Hello everyone is glad that I was able to get here. We are playing a little with syspass, but we have a problem
Connection error (BIND).
LDAP ERROR: Can not contact LDAP server (-1)
LDAP DN: syspass
I do not how I can not figure out what’s wrong, but I’ve been through a lot of options:
- I was trying to specify FQDN and ip server name
- The user is specified without prefixes simply Administrator (Domain Administrator in Active Directory)
- I checked telnet access to ldap server
- I tried to specify the server with all the possible prefixes ldap. *, Ldap:
But I’m getting this error. I want to know in addition to installing php56w-ldap, I had to do some other setup?
Here is a screenshot of my setting
Comments
I have a strange issue. Best part of users can login, but few can’t. That’s return wrong password and get this error:
Erreur de connexion (BIND)
LDAP ERROR: Can’t contact LDAP server (-1)
LDAP DN: CN=LDAPUSER,CN=Users,DC=MYBUSINESS,DC=local
They are all in the same LDAP folder, I didn’t specifie Group in sysPass setting.
Could be special char in password?
Hi, can you tell me if the LDAP connection changes on every login?. This is a feature that runs when a DNS hostname is given for the LDAP server. You can see it the sysPass event log.
In addition, it’s happen only in the first loggin. Once got User Disabled, that do not happen again.
Not sure what you asking for. But I juste log once with one browser and logged again in Private mode. I got this in log (Commit version: 6f44f8c):
First:
1262 2015-12-09 09:34:11 Se connecter SXXXXXXXXX ... (LDAP)
Connexion au serveur : srvdc.mybusiness.local
Utilisateur : sxxxxxxxxx
Profil : Admin
Groupe : Admins
Second:
1265 2015-12-09 09:42:18 Se connecter SXXXXXXXXX ... (MySQL)
Utilisateur : sxxxxxxxxx
Profil : Admin
Groupe : Admins
1264 2015-12-09 09:42:18 ldapBind ... Erreur de connexion (BIND)
LDAP ERROR: Can’t contact LDAP server (-1)
LDAP DN: CN=LDAP,CN=Users,DC=mybusiness,DC=local
I enabled Debug, I took a look in error.log. what display is wrong:
ldap_url_parse_ext(ldap://localhost/)
ldap_init: trying /etc/ldap/ldap.conf
ldap_init: using /etc/ldap/ldap.conf
ldap_init: HOME env is NULL
ldap_init: trying ldaprc
ldap_init: LDAPCONF env is NULL
ldap_init: LDAPRC env is NULL
ldap_create
ldap_url_parse_ext(ldap://dcfiles.mybusiness.local:389)
ldap_sasl_bind_s
ldap_sasl_bind
ldap_send_initial_request
ldap_new_connection 1 1 0
ldap_int_open_connection
ldap_connect_to_host: TCP dcfiles.mybusiness.local:389
ldap_connect_to_host: getaddrinfo failed: Nom ou service inconnu
ldap_err2string
ldap_err2string
No Ideal where that «dcfiles» is from. this is not what is set in the config file.
Seconde attemp, got:
ldap_url_parse_ext(ldap://localhost/)
ldap_init: trying /etc/ldap/ldap.conf
ldap_init: using /etc/ldap/ldap.conf
ldap_init: HOME env is NULL
ldap_init: trying ldaprc
ldap_init: LDAPCONF env is NULL
ldap_init: LDAPRC env is NULL
ldap_create
ldap_url_parse_ext(ldap://sbs2k3.mybusiness.local:389)
ldap_sasl_bind_s
ldap_sasl_bind
ldap_send_initial_request
ldap_new_connection 1 1 0
ldap_int_open_connection
ldap_connect_to_host: TCP sbs2k3.mybusiness.local:389
ldap_new_socket: 17
ldap_prepare_socket: 17
ldap_connect_to_host: Trying 192.168.0.2:389
ldap_pvt_connect: fd: 17 tm: 10 async: 0
ldap_ndelay_on: 17
attempting to connect:
connect errno: 115
ldap_int_poll: fd: 17 tm: 10
ldap_is_sock_ready: 17
ldap_is_socket_ready: error on socket 17: errno: 113 (No route to host)
ldap_pvt_connect: -1
ldap_close_socket: 17
ldap_err2string
ldap_err2string
This «sbs2k3» is from a old server removed. Maybe the issue is on my ldap server side? But the ldap still not use the right configuration from the config file.
That is the behavior that I told you, if you provide an LDAP hostname (myserver.mydomain.com) it will search for other AD servers on your domain to make auth requests.
If you only set an ip address (your AD ip address), it will not search for other servers….
OK, didn’t know that. I set a IP, Tested OK
Thanks!
Check your AD, it could you get some annoying issues with «ghost» servers…
2 participants
LDAP (Lightweight Directory Access Protocol) is a protocol used for accessing and maintaining distributed directory information services over an IP network. The ldap_bind invalid credentials (49) error is a common error that occurs when trying to authenticate with an LDAP server. This error occurs due to incorrect username and password, or due to a misconfiguration in the LDAP server.
If you encounter this error, don’t worry. In this guide, we will show you how to fix ldap_bind invalid credentials (49) error step-by-step.
Step 1: Check the LDAP Server Status
The first step to fixing ldap_bind invalid credentials (49) error is to check if the LDAP server is running and reachable. To do this, you can use the ping command to ping the server IP address.
ping ldap.server.ip.address
If the LDAP server is running and reachable, you should receive a response. If not, you need to check the network connection and make sure that the LDAP server is up and running.
Step 2: Verify the Username and Password
The second step is to verify the username and password that you are using to authenticate with the LDAP server. Make sure that the credentials are correct and match the ones stored in the LDAP server.
Step 3: Check the LDAP Configuration
If the username and password are correct, the next step is to check the LDAP configuration. Ensure that the LDAP server is configured correctly, and the LDAP client is using the correct configuration file.
Step 4: Check the LDAP Client Configuration
If the LDAP configuration is correct, the next step is to check the LDAP client configuration. Ensure that the LDAP client is using the correct server address, port number, and protocol.
Step 5: Enable LDAP Debugging
If you are still having issues with ldap_bind invalid credentials (49) error, you can enable LDAP debugging to get more information about the error. To do this, add the following lines to the LDAP client configuration file:
loglevel 256
debug yes
This will enable debugging and provide more information about the error.
Frequently Asked Questions (FAQ)
Q1. What is ldap_bind invalid credentials (49) error?
ldap_bind invalid credentials (49) error is an error that occurs when trying to authenticate with an LDAP server. This error occurs due to incorrect username and password, or due to a misconfiguration in the LDAP server.
Q2. How can I fix ldap_bind invalid credentials (49) error?
To fix ldap_bind invalid credentials (49) error, you need to check the LDAP server status, verify the username and password, check the LDAP configuration, check the LDAP client configuration, and enable LDAP debugging.
Q3. How do I ping an LDAP server?
To ping an LDAP server, use the ping command followed by the server IP address:
ping ldap.server.ip.address
Q4. How do I verify the LDAP configuration?
To verify the LDAP configuration, ensure that the LDAP server is configured correctly, and the LDAP client is using the correct configuration file.
Q5. How do I enable LDAP debugging?
To enable LDAP debugging, add the following lines to the LDAP client configuration file:
loglevel 256
debug yes
- LDAP Tutorial
- LDAP Authentication
- LDAP Server Configuration
We hope that this guide has helped you to fix ldap_bind invalid credentials (49) error. If you have any further questions or need assistance, please feel free to contact us.
Follow through this tutorial to learn how to integrate sysPass with OpenLDAP for authentication and account management.
Integrate sysPass with OpenLDAP for Authentication
- Install and Setup OpenLDAP server
In our previous tutorials, we covered how to install and setup OpenLDAP server. Follow the link below to check them.
Install and Setup OpenLDAP server
- Install and Setup sysPass
Follow the link below to install and setup sysPass.
Install and setup sysPass on Linux
- Integrate sysPass with OpenLDAP for Authentication
To begin, ensure sysPass is installed with PHP-LDAP modules.
php -m | grep ldap- Create OpenLDAP User Group for sysPass
Create an group of OpenLDAP that can be used to control access to sysPass. All members of the group to be created will allowed to access/login to sysPass.
Follow our guide below to learn how to setup OpenLDAP groups.
How to Create OpenLDAP Member Groups
In our OpenLDAP server, we have created a group called syspass.
Some members have been added to this group as evident in the command output below;
ldapsearch -H ldapi:/// -Y EXTERNAL -LLL -Q -b "dc=ldapmaster,dc=kifarunix-demo,dc=com" cn=syspassSample output;
dn: cn=syspass,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: groupOfNames
cn: syspass
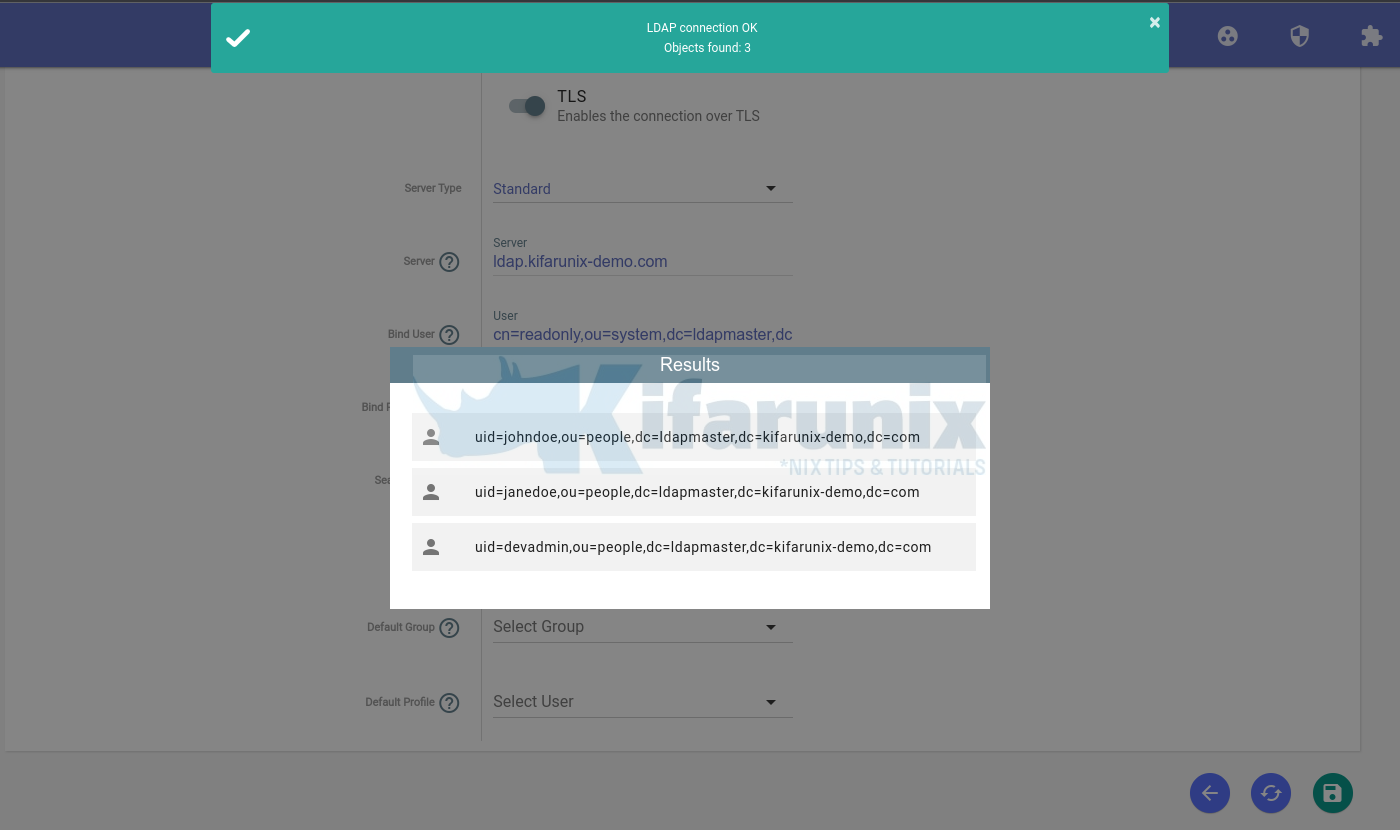
member: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=devadmin,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
Integrate sysPass with OpenLDAP for Authentication
Once you have setup your OpenLDAP user/groups for sysPass authentication, login to sysPass web user interface as administrator.
- Create OpenLDAP users group.
This will be required to specify the default group under which OpenLDAP users belong to on sysPass.
To create group, click Users and accesses icon > GROUPS > New Group.
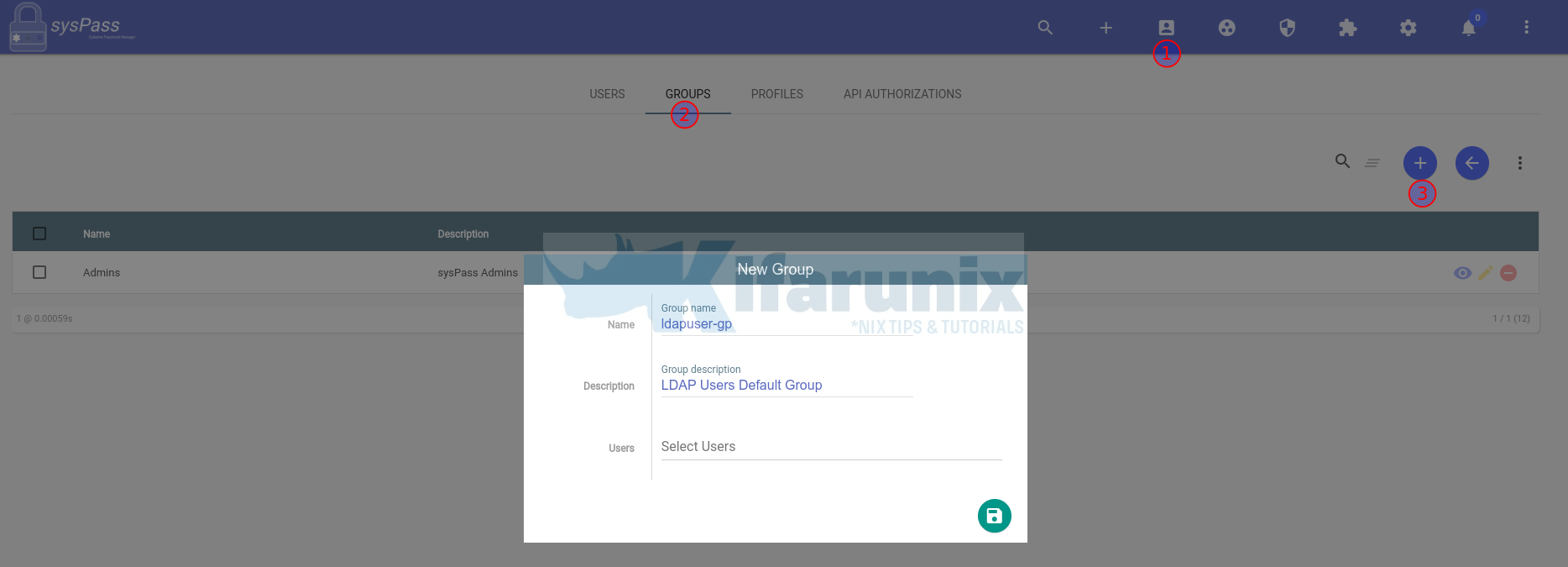
Save the group.
- Next, create OpenLDAP Users default Profile
This is where you define the default permissions to be assigned to a specific user profile. To create a profile, click Users and accesses icon > PROFILE > New Profile.
Sample account permissioms.
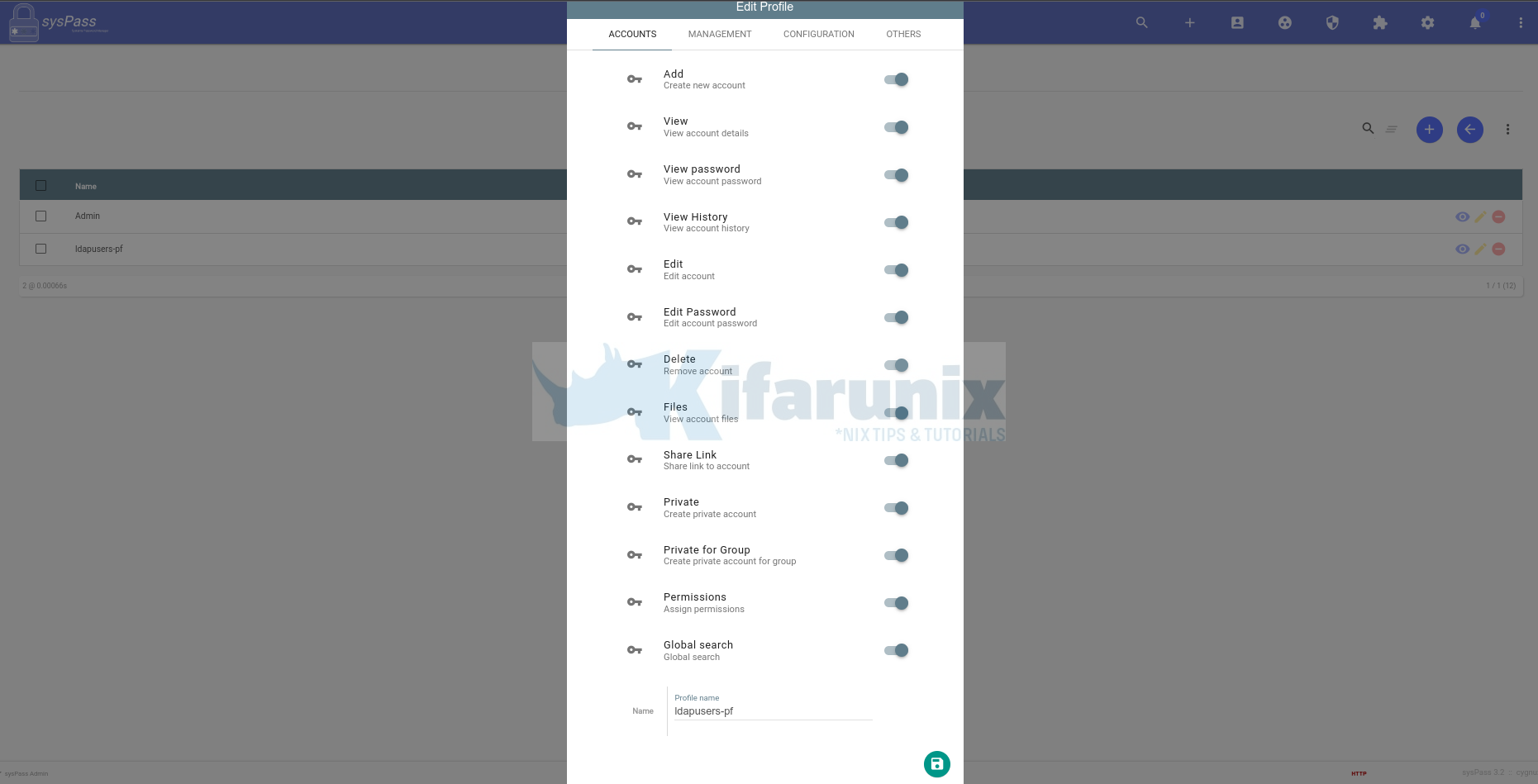
For the rest of the accesses, we didn’t give any for this particular profile. Feel Free to set the accesses accordingly.
So we now have a group, ldapuser-gp, and profile, ldapusers-pf.
Note that you should be able to define the specific profile/groups once the LDAP users are in the sysPass system.
- Next, click the gear icon to access the configuration menu and click LDAP.
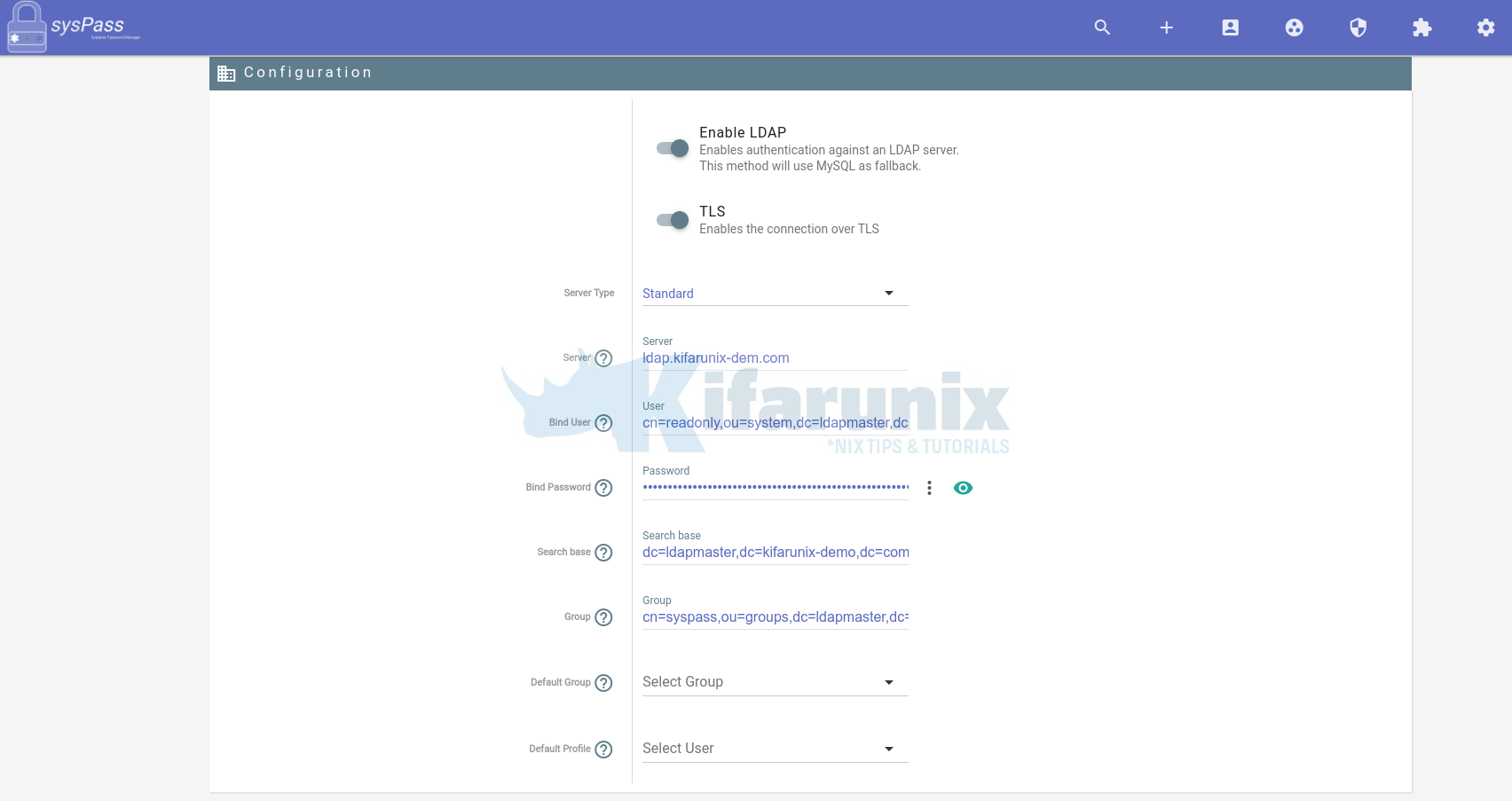
- Define sysPass OpenLDAP Configuration options
- Toggle the button to enable LDAP based authentication.
- Also turn on TLS connection if your OpenLDAP server is configured with TLS.
- To be able to use TLS connection, you need to;
- Install LDAP CA cert on the sysPass server
- Define the LDAP CA Path on sysPass server as shown below.
- To be able to use TLS connection, you need to;
- Server type:
standard. - Server:
- This is the LDAP server url or IP address. In our setup, ldap.kifarunix-demo.com.
- Bind User:
- This is the DN of the user to authenticate. In our setup, it is
cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com.
- This is the DN of the user to authenticate. In our setup, it is
- Bind Password:
- The credentials for the user to authenticate
- This is the password for the user specified by the bind DN above.
- Search Base:
- defines the location in the OpenLDAP directory where the search for a particular directory object begins.
- In our setup, the search base for users and groups is
dc=ldapmaster,dc=kifarunix-demo,dc=com.
- Group:
- This defines the group to which the user must belong to to be able to login to sysPass.
- As seen above, the group in our setup is
cn=syspass,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com.
- Default Group and Default Profile, leave empty.
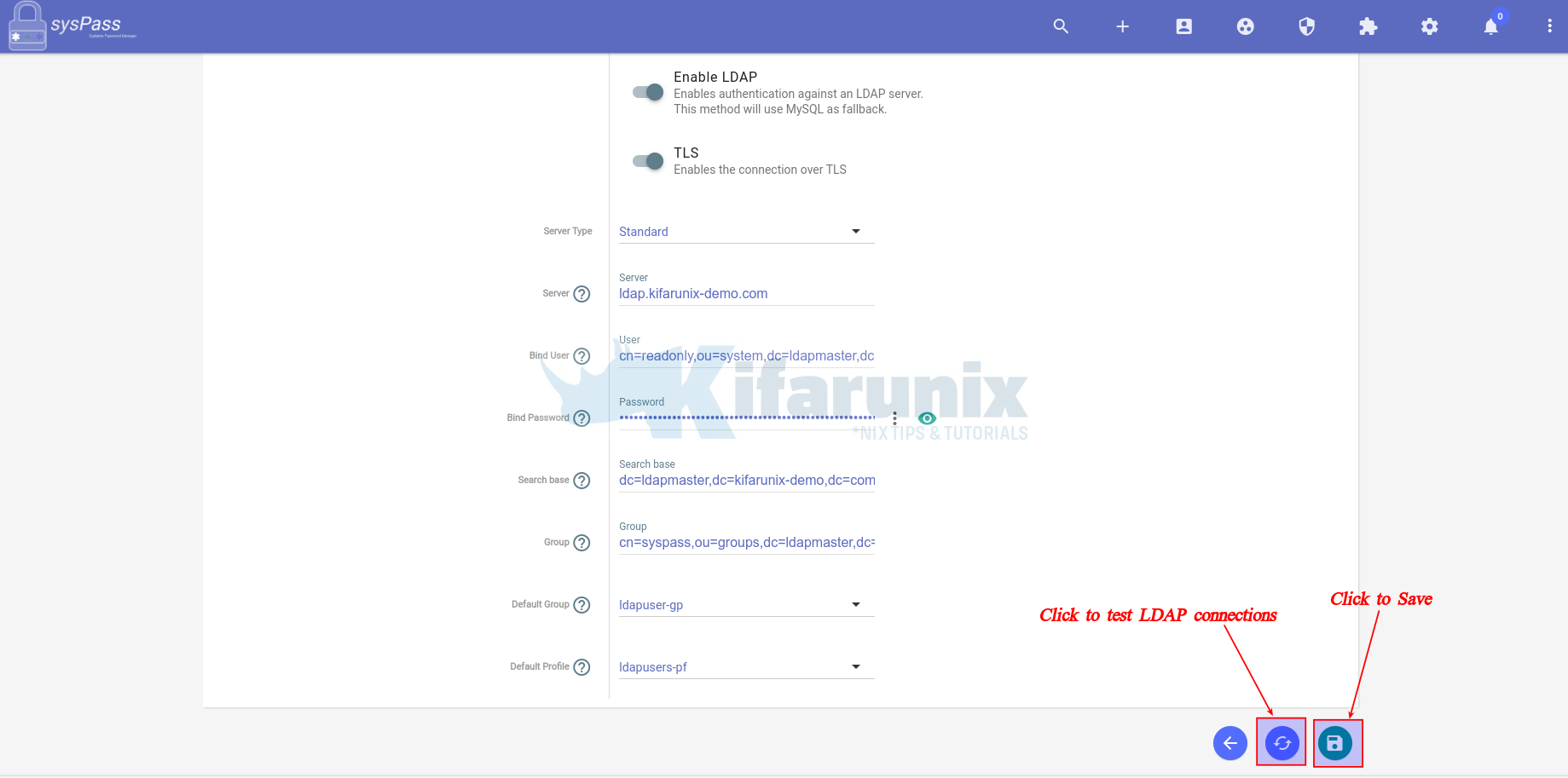
- Next, click the “exchange” icon to check connection to LDAP server. Ensure you have installed OpenLDAP CA certs if you enabled TLS before you can test the connection.
- If the connection is successful, you should see a list of all users in the OpenLDAP sysPass group.
Install OpenLDAP server CA cert and define the path on sysPass server.
Install OpenLDAP utilities on the sysPass server;
apt install ldap-utils -yDownload LDAP CA cert;
openssl s_client -connect ldap:389 -starttls ldap -showcerts </dev/null 2>/dev/null | openssl x509
-----BEGIN CERTIFICATE-----
MIIDozCCAougAwIBAgIUDd/aVBaJgUpWFNUbXOHYZTIb5KYwDQYJKoZIhvcNAQEL
BQAwYTELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UE
CgwTRGVmYXVsdCBDb21wYW55IEx0ZDEdMBsGA1UEAwwUKi5raWZhcnVuaXgtZGVt
by5jb20wHhcNMjIwMTIyMjAwOTUwWhcNMjMwMTIyMjAwOTUwWjBhMQswCQYDVQQG
EwJYWDEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENv
bXBhbnkgTHRkMR0wGwYDVQQDDBQqLmtpZmFydW5peC1kZW1vLmNvbTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBANVwVxFtjvHrgTHADFmE/NfsBjnnsorD
d6Hww+RDKTTdwpSQtAi5e9roP4umjLelQmIs2iPijBwFzTwh1ok7e40K0WFUCXwW
O2R2FomvwXe5D5VmlXLc4jY8/z6QuSv/j27q3DT44ywV8WmtWQ732cLo6YT1e441
LeXcCn258zvH8QE4UJOErJqDijFzuSxTj0gAsHe7ef+B2rhhD9Jzh6g4RYzDWmI3
oAZT/oArfWJFf+yP9eCunn/Q+b2RVWB9/Do9MYGdqOJJcDJ1w3pAyuEUWnDqTrhR
wjpIFub8lRlqrlNv7raw++aIIIUzCkl74/ReLgMRYlHAHC2pfMgLYjkCAwEAAaNT
MFEwHQYDVR0OBBYEFMN/TE6ZSw95erqDLAXa/LOfRFtqMB8GA1UdIwQYMBaAFMN/
TE6ZSw95erqDLAXa/LOfRFtqMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEL
BQADggEBAL+PuCNgR0MnOzl6IrxVZA9dDH0/DnMm2WjxkS3w5sfIPpUlVgSHmVeT
+a9raqFrve7RXHRBwouWlO/3n0218WSns6nyl9hTWbYIlIjCTFVCEFe68Q0ulcPy
AUEQBoKc6fUZCtenJDo2SVKt7dnX1EAi4Ohnig+f9zMrYFxYajdFAxJJV6wxJnnF
duLYpRexUxdzOvPUP4vkP2haZmRRWBDfmj2bSQF/r3DE4Yg8nVxHndsmxcVls4wF
7ddAL/Gx5Lv3QZPpxi8ZcHV8SRCP8N5VZP+hINr/M4gw3YO/S5F0TXnq5LQP0ePD
bkc1+yvlgKUPaXH20/C1COiGI+r8UGA=
-----END CERTIFICATE-----
Install the OpenLDAP CA cert on specific path;
cat > /etc/ssl/certs/openldap-ca.pem << 'EOL'
-----BEGIN CERTIFICATE-----
MIIDozCCAougAwIBAgIUDd/aVBaJgUpWFNUbXOHYZTIb5KYwDQYJKoZIhvcNAQEL
BQAwYTELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UE
CgwTRGVmYXVsdCBDb21wYW55IEx0ZDEdMBsGA1UEAwwUKi5raWZhcnVuaXgtZGVt
by5jb20wHhcNMjIwMTIyMjAwOTUwWhcNMjMwMTIyMjAwOTUwWjBhMQswCQYDVQQG
EwJYWDEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENv
bXBhbnkgTHRkMR0wGwYDVQQDDBQqLmtpZmFydW5peC1kZW1vLmNvbTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBANVwVxFtjvHrgTHADFmE/NfsBjnnsorD
d6Hww+RDKTTdwpSQtAi5e9roP4umjLelQmIs2iPijBwFzTwh1ok7e40K0WFUCXwW
O2R2FomvwXe5D5VmlXLc4jY8/z6QuSv/j27q3DT44ywV8WmtWQ732cLo6YT1e441
LeXcCn258zvH8QE4UJOErJqDijFzuSxTj0gAsHe7ef+B2rhhD9Jzh6g4RYzDWmI3
oAZT/oArfWJFf+yP9eCunn/Q+b2RVWB9/Do9MYGdqOJJcDJ1w3pAyuEUWnDqTrhR
wjpIFub8lRlqrlNv7raw++aIIIUzCkl74/ReLgMRYlHAHC2pfMgLYjkCAwEAAaNT
MFEwHQYDVR0OBBYEFMN/TE6ZSw95erqDLAXa/LOfRFtqMB8GA1UdIwQYMBaAFMN/
TE6ZSw95erqDLAXa/LOfRFtqMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEL
BQADggEBAL+PuCNgR0MnOzl6IrxVZA9dDH0/DnMm2WjxkS3w5sfIPpUlVgSHmVeT
+a9raqFrve7RXHRBwouWlO/3n0218WSns6nyl9hTWbYIlIjCTFVCEFe68Q0ulcPy
AUEQBoKc6fUZCtenJDo2SVKt7dnX1EAi4Ohnig+f9zMrYFxYajdFAxJJV6wxJnnF
duLYpRexUxdzOvPUP4vkP2haZmRRWBDfmj2bSQF/r3DE4Yg8nVxHndsmxcVls4wF
7ddAL/Gx5Lv3QZPpxi8ZcHV8SRCP8N5VZP+hINr/M4gw3YO/S5F0TXnq5LQP0ePD
bkc1+yvlgKUPaXH20/C1COiGI+r8UGA=
-----END CERTIFICATE-----
EOL
You can use one command though;
openssl s_client -connect ldap:389 -starttls ldap
-showcerts </dev/null 2>/dev/null |
openssl x509 > /etc/ssl/certs/openldap-ca.pemsysPass OpenLDAP User Login
Once you have configured sysPass for OpenLDAP authentication, you need to generate a temporary master password as it is required for every first login. Temporary master password is used so as not to reveal the original admin password.
To generate temporary master password, login to sysPass as admin and navigate to Configuration > Encryption > Temporary Password. Note the lifetime of the password.
For every new user logging in, share with them the temporary master password generated.
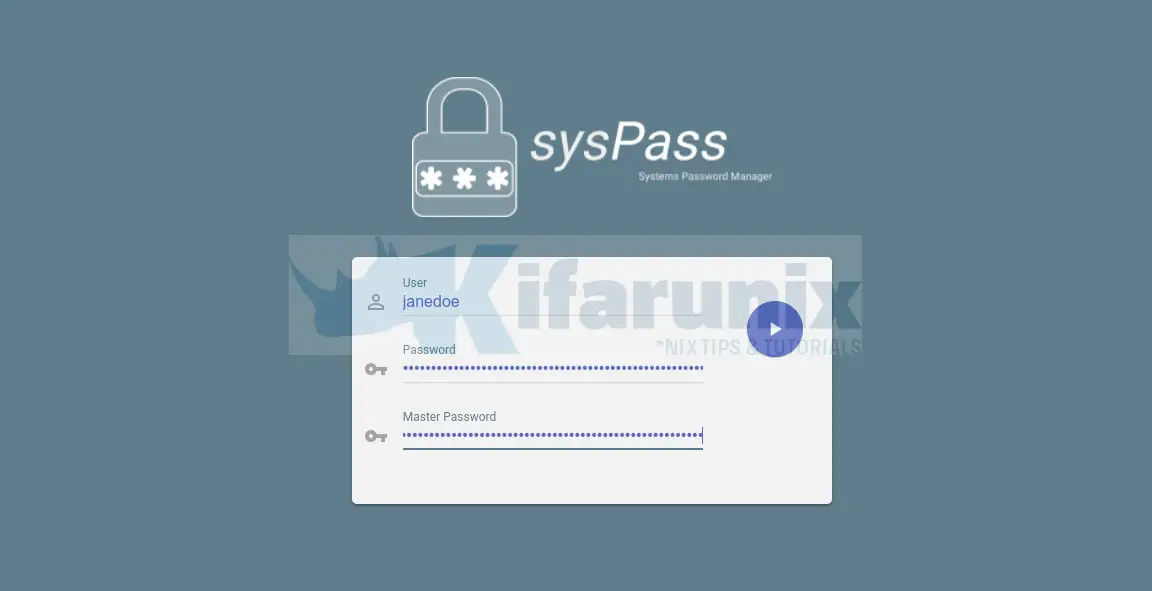
For example, logging in as our LDAP user janedoe;
When you first enter your credentials and press Enter, authentication will fail with Master password is not saved or wrong.
The enter the username/password and temporary master password provided.
From Administrator site, you should be able to see LDAP accounts added to the sysPass system.
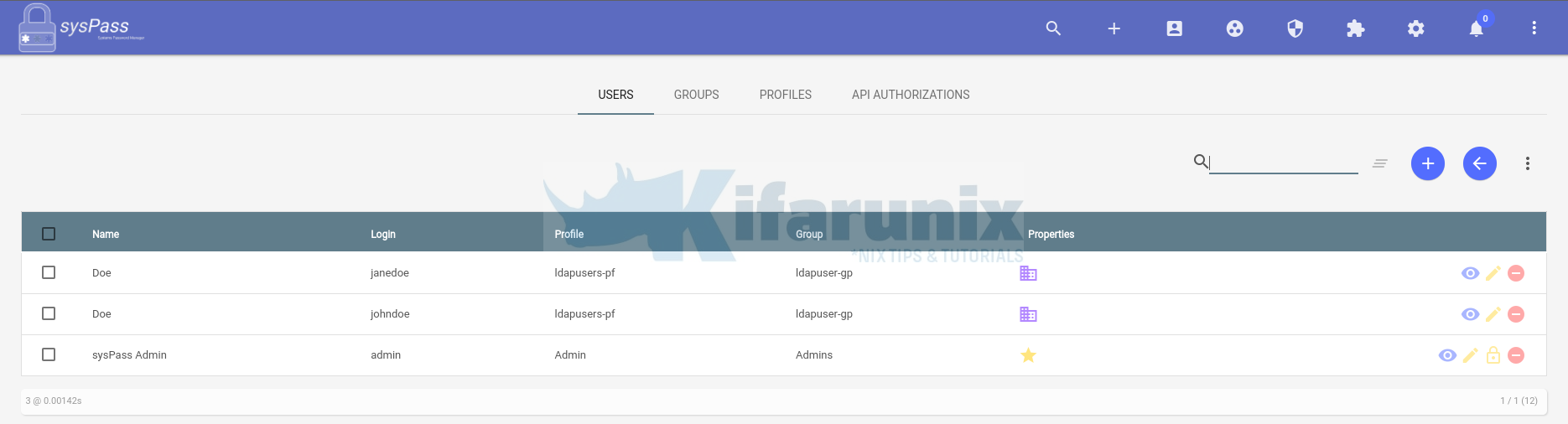
And that is how easily you can integrate sysPass with OpenLDAP for authentication.
Other Tutorials
Configure SSSD for LDAP Authentication on Ubuntu 22.04
Integrate Gitlab with OpenLDAP for Authentication
If you are getting error below after giving the correct password
Nov 2 03:56:42 testserver sshd[30173]: pam_ldap: error trying to bind as user «uid=testuser,ou=People,dc=test,dc=testdomain,dc=com» (Invalid credentials)
Nov 2 03:56:43 testserver sshd[30173]: Failed password for testuser from 10.17.0.3 port 51306 ssh2
Reason: Password is not syncing properly to all client server during the scheduled window
Solution : Restart the slapd service on LDAP server & it will sync to all server.
#/etc/init.d/slapd restart
Hope it helps.


