server’s security certificate. This error message, (with different issuers) is frequently mentioned on the net but I cannot get any of the many many solutions to work in my case. Any advice would be gratefully received.
SSL error : Contact your help desk with the following information: You have not chosen to trust «/C=US/ST=/L=/O=The Go Daddy Group, Inc./OU=Go Daddy Class 2 Certification Authority/CN=», the issuer of the server’s security certificate (SSL error 61).
-
Re: Citrix and SSL Error 61
Originally Posted by halfhearted
I’m using Ubuntu 12.04 LTS (32bit) and the latest Linux version of Citrix Receiver. Whenever I try to connect to my work network through Citrix I get the error message below. As far as I can see it’s not true, I *am* trusting the issuer of the server’s security certificate. This error message, (with different issuers) is frequently mentioned on the net but I cannot get any of the many many solutions to work in my case. Any advice would be gratefully received.
SSL error : Contact your help desk with the following information: You have not chosen to trust «/C=US/ST=/L=/O=The Go Daddy Group, Inc./OU=Go Daddy Class 2 Certification Authority/CN=», the issuer of the server’s security certificate (SSL error 61).
This is actually straight from Ubuntu’s Citrix help page:
To prevent the following error when accessing remote sessions:
Citrix Receiver
SSL error
Contact your help desk with the following information:
You have not chosen to trust»/C=US/ST=/L=/O=Equifax/OU=Equifax Secure Certificate Authority/CN=», the issuer of the server’s security certificate ((SSL error 61).Make Firefox’s certificates accessible to Citrix, e.g.,
Code:
sudo ln -s /usr/share/ca-certificates/mozilla/* /opt/Citrix/ICAClient/keystore/cacerts
It worked perfectly for me.
-
Re: Citrix and SSL Error 61
Thanks very much damage84. It worked but I don’t understand why. What does «ln -s» mean? Thanks for your help.
-
Re: Citrix and SSL Error 61
Originally Posted by halfhearted
Thanks very much damage84. It worked but I don’t understand why. What does «ln -s» mean? Thanks for your help.
No problem, it works because the root problem is Citrix doesn’t have access to the SSL certificate required to make a secure connection. Since it has no way of guranteeing the connection it rejects / doesn’t connect. What that command does is create a link to Mozilla’s SSL certificates in Citrix’s certificate folder. That’s what ln -s does, it creates a link, like a Windows shortcut so that when Citrix looks in it’s own certicate folder, it sees Mozilla’s certificates so instead of seeing a folder that lacks the right certificate, it sees a folder that has the right certificate so it can verify and make the connection securely.
-
Re: Citrix and SSL Error 61
Hi damaged84.
I’ve tried the solution you gave but got an error :
ln: target `/opt/Citrix/ICAClient/keystore/cacerts’ is not a directoryWhat am I doing wrong?
Thanks!
-
Re: Citrix and SSL Error 61
Well fbrites (if you are still looking) it could be that Citrix hasn’t installed properly and created the folder. See if the other folders in the pathname exist in /opt.
-
Re: Citrix and SSL Error 61
ln -s of certificates from mozilla to citrix is not enough some times.
i had to install the Go Daddy root certificate and the Intermediate certificate, copy them in citrix cacerts dir and it finally works
-
Re: Citrix and SSL Error 61
Originally Posted by rigobertomanchu
ln -s of certificates from mozilla to citrix is not enough some times.
i had to install the Go Daddy root certificate and the Intermediate certificate, copy them in citrix cacerts dir and it finally works
How did you do this?
-
Re: Citrix and SSL Error 61
This Error 61 has been a recurring problem for me. On Windows it seems to come and go in association with Firefox updates.
I haven’t been able to resolve the issue in Ubuntu. I tried the ln -s command above but the problem persists. I checked the contents of
/opt/Citrix/ICAClient/keystore/cacerts
and all the links are there that appear in the Mozilla certificate directory.The specific error I get now includes that I have chosen not to trust «Entrust Certification Authority — L1C», but there are three Entrust certificates in the cacerts directory:
Entrust.net_Premium_2048_Secure_Server_CA.crt
Entrust.net_Secure_Server_CA.crt
Entrust_Root_Certification_Authority.crtAny help would be appreciated. Thanks.
Last edited by pdowty; December 18th, 2012 at 10:07 PM.
-
Re: Citrix and SSL Error 61
Resolved my Error 61 after finding a post that suggested finding a working Windows Citrix Receiver and exporting the problem certificate from the Windows browser and placing in the Ubuntu directory. It worked. Whew! What a pain.
Bookmarks
Bookmarks

Posting Permissions
In your browser goto the site where you launch your citrix session from and click on the padlock widget on far left part of the url
-> click on «Connection is secure»
______ on chrome browser ______
-> click on «Certificate is valid»
this will open a popup window
-> on chrome click on tab «Details»
-> look at the field «Certificate Hierarchy»
-> click on the bottom most line which is the name of your cert
-> hit Export (which will download the cert file)
______ on firefox ______
-> click on «More information»
this will open a popup window get into its «Security» tab
-> click on «View Certificate»
-> this will open a page click on the «DigiCert High Assurance EV Root CA» tab
-> look at «Miscellaneous» -> Download
-> click on «PEM (cert)» and it will download the cert file
we are done with the browser
rename the cert file you just downloaded so it ends with .pem … my freshly downloaded file lives at ~/Downloads/foo.bar.pem
in a terminal issue following commands
cd /opt/Citrix/ICAClient/keystore/
sudo mv cacerts cacerts~~ignore
sudo ln -s /etc/ssl/certs cacerts
sudo cp ~/Downloads/foo.bar.pem /opt/Citrix/ICAClient/keystore/cacerts
if your box does not have dir /opt/Citrix/ICAClient/keystore/cacerts then you can identify your correct path by issuing
dpkg -L icaclient | grep cacerts
finally issue
# this engages above new .pem file
/opt/Citrix/ICAClient/util/ctx_rehash
PS … if Citrix is reading this please slurp this up and post on your Citrix workspace install site to help folks like me who had to struggle for hours first time as nowhere is this documented
The following Error occures when trying to use Citrix (access SAP Training via Citrix) on Ubuntu 15.10:
Citrix Receiver
SSL error
Contact your helpdesk with th following inofrmation:
You have not chosen to trust «Symantec Class 3 Secure Server CA / G4», the issuer of ther server’s security certificate (SSL error 61).
I installed Citrix according the Tutorial How to install Citrix Receiver icaclient in Ubuntu 14.04 LTS 64-bit The installation completed without any errors.
I also made sure that the certificates are there according to the CitrixXenAppPlugin — configure certificates:
Additionally I checked in Firefox if the certificates are known and even checked all marks (which where not checked before) (Under Settings -> Advanced -> Certificates):
What am I missing?
asked Mar 15, 2016 at 15:17
Thorsten NiehuesThorsten Niehues
1,1775 gold badges15 silver badges31 bronze badges
1
Solution 1
OK thx to the hints from @sletarte here the solution:
- Place certificate to be trusted in
/usr/local/share/ca-certificates - Execute
sudo update-ca-certificates
You should see something line this:
1 added, 0 removed; done. Running hooks in /etc/ca-certificates/update.d.... Adding debian:SymantecClass3SecureServerCA-G4.pem - Use Google Chrome instead of Firefox
Solution 2
Follow the steps from Citrix Workspace App for Linux: How to trust a CA certificate?
answered Mar 21, 2016 at 8:55
Thorsten NiehuesThorsten Niehues
1,1775 gold badges15 silver badges31 bronze badges
I’m using Ubuntu 16.04.1, Firefox 50 and Citrix Receiver 13.4.
@thorsten-niehues solution didn’t work for me unfortunately.
To solve the problem, I had to copy the .crt file to /opt/Citrix/ICAClient/keystore/cacerts
I was then able to connect to Citrix with Firefox and with Chrome without any problem.
d a i s y
5,3919 gold badges40 silver badges59 bronze badges
answered Jan 27, 2017 at 10:40
Not sure what scripts are run in your Citrix install, but I believe you may still need to tell Ubuntu to trust the root CA — you can do that by running sudo dpkg-reconfigure ca-certificates from the directory where you have the .crt files for Citrix. mozilla has its own directory (/usr/share/ca-certificates/mozilla) and that may be where it is looking to show the list of trusted certs that you see in Firefox.
answered Mar 15, 2016 at 15:34
2
After months of trouble-free operation, Citrix Receiver decided to wreak some havoc one morning last week.
Connecting to work (using Firefox on Ubuntu and Citrix Receiver for Linux 13.8) was trouble free as usual.
However, when I then tried to select a PC to remote into, Citrix informed me that …
“You have chosen not to trust Entrust Root Certification Authority – G2. SSL error 61”
At that point, I reflected that what I knew about Citrix and SSL certificates would fit on the back of a fag packet.
After some intensive “research” it should now fit into a short blog post…
Citrix Receiver for Linux has a bug…again
A quick internet search lead me to the Citrix Support site.
Their advice ( perhaps understandably), was to upgrade Citrix Receiver to the latest version.
After some fiddling around – steps for installing on Ubuntu can be found here if you’re interested, I had the latest version.
Now, I’m not sure whether it’s just an unfortunate coincidence or whether I’ve upset the good people at Citrix, but it seems that whenever I install the latest version, there is a Linux specific bug.
So, after about half an hour of messing about, I was back where I started with the same error and the same version of Citrix Receiver.
Attempting to connect via Chrome gave exactly the same result.
Re-installing my certificates
Re-reading the error message, I noticed that it was a specific certificate that was the problem.
Running a search, I was able to confirm that the said certificate is available from Entrust.
Once I’d downloaded the certificate in question, it was simply a matter of putting it where Citrix Receiver could see it.
So…
sudo cp entrust_g2_ca.cer /opt/Citrix/ICAClient/keystore/cacerts/.
Magically, Citrix Receiver was happy again and I was able to connect.
Some points to note for next time
A colleague of mine had the same issue. He is running Debian.
His solution was to :
– delete the files in the Citrix Receiver certs directory :
/opt/Citrix/ICAClient/keystore/cacerts/
– create a symlink in the directory from the certificates in
/etc/ssl/certs
If you’re reading this because you have a similar problem and the first solution doesn’t work, then perhaps this may be worth a try ( backup the certificate files before deleting them though !)
I’m still not sure of the root cause of this issue, although I suspect it may be something to do with browser updates.
On the plus side I’ve avoided having to drag myself into the office…for now.
Back in 1993, I discovered that I could get paid money for doing fun stuff with computers.
Over the years, I’ve specialised in Oracle Databses as a developer, a DBA and sometimes, an architect.
It’s my evil alter-ego — The Antikyte — who writes a blog about my various technical adventures.
Yes, that is his Death Star parked in the Disabled Bay.
I currently live in the South-West of England with Deb, my long-suffering wife.
View all posts by mikesmithers
В некоторых из этих случаев ваш компьютер может отображать очень хорошую ошибку, указывающую на ошибку пользователя SSL Ubuntu Citrix 61. Эта ошибка может иметь множество причин.
Ускорьте свой ПК всего за несколько кликов
Загрузите это программное обеспечение сейчас и попрощайтесь с проблемами вашего компьютера. г.
<раздел>
CTX203362
Текст всплывающей подсказки
<раздел>
статья | Инструкции / общий вопрос Нарушение безопасности | likeCount считает это руководство полезным | Созданный: ItemFormattedCreatedDate|Измененный: ItemFormattedModifiedDate
Текст всплывающей подсказки
статья | Инструкции и общий вопрос Нарушение безопасности | likeCount считает это полезным | Созданный: ItemFormattedCreatedDate|Измененный: ItemFormattedModifiedDate
<раздел>
Симптомы или ошибки
Эта статья предназначена только для администраторов Citrix и технических клубов. Неадминистраторам следует позвонить в службу поддержки / ИТ-отдел, а также отправить дополнительную информацию по адресу CTX297149.
Receiver for Linux выдает следующие ошибки при запуске обнаруженных персональных компьютеров / приложений:
Вы никогда не были уверены, что доверяете «центру сертификации», какому-то из наших издателей сертификатов безопасности сервера (ошибка SSL 61).
<раздел>
Решение
Важно! Этой статьей фактически пользовались системные администраторы. Если с этой проблемой сталкивается человек, который обычно не является системным администратором, обратитесь в службу поддержки вашей компании и попросите найти путь к этому документу.
Обновить до последнего получателя
Версия
Как исправить ошибку SSL 61 в широкополосном приемнике Citrix в Linux?
Поместите доверенный документ в / usr / local вместо share / ca-Certificates.Запустите sudo update-ca-Certificates. Вы должны увидеть следующую строку: одна добавлена, 0 удалено; делал. Запустите эти острые когти в /etc/ca-certificates/update.d. Добавить Добавлен Debian: SymantecClass3SecureServerCA-G4.pem.Используйте Google Chrome вместо Firefox.
Скачать базовый / промежуточный SSL-сертификат (.Crt /.Установите сертификат Cheer / Intermediate на свой компьютер.Если на всех компьютерах потенциальных клиентов установлено антивирусное программное обеспечение, убедитесь, что соответствующий антивирусный инструмент доверяет сертификату.
Если это не решит проблему, перейдите к следующему разделу.
Дополнительные отчеты об обновлениях функций Receiver см. в разделе Market to – Citrix Receiver Matrix Feature.
Отсутствует корневой / промежуточный сертификат
Это сообщение об ошибке означает, что у клиента устройства на самом деле нет корневой / промежуточной карты, необходимой для установления доверия с тем лицензирующим органом, который выпустил собранный сертификат.
Использовать корневой сертификат
Если вам нужно проверить квалификацию сервера, который еще был выдан комодом для хранения записей и еще не был упомянут на пользовательском устройстве, следуйте лучшим специальным инструкции перед добавлением StoreFront.
- Получить рут из-за сертификата в формате PEM.
Совет: Если вы не можете найти этот сертификат в этом формате, используйте эту утилиту openssl, чтобы преобразовать любой сертификат в формате CRT в тот, который вам лучше просто файл .pem. - Как пользователь, который обычно устанавливает пакет (обычно root):
- Скопируйте файл без запроса в $ ICAROOT, а не в хранилище ключей / cacerts.
- Выполните следующую команду:
$ ICAROOT / util / ctx_rehash
Используйте продвинутый сертификат
Если ваш сервер StoreFront не может предоставить промежуточные сертификаты, соответствующие обычно используемому сертификату, если вам необходимо предоставить расширенные сертификаты для начинающих для поддержки пользователей предоплаченных чиповых карт, выполните следующие действия, чтобы начать установку StoreFront Add store.
- Получите промежуточные сертификаты отдельно в формате PEM.
Совет: если вам не удалось найти запись в таком расположении, используйте специальную утилиту openssl для получения сертификата на жестком диске компьютера CRT здесь, в файле. pem файл для. - как пользователь, который также установил пакет (обычно root):
- Копировать регистры – $ ICAROOT или хранилище ключей / intcerts.
- Запустите здесь команду от имени пользователя, настроившего пакет:
$ ICAROOT / util / ctx_rehash
<раздел>
Дополнительные ресурсы
Как мне доверять сертификату безопасности сервера?
Если аккредитация кажется недоступной популярным правом – например, вы получаете срочные предупреждения или ошибки при попытке входа в определенные инструменты – откройте Связку ключей. Щелкните правой кнопкой мыши конкретную квалификацию и нажмите «Получить информацию». Часто открывайте меню «Доверие» и отметьте «Всегда доверяйте при использовании этого сертификата».
Эта статья предназначена только для руководителей Citrix и специалистов по гольфу. Не администраторы, вероятно, обратятся в службу поддержки / ИТ-поддержку своей компании и свяжутся с CTX297149 только для получения дополнительной информации.

Receiver для Linux отображает правильную ошибку при загрузке настольных / печатных курсов:
Вы больше не доверяете CA как эмитенту сертификата безопасности сервера аэропорта (SSL ошибка 61).
Важно! Эта статья могла быть создана для системных администраторов. Если кто-то столкнется с этим Если вы определенно будете проблемой, а не подходящим системным администратором, обратитесь в службу поддержки вашей организации за помощью и обратитесь к типу информации.
К
Обновите приемник до последней версии
- Обновите Receiver до этой новой версии, чтобы убедиться, что все это решает проблему.
- Если кто-то использует сертификаты SHA2, весь старый основной получатель просто не поддерживает эти сертификаты. См. Раздел Приемник CTX200114 – поддержка Citrix для SHA-2, где представлена информация о версиях приемника, которые предоставляют сертификаты SHA-2.
В противном случае перейти к следующему разделу.
Информацию об обновлениях функций приемника см. в таблице функций приемника Citrix.
Отсутствует корневой / промежуточный сертификат
отказ
В этом сообщении говорится, какие эксперты утверждают, что клиентский планшет определенно не имеет необходимого корневого / промежуточного сертификата, которому доверяли бы ответственные лица при рассмотрении сертификата, выдавшего сертификат веб-сервера.
Используйте корневые сертификаты
Если вам действительно нужно проверить подлинность сертификата официанта, который был выдан только с помощью какого-либо средства отслеживания сертификатов и который затем снова не является доверенным на пользовательском устройстве, выполните эти инструкции перед добавлением StoreFront.
- Получите учетные данные root в формате PEM.
Совет: Если вы не можете найти конкретный инструмент в этом формате, используйте большинство из утилит openssl для преобразования отличного официального документа .crt в красивый файл .pem для преобразования. - Как пользователь, загрузивший комплект (обычно root):
- Скопируйте начало в usd ICAROOT / keystore / cacerts.
- Выполнить текущее действие:
$ ICAROOT / util и ctx_rehash
Использовать продвинутый сертификат новичка
Ускорьте свой ПК всего за несколько кликов
Ваш компьютер работает медленно и нестабильно? Вас мучают таинственные ошибки, и вы беспокоитесь о потере данных или сбое оборудования? Тогда вам нужен ASR Pro — идеальное программное обеспечение для устранения неполадок Windows. С ASR Pro вы можете исправить широкий спектр проблем всего за несколько кликов, включая ужасный синий экран смерти. Приложение также обнаруживает аварийные приложения и файлы, поэтому вы можете быстро решить их проблемы. И самое главное, это совершенно бесплатно! Так что не ждите — загрузите ASR Pro прямо сейчас и наслаждайтесь бесперебойной, стабильной и безошибочной работой на ПК.
Если наш собственный сервер StoreFront небезопасен для предоставления промежуточных сертификатов, которые содержат установленный сертификат, или если вам необходимо установить новые сертификаты непосредственно для поддержки пользователей смарт-карт в Интернете, придерживайтесь следующих шагов. прежде чем доверять практически любому проверенному StoreFront – добавьте резерв.
- Получите эти продвинутые сертификаты для начинающих отдельно в формате PEM.
Совет: Если вы не можете найти свой сертификат в этом формате, воспользуйтесь Openssl Electrical Power. Преобразуйте прибор из формата CRT в этот файл .pem. - от имени пользователя, установившего пакет (обычно root):
- Скопируйте файлы в $ ICAROOT, а не в хранилище ключей / intcerts.
- Выполните следующее администрирование, хотя пользователь, установивший это устройство:
Как исправить ошибку SSL 4 в Citrix?
На потенциальном клиентском устройстве откройте Панель управления.Удалите, как правило, текущую версию Citrix Receiver:Загрузите каждую старую версию Citrix Receiver.Закройте все веб-браузеры.Выполните новую стандартную установку Citrix Receiver (например, 4.6)Запустите Citrix Storefront и проверьте его.
$ ICAROOT / util / ctx_rehash
Загрузите это программное обеспечение сейчас и попрощайтесь с проблемами вашего компьютера. г.
Ubuntu Citrix Client Ssl Error 61
Erreur Ssl Client Ubuntu Citrix 61
г.
After months of trouble-free operation, Citrix Receiver decided to wreak some havoc one morning last week.
Connecting to work (using Firefox on Ubuntu and Citrix Receiver for Linux 13.8) was trouble free as usual.
However, when I then tried to select a PC to remote into, Citrix informed me that …
“You have chosen not to trust Entrust Root Certification Authority – G2. SSL error 61”
At that point, I reflected that what I knew about Citrix and SSL certificates would fit on the back of a fag packet.
After some intensive “research” it should now fit into a short blog post…
Citrix Receiver for Linux has a bug…again
A quick internet search lead me to the Citrix Support site.
Their advice ( perhaps understandably), was to upgrade Citrix Receiver to the latest version.
After some fiddling around – steps for installing on Ubuntu can be found here if you’re interested, I had the latest version.
Now, I’m not sure whether it’s just an unfortunate coincidence or whether I’ve upset the good people at Citrix, but it seems that whenever I install the latest version, there is a Linux specific bug.
So, after about half an hour of messing about, I was back where I started with the same error and the same version of Citrix Receiver.
Attempting to connect via Chrome gave exactly the same result.
Re-installing my certificates
Re-reading the error message, I noticed that it was a specific certificate that was the problem.
Running a search, I was able to confirm that the said certificate is available from Entrust.
Once I’d downloaded the certificate in question, it was simply a matter of putting it where Citrix Receiver could see it.
So…
sudo cp entrust_g2_ca.cer /opt/Citrix/ICAClient/keystore/cacerts/.
Magically, Citrix Receiver was happy again and I was able to connect.
Some points to note for next time
A colleague of mine had the same issue. He is running Debian.
His solution was to :
– delete the files in the Citrix Receiver certs directory :
/opt/Citrix/ICAClient/keystore/cacerts/
– create a symlink in the directory from the certificates in
/etc/ssl/certs
If you’re reading this because you have a similar problem and the first solution doesn’t work, then perhaps this may be worth a try ( backup the certificate files before deleting them though !)
I’m still not sure of the root cause of this issue, although I suspect it may be something to do with browser updates.
On the plus side I’ve avoided having to drag myself into the office…for now.
Содержание
- There are a lot of SSL errors out there. Way too much, right?
- 1. SSL error
- «ssl_error_no_cypher_overlap»
- Quick fix
- Proper fix
- 2. SSL error
- «ssl_error_rx_record_too_long»
- Quick fix
- Proper fix
- 3. SSL error
- «ssl_error_syscall»
- Quick fix
- Proper fix
- 4. SSL error
- «ssl_error_bad_cert_domain»
- Quick fix
- Proper fix
- 5. SSL error
- «ssl_error_internal_error_alert»
- Quick fix
- Proper fix
- 6. SSL error
- “ssl error 31”
- Quick fix
- Proper fix
- 7. SSL error
- «ssl error 61”»
- Quick fix
- Proper fix
- Thread: Citrix and SSL Error 61
- Citrix and SSL Error 61
- Re: Citrix and SSL Error 61
- Ssl error 61 you have
- Выбранное решение
- Все ответы (6)
- Ssl error 61 you have
- Chosen solution
- All Replies (6)
- How to fix SSL error 61 in Citrix Web Receiver on Linux
- Related Posts
- 29 Comments
There are a lot of SSL errors out there.
Way too much, right?
You as a sysadmin know that for sure – Certificate Errors, Configuration Errors, Server Errors, Protocol Errors, and others.
Here you’ll find a list of the most common xxxxx errors and proven quick fix solutions:
And you’ll find the solution to get rid of ALL SSL errors – forever: Test PRTG as your new monitoring tool and get stared within minutes!
1. SSL error
«ssl_error_no_cypher_overlap»
Quick fix
Did you receive the error message “ssl error no cypher overlap” while using Firefox or another web browser? Then you are dealing with one of the most common SSL errors. The cypher overlap error occurs due to a misconfiguration of the TLS/SSL settings.
The SSL error can easily be solved by adjusting the settings in your browser. If you are using Mozilla Firefox, access the settings page and choose the add-on section. Check the add-on list for any extensions that you did not install yourself. Deactivate all unnecessary add-ons and plug-ins, then restart the browser.
You can also reset both the TLS and the SSL settings. In your brower, type about:config to open the settings. Type TLS in the search box and look through the TLS settings. If there are any modified settings, restore them back to default. Repeat these steps to reset the SSL settings as well.
Proper fix
Switch to PRTG: PRTG uses the SSL Security Check Sensor and lets you use SSL to encrypt your own monitoring data. PRTG helps you secure data traffic and notifies you at once if the security rating changes.
2. SSL error
«ssl_error_rx_record_too_long»
Quick fix
The common SSL error “ssl error rx record too long” may occur in your browser when visiting a website via HTTPS. The error is often accompanied by the error message “SSL received a record that exceeded the maximum permissible length” or a similar message. This means that the web server is sending HTTP data instead of HTTPS data.
This common SSL issue is usually caused by an error in the SSL implementation on the server itself. There are several things that you can do to solve the problem:
- Ensure that SSL is configured correctly on the server.
- Check if your browser is using the same port as the web server. To use port 443, some servers such as Apache require a configuration first.
- If you are using a proxy server, the error can show up as well. In this case, make sure that your local proxy is configured correctly.
Proper fix
Switch to PRTG: PRTG uses the SSL Security Check Sensor and lets you use SSL to encrypt your own monitoring data. PRTG helps you secure data traffic and notifies you at once if the security rating changes.
3. SSL error
«ssl_error_syscall»
Quick fix
Are you facing the error message “ssl error syscall”, there is a problem with your SSL configurations. This can be caused by a disabled proxy protocol which leads to a failed request of the SSL handshake.
To fix the problem, make sure that you enable the proxy protocol in the inbound traffic. Also check if TLS is properly configured in the web server, as a misconfiguration of the server may lead to this error as well.
Proper fix
Switch to PRTG: PRTG uses the SSL Security Check Sensor and lets you use SSL to encrypt your own monitoring data. PRTG helps you secure data traffic and notifies you at once if the security rating changes.
4. SSL error
«ssl_error_bad_cert_domain»
Quick fix
The error code “ssl error bad cert domain” and the error message “The certificate is only valid for the following names” is often experienced by users while trying to access their SSL encrypted website or network. The error code indicates that there is a configureation problem with the SSL certificate of the website. The SSL error is commonly reported by Firefox users, but may also occur in other browsers.
Depending on the individual cause of the error, try the following troubleshooting solutions:
- If caused by an SSL misconfiguration of the website itself, the configuration needs to be adjusted by the website’s admin. If it is your website, make sure that your SSL certificate is active and switch to HTTPS.
- In some cases, the browser’s cache and cookies may lead to an SSL error. If this is the case, you can simply solve the problem by clearing the cache in the settings.
Proper fix
Switch to PRTG: PRTG uses the SSL Security Check Sensor and lets you use SSL to encrypt your own monitoring data. PRTG helps you secure data traffic and notifies you at once if the security rating changes.
5. SSL error
«ssl_error_internal_error_alert»
Quick fix
SSL error code “internal error alert” is a common problem faced by users of Mozilla Firefox and other web browsers. The error message indicates that there is a problem with the secure SSL connection. It may be caused either by the SSL certificate or by the settings of your browser.
To fix the problem, try the following troubleshooting steps:
- Make sure you are using a valid SSL certificate.
- Update your browser to the latest version.
- Disable unknown or unnecessary add-ons in the Firefox settings.
- Ensure that HTTPS is set up correctly.
- If the error persists after these steps, restart your browser.
Proper fix
Switch to PRTG: PRTG uses the SSL Security Check Sensor and lets you use SSL to encrypt your own monitoring data. PRTG helps you secure data traffic and notifies you at once if the security rating changes.
6. SSL error
“ssl error 31”
Quick fix
Are you facing Citrix client SSL error code 31? Then you are dealing with one of many SSL errors with Citrix. Error 31 can be caused by a variety of misconfigurations or outdated version of the service provider.
To solve the problem, make sure the SSL certificate is valid. Also update your service provider to the newest version to avoid problems with the compatibility. Also check if any corporate settings or your firewall is blocking the connection.
Proper fix
Switch to PRTG: PRTG uses the SSL Security Check Sensor and lets you use SSL to encrypt your own monitoring data. PRTG helps you secure data traffic and notifies you at once if the security rating changes.
7. SSL error
«ssl error 61”»
Quick fix
SSL error 61 is an error code regularly experienced by Citrix users. There are several error messages that can be displayed for receiver users when accessing Citrix StoreFront or web interface applications, such as:
“Cannot connect to the Citrix XenApp Server. SSL Error 61: You have not chosen to trust ‘Certificate Authority’, the issuer to the server’s security certificate.”
“The server certificate received is not trusted (SSL Error 61)”
“You app is not available. Try again later.”
As a system administrator, you can try the following solutions to get rid of SSL error 61:
- Update to the latest receiver version, as older versions may not support SHA2 certificates.
- Ensure that you have the required root certificate or intermediate certificate. You can download the certificates from your SSL certificate provider. If you use an antivirus software, make sure that your antivirus software trusts the SSL certificate.
- Check if the server certificate is compliant with the instruction in RFC 3280 in terms of the Enhanced Key Usage field.
Proper fix
Switch to PRTG: PRTG uses the SSL Security Check Sensor and lets you use SSL to encrypt your own monitoring data. PRTG helps you secure data traffic and notifies you at once if the security rating changes.
Источник
Thread: Citrix and SSL Error 61
Thread Tools
Display
Citrix and SSL Error 61
I’m using Ubuntu 12.04 LTS (32bit) and the latest Linux version of Citrix Receiver. Whenever I try to connect to my work network through Citrix I get the error message below. As far as I can see it’s not true, I *am* trusting the issuer of the server’s security certificate. This error message, (with different issuers) is frequently mentioned on the net but I cannot get any of the many many solutions to work in my case. Any advice would be gratefully received.
SSL error : Contact your help desk with the following information: You have not chosen to trust «/C=US/ST=/L=/O=The Go Daddy Group, Inc./OU=Go Daddy Class 2 Certification Authority/CN=», the issuer of the server’s security certificate (SSL error 61).
Re: Citrix and SSL Error 61
I’m using Ubuntu 12.04 LTS (32bit) and the latest Linux version of Citrix Receiver. Whenever I try to connect to my work network through Citrix I get the error message below. As far as I can see it’s not true, I *am* trusting the issuer of the server’s security certificate. This error message, (with different issuers) is frequently mentioned on the net but I cannot get any of the many many solutions to work in my case. Any advice would be gratefully received.
SSL error : Contact your help desk with the following information: You have not chosen to trust «/C=US/ST=/L=/O=The Go Daddy Group, Inc./OU=Go Daddy Class 2 Certification Authority/CN=», the issuer of the server’s security certificate (SSL error 61).
This is actually straight from Ubuntu’s Citrix help page:
To prevent the following error when accessing remote sessions:
Citrix Receiver
SSL error
Contact your help desk with the following information:
You have not chosen to trust»/C=US/ST=/L=/O=Equifax/OU=Equifax Secure Certificate Authority/CN=», the issuer of the server’s security certificate ((SSL error 61).
Источник
Ssl error 61 you have
Every time I try to connect to my internal website from a Linux OS Thin Client I recieve the SSL error 61. Firefox is the only browser on the Thin Client. There are no issues connecting from Non-Linux systems on any browser including Firefox.
Error Below: SSL error Contact your help desk with the following information: You have not chosen to trust » Go Daddy Secure Certificate Authority — G2″, the issuer of the server’s security certificate (SSL error 61).
How do I fix this error? I have already tried installing the cert manually to the client.
Выбранное решение
Cor-el: This does solve the issue for SHA1 certs.
I have added the certificate to the Citrix DB. I finally found the issue after researching the forums of Citrix and other various sites.
This issue is the cert itself, we purchased a cert and uses SHA2, however the Linux Citrix Receiver does not support SHA2 at this point.
So the only resolution is to either Re-Key the cert to use SHA1 or wait for an update from Citrix.
Thank you both for your time.
Все ответы (6)
With Citrix? I do see threads on that on the web:
The discussion seems to be outside the scope of Firefox support, but it could be that I just don’t understand it very thoroughly.
It is connecting through a Citrix Receiver but that should be irreverent as the certs are installed through Firefox and are handled, and Firefox is the application displaying that the CA is not trusted.
I guess what I’m getting at is for some reason the CA is not trusted, how do I force Firefox to realize that the CA is trusted even though I have installed the Root cert already. I have contacted Citrix and they said this is not their issue, HP has no idea why. The last party I have not contacted is Firefox. Maybe I’m just grasping at straws here?
Источник
Ssl error 61 you have
Every time I try to connect to my internal website from a Linux OS Thin Client I recieve the SSL error 61. Firefox is the only browser on the Thin Client. There are no issues connecting from Non-Linux systems on any browser including Firefox.
Error Below: SSL error Contact your help desk with the following information: You have not chosen to trust » Go Daddy Secure Certificate Authority — G2″, the issuer of the server’s security certificate (SSL error 61).
How do I fix this error? I have already tried installing the cert manually to the client.
Chosen solution
Cor-el: This does solve the issue for SHA1 certs.
I have added the certificate to the Citrix DB. I finally found the issue after researching the forums of Citrix and other various sites.
This issue is the cert itself, we purchased a cert and uses SHA2, however the Linux Citrix Receiver does not support SHA2 at this point.
So the only resolution is to either Re-Key the cert to use SHA1 or wait for an update from Citrix.
Thank you both for your time.
With Citrix? I do see threads on that on the web:
The discussion seems to be outside the scope of Firefox support, but it could be that I just don’t understand it very thoroughly.
It is connecting through a Citrix Receiver but that should be irreverent as the certs are installed through Firefox and are handled, and Firefox is the application displaying that the CA is not trusted.
I guess what I’m getting at is for some reason the CA is not trusted, how do I force Firefox to realize that the CA is trusted even though I have installed the Root cert already. I have contacted Citrix and they said this is not their issue, HP has no idea why. The last party I have not contacted is Firefox. Maybe I’m just grasping at straws here?
Источник
How to fix SSL error 61 in Citrix Web Receiver on Linux

In particular, the problem is about the SSL error 61 in the Citrix (Web) receiver under Linux and how to fix it. Since I have been running almost exclusively under Kubuntu for several months, the Citrix Reiceiver also moved into the new Linux box. Unfortunately, no connection to systems could be established, since the receiver disconnected with the following error message.
SSL Error 61: You have not chosen to trust “Go Daddy Root Certificate Authority – G2”, the issuer to the server’s security certificate.

Now there are two solutions. Either you get the missing certificates and insert them into the following directory:
Or you have Firefox installed… How does Firefox help us? Because the root certificates of Firefox can be shared with the Citrix receiver with only one command via symbolic links. The whole works as follows:
In this case, a symbolic link for each root certificate that the Firefox knows is created in the Citrix directory, so that it can participate. Now your SSL error 61 should be gone.
If, for whatever reason, you want to undo the changes, you can run the following two commands:
running ubuntu 22.10, this one worked for me
sudo ln -s /etc/ssl/certs/* /opt/Citrix/ICAClient/keystore/cacerts
thanks for pointing me in the right direction!
After trying numerous things, this was the solution that works.
Thanks so much LUKA
This even worked for my 22.04 release of Ubuntu. Thank you very much Luka
This even worked for my 22.04 release of Ubuntu.
Thank you very much Luka.
If anyone having the same issue still after this fix. Might want to check your keystore/cacerts isn’t stored elsewhere depending on where you installed the citrix client.
i.e. /home/user/ICAClient/* rather than /opt/citrix
need to link to the keystore that’s in use.
Hi,
Thank you for posting this, Saved my day.
I am still getting SSL error 61 message on my Ubuntu 20.04 desktop. WHen I type I get these error messages (see below). ANy ideas?
sudo ln -s /usr/share/ca-certificates/mozilla/* /opt/Citrix/ICAClient/keystore/cacerts/
I get the following messages in Terminal:
ln: failed to create symbolic link ‘/opt/Citrix/ICAClient/keystore/cacerts/T-TeleSec_GlobalRoot_Class_2.crt’: File exists
Источник
by Theresa Miller
So, it was finally time to rollout SHA2 certificates for your Citrix environment. After doing so, you test your applications by launching your favorite Citrix XenApp Application. To your surprise, the application will not open and returns an SSL Error 61. Now what, what can be done to fix this issue?
Check your Trust Root or Intermediate Certificate
One of the likely causes is that the PC you are working on is missing it’s Trusted Root or Intermediate Certificate. Your certificate provider can let you know which certificate type they use. How do we make sure these are in place? This can be done manually per PC as shown in the example below, or automated per the following Microsoft article (https://technet.microsoft.com/en-us/library/cc754841.aspx). Here are the steps to update an individual PC using a Digicert root certificate. Note that these steps would be similar for most certificate providers.
————————————————————————————————
Advertisement:
Monitor/Access your virtual servers, workstations & data using Citrix XenDesktop with 24×7 support and a 99.9% uptime guarantee through CloudDesktopOnline. To know more about QuickBooks Hosting on Citrix XenDesktop, visit Apps4Rent.
————————————————————————————————
1) Open Internet Explorer go to https://www.digicert.com/digicert-root-certificates.htm
2) Download the Intermediate Certificate called “DigiCert SHA2 High Assurance Server CA” or the appropriate certificate for your environment and save your PC or a network location
3) Go to Start, Search from your Windows 7 workstation
4) Type MMC and press enter
5) From the menu select, Add/Remove SnapIn
6) Select Certificates and click “Add”, then click OK
7) Choose Computer Account and click Next
Choose Local Computer and click finish and click OK
9) Expand Intermediate Certificates and click on Certificates.
10) Right-click on Certificates, then selectAll Tasks, and click Import
11) Click Next on the Certificate Import Wizard
12) Click Browse and go to the location of the downloaded certificate and then click Next
[wp_ad_camp_1]
13) Click Next
14) Click Finish
15) Test the application to verify the SSL Error 61 error has gone away
If the error didn’t go away or if the certificates were already set the way that should have been, then the next stop is to look at your version of Citrix Receiver.
Citrix Receiver
Updating to the latest Citrix Receiver version will typically resolve the issue once the certificates are in place. Here is the link to Citrix Receiver for Windows http://www.citrix.com/go/receiver.html?posit=glnav, and here is the latest version for a MAC http://www.citrix.com/downloads/citrix-receiver/mac.html
Say Goodbye to SSL Error 61!
Was trying to connect to a Citrix Workspace and kept getting the following error “You have not chosen to trust “Entrust Root Certification Authority – XX”, the issuer of the security certificate (SSL error 61)“. I have hit this error in the past and had fixed it but couldn’t find my notes from how I had fixed it back then, so I had to resort to searching on the web based on vague memories of how I had fixed. After a bit of effort I found two solutions that people had suggested:
Solution 1:
Create a symbolic link pointing the /opt/Citrix/ICAClient/keystore/cacerts directory to /usr/share/ca-certificates/mozilla/ , using the command below as root:
mv /opt/Citrix/ICAClient/keystore/cacerts /opt/Citrix/ICAClient/keystore/cacerts.bak ln -s /usr/share/ca-certificates/mozilla/ /opt/Citrix/ICAClient/keystore/cacerts
Unfortunately, this didn’t resolve the problem for me.
Solution 2:
The second solution people recommended was to link /opt/Citrix/ICAClient/keystore/cacerts directory to the /etc/ssl/certs/ directory, using the command below as root:
mv /opt/Citrix/ICAClient/keystore/cacerts /opt/Citrix/ICAClient/keystore/cacerts.bak ln -s /etc/ssl/certs/ /opt/Citrix/ICAClient/keystore/cacerts
After I linked the directory to /etc/ssl/certs things immediately started working without errors. This time I am blogging about it so that the next time I don’t waste time trying to find the solution.
– Suramya