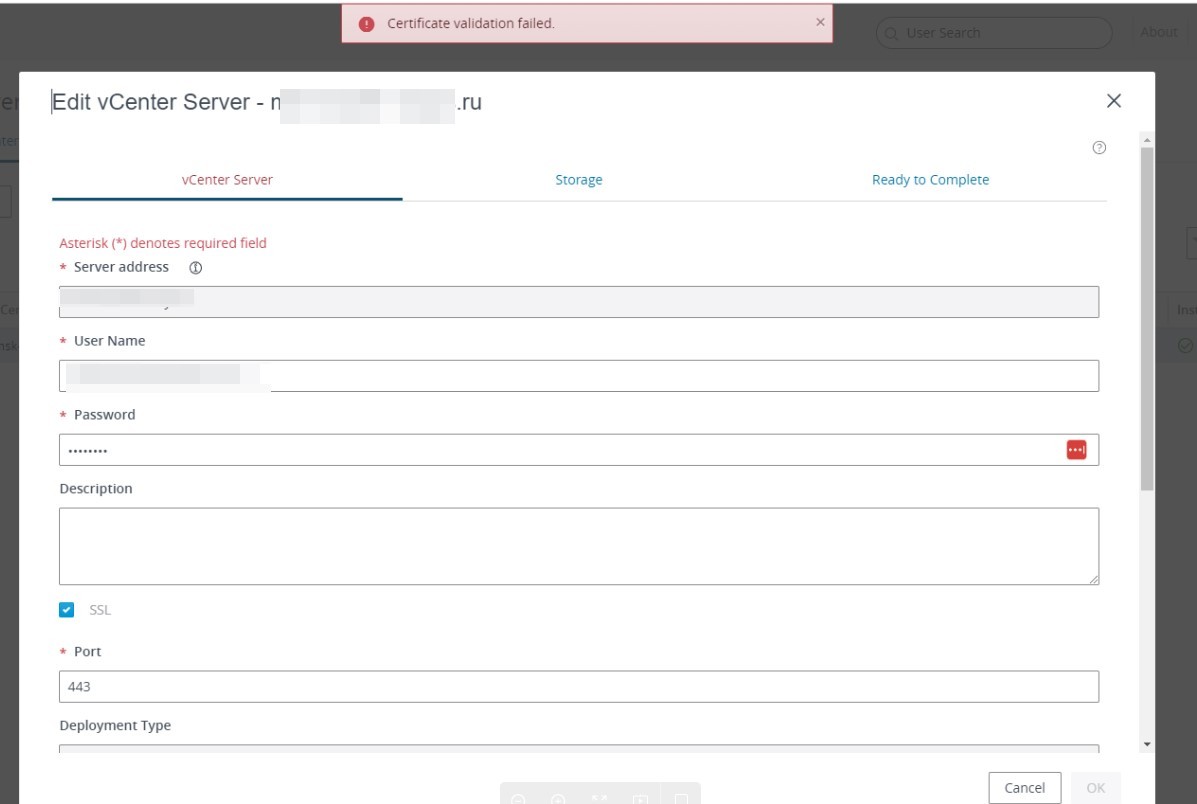
Ошибки на connect server horizon C:ProgramDataVMwareVDMlogs
2022-09-13T11:11:08.024+03:00 ERROR (1238-1A54) <ajp-nio-127.0.0.1-8009-exec-7> [Connection4] Connection to the vCenter Server https://msk-vcsa01.adminbd.ru:443/sdk failed.
2022-09-13T11:11:08.031+03:00 DEBUG (1238-1A54) <ajp-nio-127.0.0.1-8009-exec-7> [Connection4] [EXCEPTION] Connection to the vCenter Server https://msk-vcsa01.adminbd.ru:443/sdk failed.: javax.xml.ws.WebServiceException: Could not send Message. com.vmware.vdi.logger.Logger.debug(Logger.java:44)
javax.xml.ws.WebServiceException: Could not send Message.
at org.apache.cxf.jaxws.JaxWsClientProxy.mapException(JaxWsClientProxy.java:183)
at org.apache.cxf.jaxws.JaxWsClientProxy.invoke(JaxWsClientProxy.java:145)
at com.sun.proxy.$Proxy273.retrieveServiceContent(Unknown Source)
at com.vmware.vdi.vcwrapper.Connection4.connect(SourceFile:199)
at com.vmware.vdi.vcwrapper.Connection4.connect(SourceFile:173)
at com.vmware.vdi.vcwrapper.ConnectionManager.getConnection4(SourceFile:93)
at com.vmware.vdi.vlsi.server.utils.certificate.VirtualCenterCertificateHandler.validate(VirtualCenterCertificateHandler.java:60)
at com.vmware.vdi.vlsi.server.utils.certificate.ServerSpecCertificateHandler.validate(ServerSpecCertificateHandler.java:42)
at com.vmware.vdi.vlsi.server.utils.certificate.ServerSpecCertificateHandler.validate(ServerSpecCertificateHandler.java:10)
at com.vmware.vdi.vlsi.server.utils.certificate.CertificateServer.validate(CertificateServer.java:58)
at com.vmware.vdi.vlsi.server.utils.certificate.CertificateServer.validate(CertificateServer.java:41)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(Unknown Source)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(Unknown Source)
at java.base/java.lang.reflect.Method.invoke(Unknown Source)
at com.vmware.vdi.vlsi.rest.service.impl.VlsiMethodWrapper.invoke(VlsiMethodWrapper.java:49)
at com.vmware.vdi.vlsi.rest.reflect.impl.VlsiInvocation.invoke(VlsiInvocation.java:81)
at com.vmware.vdi.vlsi.rest.reflect.ReflectEngine.invokeService(ReflectEngine.java:79)
at com.vmware.vdi.vlsi.rest.RestApiServlet.doPost(RestApiServlet.java:145)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:681)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:764)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.filters.FailedRequestFilter.doFilter(FailedRequestFilter.java:97)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at com.vmware.vdi.vlsi.rest.EncodingFilter.doFilter(EncodingFilter.java:37)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at com.vmware.vdi.vlsi.rest.authentication.RestApiAuthFilter.doFilter(RestApiAuthFilter.java:143)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at com.github.ziplet.filter.compression.CompressingFilter.doFilter(CompressingFilter.java:263)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:197)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:97)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:543)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:135)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:78)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:367)
at org.apache.coyote.ajp.AjpProcessor.service(AjpProcessor.java:526)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:882)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1691)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at org.apache.tomcat.util.threads.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1191)
at org.apache.tomcat.util.threads.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:659)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.base/java.lang.Thread.run(Unknown Source)
Caused by: javax.net.ssl.SSLHandshakeException: SSLHandshakeException invoking https://msk-vcsa01.adminbd.ru:443/sdk: Certificates do not conform to algorithm constraints
at java.base/jdk.internal.reflect.NativeConstructorAccessorImpl.newInstance0(Native Method)
at java.base/jdk.internal.reflect.NativeConstructorAccessorImpl.newInstance(Unknown Source)
at java.base/jdk.internal.reflect.DelegatingConstructorAccessorImpl.newInstance(Unknown Source)
at java.base/java.lang.reflect.Constructor.newInstance(Unknown Source)
at org.apache.cxf.transport.http.HTTPConduit$WrappedOutputStream.mapException(HTTPConduit.java:1400)
at org.apache.cxf.transport.http.HTTPConduit$WrappedOutputStream.close(HTTPConduit.java:1384)
at org.apache.cxf.transport.AbstractConduit.close(AbstractConduit.java:56)
at org.apache.cxf.transport.http.HTTPConduit.close(HTTPConduit.java:671)
at org.apache.cxf.interceptor.MessageSenderInterceptor$MessageSenderEndingInterceptor.handleMessage(MessageSenderInterceptor.java:63)
at org.apache.cxf.phase.PhaseInterceptorChain.doIntercept(PhaseInterceptorChain.java:308)
at org.apache.cxf.endpoint.ClientImpl.doInvoke(ClientImpl.java:530)
at org.apache.cxf.endpoint.ClientImpl.invoke(ClientImpl.java:441)
at org.apache.cxf.endpoint.ClientImpl.invoke(ClientImpl.java:356)
at org.apache.cxf.endpoint.ClientImpl.invoke(ClientImpl.java:314)
at org.apache.cxf.frontend.ClientProxy.invokeSync(ClientProxy.java:96)
at org.apache.cxf.jaxws.JaxWsClientProxy.invoke(JaxWsClientProxy.java:140)
... 48 more
2022-09-13T10:02:03.532+03:00 ERROR (150C-1244) <ABSGC33> [cc] Error executing request
2022-09-13T10:03:52.516+03:00 ERROR (02B4-0674) <ajp-nio-127.0.0.1-8009-exec-8> [Connection4] Connection to the vCenter Server https://msk-vcsa01.adminbd.ru:443/sdk failed.
2022-09-13T10:03:52.579+03:00 ERROR (02B4-0674) <ajp-nio-127.0.0.1-8009-exec-8> [FaultUtilBase] UnexpectedFault: Unexpected failure during certificate validation.
2022-09-13T10:03:52.587+03:00 ERROR (02B4-0674) <ajp-nio-127.0.0.1-8009-exec-8> [RestApiServlet] Unexpected fault:(vdi.fault.UnexpectedFault) {
errorMessage = Unexpected failure during certificate validation.,
causeString = null,
causeStackTrace = null,
errorCode = CERTIFICATE_VALIDATION_FAILED,
errorAttributes = null
} for uri /view-vlsi/rest/v1/Certificate/Validate
2022-09-13T10:05:22.602+03:00 ERROR (02B4-143C) <ajp-nio-127.0.0.1-8009-exec-7> [Connection4] Connection to the vCenter Server https://msk-vcsa01.adminbd.ru:443/sdk failed.
2022-09-13T10:05:22.606+03:00 ERROR (02B4-143C) <ajp-nio-127.0.0.1-8009-exec-7> [FaultUtilBase] UnexpectedFault: Unexpected failure during certificate validation.
2022-09-13T10:05:22.607+03:00 ERROR (02B4-143C) <ajp-nio-127.0.0.1-8009-exec-7> [RestApiServlet] Unexpected fault:(vdi.fault.UnexpectedFault) {
errorMessage = Unexpected failure during certificate validation.,
causeString = null,
causeStackTrace = null,
errorCode = CERTIFICATE_VALIDATION_FAILED,
errorAttributes = null
} for uri /view-vlsi/rest/v1/Certificate/Validate
https://kb.vmware.com/s/article/89331
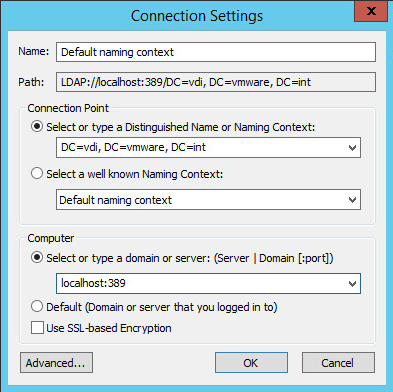
Заходим в ADSI Edit
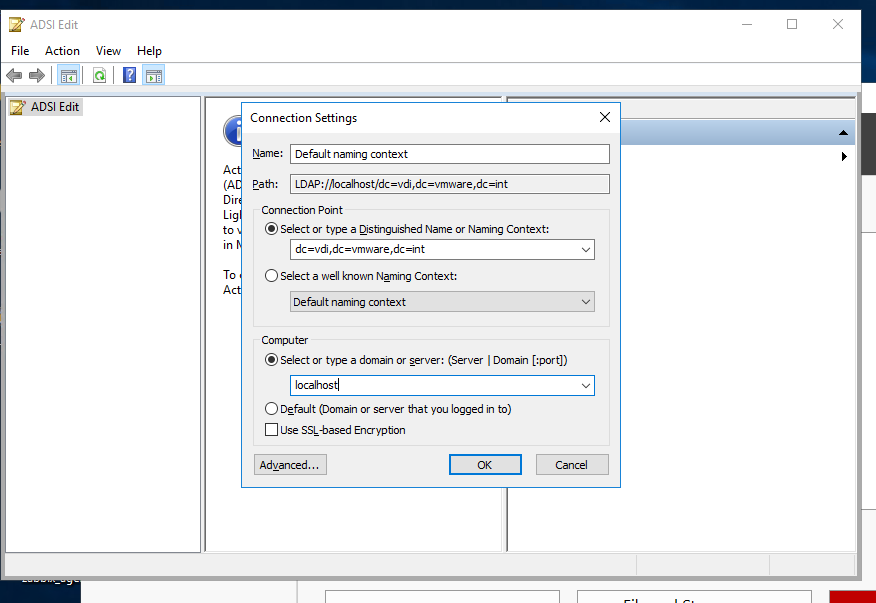
- Измените первый выбор на Select или введите Distinguished Name и введите dc=vdi,dc=vmware,dc=int
- Измените второй выбор на Выберите или введите домен или сервер и введите localhost . Нажмите ОК .
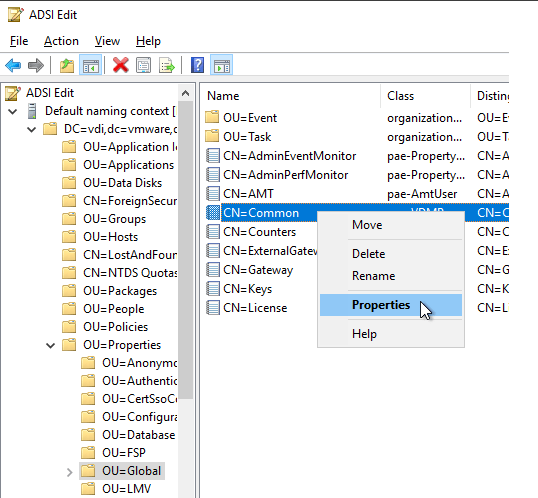
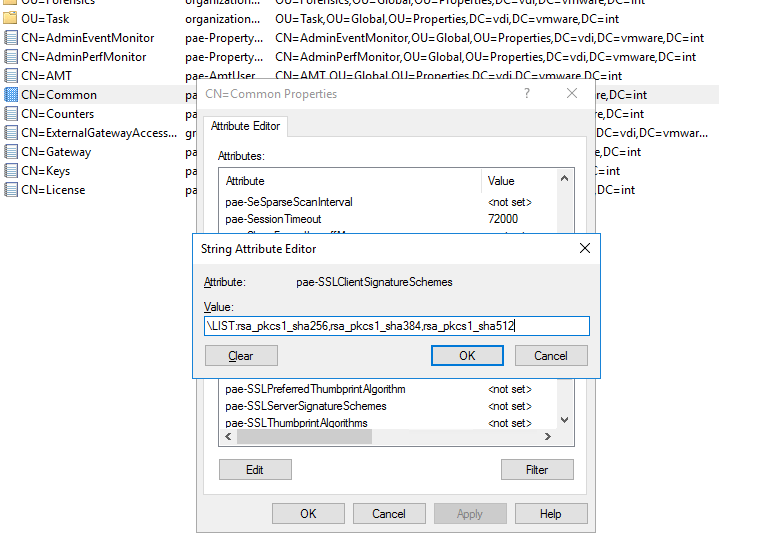
3. Перейдите в « Свойства» > «Глобальные» . Справа дважды щелкните CN=Common .
4. pae-SSLClientSignatureSchemes LIST:rsa_pkcs1_sha256,rsa_pkcs1_sha384,rsa_pkcs1_sha512
5. Перезагрузка сервера. Делаем на каждом сервере Connection-Server .
Similar Posts:
Issue Description
When using the new Horizon View Client version 4.0 you receive an SSL error when connecting to the tenant connection server. This is because DaaS uses TLS 1.0 and TLS 1.0 is disabled in version 4.
Solution / Workaround
Option 1
Use Horizon View Client 3.5.2.
Option 2
Use the group policy to configure the view client to use or allow TLS 1.0.
- Download the Horizon 7 GPO Bundle from the VMware Horizon 7.0.0 Enterprise download page (must be logged in to open link).
- Extract vdm_client.adm from the zip file.
- Run gpedit.msc on the client OS to launch the Local group Policy Editor.
- Go to Local Computer Policy > Computer Configuration > Administrative Templates.
- Right click and select Add/Remove Templates.
- Click Add.
- Navigate to the location where you extracted the vdm_client.adm file and select it.
- Go to Local Computer Policy > Computer Configuration > Administrative Template > Classic Administrative Templates > VMware View Client Configuration > Security Settings and then double-click Configures SSL protocols and cryptographic algoirthms.
- Select the Enabled radio button.
- In the Options pane, enter the following in the text field: TLSv1:TLSv1.1:TLSv1.2:!aNULL:kECDH+AES:ECDH+AES:RSA+AES:@STRENGTH
- Click OK.
- Launch View client.
Please see the following KB Article for more information: https://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2144623
I noticed today that myself and our end users are getting a generic SSL error message:
Error: An SSL error has occurred
This is showing up in the Horizon client, and on our thin clients. We’re on Horizon 6.0.1 and have 1 load balancer, 2 security servers, and 4 connection servers. After this message pops up you can just click on okay, and then reconnect and it will work just fine.
I’m not completely sure where to start on troubleshooting this.
It happens internally and externally. We have a load balancer that everybody connects to that distributed the session to 4 different connection servers. If I manually connect to the servers I do not receive the SSL error, but when I connect to our main generic URL I get the error. The sys admins are tied up all day so I’m trying to troubleshoot this on my own as much as I can.
The only thing I’ve done sofar is browse out to our generic vmview address view a web browser, and check the certificate. The certificate is still active/valid.
Are there any log files on the security servers or connection servers that I can look in to to narrow this down?
День мучений, и из-за чего? Надеюсь кому-нибудь поможет избежать напрасной траты времени.
Итак, при установке Vmware View Connection Server мы СНАЧАЛА разрешаем получать сертификат типа «веб-сервер» у нашего СА для наших CS-серверов.
Затем получаем сертификат у нашего СА.
А уж потом ставим сам CS.
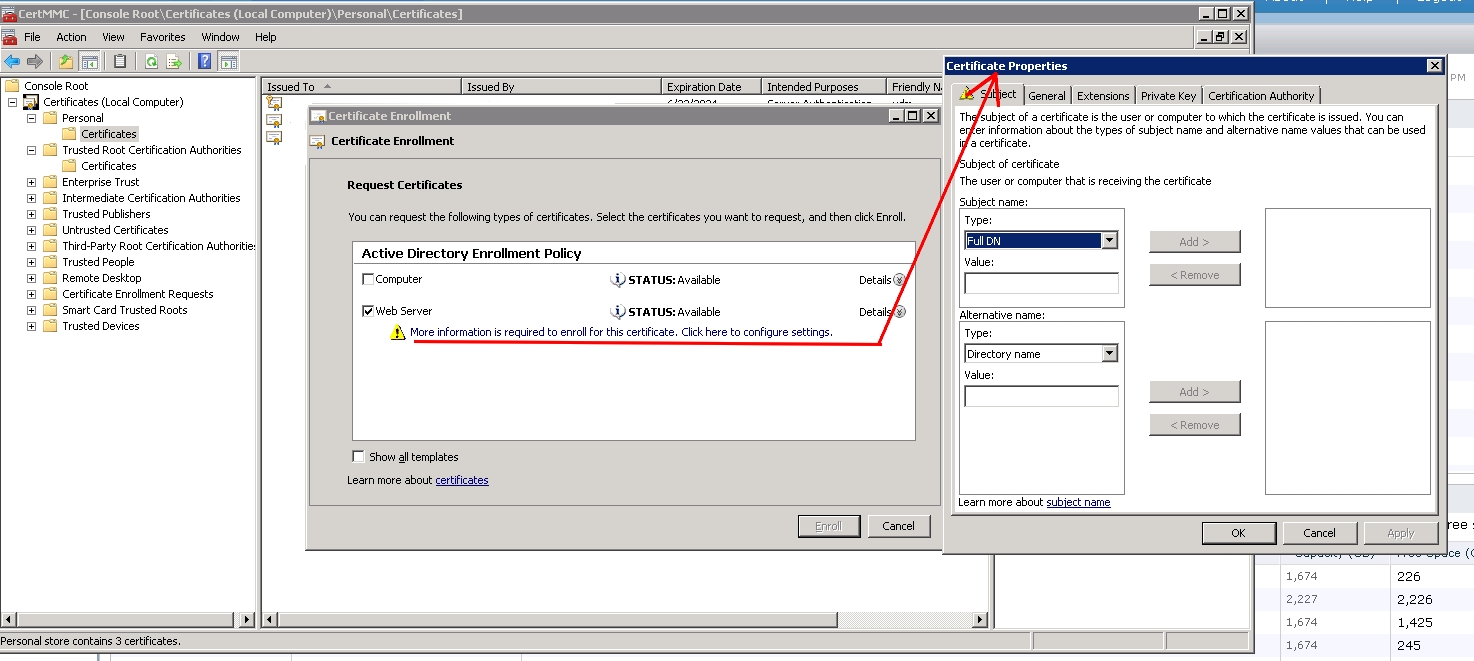
Иллюстрация сказанного:
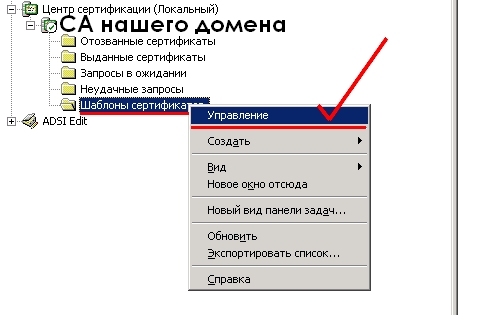
Разрешаем получать сертификаты типа Web-server нашему будущему Connection Server на нашем доменном центре сертификации (ВНИМАНИЕ! это должен быть или корневой ЦС, или, если это подчиненный ЦС — сертификат должне включать всю цепочку до корневого ЦС). Открываем оснастку ЦС, Шаблоны сертификатов, пр кнопкой — Управление. В примере — ЦС на 2003 контроллере домена.
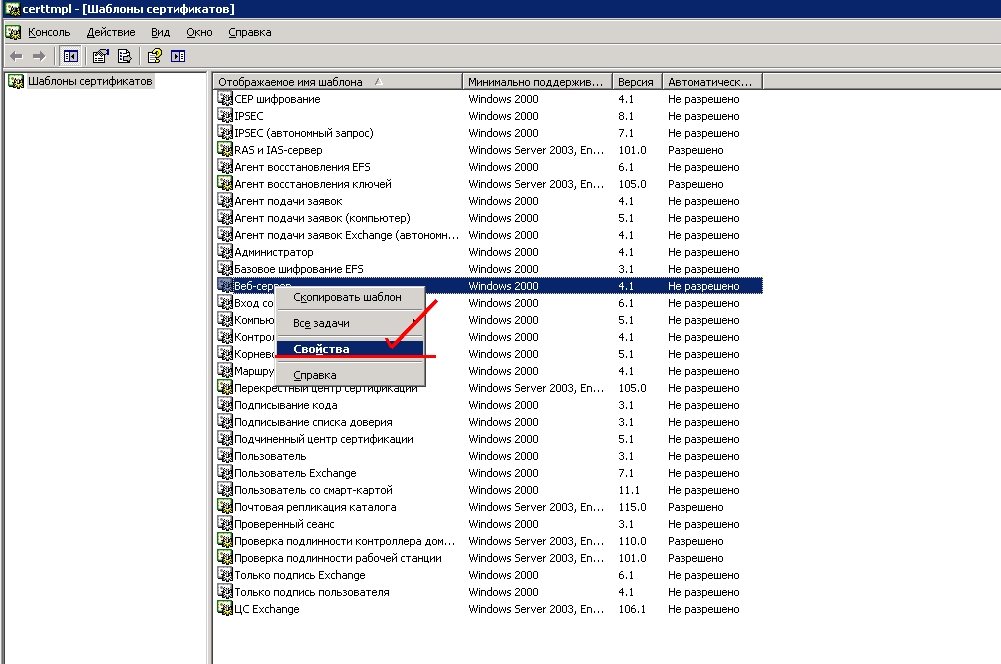
В открывшемся окне выбираем шаблон Веб-сервер, пр кнопкой — Свойства.
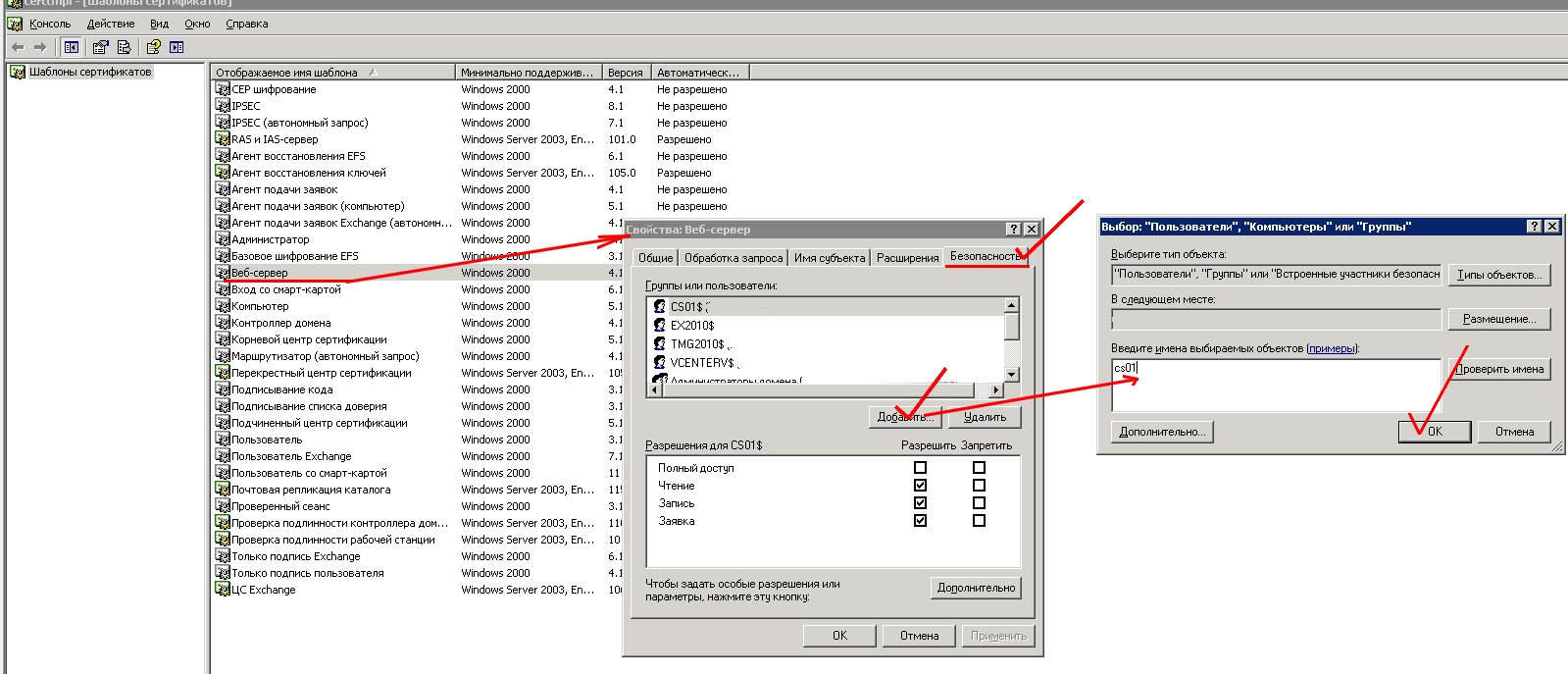
В открывшемся окне во вкладке Безопасность добавляем наш будущеий сервер CS, если сервер не виден — выбираем в Тип объекта также и Компьютеры.
Затем идем на наш будущеий CS-сервер, открываем оснастку ММС, добавляем Сертификаты — Локального ПК. Пр кнопкой на поле — Создать запрос. Ставим галку напротив Web-server, жмем ссылку на настройку атрибутов сертификата:
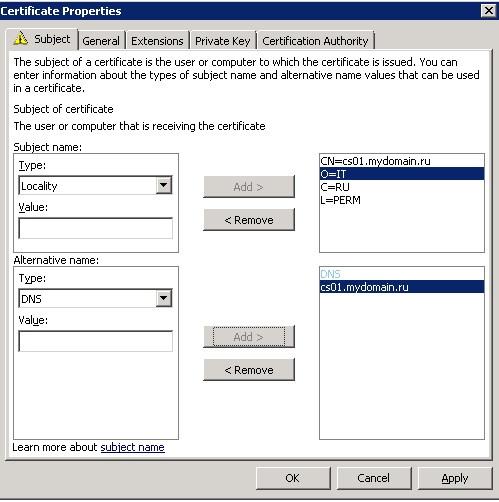
Заполняем поля атрибутов, хватит следующих — Common Name Country Locality Organization. Также не забываем заполнить поле Alternate Name DNS, пишем то же самое что и СN:
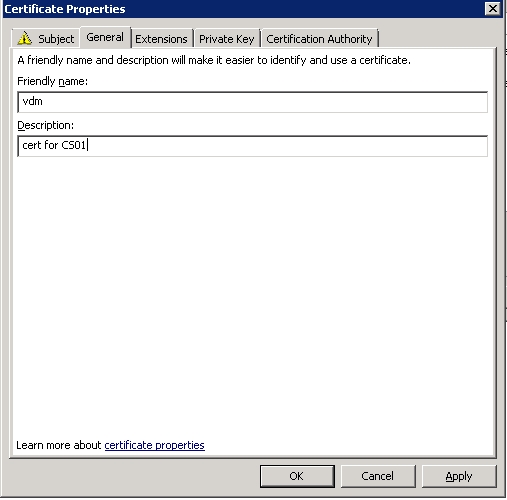
Дружественное имя делаем именно таким — VDM — зачем-то в мануалах vmware много на это указаний, может там внутри чего привязано именно к этом имени
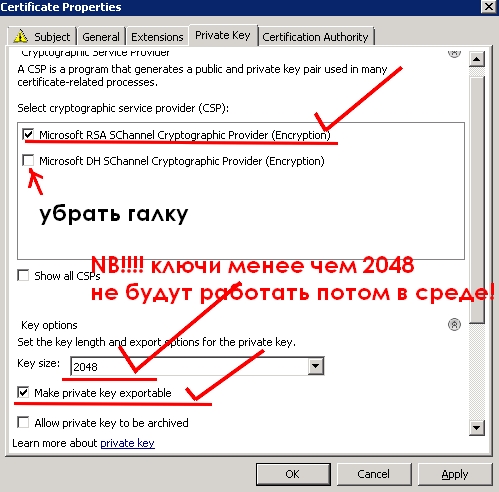
Обращаем внимание, что ключ должен быть не менее 2048 символов. Иначе потом начнутся какие-то грабли при работе всей структуры.
ОК, Apply, готово.
Теперь можно ставить сам Connection Server, он не станет создавать «самоподписной» сертификат, а будет использовать вот этот, уже готовый.
Join @AdmNtsRu on Telegram
Смотрите также:
После обновления VMware View Connection Server до версии 7.0 при использовании серверов vCenter Server версии 5.0, 5.1 или 5.5 они перестают быть доступны из интерфейса View Administrator, а на вкладке Dashboard при просмотре свойств vCenter может появиться следующая ошибка.
Нажатие на кнопку Verify не приводит ни к какому результату. При попытке изменить настройки существующего сервера vCenter или добавить новый vCenter из вкладки View Configuration появляется ошибка:
vmware horizon view possibly an invalid vcenter server certificate please verity the identity of the associated vcenter server
В файле debug-*.txt на сервере View Connection Server можно найти следующие сообщения:
Server chose TLSv1, but that protocol version is not enabled or not supported by the client.
Причина проблемы: В Horizon 7 по умочанию отключен протокол TLSv1, который используется в старых версиях VMware vCenter Server. Для решения проблемы следует обновить VMware vCenter Server, либо включить поддержку TLSv1 в Horizon. Для этого выполните следующие действия:
- Выполните вход на любой из серверов View Connection Server.
- Запустите ADSI Edit.
- В поле Distinguished Name or Naming Context укажите «DC=vdi, DC=vmware, DC=int«.
- В поле Select or type a domain or server укажите «localhost:389«.
- Раскройте дерево ADSI Edit: «OU=Global, OU=Properties, DC=vdi, DC=vmware, DC=int«.
- Откройте свойства объекта CN=common.
- Найдите и отредактируйте атрибут pae-ClientSSLSecureProtocols, указав в качестве значения: «LIST:TLSv1.2,TLSv1.1,TLSv1» (не забудьте обратный слэш в начале строки).
- Нажмите OK для применения параметров.
- Перезапустите службу VMware Horizon View Connection Server на всех серверах View Connection Server.
После выполнения настроек, серверы View Connection Server смогут использовать протокол TLSv1 для подключения к vCenter Server.
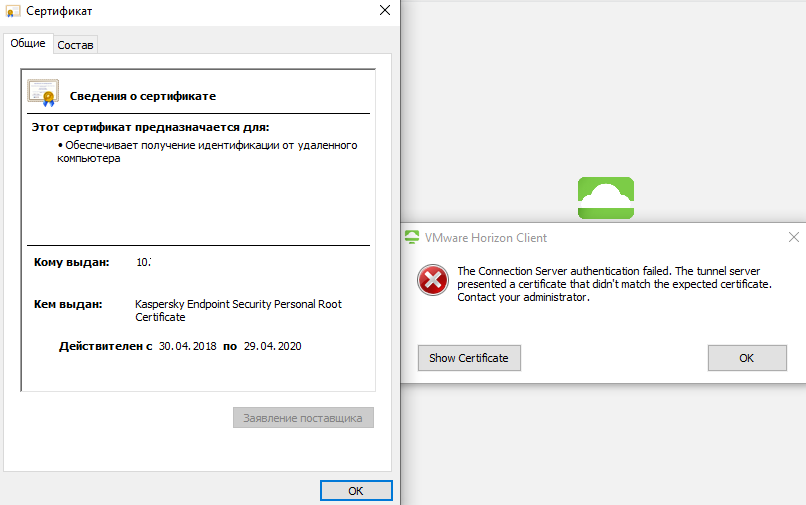
Установлен KES для windows версии 11.1.0.15919 AES56 с последними базами. Windows 10 LTSC x64.
При подключении через VMware Horizon client 5.0 последней актуальной версии, с включенной проверкой сертификата появляется ошибка не доверенного сертификата, причём сертификат подписан касперским (в строке куму указан сервер куда подключаемся),
если отключить проверку сертификата при авторизации, появляется другая ошибка и подключаться так же не даёт.
При работе с VMware vSphere Client 5.1 и 5.5 версии так же замечены проблемы в виде невозможности открыть консоль(если ответить окошку всё равно не открывает).
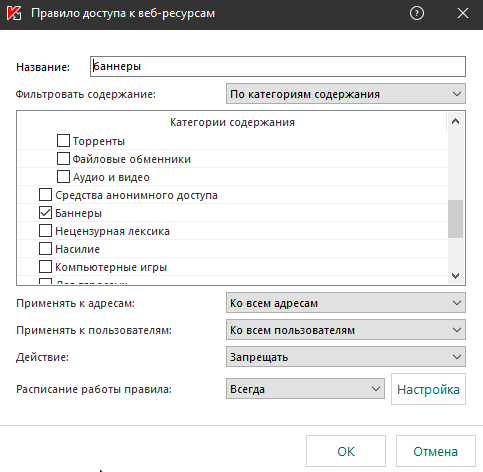
Опытным путём была выявлено что проблема возникает при включенном веб-контроле и активном любом правиле(изначально было одно правило на запрет баннеров, для экспериментов создавал запрет для списка адресов где вписывал всего один сайт) на запрет или предупреждение, если это правило просто отключить, то везде начинает открываться как надо. Как мне подключаться к серверам с включенными запретными правилами веб-контроля? И собстввено почему продукт подменяет сертификаты на свои нерабочие?
Hello there,
I have a user with a client of ours that gets a SSL error when opening up VMware Horizon Client. However, the error itself doesn’t happen every day and if the user press OK, she can move forward into the program with no issue. No other user is experiencing this. What I want to ask is what would be causing this and what can I do to remedy this? Normally, something like this isn’t a big deal but the client considers themselves to be high profile and always ask for our help to be urgent. Error is attached.
Go to vmware
Troubleshooting steps for SSL Error — Horizon
I noticed today that myself and our end users are getting a generic SSL error message:
Error: An SSL error has occurred
This is showing up in the Horizon client, and on our thin clients. We’re on Horizon 6.0.1 and have 1 load balancer, 2 security servers, and 4 connection servers. After this message pops up you can just click on okay, and then reconnect and it will work just fine.
I’m not completely sure where to start on troubleshooting this.
It happens internally and externally. We have a load balancer that everybody connects to that distributed the session to 4 different connection servers. If I manually connect to the servers I do not receive the SSL error, but when I connect to our main generic URL I get the error. The sys admins are tied up all day so I’m trying to troubleshoot this on my own as much as I can.
The only thing I’ve done sofar is browse out to our generic vmview address view a web browser, and check the certificate. The certificate is still active/valid.
Are there any log files on the security servers or connection servers that I can look in to to narrow this down?
Hi Amin,
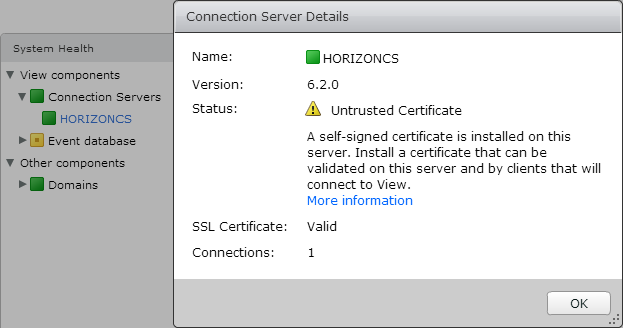
I did some work recently:
1. I followed this post’s instructions, and a self-signed certificate is installed on horizon connection server and the details of it in the connection server console is shown in figure below.
however, my VDI session tests’ results were not perfect and some client windows VMs still have the SSL error.
note that my client windows VMs are provisioned by the Horizon too.
so is it possible that the SSL error problem persist due to the «untrusted certificate»??
2. do I need to import the connection server’s certificate into all the client VMs’ MMC?
3. I checked the Horizon Client’s logs on different windows desktops that had this «SSL error» and they all showed similar errors, as listed below:
ERROR (0750) [WinCDK] utils::ParseServerUrl : Unexpectedly unable to parse URL ».
ERROR (077C) [WinCDK] UpdateMgrCDS::CdsLogCallback : CdsUtil_RemoveFile: Unable to remove file C:UsersuserAppDataLocalTempcdstmp_1692_0
ERROR (077C) [WinCDK] UpdateMgrCDS::CdsLogCallback : Failed to finish active transfer for https://softwareupdate.vmware.com/horizon-clients/index.xml: CDS_HTTP_HOST_RESOLVE_ERROR
INFO (0750) [WinCDK] BaseServices::ErrorCallback : Error(Taskname:CdkSetLocaleTask, domain:54, code:35) Callback: Entry.
ERROR (0750) [WinCDK] DefaultErrorHandler::ProcessError : DefaultErrorHandler process error ‘Error: An SSL error occurred’ (code=35).
ERROR (0468) [WinCDK] UpdateMgrCDS::CdsLogCallback : CdsUtil_RemoveFile: Unable to remove file C:UsersuserAppDataLocalTempcdstmp_7824_0
2019-10-28T20:26:35.526-07:00| host-1128| I125: DictionaryLoad: Cannot open file «C:ProgramDataVMwareVMware Horizon Viewconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.526-07:00| host-1128| I125: [msg.dictionary.load.openFailed] Cannot open file «C:ProgramDataVMwareVMware Horizon Viewconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.526-07:00| host-1128| I125: PREF Optional preferences file not found at C:ProgramDataVMwareVMware Horizon Viewconfig.ini. Using default values.
2019-10-28T20:26:35.541-07:00| host-1128| I125: DictionaryLoad: Cannot open file «C:ProgramDataVMwareVMware Horizon Viewsettings.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: [msg.dictionary.load.openFailed] Cannot open file «C:ProgramDataVMwareVMware Horizon Viewsettings.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: PREF Optional preferences file not found at C:ProgramDataVMwareVMware Horizon Viewsettings.ini. Using default values.
2019-10-28T20:26:35.541-07:00| host-1128| I125: DictionaryLoad: Cannot open file «C:ProgramDataVMwareVMware Horizon Viewconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: [msg.dictionary.load.openFailed] Cannot open file «C:ProgramDataVMwareVMware Horizon Viewconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: PREF Optional preferences file not found at C:ProgramDataVMwareVMware Horizon Viewconfig.ini. Using default values.
2019-10-28T20:26:35.541-07:00| host-1128| I125: DictionaryLoad: Cannot open file «C:UsersuserAppDataRoamingVMwareconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: [msg.dictionary.load.openFailed] Cannot open file «C:UsersuserAppDataRoamingVMwareconfig.ini»: The system cannot find the file specified.
2019-10-28T20:26:35.541-07:00| host-1128| I125: PREF Optional preferences file not found at C:UsersuserAppDataRoamingVMwareconfig.ini. Using default values.
I attached the logs but I don’t think these error messages truly help.
can anyone provide some clues?
,
last updated February 17, 2016, in
This is a description of a quick and dirty way to get SSL to work correctly in a VMware Horizon View installation in a lab environment. Do not do this in production!
The Situation
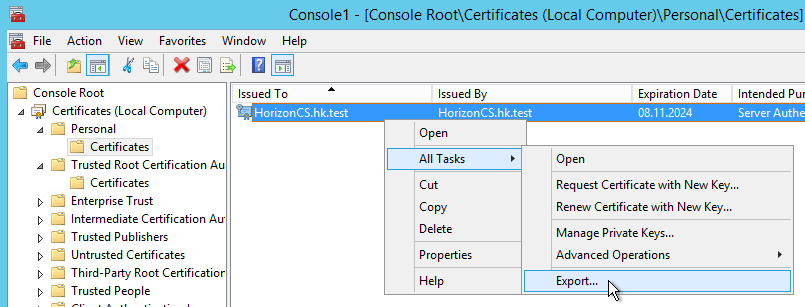
The Horizon View Connection Server installer creates a self-signed certificate which it places in the computer’s personal certificate store. This certificate’s root is not trusted by anyone, least of all by the clients trying to connect to your apps and desktops.
Establishing Trust
To make the default self-signed certificate work correctly you need to export it from the computer’s personal certificate store and then re-import it in the trusted root certificate store.
Exporting
It is OK to export without a private key; leave the file format at the default.
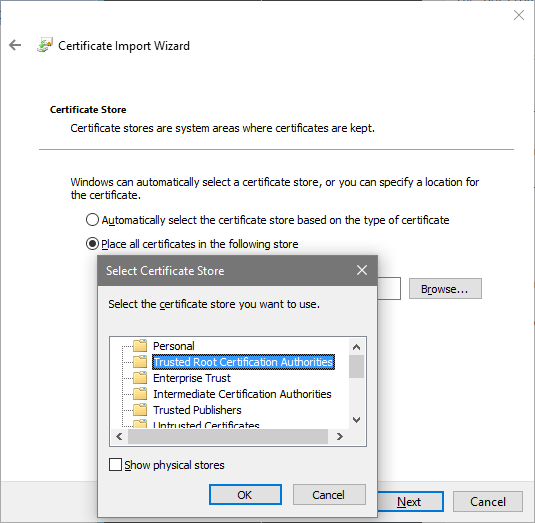
Importing – Connection Server
When re-importing the key on the Horizon View Connection Server manually select the computer’s Trusted Root Certification Authorities store:
After the import restart the Connection Server machine. View Administrator should now display the Connection Server status in green (certificate valid):
Importing – Clients
Clients that connect to Horizon need the certificate imported as trusted root certificate in the same way as described for the Connection Server above.
Name Resolution
Clients connecting to Horizon View need to be able to resolve the name as it is stored in the certificate, in all likelihood fully qualified. If your (lab) clients use a different DNS server than the Horizon installation the simplest solution is to add the Connection Server’s name and IP address to each client’s hosts file.
About the Author
Helge Klein (ex CTP, MVP and vExpert) worked as a consultant and developer before founding vast limits, the uberAgent company. Helge applied his extensive knowledge in IT infrastructure projects and architected the user profile management product whose successor is now available as Citrix Profile Management. Helge is the author of the popular tools Delprof2 and SetACL. He has presented at Citrix Synergy, BriForum, E2EVC, Splunk .conf and many other events. Helge is very active in the IT community and has co-founded Virtualization Community NRW (VCNRW).
Read more
I just did a Horizon View Upgrade from 5.2 to Horizon 7 for a large customer who uses Zero Clients for every employee. The customer is using Dell Wise P25 Zero Clients for most employees, but still have the older P20 for a select few. Both the P20 and P25 uses chipsets from Teradici, but the firmware on each is slightly different.
After the upgrade, employees using the older P20 Zero Clients would get the following error when trying to connect to their View session:
SSL Session Negotiation Failed or The Zero Client may not be compatible with the host session negotiation cipher settings.
After much research, I found a few KBs and Posts with the apparent “fix”, but none of them worked as they claimed – at least not in this environment. After spending many hours trying to resolve this, I found a solution that worked for this client. I hope this helps someone else.
This issue affects Horizon View 6.2 and 7.0. The root cause of this is due to VMware disabling support for the less secure TLS 1.0 protocol. The P25 Zero Clients need the latest 4.8 Firmware, which addresses the problem, but the P20 Zero Client’s only support firmware up to 4.5, which does not address this issue, so a workaround is needed. After following some blogs about importing a Group Policy, I found it to be a waste of time. So here is what actually works.
On each virtual desktop (or gold image), you’ll need to add the following Registry Key:
HKLMSoftwareTeradiciPCoIPpcoip_admin
Name: pcoip.ssl_protocol
Type: REG_SZ
Value: TLS1.0:TLS1.1:TLS1.2
Or download and import this .reg file I created with these settings: Regedit File Download
This allows TLS 1.0 connections via the installed agent.
On the Connection Server, edit the Connection Server Settings and uncheck Secure Tunnel
View Configuration – Servers – Connection Servers – Edit
This will allow connections to Authenticate through the Connection Server and then connect directly to the Virtual Desktop.
This fixed the issue for the customer until they can replace their older Zero Clients.
*Posts on this site may contain affiliated links*